Click the blue text to follow us with one click
“ Dream Thinker NetworkSecurity Guardian ”

Security researchers indicate that RFC 7252, also known as the Constrained Application Protocol (CoAP), is about to become one of the most abused protocols in DDoS attacks.
What is CoAP?
CoAP was officially approved in 2014 and has only been widely used since this year. It is a lightweight machine-to-machine (M2M) protocol that can run on smart devices with limited memory and computational resources. Simply put, CoAP is very similar to HTTP, but it operates over UDP instead of TCP, making UDP a lighter alternative to TCP for data transmission.
Just as HTTP is used to transmit data and commands (GET, POST, CONNECT, etc.) between clients and servers, CoAP also allows similar multicast and command transmission functionalities but with fewer resources, making it an ideal choice in the rapidly evolving Internet of Things (IoT) device environment. However, like any other UDP-based protocol, CoAP is inherently vulnerable to IP address spoofing and packet amplification, which is a primary reason for its susceptibility to DDoS attack abuse.
Attackers can send a small UDP packet to a CoAP client (IoT device), which will respond with a larger packet. In the world of DDoS attacks, the size of this packet response is referred to as the amplification factor, which for CoAP can range from 10 to 50, depending on the initial packet and the resulting response (the extent and the protocol analysis you are reading).
Moreover, due to CoAP’s vulnerability to IP spoofing, attackers can replace the “sender IP address” with the IP address of the victim they intend to target with DDoS attacks, causing the victim to suffer from the amplified CoAP traffic.
The designers of CoAP added security features to prevent these types of issues, but as noted by Cloudflare, if device manufacturers implement these CoAP security features, then the CoAP protocol would no longer be as convenient, negating all the advantages of a lightweight protocol. This is why most CoAP implementations today use the “NoSec” security mode instead of a hardened security mode, which keeps the protocol lightweight but also makes it vulnerable to DDoS attacks.
The Rise of CoAP
In the past, due to CoAP’s role, even if all devices were running in NoSec mode, those vulnerable devices would not pose a problem. However, the reality has changed. According to Dennis Rand, founder of eCrimeLabs, who spoke at this year’s RVAsec security conference, the number of CoAP devices has surged since November 2017. This explosive growth is attributed to CoAP being used as part of the QLC chain (formerly known as QLink). The QLC chain is a project aimed at utilizing available WiFi nodes across China to build a decentralized mobile network based on blockchain.
Device Count Chart
However, this sudden increase in readily available and poorly secured CoAP clients has gone unnoticed. In recent weeks, the first DDoS attacks conducted through CoAP have begun to take effect.
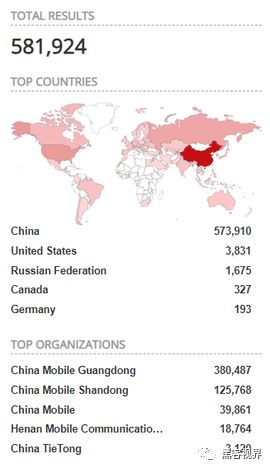
A security researcher dealing with DDoS attacks told foreign media that the frequency of CoAP attacks has been increasing over the past few months, evolving from occasional occurrences to an average transmission speed of 55Gbps, with the maximum reaching 320Gbps. According to data from Link11, a company specializing in DDoS handling, the average attack strength of 55Gbps is an order of magnitude higher than the typical DDoS attack of 4.6Gbps. Among the 580,000 CoAP devices currently available on Shodan, about 330,000 (ab) are used for relaying and amplifying DDoS attacks, with amplification factors of up to 46 times. In the attacks recorded by researchers, most targeted various online services in China, as well as some MMORPG (massively multiplayer online role-playing) platforms outside mainland China. It is still unclear whether CoAP has been added as an attack option on DDoS-for-hire platforms, but if this occurs, the negative impacts of such attacks will be further exacerbated.
As with most protocols developed using IoT, the key issue seems not to be the protocol design related to security features but rather how device manufacturers configure and deliver CoAP in real-time devices.
Unfortunately, this is not uncommon. Many protocols are often misconfigured by device manufacturers, either accidentally or intentionally, with manufacturers tending to prioritize interoperability and practicality (rather than security) as the primary reference factor for configuration. Many believe that if countries around the world had stricter regulations on IoT devices and their security features, such disasters could have been entirely avoided.
This article was compiled by Hacker Vision from various online sources; please indicate “Reprinted from Hacker Vision” and include a link when reprinting.


Click to read the original article for more information

