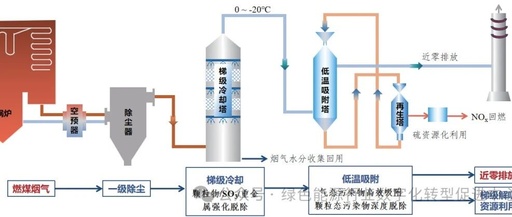
Innovative Case Study of Green Technology (44): Near-Zero Emission Control Technology for Flue Gas Pollutants Using Low-Temperature Method (COAP)
Company Overview The Huaneng Clean Energy Research Institute is committed to serving the country’s high-level technological self-reliance and strength, taking the lead in the innovation of new energy technologies in China’s power industry. It aims to build a first-class international research institution characterized by low-carbon clean energy, positioning itself as the technological engine for the … Read more