
Click the above blue text to follow us
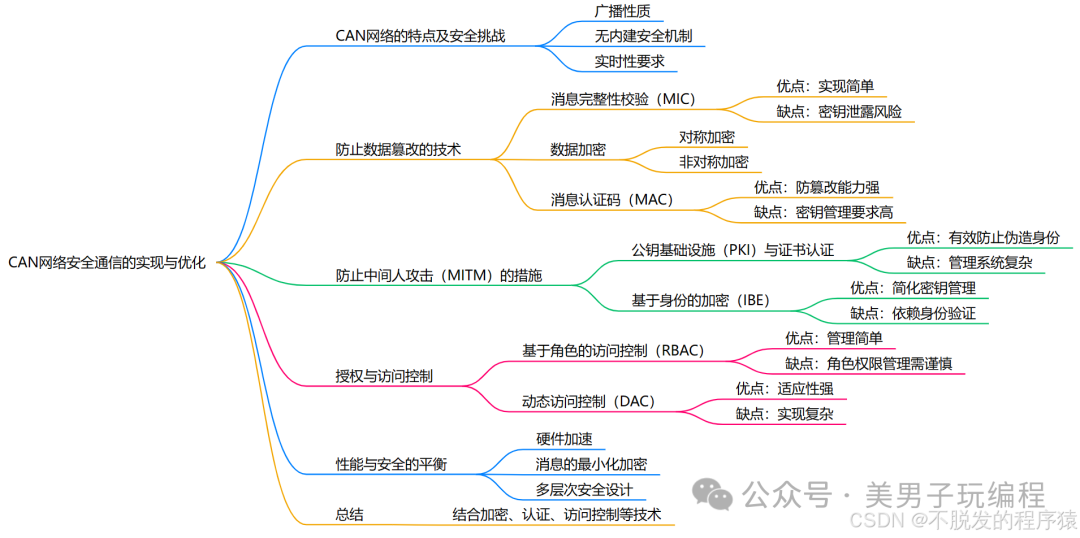
Implementing secure communication in the CAN network is key to ensuring data integrity, protecting information confidentiality, and preventing man-in-the-middle attacks.
By introducing technologies such as encryption, authentication, and access control, the security of communication can be effectively enhanced.
However, given the performance requirements of embedded systems, it is essential to flexibly select and optimize appropriate security technologies.
1
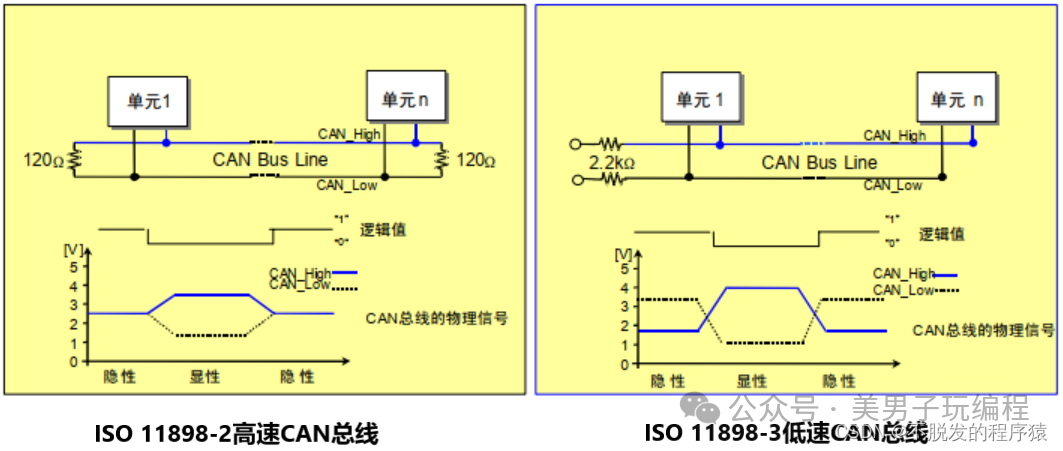
Characteristics of CAN Networks and Their Security Challenges
The CAN network is a serial communication protocol widely used in automotive, industrial automation, and embedded systems, primarily designed for efficient real-time data transmission and low-cost implementation.
Its main characteristics include:
- Broadcast Nature: The CAN bus is a broadcast protocol, allowing all nodes to receive messages on the same bus, making it susceptible to attacks.
- No Built-in Security Mechanisms: The original CAN protocol does not have any built-in encryption, authentication, or access control mechanisms.
- High Real-time Requirements: The CAN protocol is mainly used in real-time control systems, so the introduction of security mechanisms should not significantly increase latency or reduce real-time performance.
2
Technologies to Prevent Data Tampering
Data tampering attacks mainly refer to malicious nodes altering the data packets transmitted on the CAN bus, affecting the normal operation of the system.
To prevent such attacks, the following technologies can be employed:
2.1 Message Integrity Check
A simple and effective method to prevent data tampering is to attach an integrity check code (such as HMAC) to each CAN message, ensuring that the data has not been modified during transmission.
- Working Principle: By appending a checksum to the data frame, the receiver can use the same algorithm and key to compute the message integrity and compare it with the appended checksum. If the message has been tampered with during transmission, the computed checksum will not match, allowing the receiver to detect data tampering.
- Advantages: This method is cost-effective and easy to implement, suitable for scenarios with high real-time requirements.
- Disadvantages: If the encryption algorithm is misused or the key is leaked, an attacker may forge legitimate messages.
2.2 Encryption Protection
Data encryption is another important means to prevent data from being maliciously tampered with or leaked.
Encryption ensures that even if data is intercepted during transmission, attackers cannot read or alter the content.
Symmetric Encryption: Using symmetric encryption algorithms such as AES (Advanced Encryption Standard) to encrypt the message content. Both parties share an encryption key, with the sender encrypting the message and the receiver decrypting it.
- Advantages: Fast speed, suitable for environments with high real-time requirements.
- Disadvantages: Key distribution and management are relatively complex.
Asymmetric Encryption: Using asymmetric encryption algorithms such as RSA or ECC (Elliptic Curve Cryptography), the sender encrypts the message with the receiver’s public key, and the receiver decrypts it with their private key.
- Advantages: More secure key management.
- Disadvantages: Higher computational overhead, which may become a bottleneck in systems with high real-time requirements.
2.3 Message Authentication Code
An enhanced method for verifying data integrity is to use a Message Authentication Code (MAC) to ensure that the message has not been tampered with.
Working Principle: The sender encrypts the data with a key to generate a MAC value, and the receiver uses the same key to compute the MAC value of the received data and compares it with the sent MAC value. If they match, the data has not been tampered with; otherwise, it is considered tampered.
- Advantages: Strong anti-tampering capability, especially suitable for protecting data integrity.
- Disadvantages: Requires key sharing, and the security of key management is critical.
3
Preventing Man-in-the-Middle Attacks
Man-in-the-Middle (MITM) attacks refer to attackers eavesdropping on and altering messages on the communication link, silently obtaining or tampering with data between victims.
To prevent such attacks, the following measures can be taken:
3.1 Public Key Infrastructure and Certificate Authentication
MITM attacks often rely on identity forgery or replacing legitimate node messages.
Introducing PKI (Public Key Infrastructure) and digital certificate authentication in the CAN network is an effective method to prevent such attacks.
Working Principle: Each node has a pair of public and private keys, and the public key is signed by a trusted Certificate Authority (CA). When nodes communicate, the sender encrypts the message using the receiver’s public key, and the receiver decrypts it using their private key, ensuring the confidentiality and integrity of the information.
- Advantages: Effectively prevents man-in-the-middle identity forgery, enhancing security.
- Disadvantages: Requires a robust public key management system and has higher computational overhead.
3.2 Identity-Based Encryption
In some embedded systems, there may not be a traditional CA system to manage certificates.
In such cases, Identity-Based Encryption (IBE) can be used, where the identity information of the node (such as network address) is used as the basis for generating encryption keys.
Working Principle: Each node generates key pairs using identity information without the need for centralized certificate management. Thus, only nodes with specific identities can decrypt specific messages.
- Advantages: Simplifies key management, especially suitable for dynamically changing networks.
- Disadvantages: The system relies on identity verification mechanisms; if identity information is leaked, security will be greatly compromised.
4
Authorization and Access Control
To ensure that only authorized nodes can send or receive messages, authorization and access control mechanisms in the CAN network are crucial.
4.1 Role-Based Access Control
RBAC is a common access control method that restricts nodes’ access to network resources by defining different user roles.
Working Principle: Access permissions for different types of messages are defined based on the node’s role. For example, only authenticated Electronic Control Units (ECUs) can send start commands.
- Advantages: Relatively simple to manage and implement.
- Disadvantages: Requires close attention to the definition and management of role permissions in the system.
4.2 Dynamic Access Control
For dynamically changing networks, such as smart vehicle networks or industrial control systems, policy-based dynamic access control (DAC) can provide more flexible access permission management.
Working Principle: The system adjusts access permissions in real-time based on specific situations and security policies. For example, temporary authorization or revocation of access permissions for nodes based on current network status, message importance, etc.
- Advantages: Highly adaptable, suitable for complex and frequently changing environments.
- Disadvantages: More complex to implement and manage compared to RBAC.
5
Balancing Performance and Security
Although the above security technologies can theoretically enhance the security of CAN communication, embedded systems often face constraints such as real-time performance, bandwidth, and computational resources in practical applications.
Therefore, it is essential to find a balance between security and performance:
- Hardware Acceleration: Using hardware acceleration (such as encryption engines or security modules) to improve the efficiency of encryption and decryption operations, reducing computational overhead.
- Minimized Encryption of Messages: For messages with extremely high real-time requirements, only key information can be encrypted instead of the entire message.
- Multi-layer Security Design: By designing different levels of security measures in layers, it is possible to maintain high efficiency in the system while ensuring the security of critical communications.
As the hardware performance of embedded systems improves and security technologies continue to develop, the security of CAN networks will be further enhanced, especially in applications in automotive and industrial control fields.
 Click Read the Original Article for more exciting content~
Click Read the Original Article for more exciting content~