Privacy protection? It’s not to scare everyone; information is transparent, but we should still try to maintain personal privacy. Today, we will learn about symmetric encryption and asymmetric encryption.
First, let’s read this character “钥”, is it pronounced “yao” or “yue”? Check the image below.

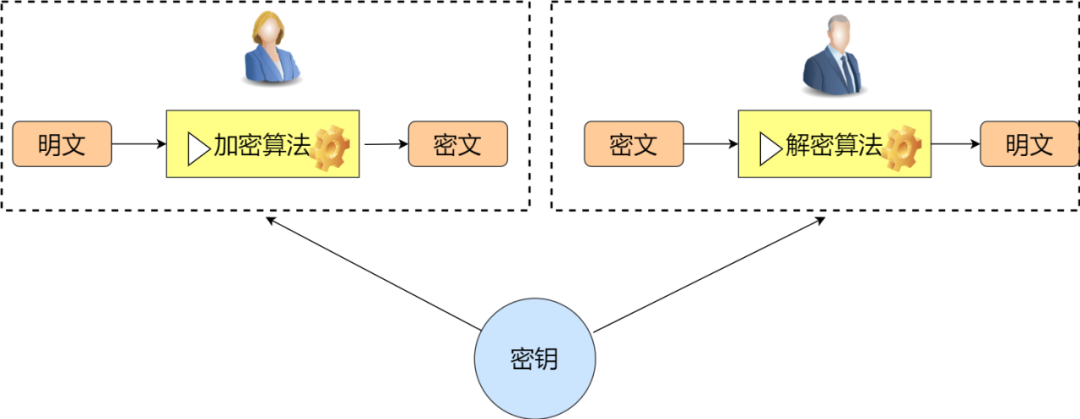
1. Symmetric Encryption
As the name suggests, in symmetric encryption, both the encrypting and decrypting parties use the same key (secret key). Specifically, the sender uses the corresponding encryption algorithm and key to encrypt the information to be sent; for the receiver, they use the decryption algorithm and the same key to unlock the information, thus being able to understand the sender’s message.
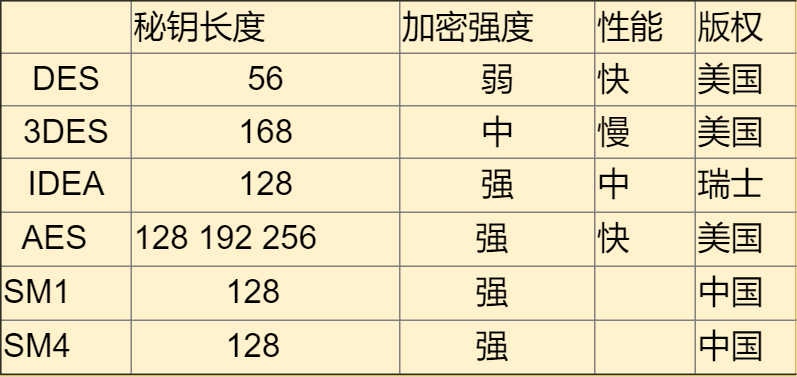
1. Common Symmetric Encryption Algorithms
Whether for storing information in databases or to prevent user cookies from leaking, corresponding encryption algorithms are usually employed to maximize the protection of sensitive information.
DES
DES uses a key that is superficially 64 bits long, but only 56 bits are actually used in the algorithm; the remaining 8 bits are used for parity checking and are discarded in the algorithm. Therefore, the effective key length of DES is 56 bits, which is commonly referred to as the key length of DES. Assuming the key is 56 bits, using a brute force attack would yield 2 to the power of 56 possible keys, requiring approximately one year to decrypt if executed once per nanosecond. However, no one does this. DES is no longer considered a secure encryption method, mainly due to its short 56-bit key.
IDEA
The International Data Encryption Algorithm (IDEA) uses a key length of 128 bits, with the advantage of having no patent restrictions.
AES
After DES was cracked, the AES algorithm was introduced shortly thereafter, offering three key lengths for selection: 128 bits, 192 bits, and 256 bits. To ensure that performance is not significantly affected, 128 bits is usually chosen.
SM1 and SM4
The previous algorithms were all foreign; we have domestically researched the national standards SM1 and SM4. Both are state standards, and the algorithms are public. The advantages are strong support and recognition from the state.
Summary of Several Algorithms
2. Asymmetric Encryption Algorithms
In symmetric encryption, the sender and receiver use the same key. In asymmetric encryption, however, the sender and receiver use different keys. The main problem it addresses is preventing leakage during the key agreement process. For example, in symmetric encryption, if Xiao Lan encrypts the message to be sent and tells you the password is 123balala, it is easy for others to intercept the password. In contrast, in asymmetric encryption, if Xiao Lan tells everyone the password is 123balala, it is useless for an intermediary because they do not have the private key. Thus, asymmetric keys mainly solve the problem of key distribution. As shown in the image below.
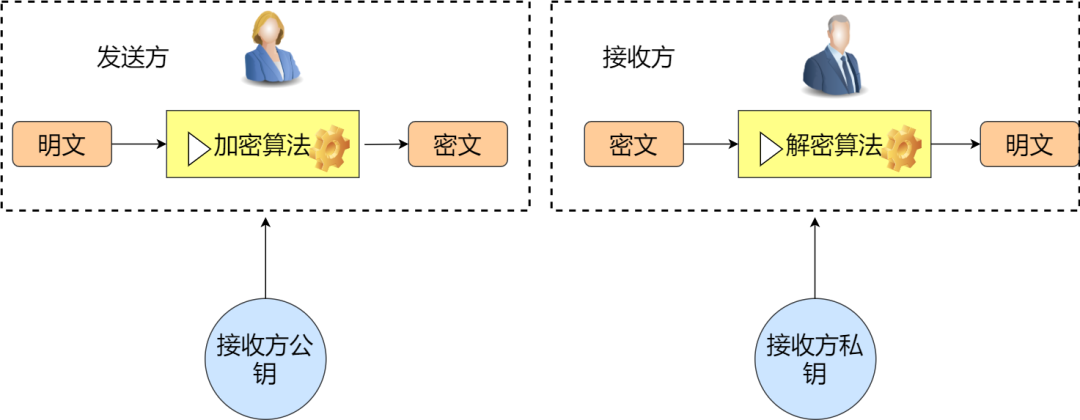
In fact, we often use asymmetric encryption. For example, when building a big data platform with multiple servers using Hadoop, key distribution is involved for convenient passwordless login across machines. Similarly, when setting up a Docker cluster, related asymmetric encryption algorithms are also used.
1. Common Asymmetric Encryption
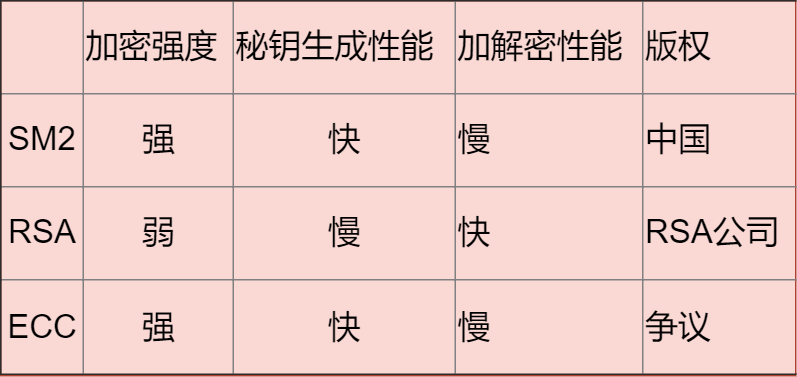
RSA (RSA Algorithm)
The advantage is that it is relatively fast. If higher encryption difficulty is desired, a long key is needed.
ECC
Proposed based on elliptic curves. It is currently the asymmetric encryption algorithm with the highest encryption strength.
SM2
Also designed based on elliptic curve problems. Its biggest advantage is national recognition and strong support.
Comparison of Three Algorithms
3. Hash Algorithms
This is something everyone should be more familiar with, such as the MD5 checksum we commonly use. In many cases, it is not used for encryption but to obtain a unique ID. During system development, various user password information is usually stored using hash algorithms, ultimately storing their hash values.
1. Common Hash Functions
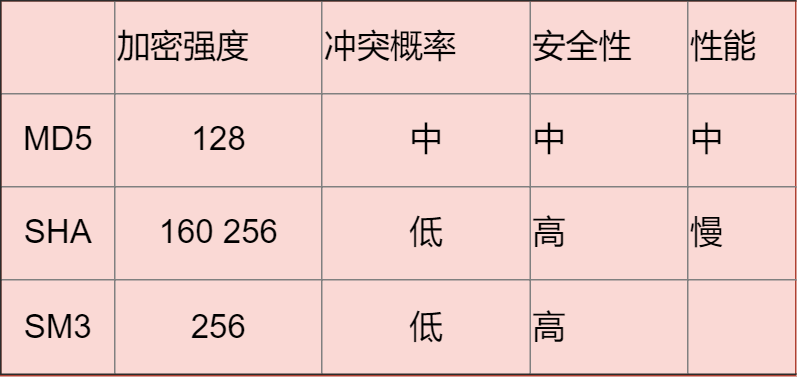
MD5
MD5 can generate a 128-bit message digest and is currently the most commonly used hash algorithm. Although its uniqueness has been compromised due to algorithm flaws, it does not pose a security problem in most scenarios. However, if the length is not limited (32 characters), it is still not recommended to continue using MD5.
SHA
Secure Hash Algorithm. SHA is divided into SHA1 and SHA2 versions. The algorithm’s idea is to receive a piece of plaintext and convert it into a ciphertext in an irreversible manner, which can also be simply understood as taking a string of input codes (called pre-mapping or information) and transforming them into a shorter, fixed-length output sequence known as a hash value (also referred to as information digest or information authentication code).
SM3
The national encryption algorithm SM3 has encryption strength similar to SHA-256. It is primarily supported by the state.
Summary
In conclusion, in most cases, use symmetric encryption, which offers good security. If distributed key distribution is needed, consider asymmetric encryption. If reversible computation is not required, use a hash algorithm. As there has been demand in this area recently, I have reviewed some materials. Thank you all for reading!
References
https://www.sdnlab.com/21145.html
https://blog.csdn.net/andylau00j/article/details/54427395
https://time.geekbang.org/
