A Comprehensive Explanation of Computer Network Principles
Introduction
Hello everyone, I am Tai Dou Xian Ruo Ru, a content creator focused on explaining technology in simple terms. This time I will share knowledge related to the principles of computer networks. I believe the content of this article is already very easy to understand, and I wish you a pleasant reading!

1. Overview of Computer Networks
Times have changed, and everyone’s lives have improved. Almost every household now has a computer, and we are all accustomed to using computers for work, gaming, chatting, and so on. Let’s think about a scenario: if there were no network, wouldn’t we be unable to chat using our computers? So how does the network help us chat online? Let’s discuss what a computer network really is.
Readers who know me understand that I usually explain in my own words first, followed by the official definition. This time, I will do the opposite: I will start with the official definition and then explain:
A computer network is a system that connects geographically independent computers through communication media to achieve data communication and resource sharing.
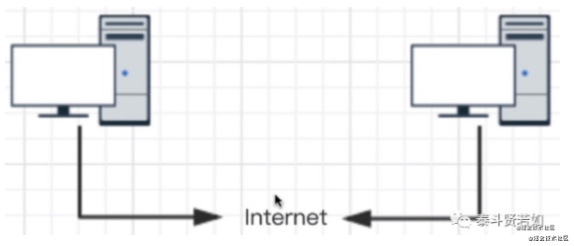
Let’s assume there are two independent and completely unrelated computers, one in Qinghai and the other in Henan, that want to transmit data (chat). Without a network, this is impossible. The network refers to the Internet. The Internet is a communication protocol. What is a protocol? For example, when we make a phone call in China, with over a billion people and various dialects, we need a common standard for effective communication, which is Mandarin. If people from different countries want to communicate, they can use English as a universal standard. Computers are like people scattered around the world, and they also need a common standard to communicate, which is the Internet standard, also known as the Internet protocol.
2. Introduction to Networks and the Story of Neighbor Wang

Let me tell you a fictional story about Neighbor Wang:
There was a man named Neighbor Wang, and his hobby was watching movies. One day, he wanted to watch a movie, but his computer had too many movies stored, and he struggled to find one, which was very frustrating. So he thought, can I categorize all the movies and put the same type of movies in the same folder? Then I could write a browser software to display the folder information, making it easier to find movies. He decided to do it, and soon enough, he organized all the folders and put them on the same page. Whenever he wanted to watch a movie, he could just click on the corresponding folder. So easy! (That’s how websites might have originated).

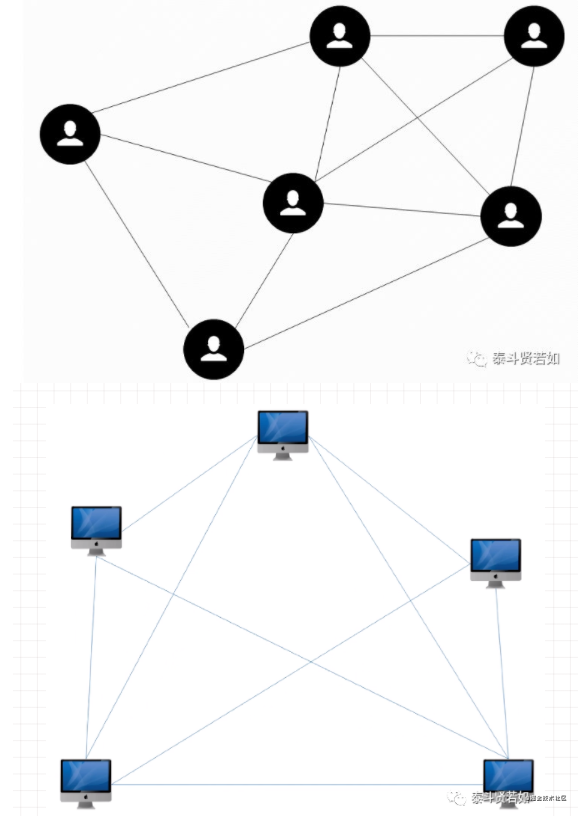
Now a new character appears, let’s call him Xiao Wang (not Xiao Wang Ba). Xiao Wang lives next door to Neighbor Wang. One day, Xiao Wang saw so many movies on Neighbor Wang’s computer and asked if he could have a similar setup on his computer to watch movies too. Neighbor Wang, being generous, agreed without hesitation and told Xiao Wang to connect a cable from his computer to his and download the software to access his computer directly. Xiao Wang was delighted and quickly followed Neighbor Wang’s instructions. Soon, he could also see what was on Neighbor Wang’s computer. With Xiao Wang, there was also Xiao Zhang, Xiao Li, and they all connected their computers with cables to share movies. Thus, a local area network (LAN) was created, which is used in companies or schools. There are many schools, and each school has its own LAN. Different cities also have different LANs. The LANs in one area or city are called metropolitan area networks (MAN), and all the MANs worldwide are referred to as wide area networks (WAN).
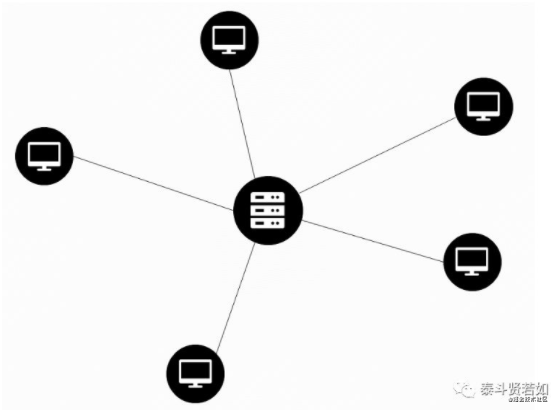
After some time, Neighbor Wang visited Xiao Wang’s house and saw that Xiao Wang had more and better movies than he did. Neighbor Wang asked Xiao Wang for a copy of those movies. Without hesitation, Xiao Wang agreed and told him to figure it out himself. Neighbor Wang thought of a good idea: he would find another computer, transfer all their resources to that computer, and both could connect to that computer to access everything. Xiao Wang smacked his forehead, realizing he should have thought of that earlier. Neighbor Wang found another computer, and they connected their computers to it, transferring all their resources. Now they could share resources easily. (That computer is called a server).
To summarize:
-
Networks classified by region: divided based on different references and types -
LAN: a company, a family, a school… -
MAN: a region, a city… -
WAN: a country, the whole world…
3. How Internet Protocols Are Distributed and Designed
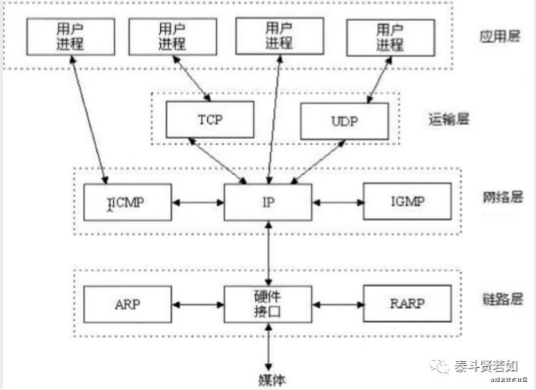
I mentioned the Internet protocol above. Internet protocols are divided into seven layers according to the OSI model and five layers according to the TCP/IP model. As shown in the figure:
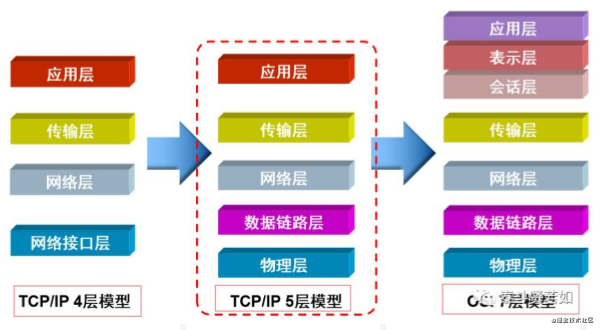
The OSI seven-layer protocol architecture is conceptually clear and theoretically sound, but it is both complex and impractical. The ISO-defined OSI reference model has faced criticism for being too large and complicated. In contrast, the TCP/IP protocol developed by technicians has gained wider application. Therefore, we only need to understand the TCP/IP five-layer protocol to grasp how the underlying communication of computers works.
4. TCP/IP Five-Layer Protocol
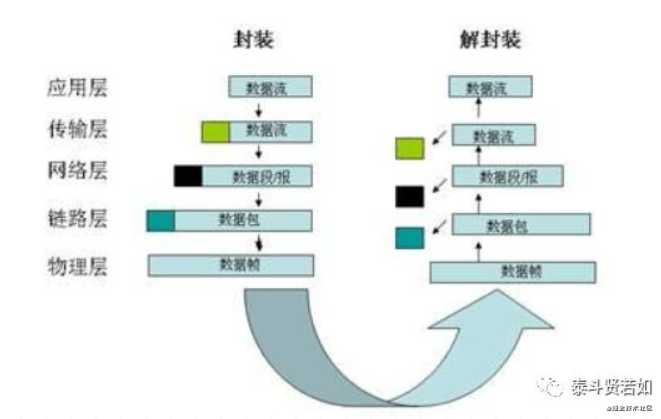
As shown in the figure, from the lowest physical layer to the highest application layer, the most direct for users is the application layer. Each layer depends on the layer below it, so I will start explaining from the lowest layer:
Note: Each layer runs a specific protocol, which together form the Internet protocol.
1. Physical Layer
The physical layer mainly consists of twisted pairs, optical cables, coaxial cables, and radio waves. Its function is simple: to connect different computers and transmit low-level electrical signals, where high voltage represents 1 and low voltage represents 0.
2. Data Link Layer
Receiving or sending pure 0s and 1s from the physical layer is meaningless. Why? Think about it: if I want to send a message to my girlfriend saying, “You are beautiful,” I need to convert that into 0s and 1s and give it to the network card, but the network card will be confused: who should it send it to? So, we must determine the target address. Just like our packages, the outer packaging has both the sender’s and recipient’s addresses, which allows for accurate delivery. Similarly, we need to add the target address to the data we send to ensure it can be received. However, if the data and address are mixed together, it becomes confusing. Therefore, we must segment the data into groups, specifying which bits are the address and which are the data, and everyone must adhere to these rules (protocols). This protocol is called the Ethernet protocol. Before the Ethernet protocol, each company had its own grouping rules; now, they all use the Ethernet protocol.
The Ethernet protocol specifies that a set of electrical signals forms a data packet called a frame, which consists of a header and data.

-
Header: fixed at 18 bytes -
Sender/Source Address: 6 bytes -
Receiver/Destination Address: 6 bytes -
Data Type: 6 bytes Data: minimum 46 bytes, maximum 1500 bytes (the specific content of the data packet)
The address in the Ethernet protocol is called the MAC address, a unique physical address for each computer, which is written on the network card. The Ethernet protocol requires that every device sending and receiving data must have a network card, which is responsible for sending and receiving data. The sending and receiving addresses refer to the network card’s address, i.e., the MAC address.
MAC Address
The MAC address is burned into each network card by manufacturers at the time of production, and this address must be globally unique. The MAC address is represented by 12 hexadecimal digits (the first six digits are the manufacturer’s number, and the last six are the serial number), ensuring no conflicts between different manufacturers.
Switch
Let me introduce something here. When two computers want to communicate, they need to connect a cable. However, if there are many computers, the number of cables connecting them becomes overwhelming. This is where the switch comes in; it is responsible for forming the local area network and studies MAC addresses. You can see its function in the interfaces shown in the picture below.

With the MAC address, the Ethernet can work. In theory, we can communicate with every computer connected to the Internet. At this point, the communication method is called broadcasting.
Broadcasting
What is broadcasting? It is a very primitive communication method, essentially shouting. If you want to propose to your girlfriend, you might shout, “xxx, marry me,” and many people nearby will hear it, but only your girlfriend will respond. That’s how broadcasting works. First, you organize a data packet and send it out as an electrical signal, and everyone on the network will receive this data. They will check if the data is for them; if not, they ignore it, but if it is, they accept it. Although this method is inefficient, it does allow communication.
What problems can broadcasting cause? If it’s in a small network environment, like a few people in a dormitory playing CS, it’s fine; you shout, and your roommates can respond, albeit with low efficiency. But if you connect to the entire Internet and communicate via broadcasting, it becomes a communication disaster. With over 6 billion people in the world, if everyone shouts one message, each person would receive over 6 billion messages, instantly paralyzing the network. This problem is called a broadcast storm. How can we solve this?
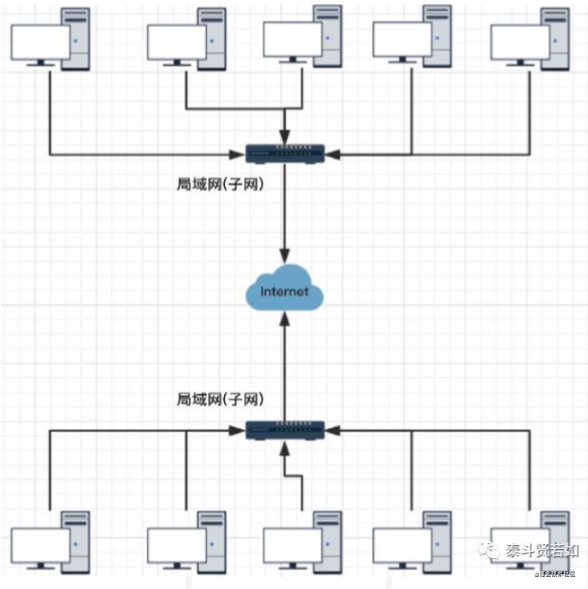
First, we need to understand that the global network (WAN) is composed of many isolated small local area networks (subnets). Different LANs are connected using routers.
Router
The switch mentioned above is responsible for forming the LAN and studies MAC addresses, while the router is responsible for forming the WAN and studies IP addresses, which I will explain next.

Broadcasting can only occur within a LAN; it cannot be done on a large network. Routers prevent broadcast storms. Each LAN is called a broadcast domain, and communication between LANs is done through routers (sending data packets to different broadcast domains/subnets), using routers to divide all computers in a LAN into subnets.
Now, let’s think about it: if we use broadcasting to send a message, it’s like being in a classroom during a lecture and wanting to pass a note to a girl. You would write both your name and the girl’s name on the note, fold it up, and ask classmates to pass it along. Each classmate would check the name on the outside and continue passing it until it reaches the girl whose name is written on it. The classroom is like a LAN. Now, if you want to communicate between different LANs, say, from Qinghai to Henan, you can’t use broadcasting; you must use express delivery. Qinghai, Henan, and many other provinces are parts of the country, which can be seen as individual LANs, while the country itself represents the WAN. How are different LANs divided? The MAC address cannot distinguish them because it only has the manufacturer’s serial number. This introduces the network layer, which uses a new address to distinguish different LANs/subnets, known as the network address.
The protocol that defines the network address is called the IP protocol, which defines the address as the IP address. It is similar to the names of provinces in our country. Continuing with the express delivery analogy, you must package the item and write both your address and province’s address, as well as your friend’s address and province’s address, and give it to the Qinghai delivery company. Then the Qinghai delivery company passes it to the Henan delivery company, which finally delivers it to your friend. There are two points to note:
-
You must write two addresses: your address (MAC address) and the province’s address (IP address) to determine the exact location of the sender and receiver. -
The Qinghai and Henan delivery companies are equivalent to routers.
Subnet Mask
Let me explain subnet masks. Now that we have both IP and MAC addresses, we can communicate between any computers. However, if I want to communicate with another computer, I need to determine whether it’s in the same IP address range as mine, similar to whether I’m in the same province as my friend. This is where the subnet mask comes in. I take my IP address and the other party’s subnet mask to calculate whether they are in the same IP range. If they are, I can communicate via broadcasting; if not, I can send the data to my router, which will forward it to the other router, and finally, the data will reach the receiving computer. This should clarify things.
IP Address
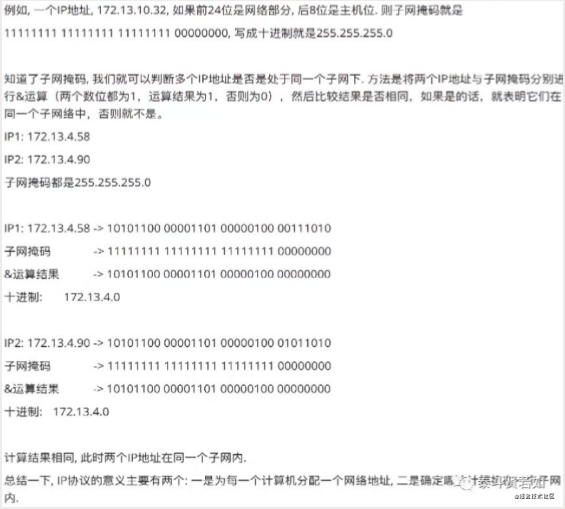
Currently, we commonly use IPv4, which specifies that a network address consists of 32 bits, divided into four parts, each 8 bits long. The maximum value each part can represent is 255, so the range of IP addresses is 0.0.0.0 to 255.255.255.255.
An IP address consists of two parts: the network part and the host part.
The network part identifies different subnets, while the host part identifies the number of hosts within the subnet.
Why are there two parts? It’s simple: imagine you want to send a letter to your girlfriend. If her address is 128 Ping An Road, Xining City, the network part will direct it to Xining City, while the host part will help you find your girlfriend.
How are the network and host parts divided? This is done using the subnet mask, which is also represented by a 32-bit binary number, divided into network and host parts, with the network part consisting of 1s and the host part consisting of 0s.
Now that we’ve covered so much, how does the IP protocol send data? The protocol specifies that the IP protocol uses IP packets for data transmission. IP packets also divide data into two parts: header and data, and when sending data, it directly loads the Ethernet data into the data part of the IP packet.

Header: length from 20 to 600 bytes
Data: maximum 65515 bytes
Since the Ethernet data packet’s data part has a maximum length of 1500 bytes, if an IP packet exceeds 1500 bytes, it must be split into several Ethernet packets for separate transmission.
To recap, the Ethernet header contains both the sender’s MAC address and the target MAC address. How do we find the target MAC address? The predecessors developed a protocol called ARP to resolve the target MAC address. How does it work? First, it is part of the data link layer. When we send a data packet, it contains the recipient’s IP address. For example, if I (172.13.4.58) want to send data to my girlfriend (172.13.4.90), I first need her MAC address to communicate. At this point, we will calculate whether we are in the same subnet (using the subnet mask).
If we are in the same subnet, we broadcast a data packet.
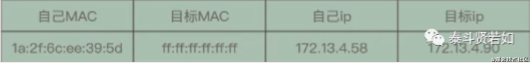
The computers in the subnet will discover this packet and return a packet containing the MAC address, thus finding the target host’s MAC address through the IP address, allowing data transmission to proceed.
If we are not in the same subnet, simply using broadcasting will not work, as broadcasting is only for the internal network. What to do then? At this point, the data packet will be sent to the gateway, which will forward it to other routers, allowing the entire WWW to find the MAC address of the desired computer.
Summary
-
ARP is a fixed protocol for finding MAC addresses using IP addresses; it is part of the data link layer. -
The significance of the network layer: it defines subnets and distinguishes between different LANs. -
IP Address: network address. -
Subnet Mask: used to determine if two devices are in the same subnet.
5. Transport Layer
Up to this point, the first three layers are capable of data transmission. However, a single computer can run multiple network applications simultaneously, such as QQ, WeChat, and LOL, all requiring network transmission. The previous three layers cannot distinguish which data is for which application. So, we introduce the fourth layer, the transport layer, which defines the concept of ports. Each network application occupies a network port, isolating data for different applications so that they do not interfere with each other.
-
Port: the association number between an application and the network card. -
Transport Layer: establishes communication from port to port. -
There are two protocols at the transport layer: TCP and UDP.
TCP Protocol
TCP protocol: reliable transmission; TCP packets have no length limit and can theoretically be infinite, but to ensure network efficiency, the length of TCP packets usually does not exceed that of IP packets to avoid fragmentation.

The TCP header mainly contains the source and destination ports.
UDP Protocol
UDP protocol: unreliable transmission; the header is only 8 bytes long, with a total length not exceeding 65535 bytes, which fits perfectly into an IP packet.

It’s similar to mailing a letter: you write the address and recipient’s name, put it in an envelope, and drop it in the mailbox without worrying about when or if the recipient receives it.
6. Application Layer
Users interact with application programs, all of which operate at the application layer. Everyone can develop their own applications, and data can come in various forms, so it’s essential to establish a data organization format. For users, the application layer is the most intuitive.
Application Layer: defines the data format for application programs.
Example: The TCP protocol can transmit data for various programs, such as Email, WWW, FTP, etc., so different protocols must define the data formats for emails, web pages, and FTP data, and these application protocols make up the application layer.
Summary
The above is an interpretation of the TCP/IP five-layer protocol. To summarize:
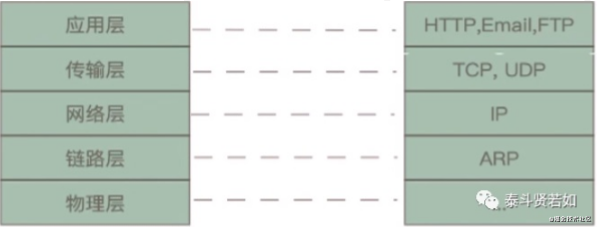
Sending data is essentially a process of encapsulating data.
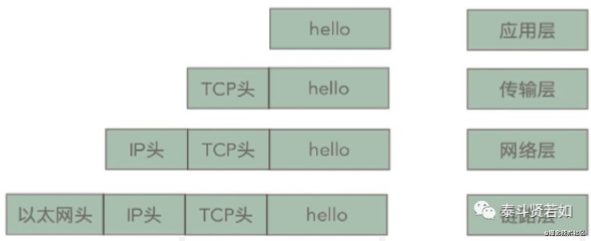
Finally, the data is sent from the physical layer, and upon receipt, the recipient opens it layer by layer to retrieve the data. The above content outlines the general process of network transmission, although many details have not been elaborated. However, understanding the above content is sufficient for development.
I highly recommend a quality content sharing architecture + algorithms. If you haven't followed yet, please long press to follow:
Long press to subscribe for more exciting content ▼
If you find this helpful, please give it a thumbs up. Thank you sincerely.