1. Industrial control systems generally lack security design
2. Industrial control systems have numerous vulnerabilities and backdoors
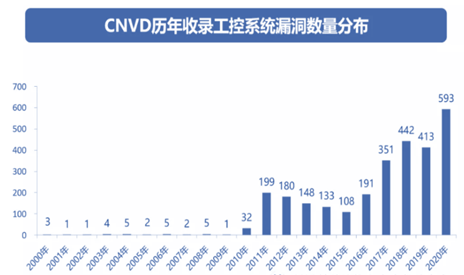
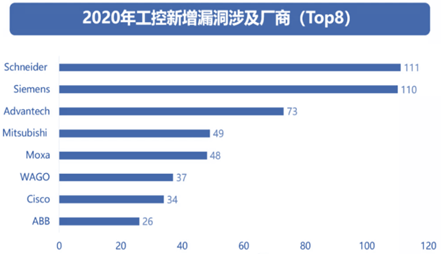
3. Chaotic device networking and lack of security protection
4. Industrial hosts running with “holes” and “diseases” has become the norm
5. Unclear industrial assets
6. Lack of necessary monitoring and early warning measures, poor visualization and readability
7. Industrial data faces security risks of theft, tampering, and loss
8. Inadequate security management systems in industrial enterprises, poor management, and unclear responsibilities
9. Inadequate security operation and maintenance management, incomplete emergency response
10. Insufficient investment in industrial control system information security, poor personnel awareness
Original source:Critical Infrastructure Security Emergency Response Center
