Author: Green Alliance Technology, Ge Wu Laboratory, Chen Jie
Background
Recently, researchers abroad discovered a code injection vulnerability in Schneider’s systems (CVE-2020-7475), which could allow Schneider PLCs to be turned into worms. If successfully exploited, this vulnerability could enable the PLC to act as a small PC executing malicious network activities, serving as an internal network jump point or a network scanner for covert penetration activities against industrial systems.
Design Flaw
This vulnerability is a clear design flaw. The following will explain the root cause of the vulnerability by comparing the configuration program designs of Siemens PLCs and Schneider PLCs.
Siemens PLC
The Siemens S7 series PLC offers various methods for PLC configuration programming, such as ladder diagram representation (LAD or FBD), a Pascal-like programming language (SCL), and an assembly-like programming language (STL). Regardless of the type of input source, the PLC program compiles the program into MC7 bytecode (STL is even a lower-level representation).
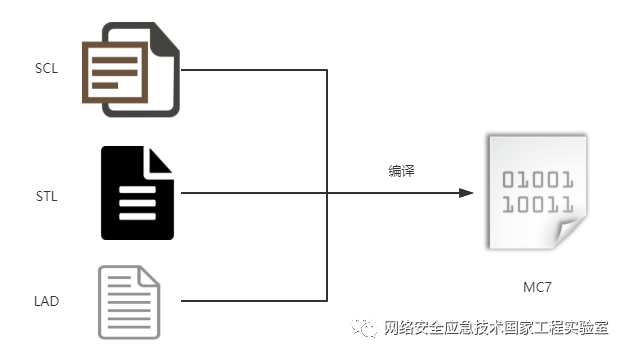
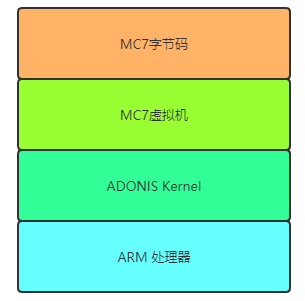
Once the configuration software compiles the project file (in MC7 file format), it is downloaded to the PLC via Siemens’ S7COMM/S7COMM-PLUS protocol, and then the MC7 virtual machine within the PLC schedules and interprets the MC7 bytecode. Since the virtual machine can restrict the resources accessed by the program, the compiled bytecode cannot directly manipulate hardware and can only access resources provided by the virtual machine, such as establishing TCP connections to send and receive data through FB blocks using TCON and TDISCON. This means that the compiled configuration program has the capability to conduct malicious network activities.
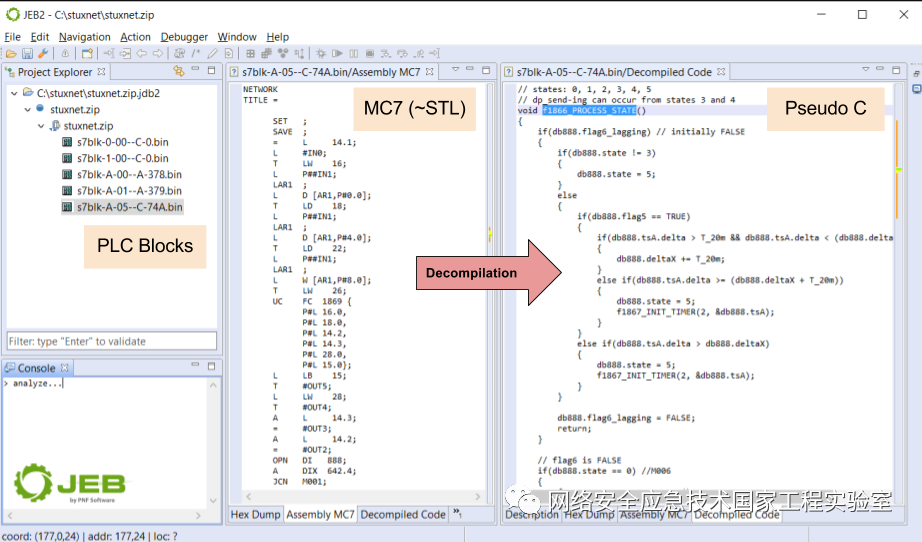
Siemens has not documented the MC7 bytecode, and one can only understand the corresponding assembly instructions through reverse engineering techniques. Fortunately, someone has already done this part of the work (using JEB plugins), and by using this tool, one can disassemble or even decompile MC7 files to understand the code logic in the configuration program. This method is particularly useful when analyzing Siemens worm viruses like Stuxnet.
Schneider PLC
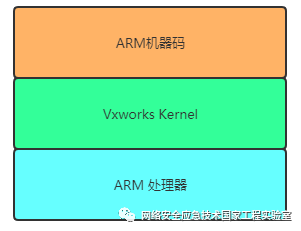
In Schneider PLCs, whether using ladder diagrams (LD), structured text (ST), or function block diagrams (FBD), all are uniformly compiled into ARM machine code, which is executed directly by the ARM processor, thus allowing complete access to the software and hardware resources on the PLC.
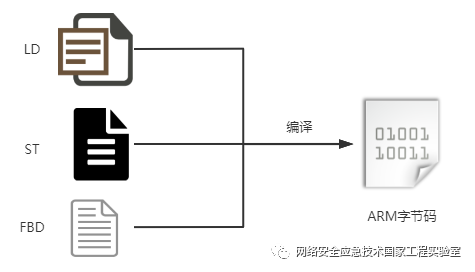
When Schneider’s configuration software compiles the project, it can be directly downloaded to the PLC using Schneider’s ModBus 90 function code (UMAS protocol). Once the PLC starts, it will execute the compiled ARM machine code. If malicious code is injected into the ARM bytecode by an attacker, the attacker can gain complete control over the PLC, having access control over critical resources such as the network, file system, and hardware I/O.
Vulnerability Details
The fundamental reason for this vulnerability is that Schneider PLC directly compiles configuration programs into ARM machine code without restricting the resources accessed during execution, leading to the potential for Schneider PLC worm viruses to have greater stealth and destructive power.
Unity Pro Reverse Engineering
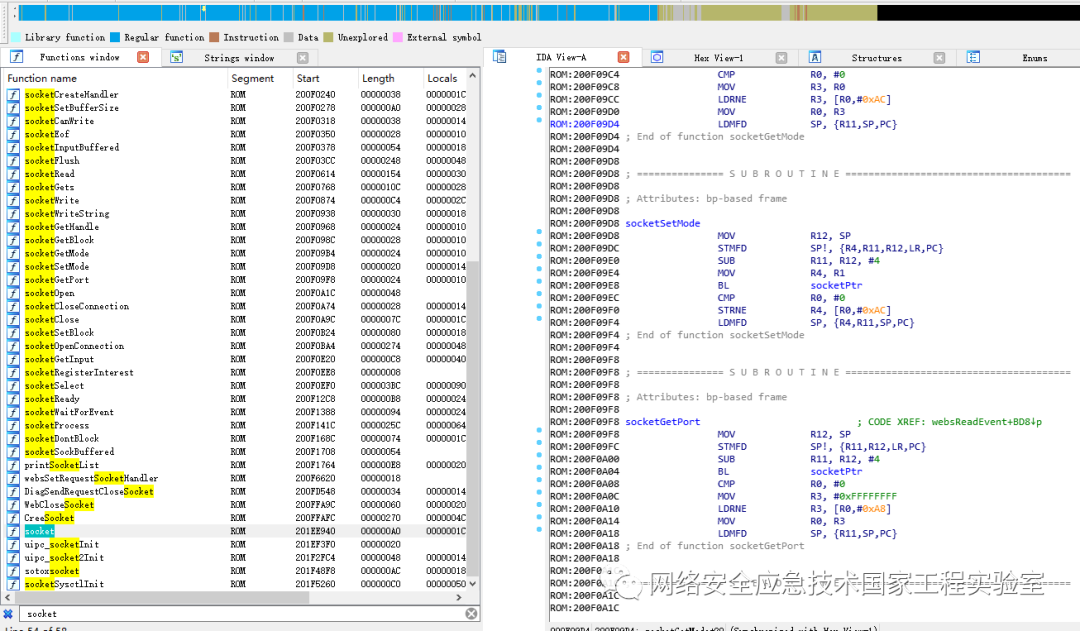
Unity Pro is the configuration programming software corresponding to Schneider PLCs, which can be used to program the PLC. To inject code into the compiled ARM code, one must first locate the part of the code responsible for the compilation. As shown in the figure below, the exported function MyAsmArmStream from asmarm.dll is responsible for compiling ARM assembly code into ARM machine code.
The first parameter of this function points to the ARM assembly string, and it returns the compiled ARM machine code data:
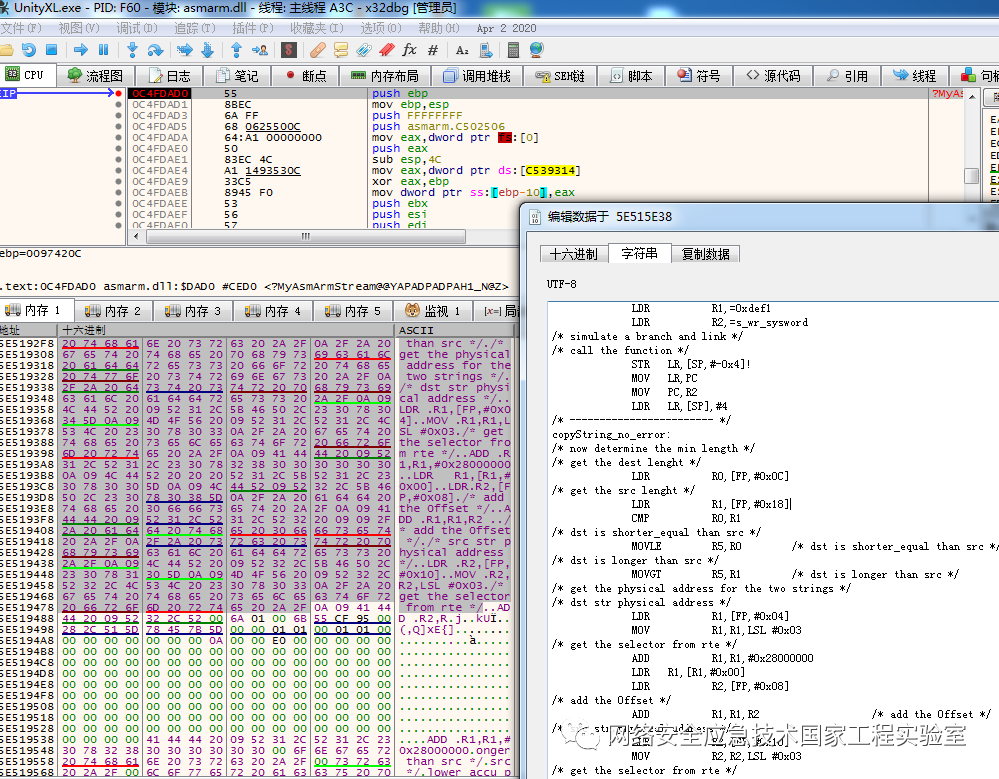
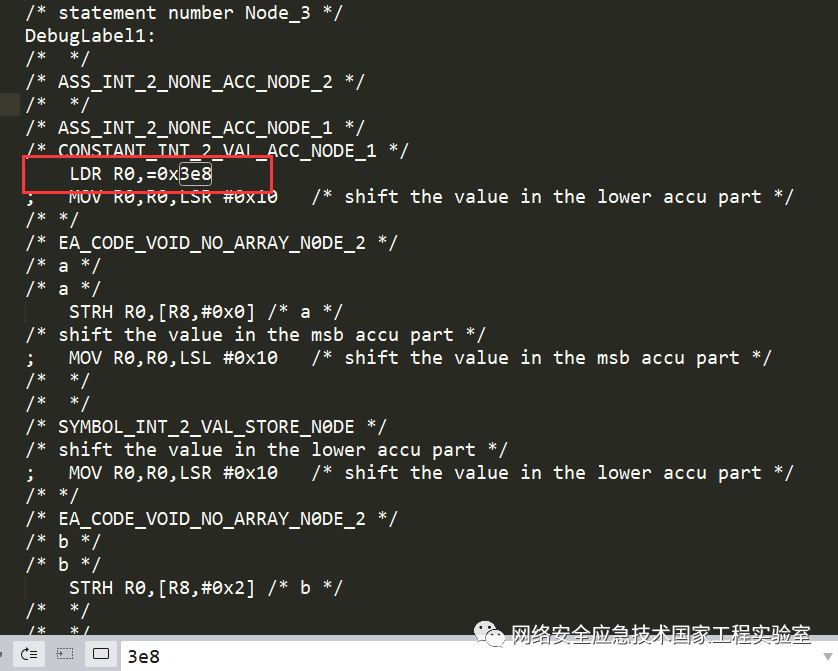
To locate the position of user-written code within the entire ARM assembly, one can write test code (as shown in the figure below):
The generated code will certainly contain the immediate value 1000 (0x3e8). By searching for this immediate value, one can quickly locate the position of user code in the configuration program and obtain the corresponding assembly code.
By simply hooking this function and modifying the incoming assembly code, one can execute arbitrary code within the Schneider PLC.
Code Writing
Schneider PLC uses the VxWorks operating system, which has already provided the necessary functions for exploitation. One only needs to find the function addresses required in the firmware (network access, account management, file access, etc.) and call them directly in ARM assembly.
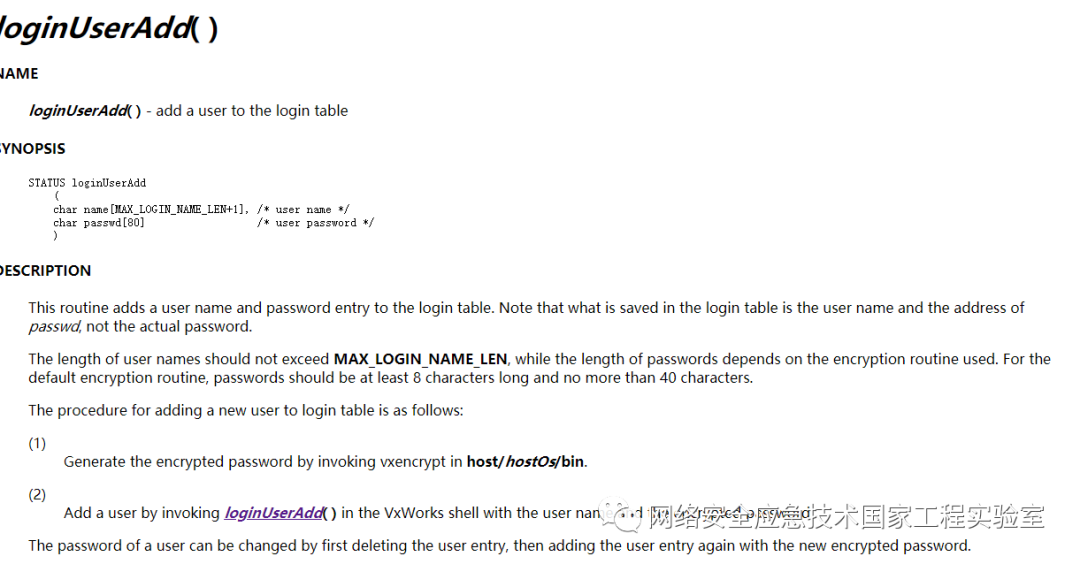
The prototypes of these functions are documented on the official website, and one just needs to construct the parameters and call them. For example, the loginUserAdd function shown in the figure below can add an account, which an attacker can use to add a backdoor account to the PLC.
Exploitation Approach
1. Rename the original asmArm.dll to asm_Arm.dll to facilitate calling a custom dynamic library.
2. Place the malicious asmArm.dll (which mainly hijacks MyAsmArmStream, modifies the incoming ARM assembly code, and calls the original asmArm.dll) into the Unity folder.
3. Run Unity and load the PLC project.
4. Recompile the project.
5. Stop the PLC.
6. Upload the project to the PLC.
7. After starting the PLC, the malicious code will be executed.
Vulnerability Mitigation
Schneider has released a security advisory, providing security patches and recommendations. In the upper computer repair, the integrity of components is mainly checked; if any component is modified, it will cause the software to fail to start, requiring reinstallation.
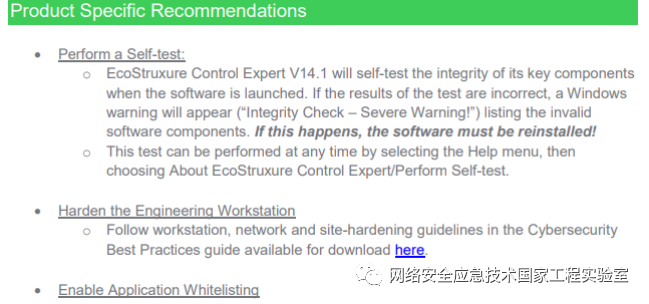
Strictly speaking, this is merely a mitigation measure. Many techniques can bypass security checks (patching security check locations, remote injection, directly forging malicious clients to download malicious projects, etc.), and design flaws are not easily fixed from a software perspective.
Conclusion
This article mainly discusses the root cause of the Schneider CVE-2020-7475 vulnerability and briefly introduces the principles of the vulnerability and some exploitation ideas. It is foreseeable that this vulnerability is not easy to completely fix fundamentally; it can only be circumvented through other technical means. This also indicates that industrial control systems must consider security not only in implementation but also in design from the outset, and security should permeate the entire lifecycle.
Reference Link
https://airbus-cyber-security.com/applying-a-stuxnet-type-attack-to-a-modicon-plc/
Please cite from: National Engineering Laboratory for Emergency Technology in Cyber Security
