Author | Green Alliance Technology, GeWu Laboratory, Chen Jie
In many upper-level configuration software, in order to facilitate developers for debugging and analysis, simulators are often equipped to simulate real PLC or HMI devices. These software generally exchange data with configuration software via TCP/UDP protocols, so some simulators may listen on specified ports, and even bind the port directly to the address 0.0.0.0, allowing other users to access them remotely.
Simulators may use the same codebase as real devices, meaning that vulnerabilities present in the simulator can also affect real devices. Conversely, vulnerabilities in real devices can also impact simulators, especially those found in private protocol parsing, such as buffer overflow vulnerabilities leading to remote code execution. If a service exposed by the simulator has high-risk vulnerabilities, attackers can exploit these vulnerabilities to compromise the developer’s host for further penetration.
1. Define research objectives, analyze the ports exposed by the simulator, and identify the services exposed by these ports, such as modbus,
ftp, s7comm, and other key services.
2. Reverse engineer the private key services, analyze the message formats of the protocols, and focus on auditing dangerous functions, such as strcpy, memcpy, atoi, and others that can easily lead to issues. During the reverse process, go through some simple vulnerabilities (stack overflow, integer overflow, hardcoded credentials, etc.).
3. Use the analyzed message formats to create fuzzing tools for fuzz testing. Since the simulator runs on the upper-level machine, the fuzzing speed may be slightly faster than directly fuzzing real devices.
Through the above research methods, some security issues of industrial control device simulators were discovered, involving vendors such as ABB, Schneider, CodeSys, etc. Below are a few examples of common security issues that occur in simulators.
Dangerous Interface CVE-2019-18995
ABB HMISimulator is a component of the HMI simulator in ABB’s PanelBuilder 600. This simulator allows for simulation debugging during development. When analyzing its security, we discovered an arbitrary file read/write vulnerability CVE-2019-18995.
ABB HMISimulator directly exposes an HTTP service. During the analysis, traditional web vulnerability discovery methods can be used. By combining some reverse engineering techniques, we quickly identified two dangerous CGI interfaces exposed by HTTP, capable of reading and writing arbitrary files.
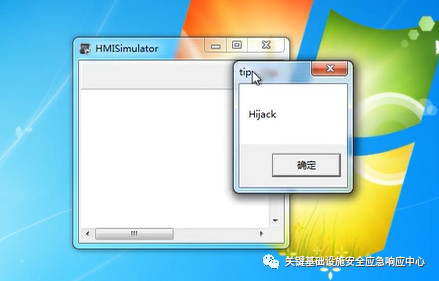
This vulnerability can achieve remote code execution by writing some critical files, such as critical exe/dll, scheduled tasks, etc. The specific process will not be elaborated here.
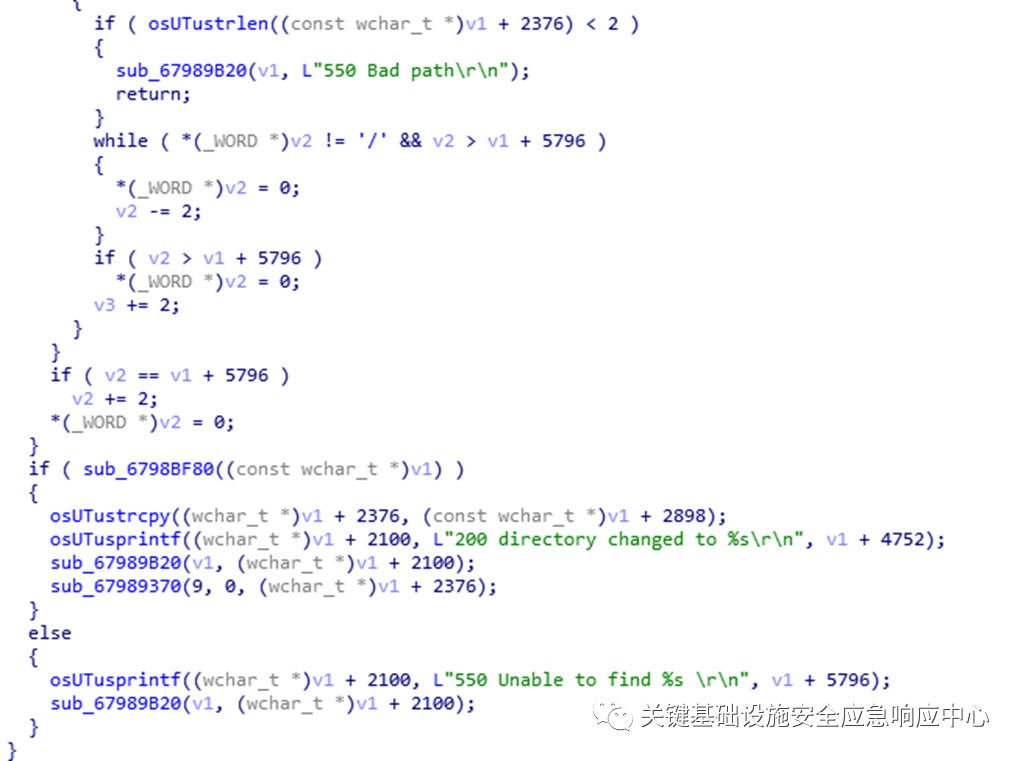
Directory Traversal CNVD-2020-09998
Vijeo-designer is a professional HMI programming design software launched by Schneider, which can complete HMI design and downloading. The HMI Simulator is the HMI simulator in this software, where we discovered a directory traversal vulnerability CNVD-2020-09998.
The HMI Simulator directly exposes an FTP service for project uploads and downloads. Due to the lack of path validation (such as ../ strings) in the FTP implementation, arbitrary directory traversal occurs.
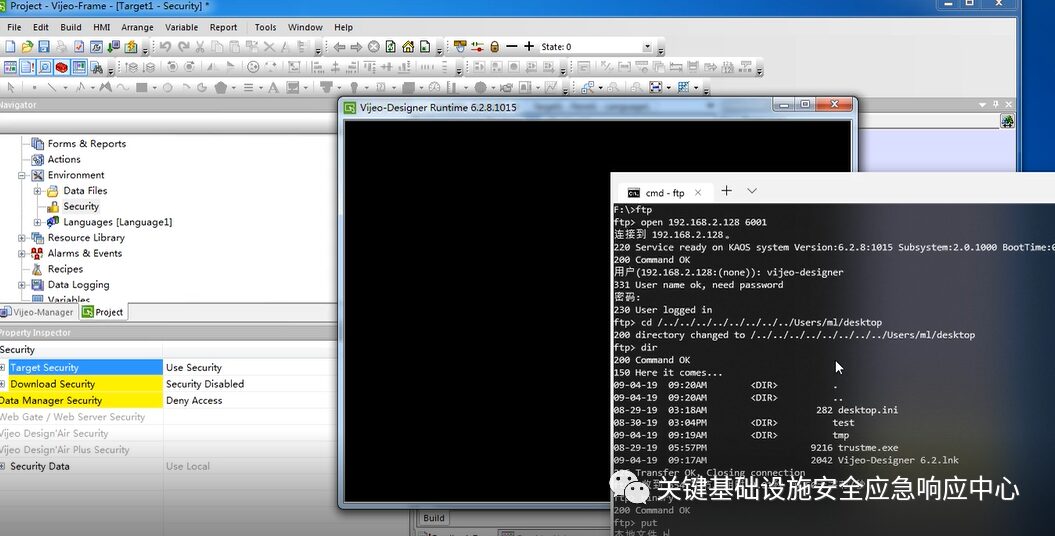
Attackers can traverse to any file directory to perform arbitrary file read/write, achieving remote code execution.
Null Pointer Dereference CVE-2019-19789
PLCWinNT is a simulation software that comes with CodeSys, used to simulate PLC, facilitating developers to debug without physical devices. Through fuzz testing of the exposed private protocol, we discovered a null pointer dereference vulnerability CVE-2019-19789.
PLCWinNT exposes port 1200, using the proprietary CodeSys protocol. Since this simulator uses global pointer variables without validation, if this variable is NULL, it leads to null pointer dereference, causing the program to crash.
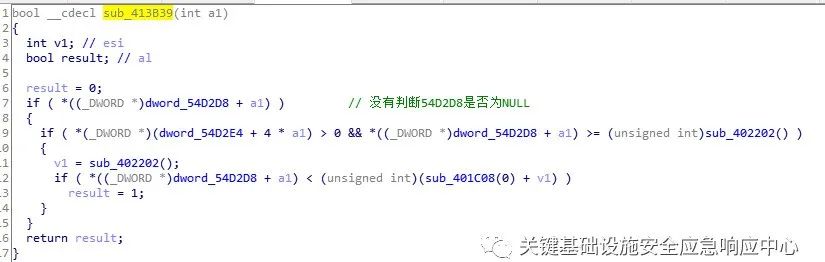
For simulators, remote denial of service is not considered very harmful, as users only use it during development, and the program can simply be restarted. However, this simulator uses the same runtime library as the real PLC, leading to vulnerabilities in the simulator affecting real devices, allowing attackers to initiate remote denial of service attacks against the PLC through this vulnerability.
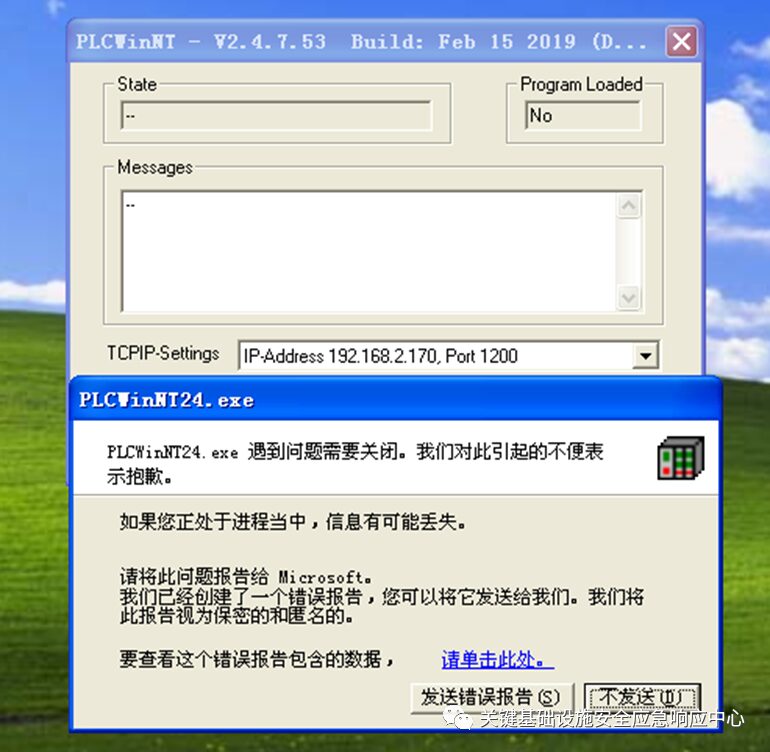
For industrial control device simulator software, there are still many security issues. Different vendors have vastly different attitudes towards security issues. The remediation cycle for these vulnerabilities can be as short as three months or as long as a year. This gap undoubtedly poses a significant threat to user security, and therefore, the following security recommendations are provided:
1. When using the simulator’s functionality, check the ports it exposes. Generally, developers use simulators only on local machines and do not utilize remote access features, so directly block the corresponding ports to prevent external access.
2. Pay attention to official security announcements and promptly update upper-level development or configuration software. If there is an automatic update feature, please enable it.
Original Source: Critical Infrastructure Security Emergency Response Center
















