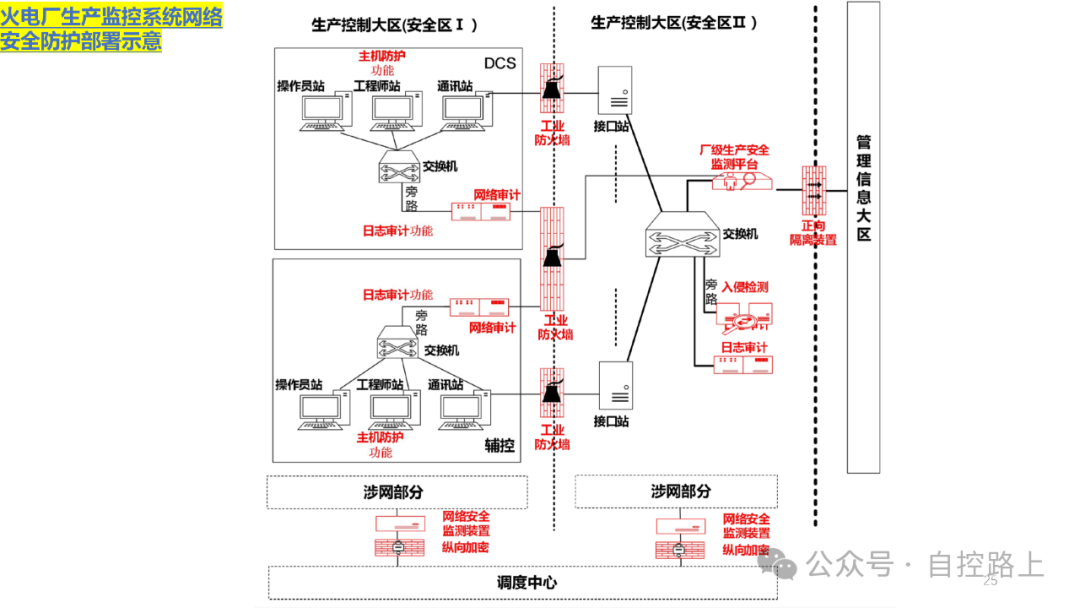
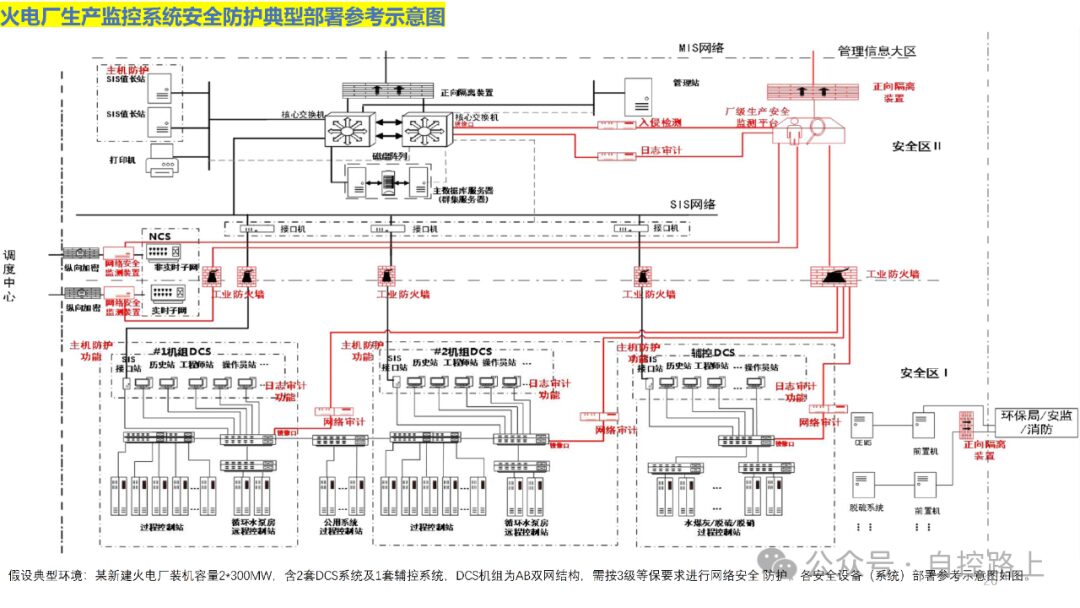
Grade protection is an important policy for national information security construction, which focuses on constructing, managing, and supervising information systems according to their grade and standards. For industrial control security construction, it should center around moderate security and prioritize key protection, focusing on important business systems from a business perspective. The following principles should be followed in the design of the scheme:
Moderate Security Principle
No information system can achieve absolute security. When implementing grade protection for industrial control security, internal areas should utilize switches configured with ACL access control list functions and IP communication filtering strategies. Host terminals should be hardened and equipped with whitelist-based antivirus software to achieve endpoint protection. In planning, a balance must be struck between security requirements, security risks, and security costs. Excessive security demands will inevitably lead to rapid increases in security costs and operational complexity. Moderate security is also the original intention of grade protection construction. Therefore, during the design of grade protection, strict adherence to basic requirements is necessary. Measures should be strengthened at the physical, network, host, application, and data levels to ensure the confidentiality, integrity, and availability of information systems. Additionally, from a cost perspective, corresponding protection strengths should be proposed based on the actual risks of the system, and security protection systems should be designed and constructed according to these protection strengths, effectively controlling costs.
Equal Emphasis on Technical Management Principle
Industrial control security issues have never been purely technical problems. Understanding the prevention of hacker intrusions and virus infections as the entirety of industrial control security issues is one-sided. Simply deploying security products is unlikely to cover all industrial control security issues. Therefore, it is essential to combine technical measures with management measures to more effectively ensure the overall security of information systems, forming a construction scheme that integrates both technical and management aspects.
Zone and Domain Construction Principle
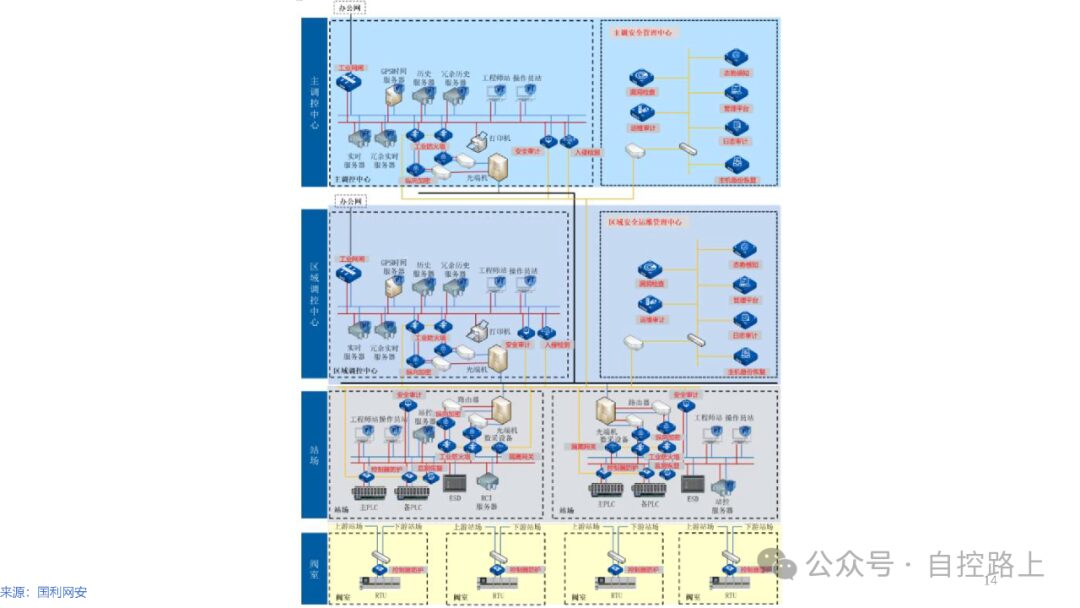
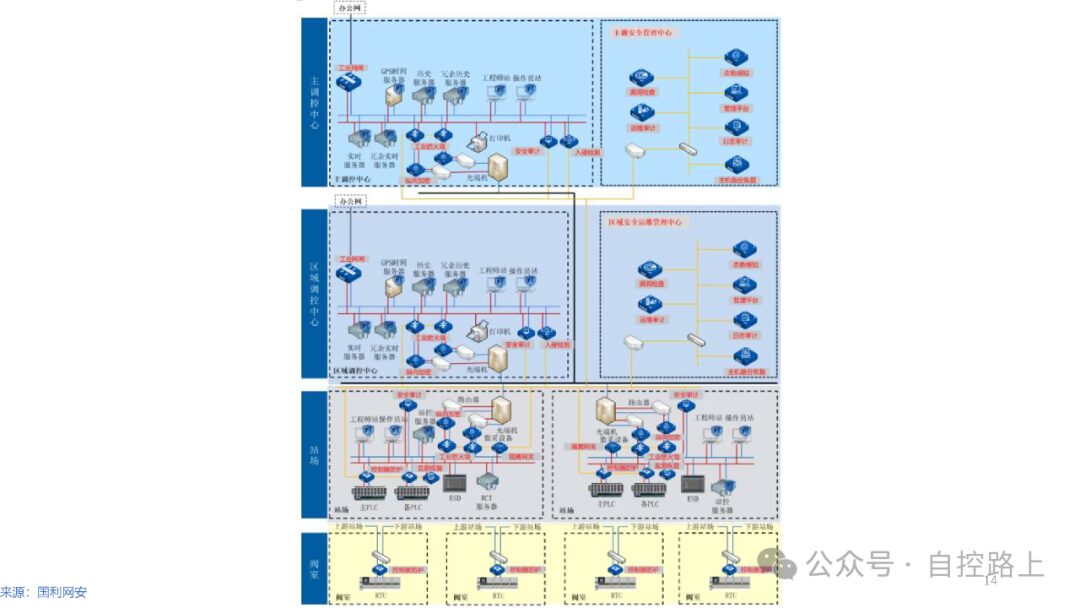
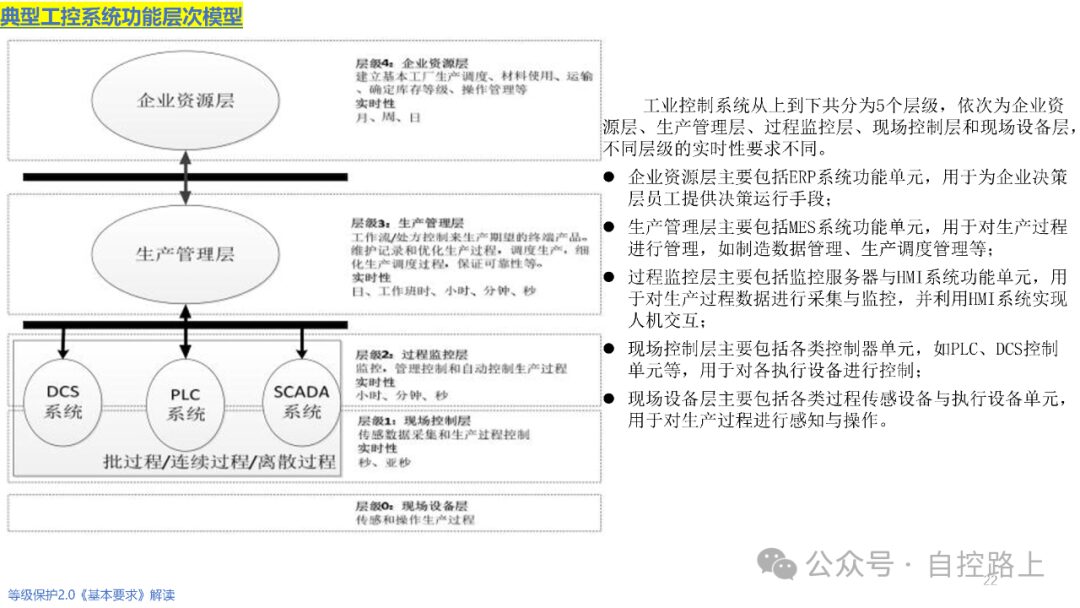
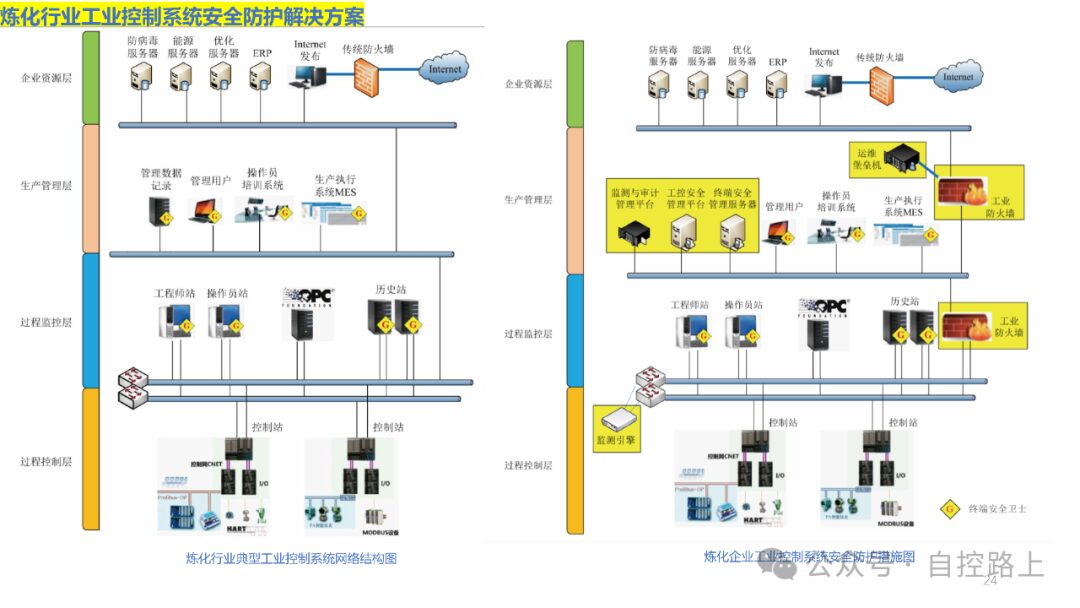
An effective method for securing information systems is through zoning and domain segmentation. Since different information assets within information systems have varying importance and access characteristics, it is necessary to group information assets with similar characteristics for overall protection, thus better ensuring the effectiveness and consistency of security policies. Additionally, zoning and domain segmentation facilitate centralized management of network systems; once a security incident occurs within certain security zones, strict boundary security protection can limit the spread of the incident across the entire network.
Standardization Principle
The security protection system should consider compliance with other standards. The technical part of the scheme will refer to GB/T 25070 for design, while the management aspect will refer to GB/T 22239, making the constructed grade protection system more broadly applicable.
Dynamic Adjustment Principle
Industrial control security issues are not static; they always change with the management-related organizational policies, organizational structures, information systems, and operational processes. Therefore, it is necessary to track changes in information systems and adjust security protection measures accordingly.
Maturity Principle