Click the “blue text” above, and select “Set as Star“
Key information will be delivered on D1 time!

The IoT is a double-edged sword. From smart homes equipped with smart locks to kettles that automatically boil morning tea via Wi-Fi, IoT technology simplifies people’s lives, but it can also come with much higher costs. There are some security trade-offs in IoT security, and the downsides may outweigh the benefits.
Before IoT technology enters businesses, homes, and daily life, people need to understand some examples that highlight the importance of security.
IoT Security: IoT Devices Make People Vulnerable
Hackers can access corporate networks through devices on the internet. Nicole Eagan, CEO of cybersecurity service provider Darktrace, described a case of IoT device security where a cyber attacker was able to access the database of an unnamed casino in the United States through a vulnerability in a smart thermometer in the casino’s aquarium.
Before discussing IoT device security guidelines, it is important to understand some examples of IoT security vulnerabilities.
Security Vulnerabilities in Consumer Smart Devices
If you’ve seen reports on how vulnerabilities in Alexa and Google Home smart assistants have been exploited to eavesdrop on users, then concerns about IoT device security are valid. Despite Amazon and Google taking measures each time, they are still thwarted by updated cyber-attack techniques.
Additionally, Samsung’s smart refrigerator also has security vulnerabilities. Because its display is integrated with the user’s Gmail calendar, even though SSL has been deployed to secure the Gmail integration, the refrigerator itself cannot verify the SSL/TLS certificate, opening the door for hackers to access the network and steal login credentials.
It is commendable that Samsung fixed this flaw in a software update, but it is unsettling for a large number of users when even a well-known brand can be attacked and compromised. This reveals an almost inevitable fact that functionality often takes precedence over security, especially for well-known manufacturers. More importantly, in 2015, Samsung also stated that it would collect and use user data in its smart TVs: if a user’s password contains personal or other sensitive information, this information could be captured and transmitted to third parties using voice recognition technology.
For instance, the globally renowned Apple Inc. also struggles to avoid cyber attacks. In February 2019, users discovered a serious vulnerability in Apple’s FaceTime application, allowing cyber attackers to access someone’s iPhone camera and microphone before accepting or declining a call.
As cyber attackers find clever ways to evade security controls to steal data, the resulting damage may be merely destructive, but what if such incidents occur in smart home facilities?
IoT Devices Exploited by Large Botnets like Mirai
Mirai is a type of malware centered around IoT, infecting IoT devices with weak credentials and turning them into remotely controlled bots or botnets. Although the creators of Mirai have been captured, they have released the source code for the malware (possibly to obfuscate and divert attention), and it now has multiple variants.
Botnets have been used to launch various DDoS attacks, including one against Rutgers University and another against Dyn, which provides domain services for well-known companies like Netflix and Twitter.
Security Vulnerabilities in Implantable Medical Devices
In the tech field, hardly any device escapes the control of cybercriminals, including medical devices.
At a Black Hat conference in 2018, Billy Rios from WhiteScope and Jonathan Butts from QED Secure Solutions demonstrated how hackers could attack life-saving implantable medical devices using remote control technology and potentially manipulate them to harm patients. The two security researchers demonstrated how to disable insulin pumps and control the Medtronic pacemaker system. In response, Medtronic cleared this vulnerability, but did not acknowledge the severity of the situation, and even 570 days after this vulnerability alert was submitted to them, the company still did not actively resolve the issue.
People might speculate how a network composed of remotely controlled IoT devices could be used to destroy the power grid (or for monitoring and data collection systems for water supply systems, or control natural gas pipelines, etc.), or how baby monitors could be hacked. These scenarios are unsettling. But it is certain that vulnerabilities in IoT devices will continue to exist. Therefore, to avoid crises, IoT device manufacturers need to pay more attention to the security risks involved, as advanced persistent threats (APT) are more dangerous.
What are the Biggest Security Risks in IoT?
Although there is little voice on what the biggest security risks facing IoT are, some security measures can be taken to protect IoT devices. The Open Web Application Security Project (OWASP) Foundation is a global non-profit organization aimed at raising awareness of security risks in areas such as web application security and mobile device security, so that organizations and individuals can make informed decisions.
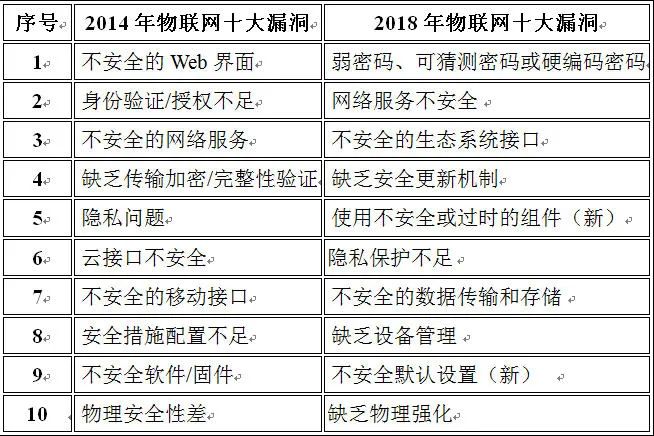
The table below lists the top ten IoT vulnerabilities discovered by the OWASP Foundation in smart devices in 2014 and 2018:
Top Ten Tips for Businesses to Ensure IoT Security
If a business’s smart devices come with unchangeable credentials or any type of authentication/authorization mechanism, then do not purchase and use them. As seen from the OWASP’s list of top ten IoT vulnerabilities in 2018, issues such as insecure ecosystems (like web interfaces and cloud platform interfaces), data security, and physical security have remained in the top ten since before 2014. This provides a clear understanding of the direction and speed of the development of IoT device security. It also raises relevant questions about the effectiveness and adoption rates of IoT security solutions.
However, as IoT becomes an indispensable part of people’s daily lives, maximum efforts must be made to protect connected devices, data, and networks. Here are some measures and methods that can be adopted.
1. Understand the Network and Connected Devices Adopted
When a business’s devices connect to the global internet, these connections can make the business’s network vulnerable to attacks, and if the devices are not adequately secured, cyber attackers can also use these devices. As more and more devices come equipped with network interfaces, it is easy for business staff to forget which devices can be accessed via the network. To ensure security, IT personnel must understand their network, the devices on the network, and the types of information that may be leaked (especially applications with social sharing features).
Cyber attackers use information such as location and personal details to track individuals, which can translate into real-world dangers.
2. Assess IoT Devices on the Network
Once you know which devices are connected to the network, an audit of the devices is required to understand their security. This can be achieved by installing security patches and updates from the manufacturer’s website, checking for updated devices with stronger security features, etc. Additionally, before purchasing devices, it is necessary to understand the security of the brand’s devices. Business procurement and application personnel should ask themselves several questions:
• Do their products report security vulnerabilities that lead to harm?
• Do device vendors meet cybersecurity needs when marketing their products to potential customers?
• How do they implement security controls in their smart solutions?
3. Implement Strong Password Protection for All Business Devices and Accounts
Businesses need to use unique passwords that are hard to guess to protect all their accounts and devices. Avoid using default passwords or common passwords (like “admin” or “password123”). If necessary, use a password manager to track all passwords. Ensure that the business and its employees do not use the same password across multiple accounts, and ensure they are changed regularly.
These steps help prevent all their accounts from being compromised. In addition to password expiration dates, it is necessary to ensure that limits are set on incorrect password attempts and that account lockout policies are implemented.
4. Use a Separate Network for Smart Devices
Using a different network for smart devices than the home or business network may be one of the most strategic methods to enhance IoT security. Through network segmentation measures, even if cyber attackers find a way to access the business’s smart devices, they cannot access the business’s operational data.
5. Reconfigure Default Device Settings
Often, many smart devices come with insecure default settings out of the box. Worse yet, sometimes these devices cannot have their configurations modified. Businesses need to evaluate and reconfigure default credentials, intrusive features and permissions, open ports, etc., according to their requirements.
6. Install Firewalls and Other Known IoT Security Solutions to Identify Vulnerabilities
Install firewalls to block unauthorized network traffic and run intrusion detection systems (IDS)/intrusion prevention systems (IPS) to monitor and analyze network traffic. Businesses can also use automated vulnerability scanners to discover security vulnerabilities in their network infrastructure. Use port scanners to identify open ports and see what network services are running. Determine if these ports are necessary and check if the services running on them have known vulnerabilities.
7. Use Strong Encryption and Avoid Unsecured Network Connections
If a business decides to remotely check smart devices, never use public Wi-Fi networks or networks that do not implement reliable encryption protocols for checks. Ensure that the business’s network settings are not operating on outdated standards (such as WEP or WPA), but are using WPA2 standards. Unsecured internet connections make business data and devices vulnerable to cyber attackers. Although WPA2 itself is known to be susceptible to key reinstallation attacks or KRACK attacks, and WPA3 is susceptible to Dragonblood attacks, installing updates and patches is the only way to keep business operations secure and can minimize risks.
8. Disconnect from the Network When Devices and Features are Not in Use
Review application permissions and read the privacy policies of these applications to understand how they intend to use the shared information. Unless the business needs to use features like remote access or voice control for more persistent IoT security checks, these features must be disabled. If needed, they can be enabled at any time. When businesses are not using devices, they should consider completely disconnecting them from the network.
9. Disable Universal Plug and Play (UPnP) Features
Universal Plug and Play features are designed to seamlessly connect network devices without configuration, but vulnerabilities in the UPnP protocol make these devices more easily discoverable by hackers. Plug and Play (UPnP) features are enabled by default on many routers, so unless businesses are willing to sacrifice security for convenience, they need to check the settings and ensure they are disabled.
10. Ensure Device Security through Physical Security Measures
Be careful not to lose phones, especially when they have applications that can control IoT devices. If this happens, in addition to having PIN/password/biometric protection on the device, ensure that users have the ability to remotely wipe phone data. Set up automatic backups or selectively back up any device data that the business may need.
Additionally, limit the accessibility of the business’s smart devices. For example, does the refrigerator need a USB port? Allow access to the minimum number of ports and consider not allowing web access (local access only) whenever possible.
Some Analysis Tools for IoT Security
In addition to the IoT security solutions discussed above, businesses have several other tools available to better view and control their networks. Wireshark and tcpdump (command-line utilities) are two open-source tools that can be used to monitor and analyze network traffic. Wireshark is more user-friendly because it has a GUI and various sorting and filtering options.
Shodan, Censys, Thingful, and ZoomEye are tools that can be used for IoT devices (like search engines). ZoomEye may be a more suitable tool for new users as it automatically generates search queries after clicking filters.
ByteSweep is a free security analysis platform provided by device manufacturers, which is another tool that testers can use for inspections before products leave the factory.
Overview of IoT Security
No matter how great the risks are, it is an undeniable fact that IoT technology has immense potential. The connectivity of IoT proves its usefulness in solving various environments and tasks. However, problems may arise when businesses rush to adopt some immature technologies and products, either completely ignoring potential security risks or not giving them enough attention.
Before developing secure and reliable products, raising customer awareness, and launching new devices, rigorous testing needs to be conducted, which can largely address many currently overlooked IoT security issues.
Copyright Notice:This article is compiled by D1Net. When reprinting, please indicate the source as: D1Net. If not indicated, D1Net reserves the right to pursue legal responsibility.
(Source: D1Net)
If you work in any field of enterprise IT, networks, or communications and wish to share your insights, you are welcome to contribute to D1Net. Submission Email: [email protected]
Submission Email: [email protected]
Click the blue text
to follow
You can also search the public account “D1net” to follow sub-public accounts in various fields under D1net (cloud computing, data center, big data, CIO, enterprise communication, enterprise application software, network communication, information security, servers, storage, AI, smart city IoT, etc.).
