The ICS Cyber Kill Chain
The ICS Cyber Kill Chain is a report written by Michael J. Assante and Robert M. Lee of the SANS Institute, published in 2015. This report describes the specific processes attackers use to target ICS and abstracts these processes into the ICS Cyber Kill Chain. The report outlines two phases of the ICS kill chain and demonstrates the practical application of the ICS Cyber Kill Chain through case studies of Havex and Stuxnet. This article provides a brief translation and introduction of the main content of the report, promoting its key ideas for discussion purposes only. The copyright remains with the original copyright holder, and any infringing content can be removed.
Cyber attacks on Industrial Control Systems (ICS) are influenced by many factors, including the attacker’s intent, attack complexity, attack capabilities, and the attacker’s familiarity with ICS and automated processes. Attackers do not simply use a single attack action to disrupt systems; rather, they gradually gain access and sufficient information through a series of efforts to achieve their attack objectives. Attack activities target the entire protective measures and systems. Understanding the specific steps of the attacker’s activities helps defenders make more informed security and risk management decisions. Additionally, understanding attacker activities can assist defenders in identifying and assessing possible attack intentions, complexities, capabilities, and familiarity with ICS, which is beneficial in evaluating the potential impact of attack activities on the organization. The authors believe that ICS networks are more defensible than enterprise IT systems. By understanding the inherent advantages of well-architected ICS and the nature of attacks against ICS, security personnel can find practical defensive measures. This article introduces the concept of the ICS kill chain to help defenders understand the network attack activities of attackers.
In 2011, analysts Eric M. Hutchins, Michael J. Cloppert, and Rohan M. Amin from Lockheed Martin created the concept of the Cyber Kill Chain™ to help decision-makers better detect and respond to cyber intrusions. This model is adapted from the military concept of the kill chain and has proven to be a very successful and widely accepted model for defenders in IT and enterprise networks. While the model does not directly apply to the unique nature of ICS network attacks, it provides a solid foundation and concept.
Cyber attacks against ICS can significantly impact production processes or equipment, requiring attackers to have a close understanding of automation processes and the design and decision mechanisms of ICS and security systems. Gaining such knowledge requires attackers to thoroughly study the system to bypass or influence security mechanisms, causing predictable impacts on the system, thereby achieving true cyber-physical attacks rather than simple acts characterized by cyber espionage, ICS sabotage, or intellectual property theft. To achieve such goals, attackers need to launch a two-phase attack against ICS. Multiple phases or more complex kill chains increase the cost of attacks and provide defenders with more opportunities to detect and disrupt attacks. To help everyone visualize ICS attack activities intuitively, this article is divided into three parts. The first two parts introduce the two phases of the ICS Cyber Kill Chain, while the third part demonstrates the practical application of the ICS Cyber Kill Chain through two typical case studies.
The first phase of ICS cyber attacks is similar to traditional espionage or intelligence operations. It is essentially very similar to the attacks defined in Lockheed Martin’s Cyber Kill Chain, aimed at gathering relevant information about ICS, studying the system, and seeking ways to breach internal boundary protections to gain access to the production environment. The process of the first phase is illustrated in the figure below.
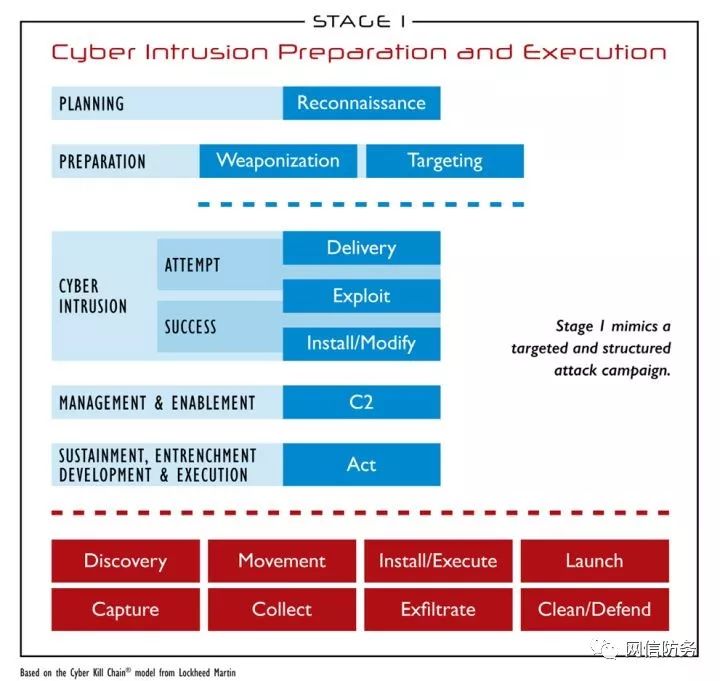
Phase One: Preparation and Execution of Cyber Intrusion
2.1 Planning Phase
The planning phase is the first step of the first phase, primarily involving reconnaissance of the target. Reconnaissance is the activity of gathering information through observation or other detection methods. Planning and reconnaissance for cyber attacks typically involve studying the target system, using open-source information gathering tools like Google and Shodan, and searching publicly available data, such as announcements and social media profiles.
The goal of the planning phase is to identify vulnerabilities in the target system, seeking relevant information for subsequent targeting, payload delivery, and buffer overflow. Information that may be useful to attackers includes personnel, networks, hosts, accounts, and protocol information, as well as related policies, processes, and procedures.
Planning and reconnaissance for ICS attacks may also include researching ICS vulnerabilities and technical characteristics, as well as understanding how to attack production processes and operational models. Passive reconnaissance techniques (often referred to as “footprinting”) can utilize a wealth of publicly available information on the Internet to scout the target system undetected. Active reconnaissance typically involves actively connecting to publicly or privately accessible attack surfaces of the target to understand its operational patterns and determining the operating system or software versions through regular queries.
Attackers may also attempt to hide themselves using normal Internet traffic and activity noise. Publicly available information about the organization helps attackers identify targets, and one thing defenders cannot choose is whether their organization is worth becoming a target.
2.2 Preparation Phase
Preparation is the second step of the first phase, which may include weaponization or targeting. Weaponization involves modifying a harmless file, such as a document file, for use in the next step of the attack. Often, weaponized files remain as document files, such as PDFs, but contain exploit tools. Weaponized document files may also maliciously leverage existing functionalities of certain software, for example, using macros in Word documents to perform part of the attack.
Targeting can also occur in the second step, referring to the identification of potential victim processes by attackers or their agents (such as scripts or tools). In modern military terms, targeting involves analyzing and prioritizing targets and matching appropriate lethal and non-lethal attack actions to these targets to achieve specific attack effects. Cyber attackers weigh their decisions based on the timing and workload of the attack, the likelihood of technical success, and the risk of detection, determining what attack tools or methods to use against the target. For instance, after reconnaissance, an attacker might determine that entering the target network via a Virtual Private Network (VPN) is the optimal strategy, as it allows for the best attack effect with minimal resource expenditure.
Weaponization and targeting can both occur, but neither is a necessary step. In the VPN example, the attacker could directly enter the target network using acquired credentials, thus eliminating the need for the weaponization process. Similarly, an attacker could send weaponized files to multiple targets without needing specific targeting before the attack, selecting targets after gaining initial access.
2.3 Cyber Intrusion Phase
To gain initial access, the third step of the first phase, known as cyber intrusion, is required. Cyber intrusion is any attempt by an attacker to gain access control over the target network or system, whether successful or unsuccessful. This includes the payload delivery process, which requires the attacker to interact with the target network in some way. For example, phishing emails can serve as the payload delivery mechanism for the attacker’s weaponized PDF, or a VPN can deliver the payload to the target network. The next step is exploitation, which is the means by which the attacker executes malicious operations. This means may involve triggering a vulnerability to gain access when a PDF or other file is opened, or directly gaining access to the network by acquiring VPN access credentials. Once exploitation is successful, the attacker will install functional components such as remote access tools or Trojans (Install). The attacker may also replace or modify existing system functionalities (Modify). For example, in newer Windows environments, the PowerShell tool provides attackers with sufficient capabilities to complete the intrusion process without relying on malware. Thus, defenders should focus on discovering and understanding threats without always assuming that threats come from malware.
2.4 Management and Control Phase
After a successful cyber intrusion, the attacker enters the next phase: management and control. The attacker can use previously installed functional components or hijack trusted communication channels like VPNs to achieve management and control functions over the target network (C2, Command and Control). Experienced attackers often establish multiple C2 channels to ensure they do not lose management control after a particular C2 tool is detected or removed, maintaining long-term management and control over the target network. Notably, C2 methods do not necessarily require direct connections that support high-frequency bidirectional communication. For instance, access to protected networks may rely on unidirectional communication paths, which may take more time to relay information out and send commands or code internally. Attackers often hide normal C2 outbound and inbound traffic by hijacking existing communications. In some cases, attackers can also establish their communication bridges by introducing special devices into the target network. By managing and controlling the target network, attackers can achieve their attack objectives.
To reach the ultimate goal, the attack process may also include the following steps: sustainment, entrenchment, development, and execution. At this stage, attackers take action; the complete list of attack activities can be extensive; however, common activities include discovering new systems or data (Discovery), moving laterally within the network (Movement), installing and executing additional functionalities (Install/Execute), launching additional functionalities (Launch), capturing transmitted communications (e.g., acquiring user credentials) (Capture), collecting data (Collect), transmitting data to the attacker (Exfiltrate), and eliminating activity traces and employing anti-forensics techniques to prevent detection (Clean/Defend), such as erasing traces of attack activities or protecting their foothold when faced with network defender incident response activities.
This may be a key step in the planning and execution of the second phase of the ICS Cyber Kill Chain. A wealth of information related to ICS and industrial processes, engineering, and operations is stored within networks connected to the Internet, such as company or enterprise networks. Therefore, defenders must assess what information and tools exist in unprotected networks that could assist attackers in executing attacks against ICS. It should also be noted that attackers can target vendor or partner networks to execute first-phase attacks to obtain necessary information, such as ICS project file transfer pathways or remote access links from integrators or vendors to ICS. When attackers successfully breach the security of ICS and can enter the second phase, the first phase can be considered complete.
Violations in IT networks provide the necessary conditions for first-phase attack actions. It is important to emphasize that if the target network has ICS components connected to the Internet, or if important information about ICS can be obtained through third-party attacks, this phase can be bypassed. Recent Black Energy 2/3 series attempts have sought to enter target systems by attacking devices connected to the Internet.
A significant portion of malware and cyber intrusions within the hacker community occurs in the first phase, making this the most likely place for national-level cyber confrontations and espionage activities. Additionally, criminals are most likely to obtain information of monetary value during this phase.
In many cases, depending on the current target of the attacker, conducting espionage is often more valuable than carrying out actual attacks that include sabotage or manipulation of systems. Sustained access to military targets that impact nations and/or criminal targets provides attackers with opportunities to initiate subsequent actions. Therefore, even in the absence of direct danger or business impact, identifying and remedying the activities of attackers engaged in network intelligence theft is crucial.
The reason ICS network attacks differ fundamentally from traditional IT network attacks is that ICS is composed of underlying engineering and process components and is designed and configured in unique ways, requiring attackers to possess extensive knowledge to impact the system meaningfully. Furthermore, well-architected ICS have multiple layers of systems and security detection sensors, which attackers must traverse each layer in the first phase to gain access to these ICS components. Unfortunately, directly connecting ICS to the Internet has greatly undermined the architectural security advantages of these ICS.
To continue leveraging these inherent defensive architectures, network maintainers must be cautious about their design choices and how they integrate systems. For instance, integrating safety systems (SIS) into the same network as control systems can significantly reduce the workload required for attackers to completely compromise the system. It also substantially reduces the opportunities for defenders to identify attacks and remedy systems. The loss of this defense mechanism, coupled with the increased value of attacks, leads to a significant decline in ICS security. ICS built with appropriate architecture can still be challenging for attackers to meaningfully and predictably impact production processes, even in environments lacking security design (which can be a significant issue). This problem will be demonstrated in the second phase of ICS attacks.
In the second phase, attackers must utilize the knowledge gained in the first phase to specifically develop and test methods capable of meaningfully attacking ICS. Unfortunately, due to the sensitivity of control devices, first-phase attack operations may lead to unintended attack outcomes. This poses a significant risk for nation-state cyber operations, as such attacks may be perceived as deliberate and have unforeseen consequences. For example, attempting to actively discover hosts on the ICS network may disrupt necessary communications or cause communication modules to fail. Simple interactions with ICS applications or their underlying infrastructure components may lead to unintended results. While this activity is included in the first phase, it can have unexpected effects on actions in the second phase. Deliberate attacks occur in the second phase, as illustrated in the figure below.
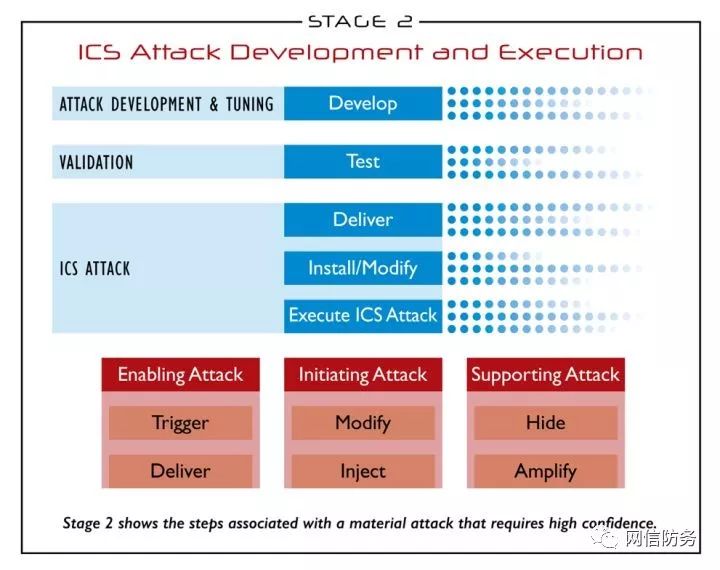
Phase Two: ICS Attack Development and Execution
3.1 Attack Development and Tuning
The second phase begins with the attack development and tuning stage, where attackers need to develop a new functionality specifically designed to impact the target ICS system as desired. This development is likely achieved through filtering specific data.
Only attackers who have a very low assessment of their ability to be detected by system owners and operators would experiment and develop their attack functionalities through real-time production environments. Therefore, under normal circumstances, the development and tuning processes of attackers are difficult to detect. Due to the lengthy development and testing times, there may also be significant delays between actions in the first and second phases.
3.2 Validation
Once attackers develop an attack functionality, the next stage is the validation phase. At this stage, attackers must test their attack functionality on systems with similar or identical configurations to confirm whether the functionality can have a meaningful and reliable impact on the target system. Even simple attacks, such as denial-of-service attacks through increased network scanning traffic, require some level of testing to confirm that scanning can cause the system to deny service. However, for more significant impacts, more complex testing may be required, and attackers may need to obtain real physical ICS devices and software components to complete the testing. While most maintainers find it challenging to keep up with ICS vendor dynamics, various government organizations can leverage their information sources and methods to identify abnormal procurement behaviors of such devices, which may indicate that attackers have completed the first phase of the attack process and are preparing to enter the second phase of the attack process.
3.3 ICS Attack
Ultimately, the actual attack on ICS occurs, where attackers deliver their developed attack functionality (Deliver), install or modify existing system functionalities (Install/Modify), and then execute the attack (Execute). Achieving the ultimate attack objectives may involve many steps (preparatory or concurrent attacks), which can be subdivided into three types: attack preparation (Enable Attack), attack implementation (Initiating Attack), and attack support (Supporting Attack). For instance, modifying specific elements of the process to trigger specific operations, causing changes in setpoints and variables, or employing deception strategies, such as misleading plant operators into believing everything is normal, are all essential steps in the actual attack on ICS.
The complexity of initiating an attack depends on the security of the system, the level of monitoring and control of processes, the degree of security design and its implementation, and the expected impact. For instance, disrupting an ICS through a simple denial-of-service attack is much easier than manipulating the process in a designed manner to attack the system or executing replay attacks (as illustrated in the figure below). Ultimately, attackers need to manipulate production processes to cause significant harm, including reliable or predictable physical damage, damage or modification of controlled devices or process elements (including modifying production schemes, recipes, and mixing plans).
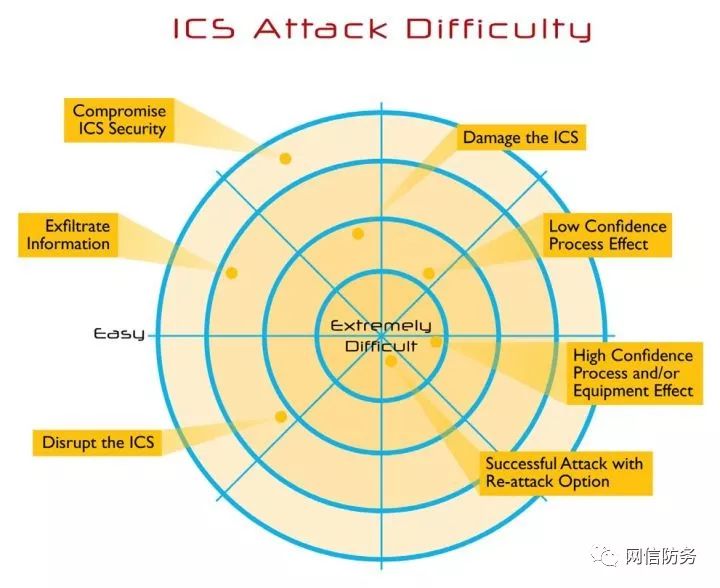
ICS Attack Difficulty Scale
While there are various ways to attack ICS environments, the most common methods of achieving functionality fall into three categories: loss, denial, and manipulation. These include loss of view, denial of view, manipulation of view, denial of control, loss of control, manipulation of control, activation of safety, denial of safety, manipulation of safety, and manipulation of sensors and instruments, as illustrated in the figure below.
There are inherent differences between IT and operational technology (OT) in ICS. For example, a denial-of-service attack on IT systems may severely impact business processes, while manipulation of sensors or processes in ICS has more significant implications, potentially leading to the failure of safety systems (SIS) designed to protect human life, resulting in casualties.
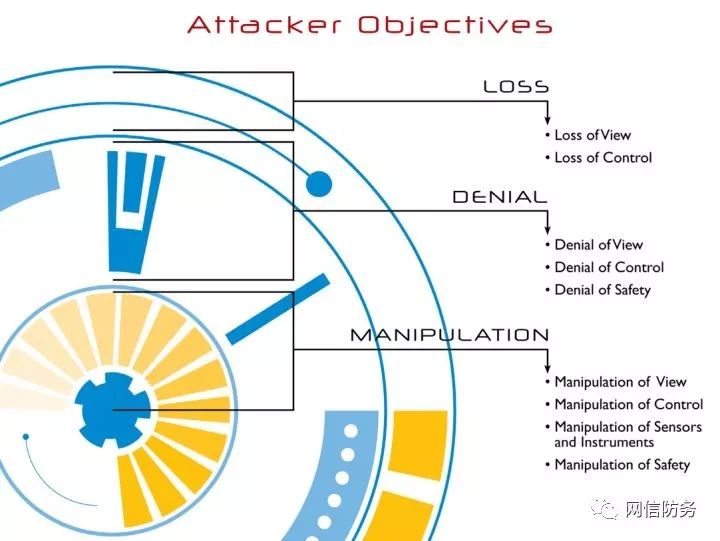
Attacker Objectives
The entire ICS security community does not fully understand what types of consequences can arise from systems suffering cyber attacks. Researchers often reference cases of power grid failures or dam breaches leading to flooding, but other impacts, such as fatal chemical leaks, reduced product quality, and product manufacturing failures due to changes in raw material recipes, are rarely mentioned. Therefore, IT and OT security personnel and national decision-makers must pay close attention to this area to identify the potential consequences and impacts that various facilities may face after being attacked, helping them gain a deeper understanding of attackers’ objectives. Industries must fully consider the issue of ICS facing cyber attacks when conducting equipment forecasting. The current issue is not whether problems will arise, but when problems will occur, and necessary security assessments, security engineering, and security monitoring tasks must be completed to plan and handle potential attack behaviors under the best conditions.
Another effective way to intuitively understand ICS attacks and the ICS Cyber Kill Chain is to study cases of ICS intrusions and attacks.
Analyzing previous cyber intrusion events targeting ICS can validate the effectiveness of the ICS Cyber Kill Chain as a defense model and deepen understanding. The ICS field has historically lacked network visibility and effective forensic evidence and data after being attacked. Therefore, it is challenging to correctly identify and extract all evidence in these cases, but it has been sufficient to understand them at a higher level.
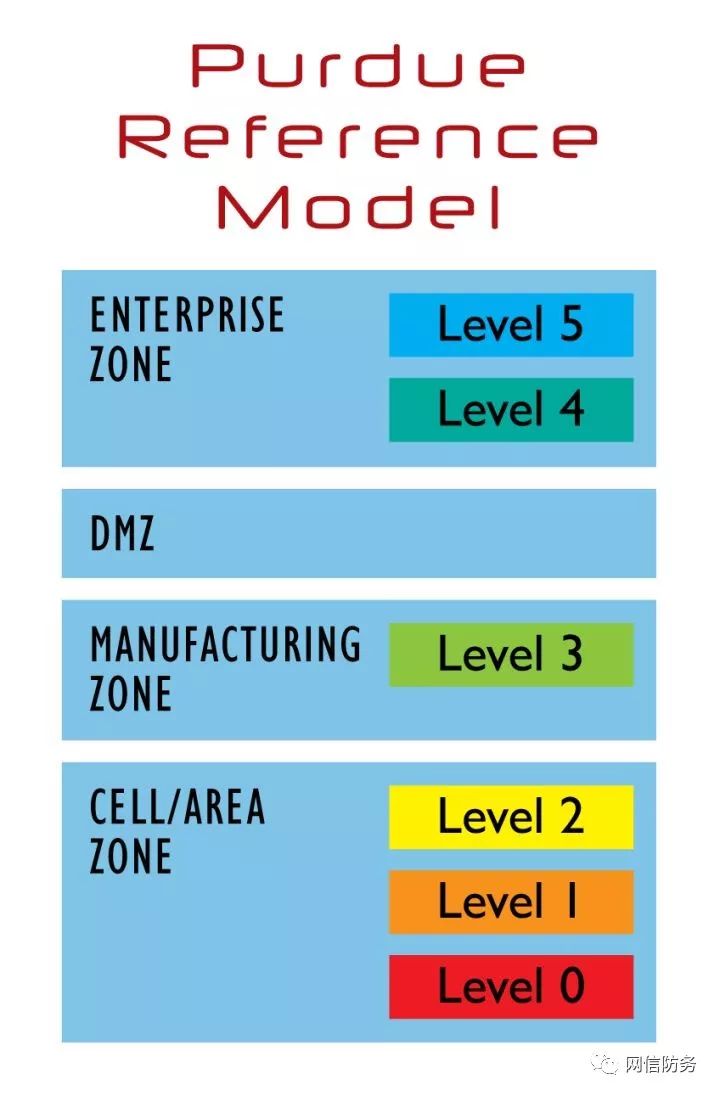
Purdue Reference Model (PERA)
First, it is crucial to understand the layout and structure of a typical ICS network. We use the Purdue Reference Model (as shown in the figure above) to illustrate the architecture of ICS networks.
In the following case studies, the Purdue model will illustrate the architectural layers affected in ICS, while the ICS Cyber Kill Chain will show which phases and steps attackers completed in their activities.
4.1 Havex
The Havex malware can collect sensitive data and network architecture information from thousands of sites worldwide during ICS attacks. It is a Trojan capable of remote access, initially used for cyber espionage but later evolved into a cybercrime tool. It also contains new code modules to adapt to the ICS environment, enabling attacks against ICS systems themselves. Public information confirms that this malware had been active for over three years by the time it was discovered.
There are several methods to implant Havex malware into the target network. The three most common methods are:
-
Sending spear-phishing emails containing malicious code
-
Infecting ICS vendor websites with malware, which infects ICS maintainers when they visit these sites (known as watering hole attacks)
-
Providing an ICS software installer infected with a Trojan, which infects the host system when the installer is run
This combination of multiple attack methods indicates that attackers can maintain flexibility and are not limited to a single technique when conducting attack activities. Observations suggest that attackers successfully identified and exploited vulnerabilities during the planning phase, such as the general trust of engineers, inherited trust, and dependence on the ICS supply chain. Additionally, the attack process utilized three typical intrusion methods from the ICS Cyber Kill Chain.
The first intrusion method involves using spear-phishing emails, where attackers first conduct reconnaissance to identify the target and customize the phishing email for it. Next, attackers combine the attachment file with an exploit and use it as an attachment to the phishing email, thus completing the weaponization process. These phishing emails are sent to pre-selected targets. The email itself serves as the payload delivery mechanism; when the user opens the email attachment, the system installs the Havex malware. Then, Havex attempts to communicate with one of hundreds of C2 servers. Havex then scans the target network to discover ICS components, collect relevant information, and send it to the C2 server, from which attackers retrieve this information. Phishing email attacks primarily affect external networks. Unless the attacked enterprise stores engineering files on the business network, this method is less likely to obtain ICS-related information.
The second intrusion method involves website infections, which can also only achieve first-phase attack objectives but utilize different methods. Notably, the intrusion of ICS vendor websites has its own kill chain, and attacking them serves merely as a stepping stone to penetrate ICS networks. Through reconnaissance activities targeting the ICS network, attackers identify the type of network and vendors for the target ICS. In this way, specific vendor websites become the subjects of weaponization, aiming to target ICS networks using these vendors. The payload delivery method in this scenario involves infecting web pages accessed via the Internet using the HTTP protocol.
Tools from the Metasploit general penetration testing framework can be used to weaponize the website. By exploiting known vulnerabilities, attackers install Havex into the target network, deploying C2 within the target network and completing the same actions as in the first intrusion method. Since access to vendor websites is typically by engineers and network administrators, this intrusion method is more likely to penetrate into ICS networks. This intrusion primarily affects the DMZ area of the ICS network, allowing deeper access to ICS systems for organizations that do not utilize the Purdue model or deep defense architecture.
The third intrusion method is the most creative, placing an infected Trojan ICS software installer on vendor websites. The reconnaissance method is the same as in the second intrusion method. However, in this case, the installer is the primary weaponized carrier, targeting ICS networks using this ICS software. Aside from the payload delivery method, the exploit, attack program installation, C2, and other related operations are the same as in other intrusions. However, the difference in this case is that even in well-architected networks that only allow Internet access from business networks or DMZ, Havex can impact areas at the lower levels of the Purdue model. This method relies on engineers transferring files from Internet-connected computers to internal production control system networks, thereby breaching network security measures (such as boundary controls). In this case, the exploit, installation, C2, and attack action steps all occur within the ICS network. Most infections discovered so far have occurred at the supervisory level, where engineers and operators can access systems such as engineering workstations and Human-Machine Interfaces (HMIs). Attackers gained valuable data from the third intrusion, making it the most commonly used intrusion method for Havex.
To date, no evidence has been observed in the security research field indicating that the attackers of Havex have taken follow-up actions. The authors believe that Havex can be described as a typical attack successfully achieving the objectives of the first phase of the ICS kill chain. So far, no evidence of its second-phase activities has been publicly released. The following figure illustrates the mapping relationship between the three intrusion methods of Havex and the Purdue model and the ICS Cyber Kill Chain.
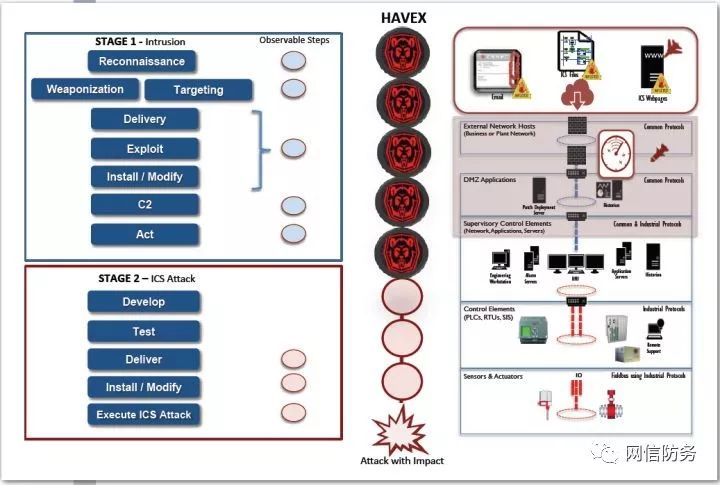
Mapping of Havex to the ICS Cyber Kill Chain and Purdue Model
4.2 Stuxnet Virus
The Stuxnet virus is reported to have caused physical damage to multiple centrifuges at the Natanz facility in Iran, making it an excellent case study for understanding the first and second phases of the ICS Cyber Kill Chain. The Stuxnet virus was only discovered in 2010; however, this attack activity may have been ongoing for several years, with estimates suggesting it began as early as 2006 or 2007. During that time, attackers invested significant efforts to develop a targeted attack tool capable of causing physical damage to centrifuges. The intelligence-gathering activities during this period strongly validate the theory of the ICS Cyber Kill Chain.
The participants behind the Stuxnet virus conducted thorough reconnaissance to determine possible attack paths to the Natanz nuclear facility. However, experts also speculate that physical components may have been used during reconnaissance to obtain confidential data about the facility. To fully understand this case, it is crucial to consider the geopolitical tensions and the impact of physical security. For instance, in 2006, a dissenting group published the purpose and location of the Natanz facility, drawing significant international attention to Iran’s uranium enrichment program. This, along with other non-cyber data, may have significantly contributed to the attackers’ planning and reconnaissance efforts. Additionally, it has been reported that the Natanz facility had a physically isolated network that did not allow traditional methods of attacking ICS through network connections. However, there may have been an internal threat, such as the intentional or unintentional use of infected engineering laptops or removable storage devices (like USB drives) to compromise the network.
The weaponization process involved placing malicious code combined with vulnerabilities on a laptop or removable storage device. The removable storage device or laptop then served as the payload delivery mechanism for the malware to enter the Natanz network. The Stuxnet virus installed itself on various versions of Windows systems and repeatedly executed the exploitation and installation phases, infecting numerous systems until it could access the Internet and contact the attackers’ C2 servers.
The activity of the Stuxnet virus represents a complete two-phase ICS attack process, manipulating production process functionalities through highly customized means to cause physical damage. This attack activity covers all levels of the Purdue model and represents the worst-case scenario encountered by victims in the ICS Cyber Kill Chain. The attack is mapped to the Purdue model, as shown in the figure below.
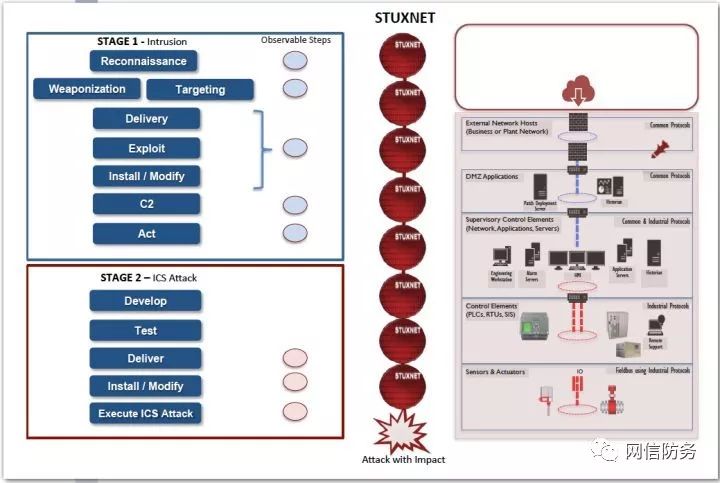
Mapping of Stuxnet to the ICS Cyber Kill Chain and Purdue Model
The ICS Cyber Kill Chain is a model built on a deep understanding of the traditional cyber kill chain, incorporating the characteristics of cyber attacks targeting ICS. By better understanding the different phases of attackers’ ICS attack activities, this model provides ICS maintainers with more opportunities for detection, remediation, and defense. From these opportunities, it can also be seen that ICS networks are more defensible than traditional IT networks, and actions such as limiting the integration of safety systems (SIS) with operational networks and avoiding direct Internet connections for ICS components play a crucial role in maintaining this network defense architecture.
More and more ICS defense models are applicable to the concept of the ICS Cyber Kill Chain. For example, the cybersecurity sliding scale model discusses protective actions and resource investments in greater detail, which can effectively safeguard the physical security, information security, and recoverability of networks. Models similar to the sliding scale model, such as proactive network defense cycles and the concept of deep defense, are crucial defensive theories. By utilizing these emerging models in conjunction with an understanding of the attackers’ ICS Cyber Kill Chain, ICS security personnel can gain more knowledge and leverage this knowledge to enhance the security of ICS more effectively.

Source: Cyber Defense Magazine
