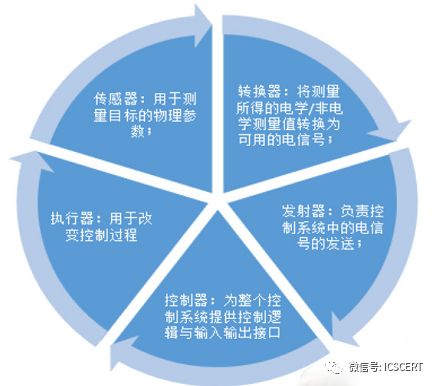
1. Industrial Control System refers to ICS (also known as Industrial Automation and Control System), which is an automatic control system composed of computer equipment and industrial process control components. The International Society of Automation (ISA) and IEC/TC65/WG released IEC 62443 “Industrial Process Measurement, Control and Automation Network and System Information Security” after integration, which provides a more detailed definition of industrial control systems: Industrial control systems include systems for automating or remotely controlling manufacturing and processing plants and facilities, building environmental control systems, and public utility facilities with geographically decentralized operations (such as electricity and natural gas), oil production, and pipelines. Classic industrial control systems typically have four functions: measurement, comparison, calculation, and correction, achieved through five components: sensors, converters, transmitters, controllers, and actuators.
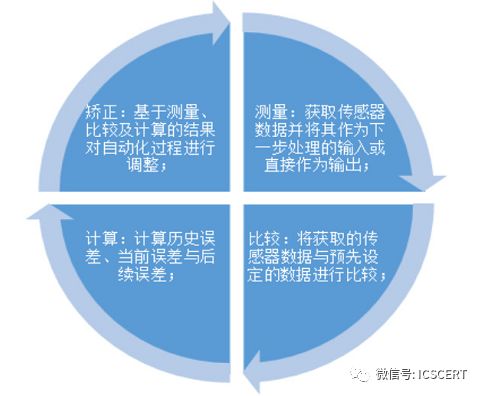
Figure 1: Four Functions of Classic Industrial Control Systems
Industrial control systems have a complex hierarchy, including the field device layer, field control layer, process monitoring layer, MES layer, enterprise management layer, and external network layer from bottom to top, achieving intelligent management operations of factory equipment through coordination of various levels. These complex levels can be divided into three business areas: Business Area One consists of actual industrial control system assets, including physical assets, digital assets, logical assets, and human assets; Business Area Two consists of customized equipment systems, which are the core system facilities for industrial control, including SCADA systems, DCS systems, and PLC systems; Business Area Three is the upper IT business area, which, in addition to general business operations, is generally connected to other business areas for better statistics and monitoring.
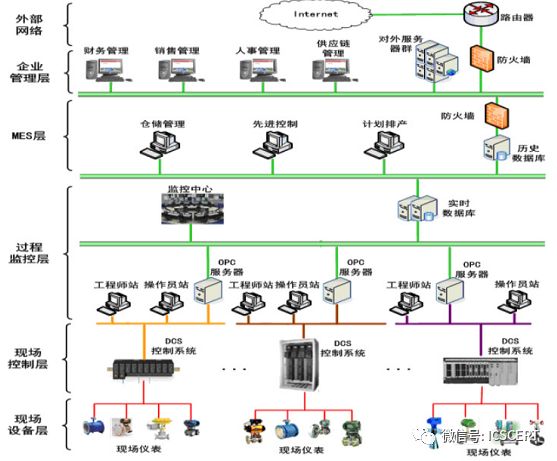
Figure 3: Hierarchical Diagram of Industrial Control Systems
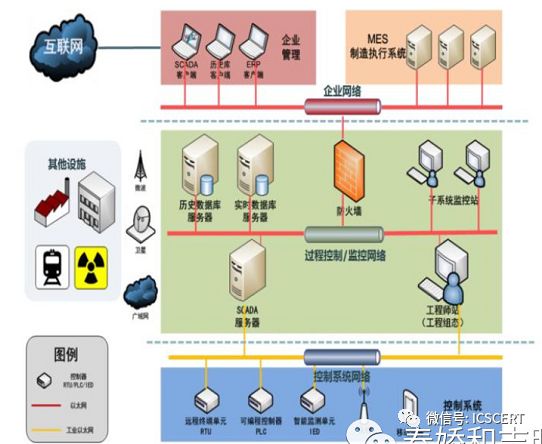
Figure 4: Three Business Areas of Industrial Control Systems
Industrial control systems are widely used in industries such as energy, transportation, water conservancy, and municipal services, with key areas including many fields closely related to international livelihoods. For example: nuclear facilities, steel, non-ferrous metals, chemicals, petroleum and petrochemicals, electricity, natural gas, advanced manufacturing, water conservancy hubs, environmental protection, railways, urban rail transit, civil aviation, urban water supply, gas supply, and heating.

Figure 5: Subfields of Industrial Control Systems
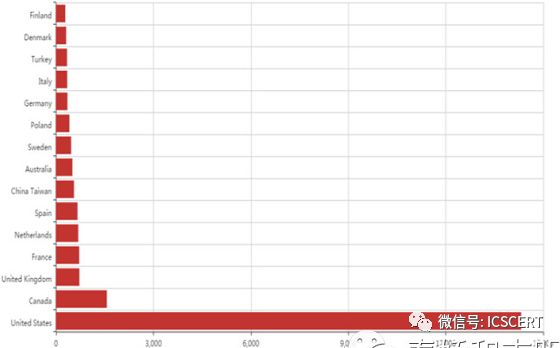
The distribution of industrial control systems is positively correlated with the level of industrial development. The United States has the largest number of industrial control systems, followed by Canada, while EU member states are also among the top in the world, with relatively fewer in Russia, Africa, and some South American countries.
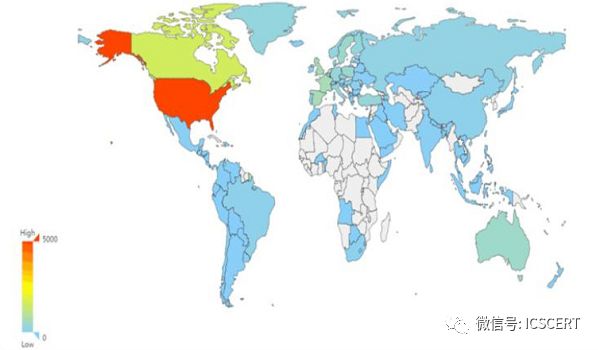
Figure 6: Global Distribution of Industrial Control Systems
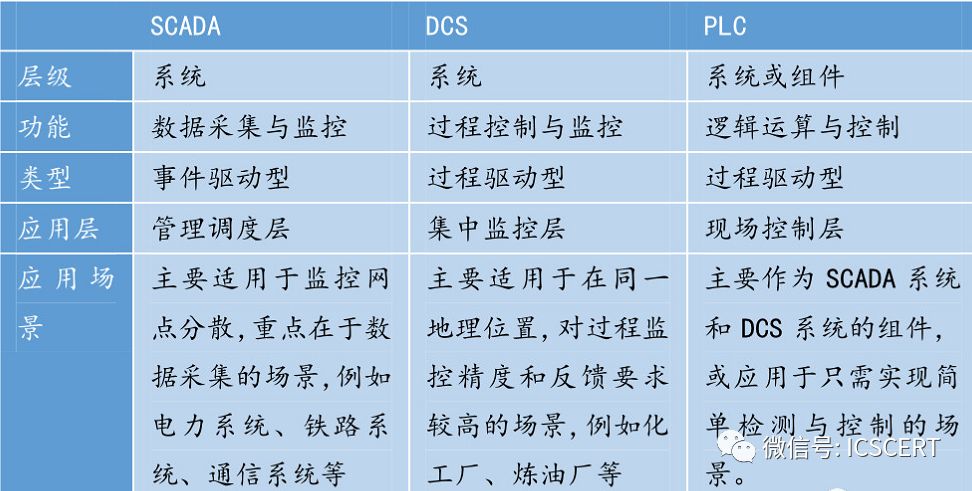
2. Industrial control systems are divided into three main categories: SCADA (Supervisory Control and Data Acquisition), DCS (Distributed Control System), and PLC (Programmable Logic Controller), which consist of various automatic control components and real-time data collection and monitoring process components, including remote terminal units, intelligent electronic devices, and communication components for component communication. The differences between various industrial control systems are analyzed in the following table:
3. SCADA is the abbreviation for Supervisory Control And Data Acquisition System, suitable for monitoring data collection, monitoring, and control over distributed points that are far apart. SCADA systems can achieve functions such as graphical user interface visualization, dynamic simulation of system status, real-time and historical data trend curve display, alarm processing, data acquisition and recording, report output, etc.
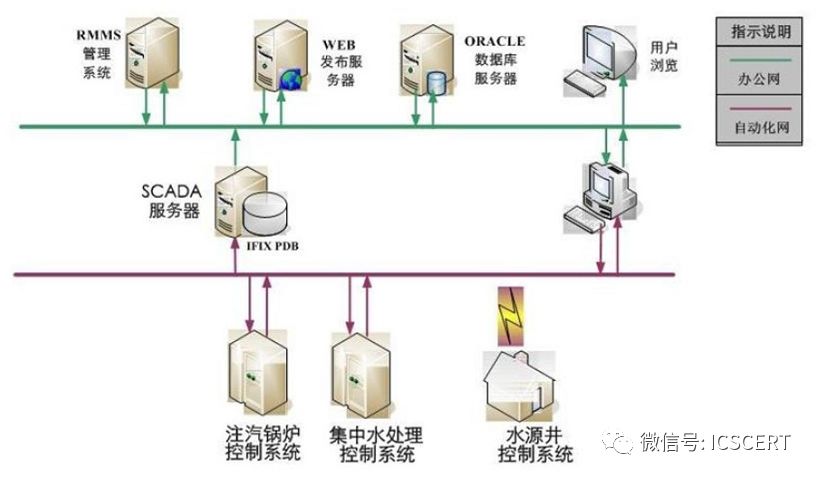
Figure 9: SCADA System Structure Diagram (Example of Oil Field Gas Supply Station)
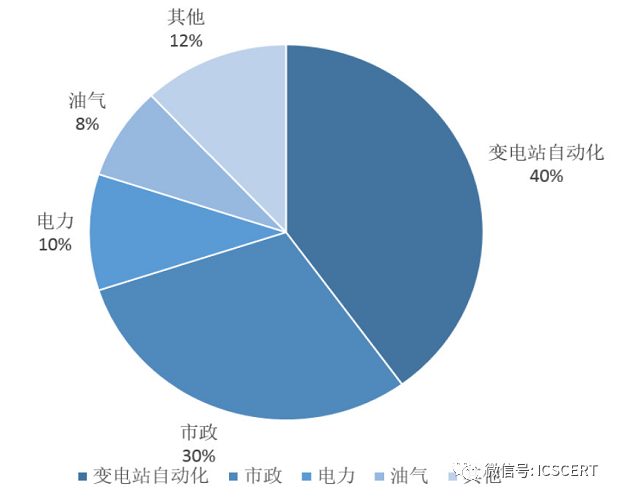
SCADA systems are widely used in substation automation, electricity, oil and gas pipelines, municipal services, water conservancy, transportation, and other fields. According to data from the Industrial Control Network, the current SCADA market size in China is approximately 10 billion yuan, with an overall market growth rate of about 10-15% in the next few years. Among them, municipal and distribution network automation may become the fastest-growing industry fields for SCADA. Currently, the main application fields of SCADA systems are substations and their automation, followed by municipal and electricity.
4. DCS is the abbreviation for Distributed Control System, which is a multi-level computer system composed of process control level and process monitoring level, linked by a communication network, integrating computer, communication, display, and control technologies (4C). DCS is inclined towards process control, coordinating local controllers to execute the entire production process through centralized monitoring. DCS typically controls numerous control points in a production process by connecting several controllers (process stations) through a network for data exchange. It uses computer operation stations to connect to controllers via networks, collect data, and convey operational instructions. DCS systems modularize the production system to reduce the impact of single faults on the entire system.
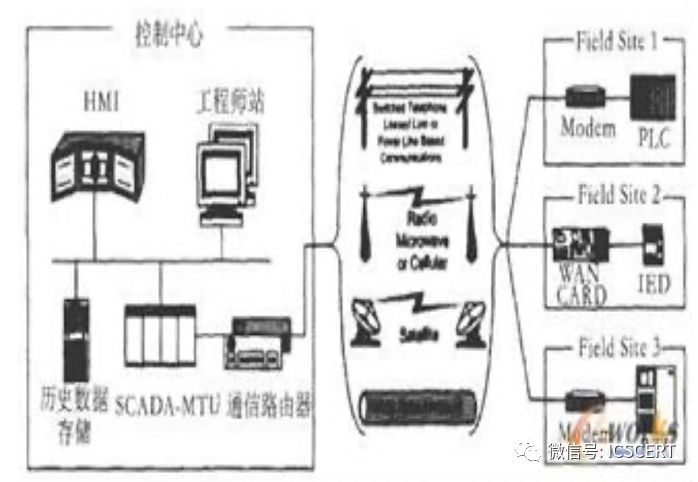
Figure 11: Main Components and Conventional Configuration of DCS Systems
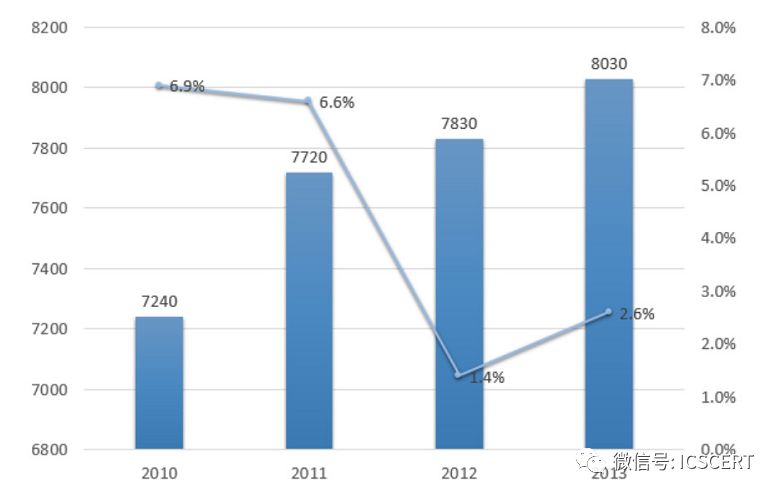
According to predictions from the Industrial Control Network, the domestic DCS market growth rate was over 6% in both 2010 and 2011, but slowed down after 2012, with a market size of approximately 8 billion yuan in 2013. Starting in the second half of 2013, the domestic wind power new projects gradually opened up, nuclear power project approvals progressed steadily, and the overall price of DCS decreased, it is expected that by 2018, the growth rate of the Chinese DCS market will continue to maintain around 5%.
DCS is mainly used in industrial control production systems located in the same geographical area, such as refineries, water and wastewater treatment, power generation equipment, chemical production bases, processing facilities, and the pharmaceutical industry. In the DCS application industry landscape, chemicals, electricity, and petrochemicals remain the top three, accounting for more than 70% of the overall market share.
In 2014, the leading market share among DCS suppliers in China was held by Zhejiang Zhongkong, with a market share of 13%, followed by Emerson Electric (12%), Schneider Electric (11%), and Honeywell (11%).
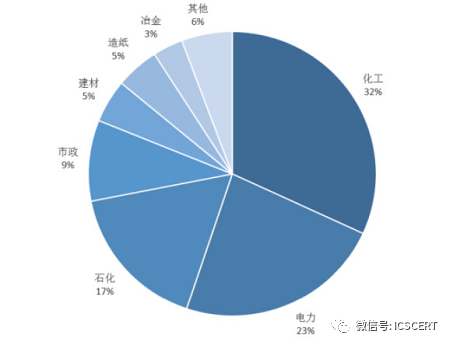
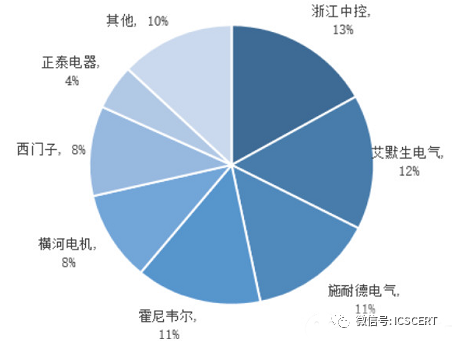
Figure 14: Market Share of DCS Suppliers in China in 2014
5. PLC (Programmable Logic Controllers) is a digital operational electronic device designed specifically for application in industrial environments, using programmable memory to store instructions for executing logical operations, sequential operations, timing, counting, and arithmetic operations, and controlling various types of machinery or production processes through digital or analog inputs and outputs. Distributed PLC control stations and intelligent I/O (Input/Output) components can directly perform automatic monitoring, automatic adjustment, sequential control, and self-protection operations on industrial production processes.
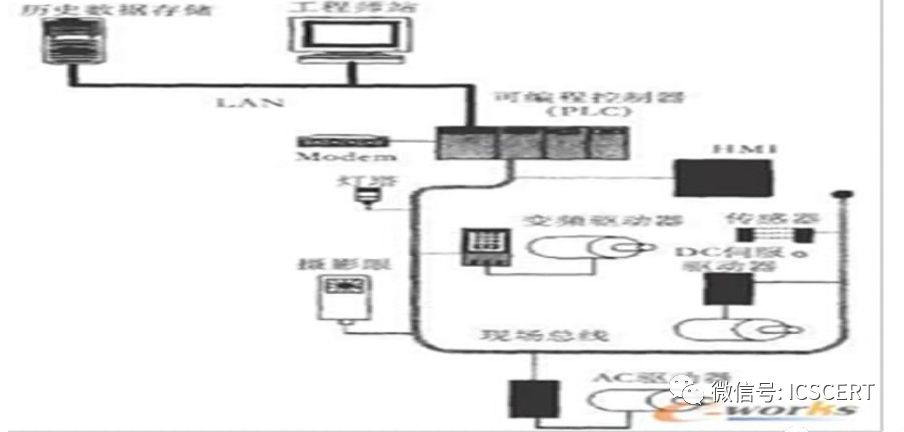
Figure 15: Main Components and Conventional Configuration of PLC Systems
According to data from the China Industry Information Network, the sales of PLCs in 2013 amounted to 7.8 billion yuan, a slight increase of 2.6% year-on-year, with the OEM market growing by 3.3%. In 2014, the domestic PLC market size was 7.62 billion yuan, a slight year-on-year decline of 2.3%, and it is expected to maintain a stable growth of 2%-3% over the next five years.
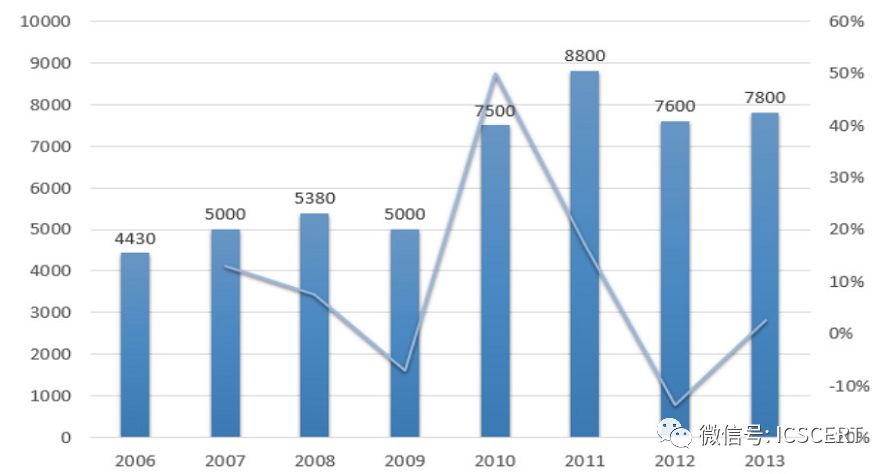
Figure 16: PLC Market Size in China (in millions) and Growth Rate
6. In the IEC 62443 standard, the definition of industrial control security is: a. Measures taken to protect the system; b. The state of the system obtained from the measures taken to establish and maintain the system; c. The ability to prevent unauthorized access and accidental changes, damage, or loss of system resources; d. Based on the capabilities of computer systems, ensuring the legitimate operating permissions of authorized personnel and systems, preventing unauthorized personnel and systems from modifying software and its data or accessing system functions; e. Preventing illegal and harmful intrusions into industrial control systems or interference with their normal operation.
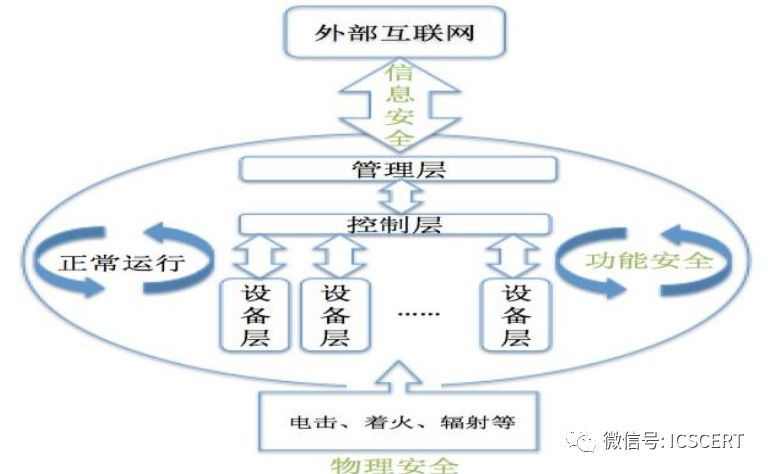
7. The security of industrial control systems can typically be divided into three categories: functional safety, physical safety, and information security. Functional safety is aimed at achieving safety functions for devices and plants; physical safety reduces hazards caused by electric shock, fire, mechanical hazards, radiation, chemical hazards, etc.; information security maintains the confidentiality, integrity, and availability of information, as well as authenticity, verifiability, non-repudiation, and reliability.

Figure 18: Comparison of Industrial Control Systems and IT Information Systems
There are essential differences in security protection between industrial control systems and IT information systems. IT information systems focus more on information security, while industrial control systems generally pay more attention to physical safety and functional safety, especially functional safety, where the safe operation of the system is the responsibility of the relevant production departments, and the information department is only in a subordinate position. In the three attributes of information security (confidentiality, integrity, availability), the priority order for IT information systems is confidentiality, integrity, availability, while for industrial control systems it is availability, integrity, confidentiality. With the close integration of information technology and industrial technology, as well as the influence of potential cyber warfare threats, industrial control systems will also shift from traditional modes to a greater focus on information security.
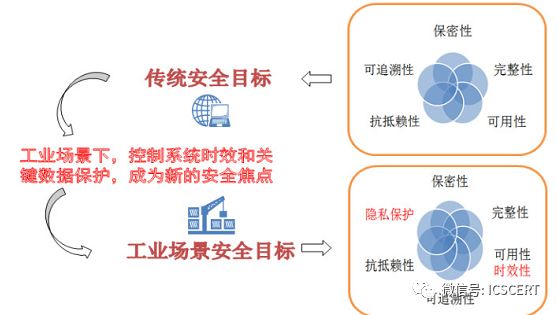
Figure 19: Differences in Goals Between Industrial Control Systems and IT Information Systems
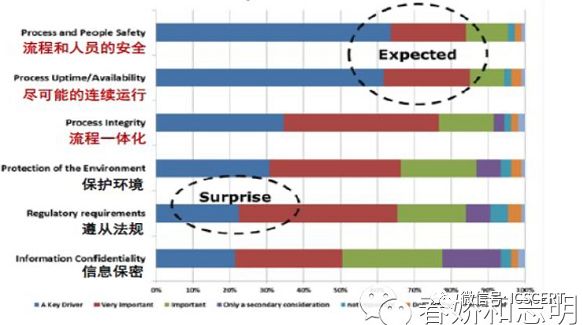
In summary, industrial control security refers to a series of protective strategies and measures for functional safety and information security in the industrial field, in addition to physical safety. The problems to be solved include ensuring the reasonable operation of the industrial control system network through measures against attacks, tampering, viruses, paralysis, and theft of secrets, to achieve the goal of ensuring the safety of industrial production.
8. Analogous to the six aspects of vulnerability defined in information security management theory, we also explain the vulnerabilities of industrial control systems in detail from six dimensions: environment, hardware, software, network, communication, and management.
(1) Physical Environment: Damage caused by fire, smoke, dust, flooding, earthquakes, social unrest, and other forms of natural or man-made disasters; security threats from adjacent areas, such as roof leaks or basement floor seepage, explosions on the street or in operational areas; physical location of equipment, environmental safety, etc.
(2) Hardware
Hardware resources include IEDs, network cables, hosts, routers, gateways, chips, I/O components, CNC machines, instruments, and actuators. These equipment assets are at risk of loss, damage, or theft. Most control devices such as PLCs, terminals, and RTUs currently use foreign control components, lacking autonomous control, which introduces logic bombs and backdoors on one hand, and on the other hand, the security protection capability of on-site control devices is weak, making it possible to obtain configuration files and crack passwords using conventional means.
(3) System Software
The vulnerabilities of industrial control system software mainly involve design flaws, inability to upgrade patches, incorrect input validation, password management, unauthorized access, inadequate authentication, and system configuration.
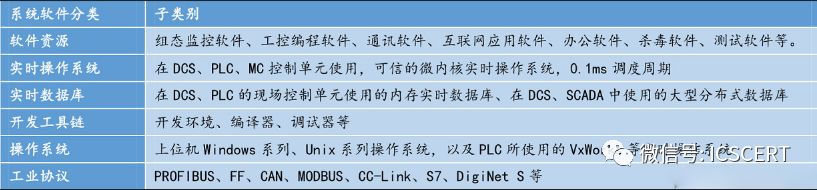
Figure 21: Classification of Industrial Control System Software
a. Design Flaws in the System. Currently, a large number of standard information network technologies or products are used in the field control devices, process control automation software, engineer stations, OPC interface machines, etc. These technologies and products have not been specifically optimized and designed for the application environment of industrial control systems, leading to the introduction of redundant functions and configurations into industrial control systems.
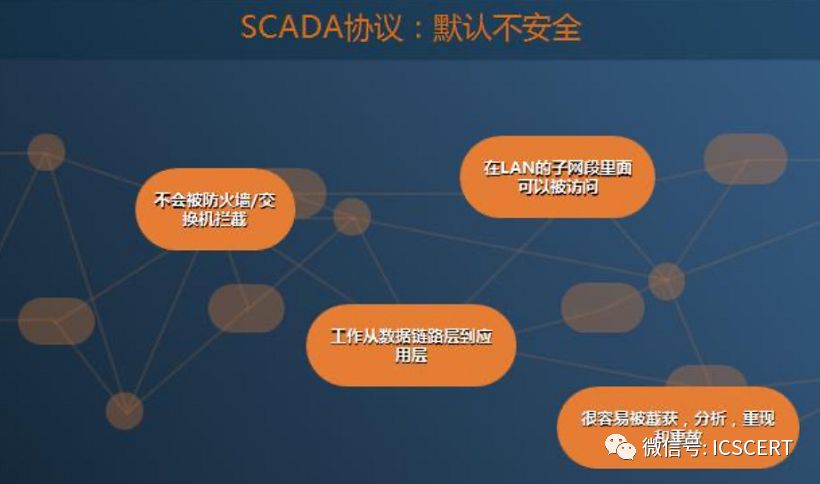
Figure 22: Inherent Vulnerabilities of SCADA
b. Lack of Virus Protection Measures in Operating Systems. Industrial control system engineer stations, operator stations, and OPC interface computers mostly use Windows systems, which have long been unable to upgrade patches and lack corresponding virus protection measures. Since operator station computers can directly issue production instructions to the industrial control system and monitor the status of production equipment, the system has numerous security vulnerabilities that greatly increase the risk of being attacked. Most vulnerabilities have existed in industrial control systems for over three years, and many have been present in open-source hacking tools for about a year.
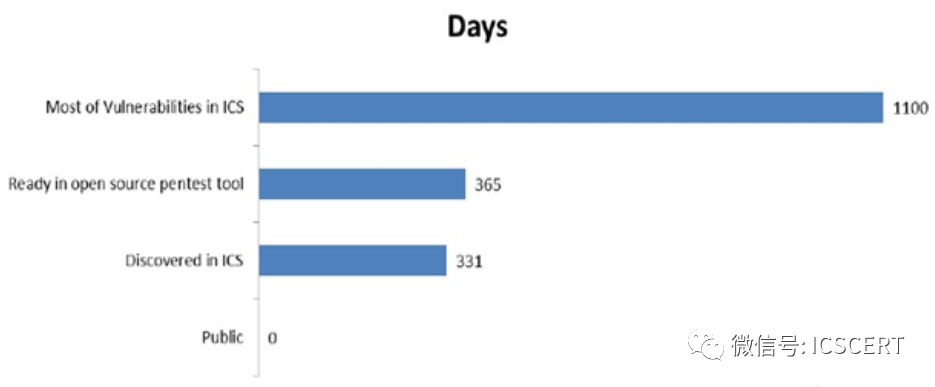
Figure 23: Duration of Vulnerabilities in ICS
c. Protocol Security Issues. The original design of the Internet only considered whether localized faults would affect the transmission of information, so protocols like TCP/IP basically did not consider security issues, and dedicated protocols for industrial control devices also have this problem.
d. Inadequate Login Authentication Mechanisms. Weak passwords are common, and there are even completely open operating states without authentication mechanisms, coupled with a lack of supervision and monitoring mechanisms, leading to the possibility of unauthorized operations on related production equipment.
e. Frequent Virus Infection Incidents Due to Negligence with Mobile Media. The misuse of mobile storage media severely affects the safety of control systems and the security of production networks, logically and physically isolating production networks and office networks. The improper use of mobile storage media, illegal copying, loss of media, and unintentional connections to the Internet can easily lead to the spread of viruses from USB drives. Once mobile storage media is infected with a virus and serves as a medium for virus transmission, bringing the virus into the internal network can significantly undermine physical isolation.
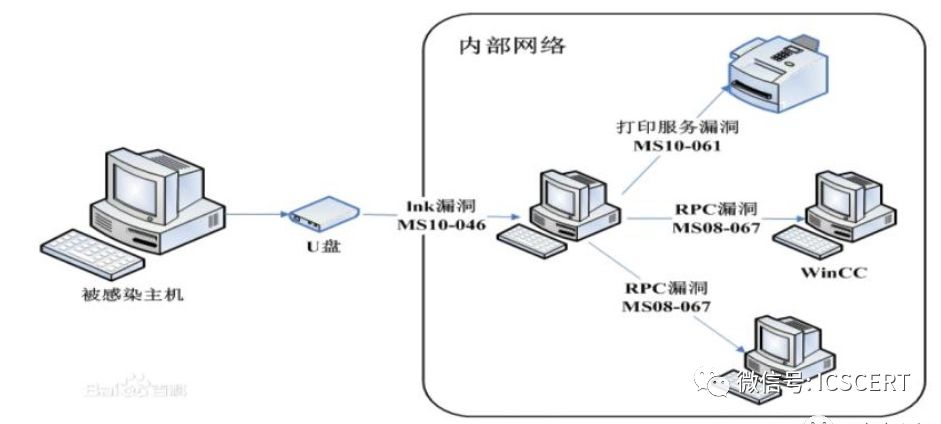
Figure 24: Virus Transmission through USB Drives
f. Remote Maintenance Leading to Unauthorized Access. During the maintenance or troubleshooting of industrial control systems, using remote maintenance diagnostics or external mobile terminals without strict security measures may lead to unauthorized access to the system.
Original Source: Chun Jiao and Zhi Ming
