1 Network Security Status Analysis of Hydraulic Control Systems
The hydraulic engineering industrial control system is widely used in various aspects such as hydrological monitoring, water resource monitoring, soil and water conservation monitoring, water network scheduling, reservoir dam (gate) monitoring, hydropower monitoring, pump station water supply and drainage monitoring, and water quality monitoring. It is an important component of hydraulic engineering infrastructure. Due to the characteristics of hydraulic control systems, such as the fact that system protection and data confidentiality were not included in the safety indicators during the early design and development stages; the extensive use of TCP/IP technology in control networks; and the weak protective measures due to the connection between industrial control networks and enterprise networks, attackers can easily invade industrial control systems through the enterprise network. The current network security status is mainly reflected in the following aspects:
(1) Industrial control systems commonly adopt 20 types of industrial field bus standards provided in IEC61158, such as Modbus series, PROFIBUS series, etc. Controllers are mostly from companies like Siemens, GE, and Schneider Electric. Malicious actors can easily exploit vulnerabilities in these communication protocols and general controllers to gain control over control areas and actuators, thereby compromising the entire system.
(2) Software upgrades for hydraulic control systems are challenging. The network of industrial control systems is based on stability, and frequent software patch upgrades pose a serious threat to system stability. Upgrade failures or errors can render the entire system unusable, resulting in significant production losses.
(3) There is a lack of virus control measures. Many control devices in the hydraulic industrial control system network are closed systems and cannot be cleaned of viruses using antivirus software. Additionally, there are no effective means to control the spread of viruses in the control network. Once infected, the virus can spread throughout the industrial control network, severely impacting production.
(4) Device diversity poses challenges. The devices in the hydraulic industrial control system network are varied, each with its own characteristics, leading to uneven security levels among devices and significant difficulties in securing the industrial control system network.
In 2001, the Maroochy sewage treatment plant in Queensland, Australia experienced 46 unexplained incidents of control device malfunction due to repeated network intrusions by internal engineers, resulting in millions of liters of sewage entering the local water supply system. In 2007, attackers infiltrated a hydraulic SCADA control system in Canada, damaging the control computer system used for Sacramento River water scheduling by installing malicious software. In 2011, hackers compromised the SCADA control system, damaging the water supply pumps of a city water system in Illinois, USA. The pathways for intrusions into hydraulic industrial control systems primarily involve attacks through enterprise wide area networks and commercial networks, exploiting vulnerabilities in general devices such as IEDs, PLCs, RTUs, controllers, and communication processors to implant malicious code and conduct destructive activities, causing significant losses to hydraulic engineering.
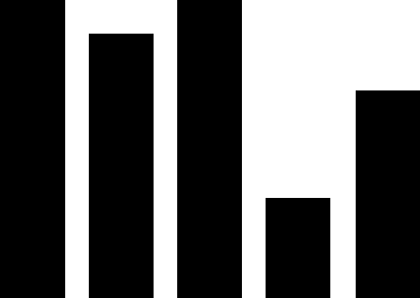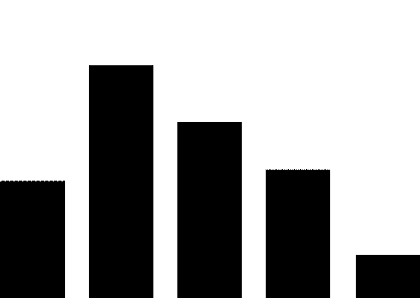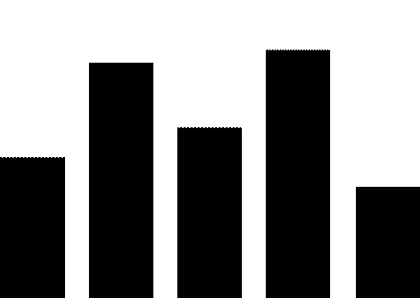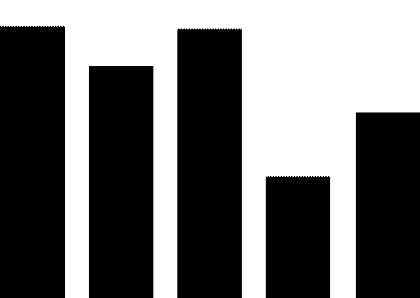
2 Vulnerability Analysis of Hydraulic Control Systems
2.1 Types of Vulnerabilities
(1) Communication protocol vulnerabilities. The integration of industrial and enterprise networks and the development of the Internet of Things have led to the widespread use of general protocols like TCP/IP and OPC in industrial control systems, which in turn has highlighted communication protocol vulnerabilities. For instance, the OPC Classic protocol (OPC DA, OPC HAD, and OPC A&E) is based on Microsoft’s DCOM protocol, which was designed before network security issues were widely recognized and is therefore highly susceptible to attacks. Additionally, OPC communication employs non-fixed port numbers, making it nearly impossible to use traditional IT firewalls to ensure security.
(2) Operating system vulnerabilities. Currently, most industrial control system engineering stations/operating stations operate on Windows platforms. To maintain relative independence of process control systems and ensure stable operation, on-site engineers typically do not install any patches after system startup. However, the issue is that without installing patches, the system remains vulnerable to attacks, creating security risks.
(3) Vulnerabilities in security policies and management processes. Sacrificing security for availability is a common phenomenon in many industrial control systems. The lack of complete and effective security policies and management processes also poses a certain threat to industrial control system network security. For example, the abuse of mobile storage media and lax access control policies in industrial control systems.
(4) Industrial virus protection vulnerabilities. To ensure the availability of industrial control application software, many hydraulic industrial control system operating stations typically do not install antivirus software. Even if antivirus software is installed, it has significant limitations during use, as virus definitions need to be updated regularly, a requirement that is particularly unsuitable for industrial control environments.
(5) Application software vulnerabilities. Due to the diversity of application software, it is difficult to establish unified protective standards to address security issues. Moreover, when application software is networked, its application ports must be opened. Therefore, conventional IT firewalls and other security devices find it challenging to guarantee security.
(6) Multiple network port access. Many network incidents stem from inadequate protection of multiple network port access points, including USB keys, maintenance connections, and laptops.
(7) Inadequate network segmentation design. Many control networks in practical applications are “open,” with no effective isolation between different subsystems, especially in industrial control networks based on OPC and Modbus communications, allowing security failures to spread rapidly through the network.
2.2 Common Vulnerability Analysis
The hydraulic engineering production process uses various industrial control systems, such as PLC systems for controlling pump stations and sluices, remote monitoring SCADA systems, comprehensive automation systems for power substations, PLC systems for controlling hydropower generating units in rural hydropower plants, and centralized control systems.
(1) PLC security vulnerabilities. The most widely used automation control systems in hydraulic engineering are PLC systems. These systems are mostly supplied by foreign vendors, including Siemens, Schneider Electric, GE, Omron, and Mitsubishi Electric Automation. For example, Schneider Electric products used in the Xiaolangdi and Wanjiazai hydraulic hubs are from major global PLC suppliers, and various security vulnerabilities exist in their PLC products. As shown in Figure 1, the exposure of PLC vulnerabilities from Siemens, Schneider Electric, and GE was revealed during cybersecurity inspections conducted by the Ministry of Public Security from 2011 to 2013.
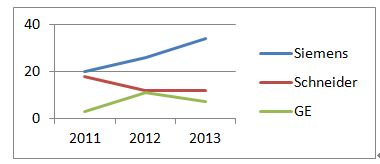
Figure 1 PLC Vulnerability Exposure
PLC vulnerabilities mainly include four categories: denial of service vulnerabilities, remote code execution vulnerabilities, user access permission vulnerabilities, and information leakage vulnerabilities. Denial of service vulnerabilities, such as Siemens Simatic S7-1200 denial of service vulnerabilities and Schneider Electric M340 PLC module denial of service vulnerabilities; remote code execution vulnerabilities, such as Siemens Simatic S7-1500 having an unknown cross-site request forgery vulnerability, and multiple Schneider Electric products having cross-site request forgery vulnerabilities; user access permission vulnerabilities, such as Siemens Simatic S7 PLC system password leakage vulnerabilities and multiple Schneider Electric products having improper verification vulnerabilities; information leakage vulnerabilities, such as Siemens Simatic S7-1200 information leakage vulnerabilities and S7-1500 insufficient entropy vulnerabilities. These vulnerabilities can be exploited, resulting in service interruptions, unauthorized operations, and information leakage.
(2) SCADA security vulnerabilities. Hydraulic engineering also extensively uses centralized control/SCADA systems based on wired or wireless communication, which have numerous security vulnerabilities in remote communication and monitoring hosts, such as Modbus/TCP authentication absence vulnerabilities, OPC remote procedure call vulnerabilities, and difficulties in dynamic port protection, as well as arbitrary code execution and denial of service vulnerabilities based on heap buffer overflow in KingView 6.53.2010.18018.
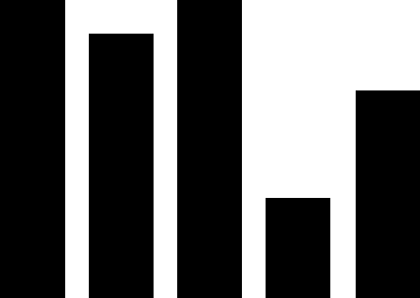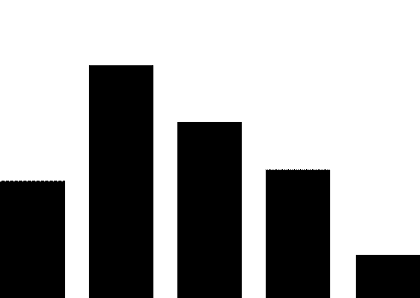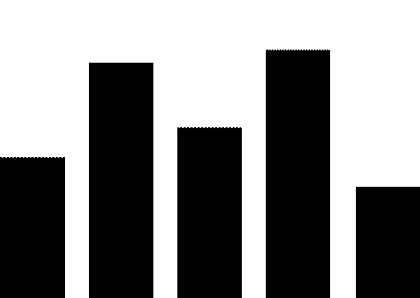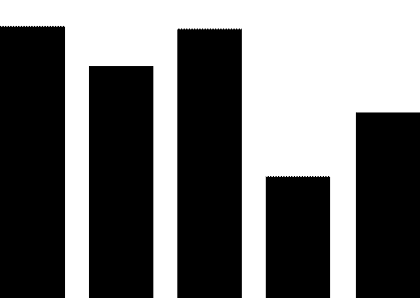
3 Risk Analysis of Network Security for Hydraulic Control Systems
3.1 Network Boundary Protection Security Issues
Besides lateral isolation and vertical encryption devices, other protective measures are inadequate. Some units have deployed traditional firewalls between production control zones, but these cannot identify proprietary industrial control protocols and cannot provide clear access allow/deny capabilities.
3.2 Host and Server Security Issues
Using traditional network antivirus software (some hosts cannot even install antivirus software), malicious code libraries cannot be updated in a timely manner, and there is a high risk of killing control programs; hosts and servers use general operating systems, and vulnerabilities in the operating system directly affect the secure operation of the system; there is no ability to detect the integrity of important programs, and once integrity is compromised, there is no recovery capability; effective technical measures to cut off the spread and destruction paths of viruses and Trojans are lacking, such as running illegal processes, opening illegal network ports, and connecting illegal USB devices.
3.3 Traffic Behavior Security Issues
Lack of capability to inspect, locate, and block unauthorized devices connecting to the internal network; inability to effectively detect network attack behaviors and record information such as attack source IP and attack type; failure to detect and alert malicious code at the network boundary, with untimely updates to malicious code libraries; lack of effective security auditing functions.
3.4 Management and Operation Security Issues
No dedicated information security positions are established, and information security management and maintenance are conducted by business departments according to their own understanding, while security regulations are incomplete. In daily operation and maintenance, there are common issues such as ineffective management and protection of media, leading to risks of virus invasion and sensitive information leakage. Emergency response plans for security protection are insufficiently comprehensive, incomplete, and lack operability, with inadequate drills and training, making it impossible to respond and restore systems promptly during actual incidents.
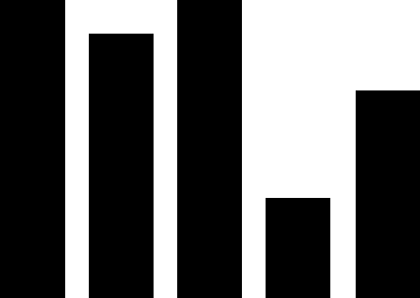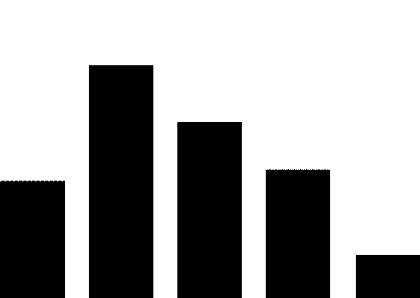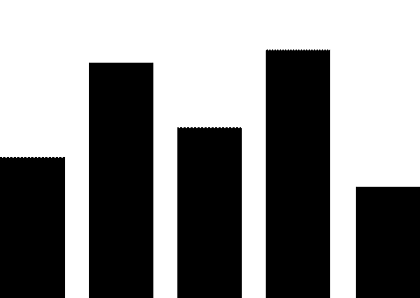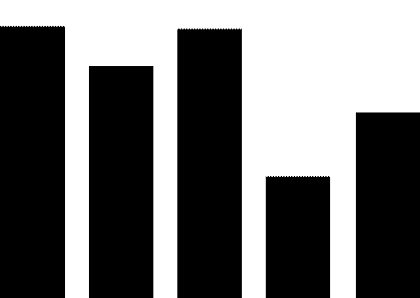
4 Thoughts on Network Security Protection for Hydraulic Control Systems
4.1 Protection Concept
Based on the current development situation in the field of industrial control network security both domestically and internationally, a “trinity” industrial control security protection strategy as shown in Figure 2 is adopted, focusing on “risk assessment, security protection, and emergency response” to build a comprehensive lifecycle security protection system for hydraulic industrial control systems, ensuring the network security of hydraulic enterprises.
(1) Risk Assessment. Through risk assessment, understand the threat status, vulnerability situation, compliance requirements, and severity faced by hydraulic industrial control assets; comprehensively grasp the security status of hydraulic industrial control systems, providing important basis for strengthening risk management and security protection construction.
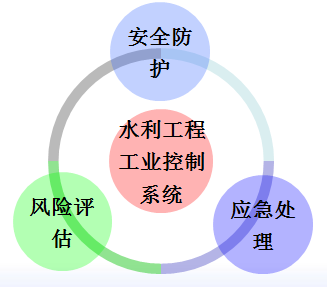
Figure 2 Security Protection Strategy for Hydraulic Control Systems
(2) Security Protection. Reasonably divide network areas and layers according to business and process requirements, clarify network boundaries, and set reasonable access rules; monitor the process status of industrial control hosts in real-time, comprehensively protect resource usage, and prohibit the operation of illegal processes; conduct real-time monitoring and alerts for network traffic, network data, and events; employ blacklist intrusion prevention and whitelist proactive defense to block or alert abnormal data and behavior.
(3) Emergency Response. Establish and improve the responsibility system for industrial control security emergency work, strengthen the monitoring of safety risks in hydraulic industrial control systems, develop emergency plans for security incidents in hydraulic industrial control systems, implement human, financial, and material security measures, and regularly organize emergency drills to minimize losses when security incidents occur in industrial control networks.
4.2 Protection Work
(1) Work Process (as shown in Figure 3).
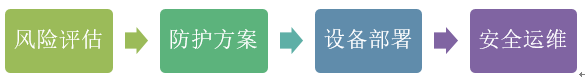
Figure 3 Work Process
Through risk assessment, identify the security risks in the network architecture, device entities, and network monitoring and auditing of hydraulic engineering industrial control systems; develop a network security protection plan for hydraulic industrial control systems based on the network structure, and deploy relevant network security devices; construct a security operation and maintenance system for the entire lifecycle of hydraulic industrial control systems.
(2) Risk Assessment. Conduct risk assessment, vulnerability analysis, and security analysis of hydraulic industrial control systems to accurately and timely understand the security status of industrial control systems. Based on the risk assessment, list the non-compliant security requirements, clarify the risks of those requirements, and provide a basis for current operation maintenance and future rectification work. Specifically, identify security risks and hidden dangers related to network security in various aspects such as operating systems, application software, network structures, and antivirus solutions in hydraulic production systems; assess the safety management systems, emergency mechanisms, and operational processes in hydraulic production systems, and provide feasible suggestions.
(3) Protection Plans and Device Deployment. Taking the network security protection of the reservoir dam safety monitoring system as an example, the protection plan and device deployment are shown in Figure 4.
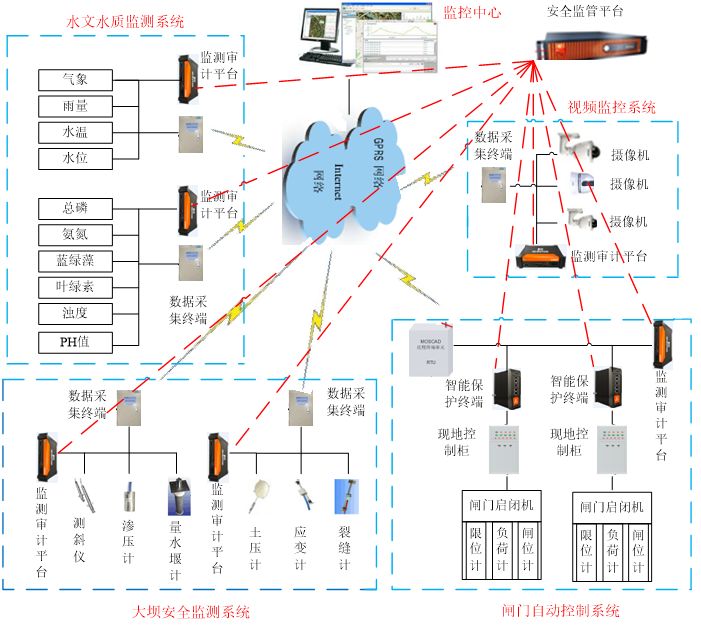
Figure 4 Network Security Protection Plan and Device Deployment for Reservoir Dam Safety Monitoring System
Host protection involves deploying industrial control guardians at the main control layer’s engineering stations, operator stations, and OPC servers, utilizing whitelist strategies for applications, networks, and USB mobile storage to prevent user violations and errors, blocking the misuse of unknown programs, mobile storage devices, and network communications, effectively enhancing the overall “immune” capability of the system network.
Key node protection involves using intelligent protection terminals to provide security for the RTUs in the reservoir dam safety monitoring system’s field control layer, effectively identifying and intercepting attack behaviors that exploit publicly disclosed RTU vulnerabilities and traffic information, allowing compliant operation traffic from trusted upper-level machines while employing dynamic learning and adaptive protection strategies to achieve protective effects on RTUs.
Network monitoring and auditing involve deploying monitoring and auditing platforms at the monitoring layer, communication layer, and bypassing layers of the reservoir dam safety monitoring system to effectively monitor network communication traffic and threat detection, alerting and auditing for illegal data collection, malicious attacks, data tampering, and unauthorized operations directed at the internal network, providing clues and event restoration functions for network security managers, and enabling real-time alerts for unauthorized manipulation and network attack behaviors.
Centralized security supervision involves deploying network security devices in the reservoir dam safety monitoring system to achieve unified security supervision and operation maintenance through a security supervision platform, which can collect and analyze threat intelligence information from on-site security devices in real-time, implementing global situational security alerts and dynamic adaptive strategies based on security analysis models, helping operation and maintenance personnel to timely discover on-site security alert information and facilitating prompt security protection responses.
(4) Safe Operation and Maintenance
Establish a security operation and maintenance monitoring center to reasonably deploy and monitor based on key business points, focusing on the availability and continuity of business systems, using key performance indicators to guide and assess the implementation and execution of industrial control system operation quality and maintenance management, and quickly and accurately locating and displaying various incidents, comprehensively presenting early warning and alert events occurring in the control system, helping operation and maintenance management personnel quickly locate and troubleshoot issues.
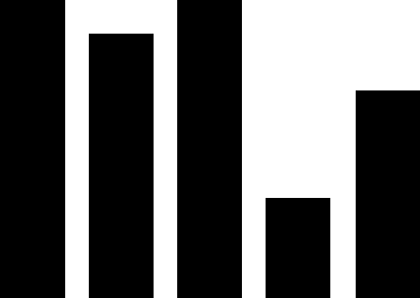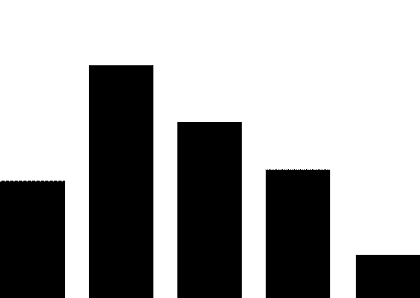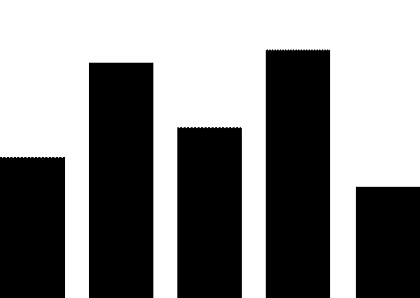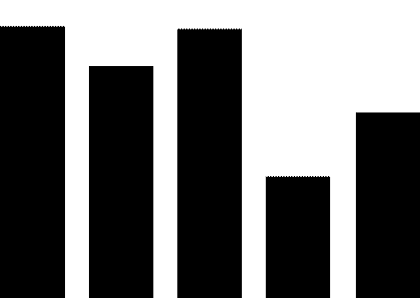
5 Conclusion and Recommendations
Industrial control network security protection requires a solution that covers the entire lifecycle of control systems. This includes tools for industrial control devices that cover major industrial control protocols, rich detection methods, and support for detecting unknown protocols; an industrial-grade network-wide security monitoring protection system that features automatic learning, automatic adaptation, and automatic generation of defense strategies; and a comprehensive safety database covering security vulnerabilities of major global manufacturers such as Siemens and Schneider Electric (including device vulnerability databases, network model libraries, and device risk statistics). Additionally, comprehensive security services must be provided to infrastructure enterprises, including vulnerability mining, penetration testing, security policies, and technical training.
(1) Conduct risk assessment work for hydraulic industrial control systems.
Use a combination of manual analysis and professional detection tools to analyze threats, assets, traffic, etc., clearly defining the security risks of each network; employ professional vulnerability mining detection tools to conduct comprehensive vulnerability mining and detection on PLCs, industrial firewalls, gateways, etc., in hydraulic engineering industrial control systems to identify vulnerabilities and defects; verify the effectiveness of security measures for Web portals and their ability to resist attacks; detect security risks present in key business systems and important office terminals; and conduct security management inspections on management organization settings, management system development, system operation and maintenance management systems, and personnel security awareness and knowledge training.
(2) Conduct network security training work for hydraulic industrial control systems.
Enhance the security assurance level of hydraulic industrial control systems through technical training, strengthen personnel’s systematic understanding of industrial control network security, improve technical personnel’s expertise and knowledge, and enhance the ability of hydraulic industrial control systems to withstand network security incidents, thereby reducing network security risks.
(3) Develop network security standards for hydraulic industrial control systems.
Based on the characteristics of hydraulic engineering industrial control systems, establish relevant standards and specifications for network security detection procedures, safety risk assessment procedures, and safety protection regulations for hydraulic engineering industrial control systems, guiding the construction and secure operation and maintenance of hydraulic industrial control systems.
Funding Project: Technical Promotion Project of the Ministry of Water Resources (SF-PX-201810).
Author Biography
Guo Jiang (1965-), male, from Tianjin, professor-level senior engineer, master’s degree, currently serves as the deputy director and chief engineer of the Tianjin Electromechanical Institute of the China Institute of Water Resources and Hydropower Research, president of the “Hydropower Station Mechanical and Electrical Technology” magazine, and director of the Industrial Control Network Security Evaluation Center of the Ministry of Water Resources, engaged in research on basic automation and industrial control system network security in hydraulic engineering.
Zhang Zhihua (1979-), male, from Tianjin, senior engineer, master’s degree, currently serves as the deputy director of the Industrial Control Network Security Evaluation Center of the Tianjin Electromechanical Institute of the China Institute of Water Resources and Hydropower Research, engaged in research, assessment, testing, and overall solution design for network security of hydraulic industrial control systems.
• end •

Authors: Guo Jiang, Zhang Zhihua
Source: Industrial Safety Industry Alliance
