Abstract
This article discusses the development of information security software and monitoring for industrial control systems, introduces the architecture of information security software and monitoring for industrial control systems, and provides a detailed analysis of information security software and monitoring across various layers including the field device layer, field control layer, process monitoring layer, manufacturing execution system (MES) layer, and enterprise management layer. It also analyzes the trends in information security software and monitoring for industrial control systems.
1 Introduction
To meet the requirements of information security standards for industrial control systems and product functionality, suppliers of industrial control systems are developing information security software for their products to satisfy the urgent needs of mainstream industrial users in today’s market, thereby achieving a dominant position in the market. Due to the frequent occurrence of information security incidents in industrial control systems, suppliers are also developing better and deeper information security software for their products. Simultaneously, to facilitate industrial users in managing the operation of industrial control systems and their information security operations, industrial control system suppliers are striving to address these challenges and develop corresponding information security monitoring software for industrial control systems. Consequently, a variety of information security monitoring software from different industrial control system suppliers has begun to emerge in the market.
With the rapid advancement of cybersecurity, the network security of industrial control systems, as an important component of cybersecurity, has attracted significant attention. Industrial control system suppliers have weaknesses in this area, thus traditional information security product suppliers, leveraging their expertise in cybersecurity, are rapidly entering the industrial control system field to develop corresponding information security products and software. Initially, these information security product suppliers installed necessary network isolation devices for industrial control system users to meet their information security requirements and configured appropriate monitoring software. Additionally, to expand the monitoring of the entire network of industrial control systems, they collaborated with industrial control system suppliers to jointly develop solutions that extend the monitoring of original network isolation devices and integrate partial events and network alarm records from various control networks and devices of industrial control system suppliers, making comprehensive monitoring of the entire network of industrial control systems possible. Consequently, software monitoring such as industrial safety monitoring and auditing platforms and industrial safety control platforms has gradually emerged to meet the information security requirements of industrial control system users.
At the same time, we should also note that industrial control system suppliers are developing information security software for industrial control system products, while information security product suppliers are developing network isolation devices, industrial safety monitoring and auditing platforms, and industrial safety control platforms. This effectively meets the general information security needs of industrial control system users. However, with the rapid growth of industrial control system users, large-scale industrial control system users are continuously expanding. For large-scale enterprise users or group-level users, effective management of information security across various factories’ industrial control systems is required, which also necessitates this information at the factory or group level. Therefore, some suppliers specializing in Enterprise Resource Planning (ERP) management software are also starting to consider how to integrate information security information for industrial control systems into their existing ERP software products. Consequently, Governance, Risk, and Compliance (GRC) management software is beginning to enter the public’s view, indicating that the information security management of industrial control systems for large-scale enterprise users can be incorporated into the GRC management platform.
Through cooperation among industrial control system suppliers, information security product suppliers, and enterprise management software suppliers, the development of information security software and monitoring technology for industrial control systems is being jointly promoted, providing more options for information security management to industrial control system users. Among them, the software and monitoring from industrial control system suppliers and information security product suppliers are essential configurations, while the software and monitoring from enterprise management software suppliers should be selected based on the scale and management requirements of the enterprise.
Next, we will introduce the architecture of information security software and monitoring for industrial control systems, provide a detailed analysis of information security software and monitoring for industrial control systems, and analyze the trends in information security software and monitoring for industrial control systems.
2 Architecture of Information Security Software and Monitoring for Industrial Control Systems
The architecture of information security software and monitoring for industrial control systems can be illustrated according to the ANSI/ISA-99.00.01 enterprise hierarchical model, as shown in Figure 1.
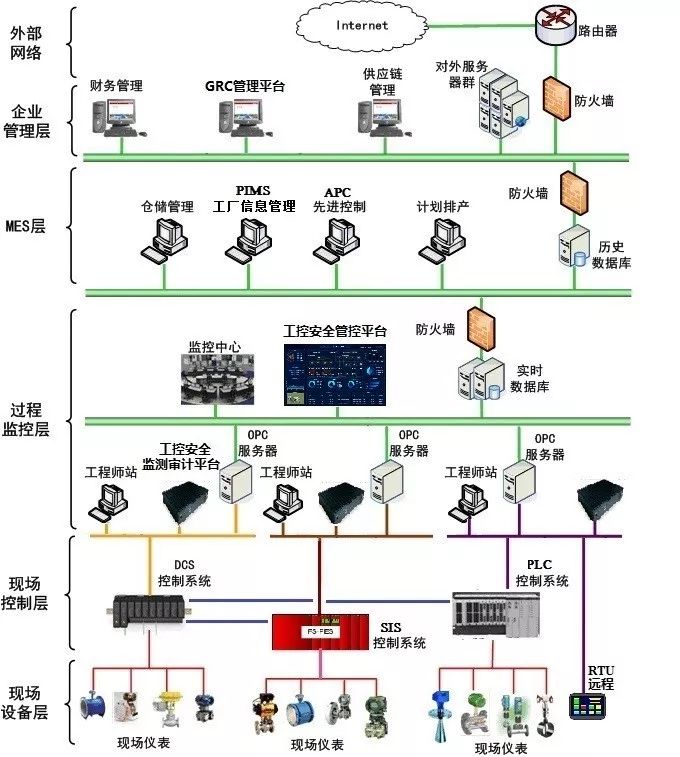
Figure 1 Schematic Diagram of Typical Information Security Software and Monitoring Architecture for Industrial Control Systems
A typical industrial control system includes the field device layer, field control layer, process monitoring layer, manufacturing execution system layer, enterprise management layer, and external network. Therefore, information security software and monitoring for industrial control systems need to consider deployment at the field device layer, field control layer, process monitoring layer, manufacturing execution system layer, and enterprise management layer. As shown in Figure 1, at the field device layer and field control layer, industrial control system suppliers need to configure corresponding information security software and monitoring for their products; at the process monitoring layer and manufacturing execution system layer, both industrial control system suppliers and information security product suppliers need to configure the appropriate information security software and monitoring for their respective products; at the enterprise management layer, information security software and monitoring are configured by enterprise management software suppliers, although for smaller enterprises, this can also be configured by network information security product suppliers.
In Figure 1, each device is considered as an endpoint, and every network must be taken into account. Therefore, information security software and monitoring for industrial control systems must consider all endpoints and all networks. Initially, information security software and monitoring for industrial control systems mainly focused on endpoints, but in recent years, software monitoring for control networks and information networks has gradually developed.
3 Analysis of Information Security Software and Monitoring for Industrial Control Systems
To facilitate the analysis of information security software and monitoring for industrial control systems, this section will provide a detailed analysis of the information security software and monitoring present in each layer, categorized by field device layer, field control layer, process monitoring layer, manufacturing execution system layer, and enterprise management layer.
3.1 Information Security Software and Monitoring for Field Device Layer
At the field device layer, some information security software configurations are required for bus-type field devices, wireless devices, and RTUs.
3.1.1 Bus-type Field Devices
For bus-type field devices, protection should be implemented at the endpoint level. Typically, this endpoint protection includes the following two aspects:
(1) Patch software for field devices;
(2) Bus access control software. (Note: Currently under development)
3.1.2 Wireless Devices
For wireless devices, protection should also be implemented at the endpoint level. Typically, this endpoint protection includes the following aspects:
(1) Patch software for wireless devices;
(2) Data transmission encryption software protocol WPA2;
(3) Software requirements for wireless communication devices.
3.1.3 RTUs
For RTUs, protection should be implemented at the endpoint level. Typically, this endpoint protection includes the following aspects:
(1) Patch software for RTUs;
(2) Software for monitoring, control, and data acquisition requirements. (Note: This is similar to the endpoint protection mentioned below)
3.2 Information Security Software and Monitoring for Field Control Layer
At the field control layer, information security software configurations are required for controllers or control stations including Data Acquisition and Monitoring Systems (SCADA), Distributed Control Systems (DCS), Safety Instrumented Systems (SIS), and Programmable Logic Controllers (PLC).
For each controller or control station, protection should be implemented at the endpoint level. Typically, this endpoint protection includes the following aspects:
(1) Patch software
Industrial control system suppliers should provide qualified relevant patches, including security patches for the operating systems used and industrial control system application software.
(2) Storm protection
For controllers and communication modules, if a network storm occurs, unsupported traffic can be filtered out to protect each control node.
3.3 Information Security Software and Monitoring for Process Monitoring Layer
At the process monitoring layer, information security software and monitoring configurations are needed for Data Acquisition and Monitoring Systems (SCADA), Distributed Control Systems (DCS), Safety Instrumented Systems (SIS), Programmable Logic Controllers (PLC), engineer stations, operator stations, OPC servers, real-time databases, and monitoring centers. This can be divided into endpoint protection and industrial safety monitoring and auditing platforms.
3.3.1 Endpoint Protection
For engineer stations, operator stations, servers, etc., protection should be implemented at the endpoint level. Typically, this endpoint protection includes the following three aspects of software:
(1) Built-in software
-
Patch and antivirus software
Industrial control system suppliers should provide qualified relevant patches, including security patches for the operating systems used and industrial control system application software, applicable to all endpoints in this layer.
Antivirus software performs regular virus scanning and removal, providing intrusion detection and prevention functions to ensure the safety of each endpoint. Common antivirus software includes McAfee, Symantec, etc.
-
Access and account management software
Access and account management typically adopts user, role, and location-based access and account management, and can also be based on object and attribute levels for access and account management.
-
Host-based firewall software
Host-based firewall technology is a software solution deployed on workstations or controllers to control traffic entering and leaving specific devices.
-
Backup and recovery software
Through effective disaster recovery, it prevents significant loss of system data and application data due to incidents. Additionally, through system management features, it allows for full backup and recovery or partial backup and recovery.
(2) Basic software
-
Audit trail software
Audit trail refers to the chronological record of system activities. This record checks the audit trail records in sequence from the beginning to the end, reviewing and verifying the environment and activities of each event. The audit trail provides evidence of activities for responsible personnel to support the realization of functions. The audit trail records system activities and user activities. System activities include activities of the operating system and application processes; user activities include activities of users in the operating system and applications. With appropriate tools and procedures, the audit trail can detect activities that violate security policies, issues affecting operational efficiency, and errors in programs.
Typically, audit logs contain information such as the time and date of operations, the nodes of operations, the usernames of operators, the types of operations, the objects and attributes affected by the operations, and other information related to the system.
-
Workstation, network, and software monitoring software
The proper functioning of workstations and network devices directly impacts the operation and reliability of the control system. By continuously monitoring these devices, abnormal behaviors can be proactively detected, optimizing system availability.
-
Mobile media and device information security software
The use of mobile media and devices directly affects system security. By scanning and monitoring these mobile media and devices, attacks on the system can be proactively prevented.
(3) Enhanced software
-
Digital signature software
The system can define certain configuration information, reports, or control applications as signed by a specific user, ensuring that this information cannot be easily modified.
-
Whitelist software
Through whitelist policies, the execution of unapproved software is blocked on both the user and server sides.
-
Advanced access control software
To facilitate subsequent maintenance support, advanced access control is provided to achieve secure remote access.
3.3.2 Industrial Control Audit and Monitoring Platform
The industrial control audit and monitoring platform is specifically designed for auditing and threat monitoring of industrial control systems. Its main functions include:
(1) Detecting network attacks against industrial control protocols, malformed messages of industrial control protocols, abnormal user operations, unauthorized device access, and the spread of malicious software such as worms and viruses, with real-time alerts.
(2) Supporting the backtracking of communication records in industrial control systems, facilitating subsequent accident investigations.
(3) Integrating with industrial control system suppliers to extract their device operation log information.
The industrial control audit and monitoring platform operates independently while sharing information with the control platform. On one hand, the monitoring audit platform provides logs and analysis data to the control platform, assisting it in better supervising the entire network system and security devices. On the other hand, the control platform also provides monitoring support for the better operation of the monitoring audit platform, ensuring stable operation and reliable data.
The industrial control audit and monitoring platform has begun to emerge and be put into use, with its typical information diagram shown in Figure 2.
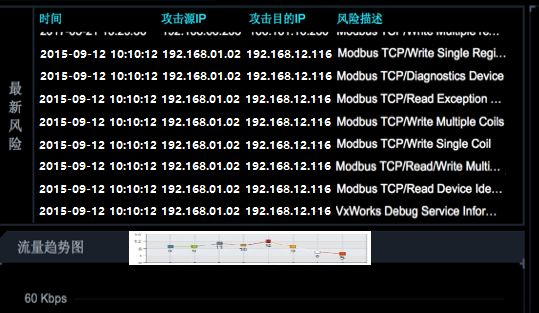
Figure 2 Typical Information Diagram of Industrial Control Audit and Monitoring Platform
3.4 Information Security Software and Monitoring for Manufacturing Execution System (MES) Layer
At the manufacturing execution system (MES) layer, information security software and monitoring configurations are needed for systems including Plant Information Management System (PIMS), Advanced Process Control (APC), historical databases, production scheduling, and warehouse management, typically divided into endpoint protection and industrial safety control platforms.
3.4.1 Endpoint Protection
For servers, protection should be implemented at the endpoint level. Typically, this endpoint protection software is similar to that mentioned in Section 3.3, and will not be elaborated further.
3.4.2 Industrial Safety Control Platform
The industrial safety control platform is a product for monitoring, configuring, and operating systems and industrial control security devices deployed in the industrial control production network and management network. Its main functions include behavior auditing, event tracking, log management, and security domain management to perceive and analyze security risk situations in the network, enhancing the predictive capability for network security events to timely curb potential threats.
Its main functions include:
(1) Unified management of security devices and information assets;
(2) Monitoring the overall network and security device situation, achieving comprehensive security awareness;
(3) Closed-loop process for event handling and control.
The industrial safety control platform has begun to emerge and be put into use, with its typical schematic diagram shown in Figure 3.
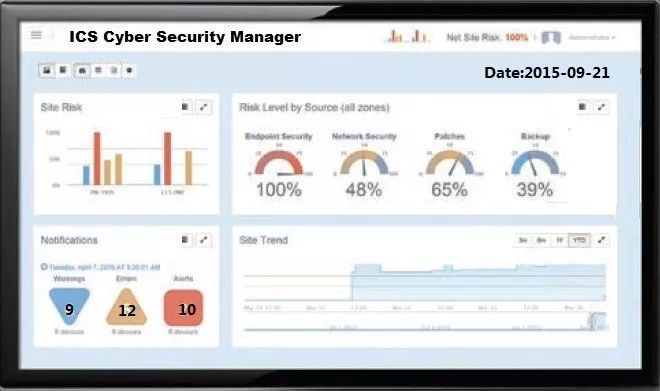
Figure 3 Schematic Diagram of an Industrial Safety Control Platform
3.5 Information Security Software and Monitoring for Enterprise Management Layer
At the enterprise management layer, information security software and monitoring configurations are needed for areas including financial management, sales management, human resources management, supply chain management, etc., all of which must be managed by the IT department. Since industrial safety control platforms cannot fully meet the information security management needs of large-scale factory-level group users, they can access the GRC enterprise management platform. Thus, the information security software and monitoring configurations at this layer can generally be divided into industrial safety control platforms and GRC enterprise management platforms.
3.5.1 Industrial Safety Control Platform
Typically, this industrial safety control platform software is the same as that mentioned in Section 3.4, and will not be further analyzed here.
3.5.2 GRC Enterprise Management Platform
The concept of GRC (Governance, Risk, and Compliance Management) has only recently emerged in China, but has developed for a considerable time abroad. Triggered by a series of negative examples such as Enron in the United States and Société Générale in France, and rooted in the Sarbanes-Oxley Act (SOX), GRC encompasses various aspects of corporate governance, risk management, and compliance operations. With the growth of enterprises, aiming for overall control and strategic execution, GRC management systems are seen as an inevitable and effective choice for enterprises to survive and thrive in an increasingly complex competitive environment, achieving corporate governance, risk avoidance, strategic performance, business process management, and compliance management including quality, safety, and environment.
The rapid growth of the Chinese economy has driven Chinese enterprises to continuously grow stronger and expand overseas. However, in the process of expansion and entering the global market, Chinese enterprises have gradually exposed numerous management issues such as low efficiency, poor performance, weak control capabilities, and lack of compliance and transparency, leading to significant losses for many enterprises. GRC is an effective management method and tool to address these issues.
(1) Complete Definition of GRC
GRC refers to a management method and toolset that is centered on strategy, based on process management, and manages and controls various business management processes to ensure the achievement of strategic and operational objectives. GRC involves the following three components:
-
Governance: Establishing a complete institutional arrangement and governance framework, treating all stakeholders fairly, formulating corporate strategic goals and policies, supervising performance, complying with laws and regulations, and transparently disclosing operational status, further managing and supervising the processes of business management itself.
-
Risk Management: Structurally identifying, assessing, mitigating, monitoring, and controlling all business and regulatory risks.
-
Compliance Management: Ensuring adherence to various systems and regulations, implementation of policies, and effective achievement of business and management objectives through internal control management mechanisms and systems.
(2) GRC Governance Model
The primary aim of GRC control is to ensure the execution of strategies based on corporate governance and control. Therefore, corporate governance is both an outcome and a means. Aligning strategic goals, focusing on business operations, emphasizing business execution and monitoring, and preventing risks and compliance while introducing performance assessment into the closed-loop of corporate control (as shown in Figure 4) ensures the effectiveness of corporate control and the sustainability of corporate governance.
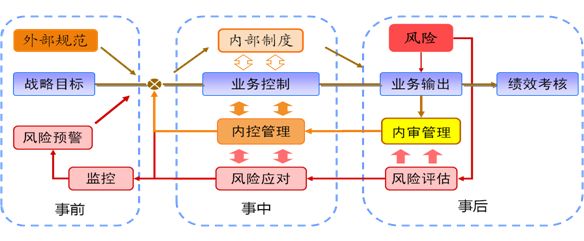
Figure 4 Corporate Control Closed-loop Model
(3) GRC and Information Security for Industrial Control Systems
For rapidly rising and developing Chinese enterprises, GRC serves as a management methodology system and toolset to improve the prominent management issues faced during the process of strengthening and expanding enterprises (such as operational performance, group control, compliance, and transparency).
GRC management software is an integrated solution that can include decision support (group control, board governance, leadership assignments, executive dashboards, office platforms, decision systems, etc.), strategic performance management (business strategy systems, comprehensive budget management, balanced scorecards, strategic monitoring, strategic reporting, performance management, human resources management, reporting management, etc.), process management (business process management, process performance, task management, collaborative management, etc.), risk management (risk management, audit management, contract management, security management, quality management, etc.), compliance management (SOX compliance, industry compliance, internal control systems, etc.), information security management (information security compliance, information security risk management, access control management, information security services, security and directory management, policy management, etc.), and presentation (portals, integration with other business systems, etc.). Typically, the integrated view of GRC is shown in Figure 5.
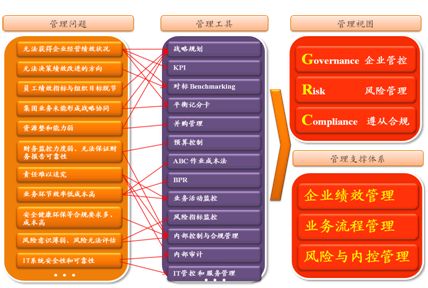
Figure 5 Integrated View of GRC
Information security for industrial control systems, as an important component of information security management, considers aspects such as defining business impacts, understanding routine and operational risks, and process handling. In the information security management module of the GRC management platform, the following solutions are provided:
-
Establishing information security policies and standards;
-
Detecting and responding to attacks;
-
Identifying and correcting information security deficiencies;
-
Conducting risk assessments and monitoring.
Through the above solutions, the goal is to reduce overall information security risks, minimize costs associated with information security incidents and compliance, and streamline the identification, measurement, and monitoring of information security processes.
Generally, the main content regarding information security management within the GRC enterprise management platform includes the following points:
-
Information security issue management;
-
Information security and policy procedure management;
-
Information security routine management;
-
Information security control assurance;
-
Information security vulnerability program;
-
Information security incident management;
-
Information security operations and compliance management;
-
Information security risk management;
-
Peripheral component interconnect (PCI) management.
The monitoring screens for information security management within the GRC enterprise management platform vary based on the user’s information security management needs. The GRC information security risk management schematic is shown in Figure 6.
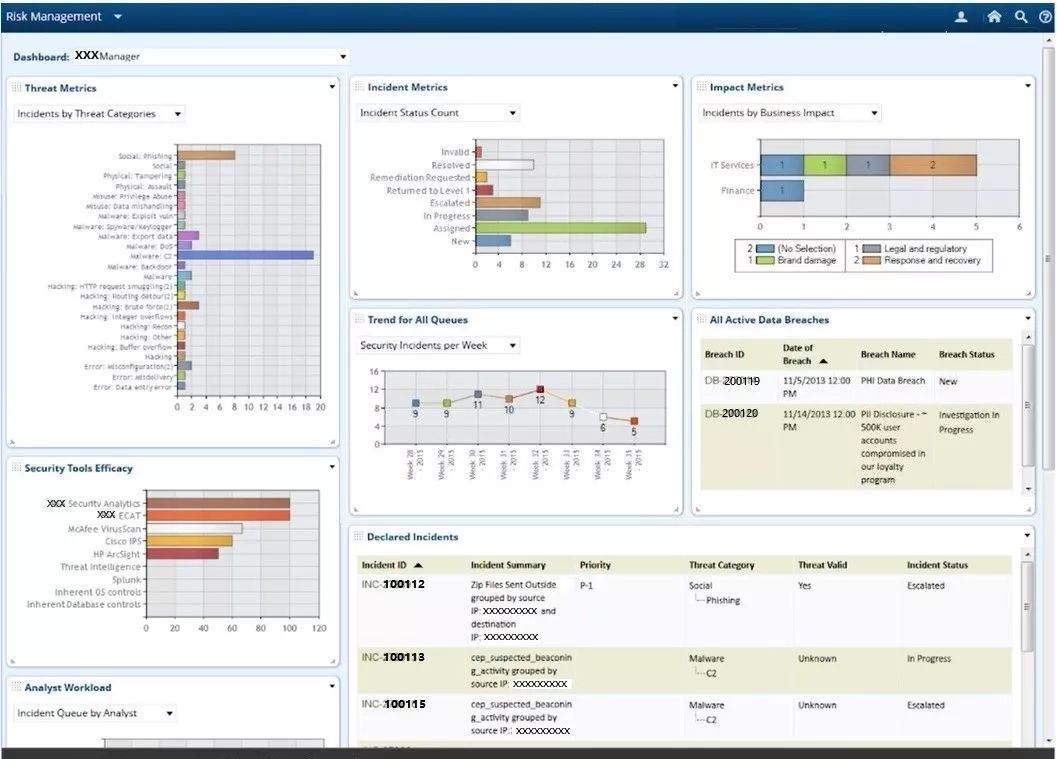
Figure 6 GRC Information Security Risk Management Schematic
(4) GRC Product Suppliers
-
Foreign GRC service providers and solutions
Leading foreign GRC market players include Axentis, BWise, MetricStream, OpenPages, Thomson Reuters, Oracle, etc. These GRC vendors enhance their GRC concepts and technology product levels through continuous updates, winning an increasingly broad market and a growing customer base. These vendors not only hold a leading position in terms of technical strength but are also shaping their roles as GRC leaders through conceptual research and strategic guidance.
Other foreign GRC market participants that have begun to challenge for leadership include Archer, Cura, Mega, Methodware, Protiviti, Strategic Thought, etc. Over the past two years, these vendors have significantly improved their GRC concepts and products, gradually providing excellent solutions and products in various fields of GRC to world-leading enterprises. Although their conceptual levels, technical platforms, and market shares have not yet reached a leadership position, they will continue to maintain a strong competitive position in the complex GRC market.
Other participants in the foreign GRC market include SAI Global, SAP, Trintech, Aline, IDS Scheer, CA, Compliance360, DoubleCheck, Neohapsis, List Group, Optial, Sword Achiever, Trintech, Xactium, etc. These vendors’ research on GRC concepts is mostly based on their existing solutions, and GRC products are limited to certain GRC areas related to their product lines. Although their solutions are currently not comprehensive and their market shares are not large, their long-term accumulated customer base and strong technical capabilities will help them grow rapidly in the GRC market.
-
Domestic GRC service providers and solutions
Research on GRC theory and practice in China is relatively late, and domestic vendors’ management experience and customer accumulation are also somewhat behind foreign ones. Therefore, domestic GRC management software providers’ GRC solutions are mostly extensions of existing solutions, with few forming comprehensive solution sets covering the GRC field. Currently, the main domestic providers of GRC services include Huadian Technology, Yonyou, Boke Information, Yanhua Yingdong, and Di Yi Huida, etc.
4 Trends in Information Security Software and Monitoring for Industrial Control Systems
Information security for industrial control systems has drawn close attention from industrial control system users. Information security software and monitoring for industrial control systems are essential components of information security. In today’s rapidly developing industrial modernization, information security software and monitoring for industrial control systems are particularly important. Industrial control system suppliers, network information security product suppliers, enterprise management software suppliers, and industrial control system users must take information security software and monitoring seriously.
From the development of the industrial control system market and the emergence of various information security software and monitoring products, it is evident that information security software and monitoring products for industrial control systems are gradually trending toward standardization, integration, and improvement.
4.1 Standardization of Information Security Software and Monitoring
The frequent occurrence of information security incidents in industrial control systems and their severe consequences have inevitably attracted high attention from governments and relevant industrial control system users. Effectively promoting information security for industrial control systems, strengthening the management of information security, and applying software and monitoring products is an inevitable trend. This will certainly impose standardization requirements on software and monitoring products.
As previously mentioned, industrial control system suppliers, information security product suppliers, and enterprise management software suppliers are all striving to develop these information security software and monitoring products. Currently, there is a wide variety of software and monitoring products in the market, and for industrial control system users, the key is how to correctly select and configure them. Therefore, more standardized requirements are needed in the market. Clearly, the standardization of information security software and monitoring products is an inevitable trend.
4.2 Integration of Information Security Software and Monitoring
Due to the diverse products and networks within industrial control systems, industrial control system suppliers develop software and monitoring for their own devices, while information security product suppliers develop software and monitoring for their network products. Therefore, the information security software and monitoring for industrial control products and network products must be well-integrated to be unified within the monitoring platform of enterprise management software suppliers. Thus, the design of information security software and monitoring for industrial control systems must be integrated.
Moreover, since information security software and monitoring are developed and designed by industrial control system suppliers, information security product suppliers, and enterprise management software suppliers, the requirement to integrate these software and monitoring together is a requirement for effective management of information security for industrial control systems, as well as a demand from industrial control system users.
4.3 Improvement of Information Security Software and Monitoring
As can be seen from the previous sections, the current information security software and monitoring for industrial control systems are still in their infancy. With the in-depth development of information security technology for industrial control systems, their software and monitoring will become more improved.
(1) More Improved Information Security Technology Software
There are many types of information security technologies for industrial control systems, and the information security technology software currently available in the market is still relatively limited. Therefore, information security software for industrial control systems will need further promotion and improvement.
(2) More Improved Information Security Monitoring Currently, the market for information security monitoring for industrial control systems is complex and requires industrial control system suppliers, network information security product suppliers, and enterprise management software suppliers to open up and ensure compatibility in design, striving to establish a unified information security monitoring system. This will save time, manpower, and material resources for industrial control system users, achieving centralized monitoring of information security for industrial control systems. Therefore, information security monitoring for industrial control systems requires collaboration among industrial control system suppliers, information security product suppliers, and enterprise management software suppliers to continuously improve.
5 Conclusion
From the analysis of information security software and monitoring for industrial control systems presented above, it is evident that information security software and monitoring have gradually formed an indispensable part of the overall deployment of information security solutions for industrial control systems. Only by earnestly and systematically learning and applying this software and monitoring can we effectively address the frequent occurrence of information security incidents in industrial control systems, ensuring the normal operation of industrial control systems and safeguarding the development of the national economy.
At the same time, we should also recognize that the deployment of information security software and monitoring for industrial control systems has just begun. With the continuous development and widespread application of industrial control systems, their information security software and monitoring will surely advance rapidly. Therefore, we should take a comprehensive approach to the information security software and monitoring for industrial control systems, actively applying and deploying them to truly enhance the construction of information security for industrial control systems.
Author: Xiao Jianrong
Source: Industrial Safety Industry Alliance

