1. Overview of Cybersecurity
1.1 Definition
Information Security: The technical and managerial security measures established and adopted for data processing systems, protecting computer hardware, software, and data from accidental and malicious destruction, alteration, and disclosure.
Cybersecurity:
-
Prevent unauthorized users from accessing information -
Prevent unauthorized attempts to destroy or modify information
1.2 Characteristics of Information Security
-
Availability: Ensures that authorized users can access information and use related information assets when needed. -
Integrity: Protects information and its processing methods to ensure they are accurate and complete. -
Confidentiality: Ensures that only authorized individuals can access the information.
1.3 Threats to Cybersecurity
-
Active Attacks selectively destroy information in various ways, including adding, modifying, deleting, forging, replaying, scrambling, impersonating, and introducing viruses. -
Passive Attacks do not interfere with the normal operation of network information systems, involving eavesdropping, interception, theft, decryption, and traffic analysis.
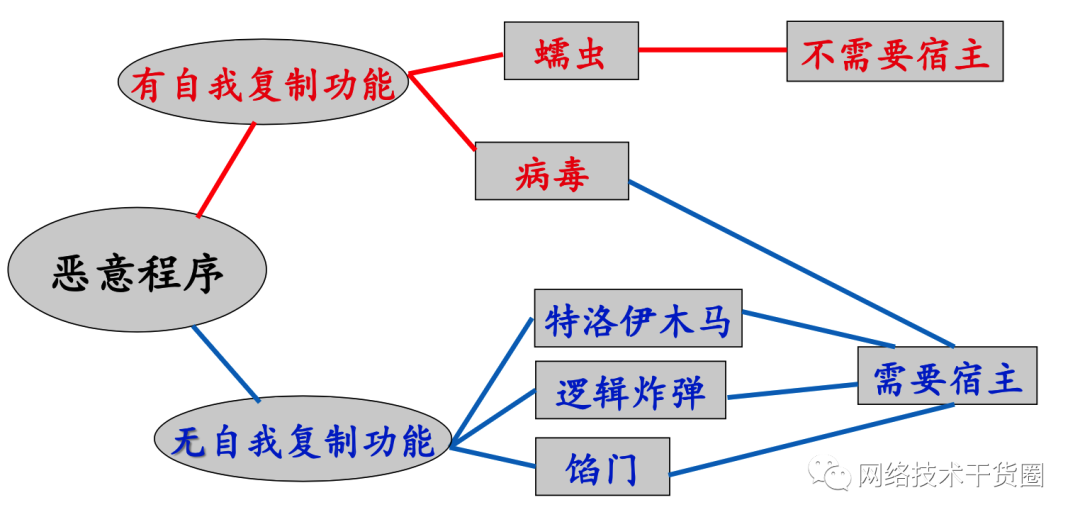
Malicious Attacks: Trojan horses, hacker attacks, backdoors, computer viruses, denial-of-service attacks, internal and external leaks, worms, logic bombs, and data loss or destruction.
-
Hacker Attacks: Hackers use computers as attack agents, sending requests to remote systems that become targets, leading to information theft. -
Trojans: Trojans spread via email or by injecting free software games. When the software or email attachment is executed, the Trojan is activated, releasing its payload to monitor computer activity, install backdoor programs, or transmit information to hackers. -
Denial of Service Attack (DoS): Refers to deliberate attacks on network protocol implementations or directly exhausting the resources of the target system, rendering it unable to provide normal services or resource access, causing the target system to stop responding or even crash. Common DoS attacks include bandwidth attacks and connectivity attacks. -
Distributed Denial of Service Attack (DDoS): (1) The target host has a large number of pending TCP connections; (2) The network is flooded with a large number of useless packets; (3) The source address is fake, generating high traffic of useless data, causing network congestion, preventing the victim host from communicating normally with the outside; (4) Repeatedly sending specific service requests at high speed exploiting flaws in the transmission protocol provided by the victim host, preventing the host from processing all normal requests; (5) In severe cases, the system may crash. -
Viruses: Parasitic in host files, embedding virus code into host files, targeting local programs or files. The key to prevention is to remove the virus code from the host file. -
Worms: Independent programs that replicate themselves. They infect other computers on the network through system vulnerabilities. The key to prevention is to patch the system. -
Vulnerabilities: Refers to defects in hardware, software, or policies that allow unauthorized users to gain access to the system without authorization or elevate their access privileges. With such access, unauthorized users can do as they please, posing a threat to network security. Distinguishing from backdoors: A backdoor is a universal access password intentionally set in the program by the hardware or software manufacturer for unauthorized access, posing a serious threat to user system security regardless of whether the password is compromised or solely held by the manufacturer. Vulnerabilities and backdoors are different; vulnerabilities are unpredictable, while backdoors are intentionally set. -
TCP Hijacking Attack: A attempts to establish an encrypted session with B, while a hacker hijacks the communication, pretending to be B, and exchanges keys with A, then pretends to be A to establish a session with B. -
IP Spoofing: Hackers change the original address to deceive firewalls, allowing packets to pass through, mistakenly regarded as legitimate communication, leading the spoofed packets into the intranet for destruction.
1.4 Characteristics of Cybersecurity
-
Confidentiality: Network information is not disclosed to unauthorized users, entities, or processes. Information is only available to authorized users. Confidentiality is an important means of ensuring network information security based on reliability and availability. Common confidentiality technologies (1) Physical Confidentiality: Using various physical methods, such as restrictions, isolation, shielding, and control, to protect information from being disclosed (lock cabinets, close doors, watch people). (2) Anti-eavesdropping: Preventing opponents from intercepting useful information. (3) Radiation Protection: Preventing useful information from radiating through various means, e.g., anti-peeping. (4) Information Encryption: Under the control of keys, using encryption algorithms to encrypt information. Even if opponents obtain the encrypted information, they cannot understand the effective information without the key. -
Integrity: Network information remains unaltered during storage or transmission, preventing accidental or intentional addition, deletion, modification, forgery, scrambling, replaying, etc. Integrity is a security feature focused on information, requiring the preservation of the original information, i.e., correct generation, correct storage, and correct transmission. Methods to ensure integrity: (1) Good Protocols: Various security protocols can effectively detect copied information, deleted fields, invalid fields, and modified fields. (2) Checksum Methods: An important means of resisting tampering and transmission failures. (3) Digital Signatures: Ensuring the authenticity of information and guaranteeing its non-repudiation. (4) Notarization: Requesting network management or intermediary organizations to verify the authenticity of information. -
Reliability: (1) The ability of a system to complete specified functions within specified conditions and time is a fundamental goal for the operation and construction of all network information systems. (2) Measured by resilience, survivability, and effectiveness. (3) Reliability is the probability that a system can correctly perform its functions within a given time and under specified conditions. (4) Improving reliability requires emphasizing reducing the number of system interruptions (failures). -
Availability: (1) Network information can be accessed and used by authorized entities as needed. This means the network information service allows authorized users or entities to use it when needed, or provides effective services to authorized users even when part of the network is damaged or needs to be downgraded. (2) Availability is the probability that the system can operate normally at any moment during task execution, usually measured by the ratio of system uptime to total working time. (3) Improving availability requires emphasizing reducing recovery time from disasters. (4) It reflects the overall reliability, maintainability, and maintenance support of products. -
Non-repudiation: (1) Also known as non-deniability, during the information exchange process in network information systems, it ensures the true identity of participants. (2) All participants cannot deny or repudiate the operations and commitments they have completed. Methods to ensure non-repudiation: (1) Using information source evidence can prevent the sender from falsely denying having sent the information; using delivery receipt evidence can prevent the receiver from later denying having received the information. (2) Digital Signature Technology is one of the means to solve non-repudiation. -
Controllability: The ability to control the dissemination and content of information to prevent the spread of undesirable content.
2. Intrusion Methods
2.1 Hackers
Hackers: Refers to technical experts or enthusiasts who enjoy solving problems and overcoming limitations. Crackers: Those who enjoy breaking into other people’s systems. The main difference between hackers and crackers is that hackers create new things, while crackers destroy things.
2.1.1 Intrusion Methods
(1) Physical Intrusion: Intruders bypass physical controls to gain access to systems, having physical access rights (e.g., they can use the keyboard). Methods range from console privileges to physically participating in the system and removing disks (reading/writing on another machine). (2) System Intrusion: Already having lower privileges of system users. If the system has not applied the latest vulnerability patches, it provides intruders an opportunity to exploit vulnerabilities to gain administrator privileges. (3) Remote Intrusion: Accessing systems remotely through the network. Intruders start from no privileges. This type of intrusion includes various forms. If there is a firewall between them and the victim host, intrusion becomes much more complex.
2.1.2 Threats to Systems
-
Software Bugs: Software bugs exist in server background programs, client programs, operating systems, and network protocol stacks. -
System Configuration: (1) Default Configuration: Many systems are delivered to customers with default, user-friendly configurations. (2) Lazy System Administrators: A shocking number of hosts are configured without system administrator passwords. (3) Generated Vulnerabilities: In fact, all programs can be configured in an insecure mode. (4) Trust Relationships: Intruders often use