✦
To implement the “Guidelines for Information Security Protection of Industrial Control Systems” and fulfill the policy requirements of the “14th Five-Year Plan” for coordinated development and safety, the Industrial Control System Information Security Industry Alliance (ICSISIA) launched a collection and selection activity for typical application cases of industrial safety systems on May 20, 2021. This initiative aims to leverage advanced examples to enhance the security protection capabilities of the industrial internet and promote the high-quality development of China’s industrial safety industry. ICSISIA has introduced a special topic on industrial safety system cases, publishing selected typical application cases for readers.
✦
✦
✦
1 Project Overview
✦
1.1 Project Background
As the cybersecurity situation for industrial control systems becomes increasingly severe both domestically and internationally, the Ministry of Industry and Information Technology (MIIT) has issued a series of documents, including the “Guiding Opinions on Strengthening Cybersecurity Work for the Industrial Internet,” “Notice on Strengthening Information Security Management of Industrial Control Systems,” and the “Guidelines for Information Security Protection of Industrial Control Systems.” These documents emphasize the importance and urgency of enhancing information security management for industrial control systems, particularly in critical sectors closely related to national economy and people’s livelihoods, such as nuclear facilities, steel, non-ferrous metals, chemicals, petroleum and petrochemicals, and power.
Steel enterprises are typical production-intensive, capital-intensive, and technology-intensive businesses with strong production continuity and high coupling of production systems. In recent years, many steel companies in China have been advancing intelligent construction, particularly investing heavily in industrial control systems to achieve intelligent upgrades and transformations. The main industrial control systems used include PCS, DCS, PLC, and SCADA, which increasingly emphasize open system design and often adopt third-party integration, with PC-based operation terminals. This improvement significantly reduces user investment and maintenance costs, but at the same time, the network risks have become more severe. Effectively preventing attacks from internal or external sources and ensuring the stability and reliability of production systems is a pressing issue for information security in the steel industry’s industrial control systems. From the experience summarized in application cases, the current issues of inadequate management, outdated protection measures, industrial network viruses, device vulnerabilities and backdoors, persistent threats (APT), and wireless technology are significant concerns. If these issues occur, they can lead to substantial economic losses, threaten personnel safety, and cause severe social impacts.
This solution is based on the current security status of the steel industry and addresses the existing security issues at Quanzhou Mingguang Steel, formulating a forward-looking and practical industrial network security defense solution.
1.2 Project Introduction
The “Automation Cybersecurity Defense Solution for the Steel Industry” targets the industrial control system network of Quanzhou Mingguang Steel, conducting risk assessments and verifications in accordance with the “Guidelines for Information Security Protection of Industrial Control Systems” and other standards. After in-depth research on the on-site network and analysis of risk issues, the system network is protected and reinforced from perspectives such as “security deficiencies, configuration rectification, and management rectification.” Different responses are adopted for different risks, following relevant standards to establish a secure network architecture for steel industrial control systems. The solution proposes a layered defense strategy for the hot-rolled network industrial control system, providing a comprehensive solution from pre-detection and early warning, in-process prevention and control, to post-audit and investigation.
1.3 Project Objectives
As the information technology level of steel enterprises continues to improve, a large amount of data is exchanged both vertically and horizontally, and the enterprise office network and production network architecture are no longer isolated. The centralized marketing and production monitoring, along with the “one network throughout” architecture, increase the likelihood of attacks on critical control systems. The steel metallurgy industry, as a key national infrastructure, must comply with cybersecurity law requirements. This solution is a typical industrial control security protection plan for the steel industry, adhering to the security technical requirements of graded protection, providing security protection for industrial control systems from four aspects: network security, host security, data security, and application security. It deeply integrates whitelist technology, adapts to the network characteristics of different process segments, and constructs a dynamic defense system for the cybersecurity of steel enterprise industrial control systems. It can be widely applied to the control system security protection of various process plants in the steel metallurgy industry, including comprehensive plants, sintering plants, iron-making plants, and steel-making plants.
This solution is based on the industry cybersecurity strategy of “security zoning, overall protection, proactive prevention, and dynamic management,” focusing on risk. It first understands the risks, then plans and implements in stages, conducting network area division, vertical layering, and horizontal zoning. At the same time, it prioritizes technology, with management following, implementing boundary-layer protection and in-domain monitoring. According to the security construction needs of the core business systems in the steel industry, combined with the characteristics of industrial control security, it builds an industrial control security management and service system for enterprises, achieving cybersecurity protection for steel industrial control systems, comprehensively enhancing the overall security of industrial control networks, and ensuring the safe and stable operation of systems. This solution adheres to the production system business characteristics of steel enterprises, meets the requirements of the MIIT’s “Guidelines for Information Security Protection of Industrial Control Systems” and relevant graded protection security requirements, designs corresponding security protection plans, and references the following notices and standards:
(1) “Notice on Strengthening Cybersecurity Management of Industrial Control Systems” (MIIT [2011] No. 451)
(2) “Information Security for Industrial Control Systems: Assessment Specifications” (GB/T 30976.1—2014)
(3) “Information Security for Industrial Control Systems: Acceptance Specifications” (GB/T 30976.2—2014)
(4) “Network Security for Industrial Automation and Control Systems” (GB/T 33007, GB/T 33008, GB/T 33009)
(5) “Guidelines for Information Security Protection of Industrial Control Systems” (MIIT [2016] No. 338)
(6) “Information Security Technology: Basic Requirements for Network Security Graded Protection – Part 5: Extended Requirements for Industrial Control System Security” (GA/T 1390.5-2017).
✦
2 Project Implementation
✦
The overall security solution process is shown in Figure 1.
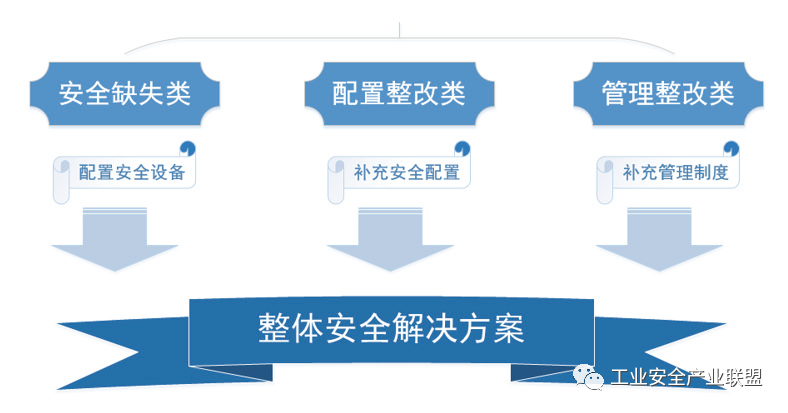
Figure 1 Overall Security Solution Process
2.1 Industrial Control Security Protection Solution (Configuration of Security Devices)
(1) Boundary Security Protection
Deploy industrial firewalls at the boundary with the information technology room to ensure logical isolation between areas, and implement deep detection and security during data transmission through policies, as shown in Figure 2.
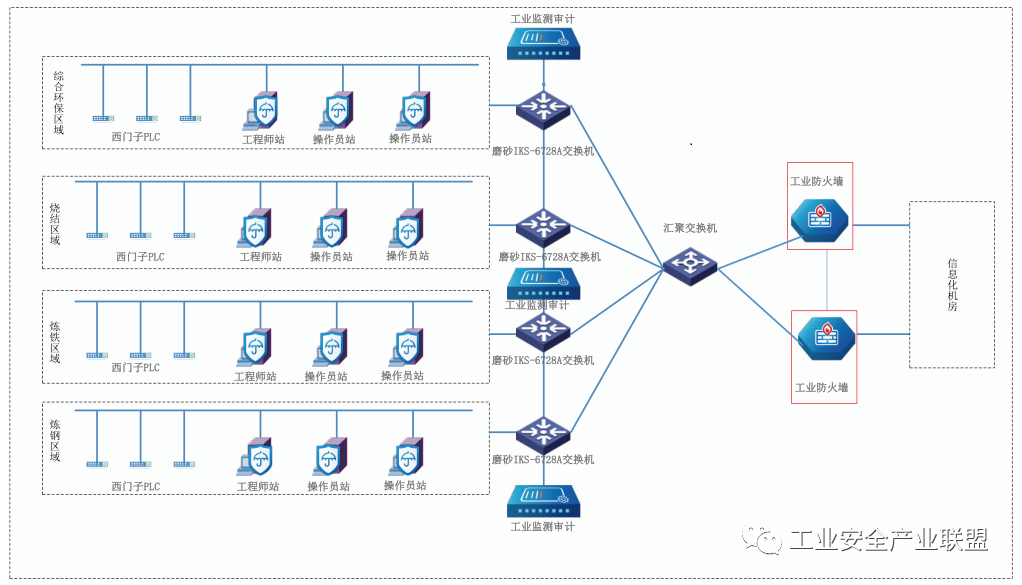
Figure 2 Boundary Firewall Deployment
The firewall mainly implements the following functions:
-
Known Industrial Control Threat Detection: Real-time detection of attack behaviors in the industrial control network, handling and alerting intrusions in real-time through an embedded industrial control threat library and detection rules.
-
Self-learning of Industrial Control Behavior and Protocol Rules: By deeply analyzing industrial control protocols and behaviors, it automatically learns operational behaviors and rules based on industrial control protocols, establishing a security detection model.
-
Black and White List Access Control: Controls network transmission behaviors through whitelist rules, ensuring normal business operations while blocking unnecessary network traffic and abnormal attack behaviors. Known blacklists effectively prevent the harm of known vulnerabilities.
-
Deep Detection of Industrial Control Protocols: Supports deep packet inspection of OPC protocols, dynamic port opening for OPC, message format and integrity checks. Supports deep detection of industrial control protocols such as Ethernet/IP, Modbus/TCP, IEC 104, DNP3, PROFINET, MMS, S7, GOOSE, SV, etc., including message format checks, function code control, register control, and connection status control. Supports deep packet inspection of proprietary protocols in the oil and gas industry. Supports detection of custom format industrial control protocols.
-
Traditional State Detection Packet Filtering: Filters data packets based on access control rules. Dynamic filtering technology is used to open required ports for legitimate access connections dynamically, and automatically closes corresponding ports when the connection ends.
(2) Monitoring and Auditing Solution
Deploy auditing detection devices at key core nodes in each logical area, mainly for instruction-level detection of traffic, logs, and critical data, as shown in Figure 3.
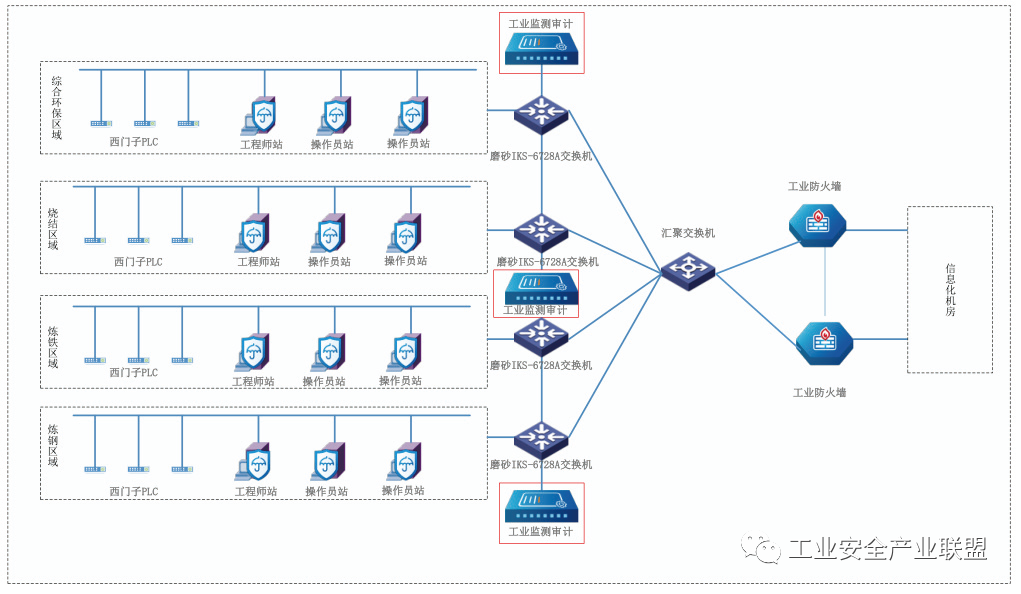
Figure 3 Auditing Detection Device Deployment
Main functions include:
-
Real-time Industrial Network Security Monitoring
Default monitoring of the industrial control network in real-time through a bypass method (can also be connected in series), auditing elements such as protocols, traffic, date and time, users, event types, and whether events are successful, and statistically analyzing to display the network’s security status in real-time.
-
Intrusion Detection
Real-time detection of attack behaviors in the industrial control network, establishing monitoring rules using an embedded industrial control vulnerability library and industrial control behavior whitelist, and alerting intrusions in real-time.
-
Non-compliant Behavior Monitoring
Detecting non-compliant industrial control network behaviors in business traffic through custom rules or whitelist rules, providing real-time alerts and responses to non-compliant behaviors, and retaining network data.
-
Deep Detection of Industrial Control Protocols and Flow Restoration
The deep packet parsing engine supports most mainstream industrial control protocols, including Modbus TCP, IEC 104, DNP3, S7, CIP, Ethernet/IP, OPC, etc. The deep monitoring engine supports IP fragmentation reassembly and TCP segmentation restoration, and provides early warning for industrial malformed messages. The deep detection engine supports the instruction set and data message flow restoration of industrial protocols, providing a basis for security post-event tracking.
-
Audit Warning for Important Industrial Events
Records and warns significant industrial network behaviors such as starting, stopping, uploading, and downloading in the industrial network control system.
-
Data Retention
Retains all original network data according to user-defined settings, configurable for retention of six months or more.
-
Security Auditing and Anomaly Response
Audits security events, promptly tracing the trajectory of security incidents. Conducts fine-grained auditing of user operational behaviors to facilitate the restoration of operational truths. An independent alert response mechanism can define response methods for security events of different security levels.
(3) Host Security and Mobile Storage Solution
Install host guardians on operation stations, management terminals, and servers in various areas to manage the operating system itself, baselines, applications, services, and USB ports, as shown in Figure 4.
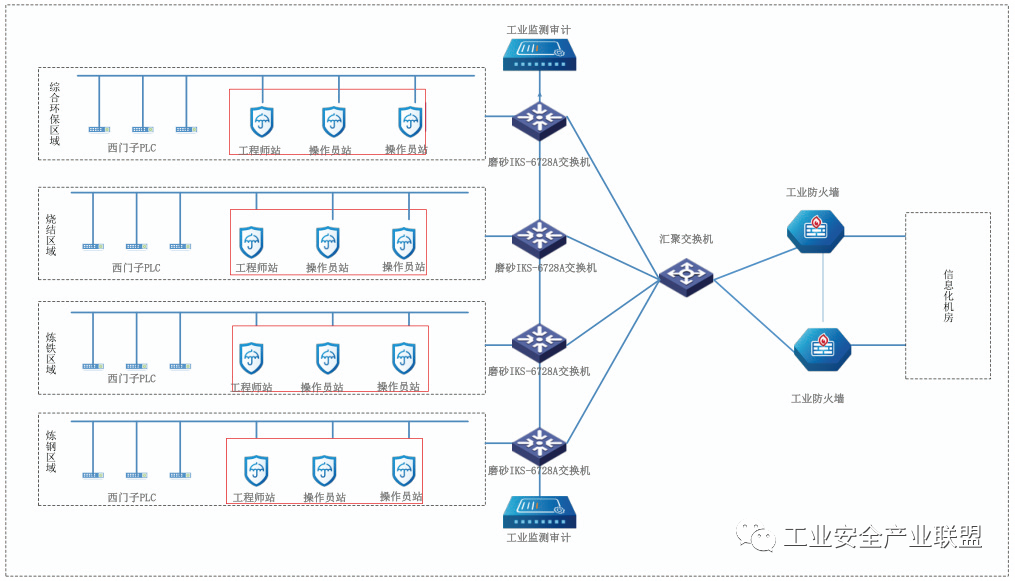
Figure 4 Host Guardian Installation
Main functions include:
-
Application Whitelist Protection
Prohibits the execution of illegal processes outside the whitelist, confirming the integrity of programs through certificates, checksums, etc., thereby preventing the execution of programs that have been infected or tampered with by viruses.
-
Mobile Storage Media Whitelist Protection
USB Device Recognition: Supports recognition of general USB devices.
USB Device Auditing: Provides operation records of USB storage devices, which cannot be deleted or tampered with.
USB Device Whitelist: Prohibits the connection of illegal USB devices outside the whitelist, generating security events.
-
Whitelist Management
Whitelist Generation: Establishes a whitelist through an automatic scanning function.
Whitelist Import and Export: Provides import and export functions for the whitelist.
Whitelist Update: When new programs, network services, and USB devices need to be added, these new settings can be easily updated to the whitelist.
-
Integrity Protection for Specific Objects
Provides integrity protection for files in specific installation directories, preventing malicious programs or erroneous operations from injecting, modifying, or deleting target files.
-
Security Event Auditing
Security Event Logs: Non-whitelist processes running and USB device connections generate security events.
Security Event Auditing: Records of security events cannot be deleted or tampered with.
-
Secure USB Drives
Using secure USB drives can control files in mobile media, allowing transmission only within a secure range, preventing non-whitelisted hosts from reading files.
2.2 Engineer Station Electronic Lock Solution (Supplementary Security Configuration)
Combining existing security measures and actual terminal security needs, the security login system management construction adopts an identity authentication system, which consists of a server, client, and USB Key, as shown in Figure 5. It can achieve dual authentication of physical identity and user identity, fundamentally compensating for the inherent flaws of the Windows system and ensuring operating system security. The system adopts a mixed architecture of C/S and B/S to manage terminal logins, achieving functions such as computer terminal login, screen locking, management, log collection, and display, effectively managing and reducing management costs while enhancing client security.
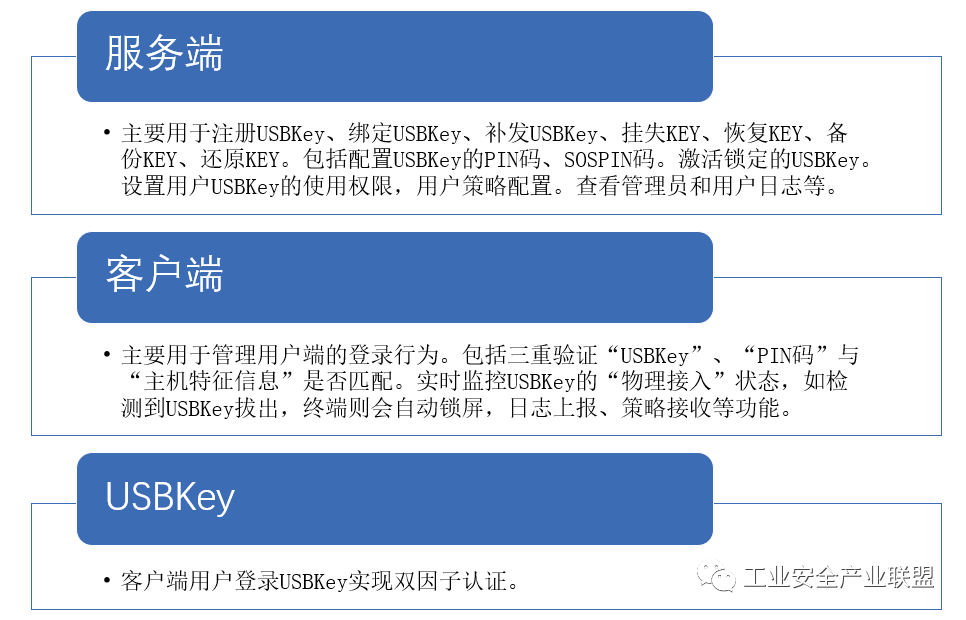
Figure 5 Composition of the Identity Authentication System
2.3 Security Management (Supplementary Management System)
Establish various management regulations, management methods, and interim regulations based on the basic requirements of the security management system. The specific management regulations, management methods, and implementation methods derived from the principles and guiding strategies specified in the main security policy document must be operational and effectively implemented.
The system needs to have a unified format and effective version control; the release method must be formal, effective, and indicate the release scope, with registration of documents sent and received. The information security leadership team is responsible for regularly organizing relevant departments and personnel to review the rationality and applicability of the security management system, and to periodically or irregularly review and revise the security management system.
From the perspectives of management system risk and security awareness risk, a baseline assessment of the existing security management system of client enterprises is conducted. Firstly, the technical level and security awareness of operational management personnel vary greatly, leading to significant security risks due to unauthorized access and violations. Secondly, the relatively closed environment of domestic industrial control systems means that internal personnel’s erroneous operations, violations, or intentional destructive actions become major security risks faced by industrial control systems. Lastly, industrial control systems generally lack comprehensive security policies, management systems, and training for personnel’s security awareness. Based on this, the following constructions were carried out for client enterprises:
-
Construction of Security Management Systems
-
Construction of Security Management Organizations
-
Construction of Security Management Personnel
-
Construction of Security Management Operations
2.4 Application Effects
The “Automation Cybersecurity Defense Solution for the Steel Industry” has been implemented in group enterprises such as Fujian Ming Steel, Shougang, and Ma Steel. The overall implementation includes risk research and analysis of industrial control networks, improvement of the security management system (analysis and preparation of security management regulations, security awareness training, improvement of industrial control security emergency response mechanisms, optimization of operation and maintenance systems), and establishment of a security technology system (industrial control security domain division, industrial control network security detection, industrial control security domain protection, industrial control security management platform). The products include an industrial control security management platform, industrial control monitoring and auditing, intrusion prevention systems, intrusion detection systems, industrial control firewalls, and industrial host guardians.
This project has also achieved the following results:
(1) Compliance with Security Requirements: This project is based on compliance with national security laws and strives to adhere to the relevant technical and management requirements in the “Guidelines for Information Security Protection of Industrial Control Systems,” conducting security protection construction for industrial control systems based on the production business characteristics of enterprises.
(2) Optimization of Resource Allocation: This solution is designed from the user’s perspective, maximizing the use of existing resources of enterprises under compliance, while effectively integrating the operational models of higher-level units to enhance security protection levels under limited resources.
(3) Improvement of Enterprise Security Protection: The results of this project provide a fundamental guarantee for the stable operation of industrial control networks in steel companies, preventing various threats such as viruses, Trojans, and attacks from internal and external personnel, as well as the exploitation of software backdoors, significantly enhancing the ability of industrial control systems to prevent threats in an increasingly harsh network environment, effectively ensuring the stable development of the national economy.
(4) Establishing a Benchmark and Creating a Demonstration: The solution design provided by this project targets the technical characteristics of industrial control systems and the business characteristics of the steel industry, fully covering management and technology, meeting regulatory and future business development needs, and accumulating rich experience among related enterprises in the steel industry, serving as a good demonstration for other parallel enterprises in the group.
✦
3 Case Highlights
✦
(1) The case provides a solid foundation for client enterprises to carry out graded pilot projects for network security.
The implementation target of this case is Fujian Quanzhou Mingguang Steel, which is also one of the first batch of pilot enterprises for graded network security in industrial internet in Fujian Province. Before the pilot was determined, the implementation process fully referenced the “Guidelines for Information Security Protection of Industrial Control Systems” and the relevant technical and management requirements in version 2.0 of the “Basic Requirements for Network Security Graded Protection,” providing comprehensive protection to reduce network security incidents and economic losses for enterprises.
(2) Significant Innovative Demonstration Benefits
Through project construction, it is conducive to incubating industry standards and improving the efficiency and level of industry supervision and enterprise management. It is particularly beneficial in forming a demonstration effect for industrial control and network security regulation in the steel field.
(3) Outstanding Management Benefits
This solution establishes a cybersecurity management system for the industrial control network of Fujian Quanzhou Mingguang Steel based on a bidirectional mechanism, formulates business and technical specifications for the comprehensive management platform of industrial control security, and establishes a management standard and system, achieving unified management of all industrial control security protection devices and systems, reducing operation and maintenance management costs. It especially provides model guidance for group-level industrial control information technology.