Summary of Chapter Key Points, Please Click Below 👇
[Adult Higher Education Preparation] Key Points for Chapter One of Computer Fundamentals
[Adult Higher Education Preparation] Key Points for Chapter Two of Computer Fundamentals
[Adult Higher Education Preparation] Key Points for Chapter Three of Computer Fundamentals
[Adult Higher Education Preparation] Key Points for Chapter Four of Computer Fundamentals
Part Five: Computer Networks
Knowledge Point 1: Overview of Computer Networks
1. Definition of Computer Networks
A group of independent functional computers interconnected through communication devices and transmission media, supported by communication software, to achieve resource sharing, information exchange, or collaborative work among computers.
Computer networks are the product of the close integration of computer technology and communication technology.
Knowledge Point 2: Development History of Computer Networks
1. The first generation of computer networks focused on data communication.
2. The second generation of computer networks focused on resource sharing.
A typical representative of this stage is the ARPANET developed by the U.S. Department of Defense’s Advanced Research Projects Agency (ARPA), which is also the earliest origin of the Internet.
3. The third generation of computer networks focused on system standardization.
4. The fourth generation of computer networks is centered around the Internet.
The predecessor of computer networks is the ARPANET created by the U.S. Department of Defense in 1969.
The birth of computer networks: ARPANET (1969).
Knowledge Point 3: Development Trends of Computer Networks
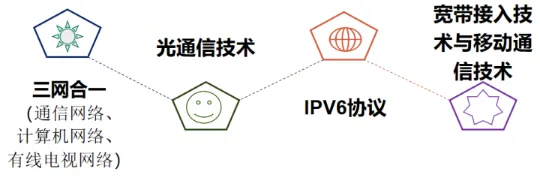
1. Integration of Three Networks
Communication networks, computer networks, and cable television networks are gradually evolving into a unified IP network, known as the integration of the three networks.
2. Optical Communication Technology
With the development of optical devices, various optical multiplexing technologies, and optical network protocols, the capacity of optical transmission systems has increased from Mb/s to Tb/s, a nearly 100,000-fold increase.
The development of optical communication technology has two main directions: one is the development of backbone transmission towards high-speed, large-capacity optical transmission networks, ultimately achieving all-optical networks; the other is the development of access networks towards low cost, integrated access, and broadband optical fiber access networks, ultimately achieving fiber to the home and fiber to the desktop.
3. IPv6 Protocol
The TCP/IP protocol suite is one of the cornerstones of the Internet. The currently widely used version of the IP protocol is IPv4, which has a 32-bit address length, theoretically allowing for about 4 billion (232) addresses. As Internet applications become more widespread and network technology continues to develop, IPv4 issues are becoming increasingly evident, primarily due to address resource exhaustion, rapid expansion of routing tables, and insufficient support for network security and multimedia applications. IPv6, as the next-generation IP protocol, adopts a 128-bit address length, theoretically allowing for about 2128 (3.402823*1038) addresses.
4. Broadband Access Technology and Mobile Communication Technology
(1) Frequency
In physics, frequency is the number of vibrations completed per unit time, describing the frequency of an object’s oscillation. In signal communication, frequency often measures the number of pulses that occur in a unit time for periodic cyclic signals. Frequency is commonly represented by the symbol f or v, with the unit of Hertz (Hz). Common unit conversions are: 1 kHz = 1000 Hz, 1 MHz = 1000 kHz, 1 GHz = 1000 MHz.
(2) Data Communication System
A data communication system enables the transmission of information, and a complete data communication system can be divided into three main components:
① Source (source system: sending end, sender)
② Channel (transmission system: transmission network)
③ Destination (destination system: receiving end, receiver)
(3) Channel Bandwidth
The channel refers to the path for transmitting signals in a communication system, including communication lines and transmission devices. Channels can be classified based on the transmission medium used into wired channels and wireless channels; based on the type of signal suitable for transmission, they can be classified into analog channels and digital channels.
Knowledge Point 4: Components of Computer Networks
1. Physically, computer networks consist of computer systems, network nodes, and communication links. Computer systems perform various data processing. Communication links and network nodes provide communication functions.
Communication lines, also known as transmission media (network transmission media), can be classified into wired transmission media and wireless transmission media based on their forms.
(1) Wired Transmission Media: Mature technology, stable performance, and relatively low cost, currently the most commonly used media in local area networks. Wired transmission media mainly include twisted pair, coaxial cable, and fiber optics.
① Twisted Pair:
Two insulated copper wires twisted together. The higher the number of twists per unit length, the stronger the ability to cancel interference.
② Coaxial Cable:
Coaxial cable consists of an inner conductor copper core, an insulating layer, a woven outer conductor shielding layer, and a plastic protective layer. Due to the shielding layer, coaxial cables have good anti-interference capability.
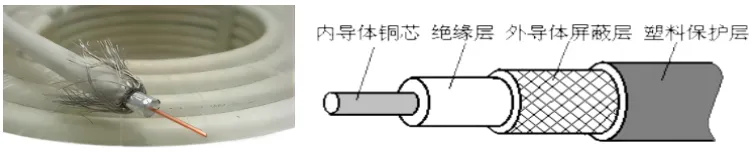
③ Fiber Optics:
Fiber optics are made from very transparent quartz glass drawn into thin strands, using the principle of total internal reflection for signal transmission.

Advantages of Fiber Optics:Fast transmission speed, long transmission distance, strong anti-interference capability, low attenuation, small size, and light weight.
Disadvantages of Fiber Optics:High cost, and difficulty in installation and connection.
(2) Wireless Transmission Media:Radio waves, infrared, satellite communication, microwave communication, laser
2. Communication Devices (Network Connection Devices)
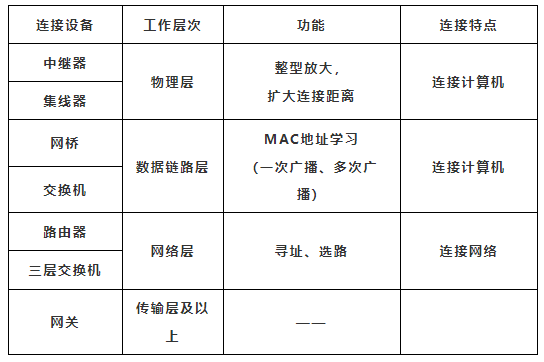
Communication devices include repeaters, routers, bridges, gateways, hubs, network cards, and modems.
(1) Repeater:
Any medium has a limited effective transmission distance; electrical signals naturally attenuate and add noise after transmitting a certain distance in the medium.
The function of a repeater is to amplify digital signals and transmit tasks, thereby increasing the effective transmission distance.
Repeaters belong to physical layer devices.

(2) Router:
Belongs to inter-network connection devices, which connect two or more networks and have functions for path selection, network address determination, and congestion control.

(3) Bridge:
A bridge is an early two-port layer 2 network device. It is a storage/forwarding device that connects two local area networks, expanding the maximum transmission distance of the network by connecting independent network segments and achieving interconnection at the data link layer (same type of network).

(4) Gateway (Protocol Converter):
The gateway is mainly used to connect networks with different structures or local area networks with hosts, and can be used for both wide area network interconnection and local area network interconnection. A gateway is a computer system or device that serves as a conversion hub.

(5) Hub:
The main function of a hub is to regenerate, reshape, and amplify received signals to extend the transmission distance of the network while concentrating all nodes around it.

(6) Network Card (Network Adapter, Network Interface Card):
It is a hardware device that connects computers to networks, an essential device for networking. The network card provides a fixed network address (MAC address) and receives data sent over the network.
It transmits data from the local machine to the network through a network cable.
Every network card has a unique global MAC address, which distinguishes the origin and destination of data transmission.
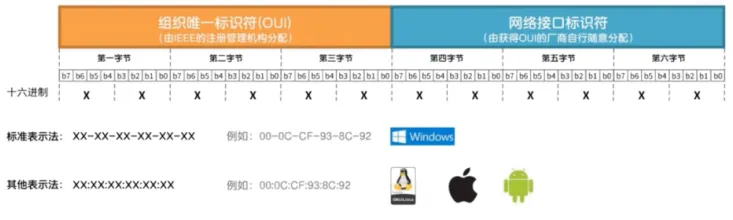
(7) Modem:
Digital signals are modulated into analog signals, and analog signals are demodulated back into digital signals.

Summary:
Knowledge Point 5: Functions of Computer Networks
1. Data Communication
Data communication is one of the basic functions of computer networks, used to facilitate the transmission of information between computers.
2. Resource Sharing
Computer resources mainly refer to the hardware, software, and data resources of computers. Resource sharing is the most important function of computer networks, especially data resources, as hardware and software can be purchased or developed, while data loss is often irretrievable.
3. Distributed Processing
Tasks are distributed to different computers in the network to achieve balanced use of network resources and implement distributed processing, such as pre-sale of train and plane tickets at multiple locations. (Load balancing)
4. Improving System Reliability
Computers can significantly enhance reliability through redundant components in the network, especially using virtualization technology.
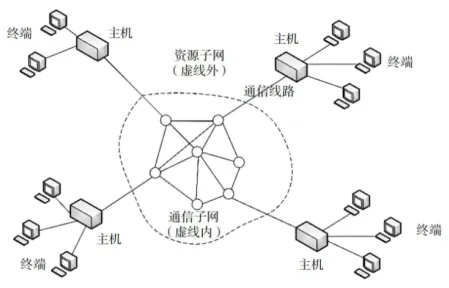
From a logical function perspective, computer networks can be divided into communication subnetworks and resource subnetworks.
The communication subnetwork provides the communication functions of computer networks, consisting of network nodes and communication links. The resource subnetwork provides the capability to access networks and process data, consisting of hosts, terminal controllers, and terminals.
1. Classification Based on Coverage Area
(1) Local Area Network (LAN): Generally connects microcomputers via high-speed communication lines, covering an area from hundreds of meters to several kilometers, typically used to connect a room, a floor, or a building.
Characteristics: small coverage area, high transmission rate, low error rate, high reliability, low cost.
(2) Metropolitan Area Network (MAN): A computer communication network established within the confines of a city, typically using technology similar to that of local area networks, but differing in medium access control methods. It generally connects hosts, databases, and LANs at different locations within the same city.
(3) Wide Area Network (WAN): Used to connect LANs or WANs between different cities. Wide Area Networks can cover a region or a country.
Characteristics: low transmission rate, high transmission error rate, but with the construction of fiber optic communication networks, the speed of wide area networks has greatly improved.
(4) Internet: The largest wide area network, which interconnects wide area networks, local area networks, etc., around the world, enabling global data communication and resource sharing.
2. Classification Based on Network Topology
Computer networks can be classified based on topology into bus topology, ring topology, star topology, tree topology, and mesh topology. Bus topology, ring topology, and star topology are commonly used in local area networks, while tree topology is often used in metropolitan area networks, and mesh topology is commonly used in wide area networks.
(1) Bus Topology (high dependency on the bus) (LAN)
Any message sent by a host spreads along the bus in two directions.
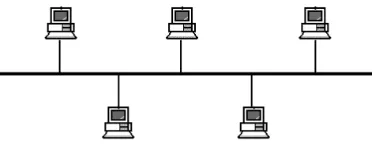
Advantages:
① Simple structure, easy to install, expand, and remove nodes.
② A single node failure has little impact on the network.
③ High channel utilization.
Disadvantages:
① Bus failure affects network communication.
② Signal delay is uncertain.
③ Difficult fault diagnosis, requiring segmented diagnosis.
(2) Ring Topology
A single closed loop formed by several nodes and links. In a ring topology structure, information is transmitted along the loop in one direction.
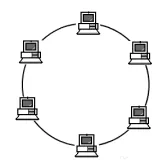
Advantages:
① Easy to install and monitor, simple transmission control mechanism.
② Fast transmission speed, easy to control in real-time.
③ Each node is equal.
Disadvantages:
① Reliability is poor, adding or removing nodes is inconvenient.
② Poor scalability; adding or deleting nodes can disrupt data being transmitted.
(3) Star Topology
Characteristics: central node, centralized control.
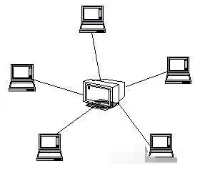
Advantages:
① Easy installation and simple control.
② A single node failure does not affect overall network communication.
③ Data transmission does not cause conflicts.
Disadvantages:
① The reliability depends on the central node.
② Total length of lines is high, resulting in high costs.
③ A failure in the central node can lead to network paralysis.
(4) Tree Topology (high dependency on the root node) (LAN/WAN)
Tree topology evolved from bus topology, where any node sends information to the root node, which then returns to the entire network.
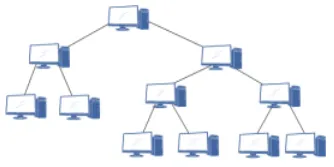
Advantages:
① Easy to expand.
② Easy to isolate faults.
Disadvantages:
① High dependency on the root node.
(5) Mesh Topology (at least two paths between every two nodes) (WAN)
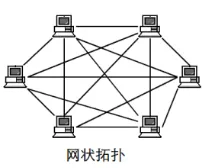
Advantages:
① High reliability.
② Resource sharing is easy.
Disadvantages:
① Long lines, high hardware costs.
② Complex management and path selection.
3. Classification Based on Transmission Medium
Computer networks can be classified into wired networks and wireless networks based on the transmission medium. Wired networks use twisted pairs, coaxial cables, fiber optics, or telephone lines as transmission media. Wireless networks primarily use radio waves or infrared as transmission media.
4. Classification Based on Network Usage Nature
Divided into public networks and private networks. Public networks are paid networks, operated by telecom departments or other communication service providers, where any unit or individual can pay to rent data communication. Private networks are established by a department based on its specific business needs, generally not providing external services. For example, networks for military, government, banking, and power systems are considered private networks.
Summary:
5. Performance Indicators of Computer Networks
(1) Rate: Refers to the data transmission rate, also known as bit rate, which indicates the number of binary digits transmitted by a data communication system per second, with units in bit/s or bps. Common rate units include: bps, Kbps, Mbps, Gbps, etc.
Knowledge Point 7: Composition of the Internet and Common Technical Terms
1. Composition of the Internet
The Internet is structured in layers, consisting of physical networks, protocols, application software, and information.
(1) Physical Networks
Physical networks consist of various network interconnection devices, communication lines, and computers.
(2) Protocols
Information transmitted over the Internet must adhere to at least three protocols: Internet Protocol, Transmission Protocol, and Application Protocol.
(3) Application Software
In practice, specific application software interacts with the Internet.
(4) Information
The purpose of building physical networks (building roads), establishing protocols (traffic rules), and using various application software (vehicles) is to transmit information (transport goods).
2. Common Technical Terms of the Internet
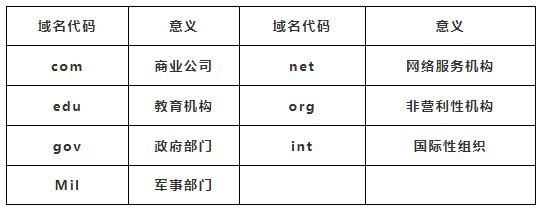
(1) ISP: Internet Service Provider, primarily provides users with dial-up internet access, WWW browsing, FTP, sending and receiving emails, BBS, Telnet, and various other services.
(2) PPP Protocol: Point-to-Point Protocol, the protocol supported when a modem connects to an ISP.
(3) DNS: Domain Name Server, a necessary route for any site on the Internet, akin to a signpost. When configuring Internet software, it’s essential to correctly input the DNS IP address provided by the ISP.
(4) Blog: Blog or Weblog, derived from “Web log”, is a very simple, user-friendly way of publishing personal information.
Knowledge Point 8: IP Addresses and Domain Name System
1. IP Address
(1) Definition of IP Address
An IP address is a unique 32-bit binary address assigned to each computer connected to the Internet, also known as an Internet address.
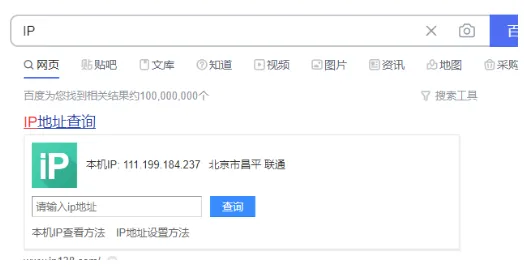
(2) IP Address Format: Dotted Decimal. Consists of 32 bits, divided into 4 groups, each group containing 8 bits, with each group ranging from 0-255, separated by dots.
Dotted decimal example: 111.199.184.237
Binary representation: 1101111.11000111.10111000.11101101
(3) Correct Format of IP Address
① Must consist of 4 octets.
② Must be separated by dots.
③ Each octet must be in the range of 0-255.
(4) An IP address consists of a network number (network address) and a host number (host address).
(5) Classification of IP Addresses:
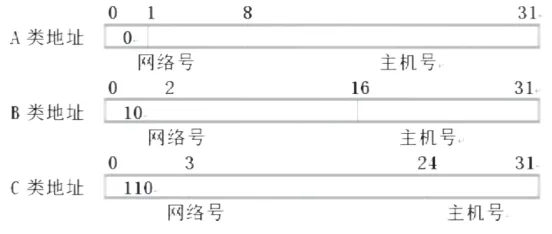
Class A: The first 8 bits represent the network number, and the last 24 bits represent the host number. The network number range is 0-127, but since the all-zero and all-one network numbers are used for special purposes, the Class A IP address network number range is 1-126. Class A IP addresses are typically used for large networks. Each Class A network can have 16,777,214 hosts.
Class B: The first 16 bits identify the network number, and the remaining 16 bits identify the host number, with the first two bits being “10”. The range of the first 8 bits is 128-191. Suitable for medium-sized networks, each Class B network can have 65,534 hosts.
Class C: The first 24 bits identify the network number, and the remaining 8 bits identify the host number, with the first three bits being “110”. The range of the first 8 bits for Class C IP addresses is 192-223. Class C IP addresses are typically used for small networks such as campus networks, with each Class C network able to support 254 hosts.
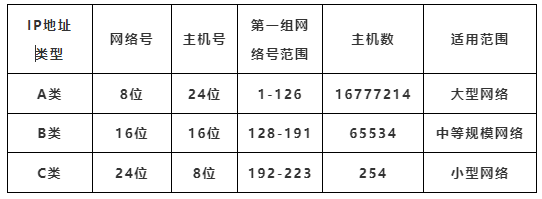
(6) Special IP Addresses: Addresses that cannot be used by ordinary hosts.
① Network Address: Used to represent the network itself, with the network number remaining constant and the host number being all zeros.
② Broadcast Address: Used to broadcast to all devices in the network, with the network number remaining constant and the host number being all ones. An IP address with all 32 bits set to 1 (i.e., 255.255.255.255) is a limited broadcast address used for local broadcasts.
③ Loopback Address: Network addresses cannot start with the decimal number 127, as the number 127 is reserved for system diagnostics, known as the loopback address. The common loopback address for a host to test itself is 127.0.0.1.
④ Private Address: IP addresses that can only be used within a local area network and cannot be used on the Internet are called private IP addresses. IP addresses used on the Internet are known as public addresses.
Class A private addresses (10.0.0.0~10.255.255.255)
Class B private addresses (172.16.0.0~172.31.255.255)
Class C private addresses (192.168.0.0~192.168.255.255)
2. Subnet Mask
(1) Meaning of Subnet Mask
The subnet mask represents the network number with all 1s and the host number with all 0s. The subnet mask cannot exist independently; it must be used in conjunction with an IP address.
Subnet mask for Class A addresses: 255.0.0.0
Subnet mask for Class B addresses: 255.255.0.0
Subnet mask for Class C addresses: 255.255.255.0
(2) Functions of Subnet Mask
① Divides the network to increase the number of networks.
To facilitate management, A, B, and C class networks can be divided into smaller networks.
② Determines the location of the host.
When two hosts communicate, the subnet mask can be used to determine if they are on the same network. If they are, the information is transmitted within the network; if not, the information is routed.
The subnet mask is the basis for determining whether any two computers’ IP addresses belong to the same subnet. The simplest understanding is that if the IP addresses of two computers are ANDed with the subnet mask and the result is the same, it indicates that the two computers are in the same subnet and can communicate directly.
3. IPv6
IPv4 uses a 32-bit address length, providing only about 4.3 billion addresses. By February 2010, less than 10% remained. IPv6 uses a 128-bit address length, offering an almost unlimited number of addresses. Conservatively estimated, IPv6 can provide about 1000 addresses for every square meter of the Earth’s surface.
(1) Advantages of IPv6:
① Larger scale: IPv6 has a larger address space and network scale, with more types and numbers of terminals connecting to the network and broader network applications.
② Faster speed: End-to-end high-performance communication exceeding 100Mb/s.
③ More secure and reliable: Object recognition, identity authentication, access authorization, data encryption and integrity, trusted networks.
④ More timely: Multicast services, quality of service (QoS), large-scale real-time interactive applications.
⑤ More convenient: Rich applications based on mobile and wireless communications.
⑥ More manageable: Ordered management, effective operations, timely maintenance.
⑦ More effective: Profitable models yielding significant social and economic benefits.
4. Regulations of the Internet Domain Name System
(1) Concept: To facilitate users, the Internet provides a user-oriented character-based host naming mechanism based on IP addresses, known as the domain name system, which is a more advanced address format. Since numeric IP addresses are inconvenient for users to remember and use, and do not indicate the owner’s organization name or nature.
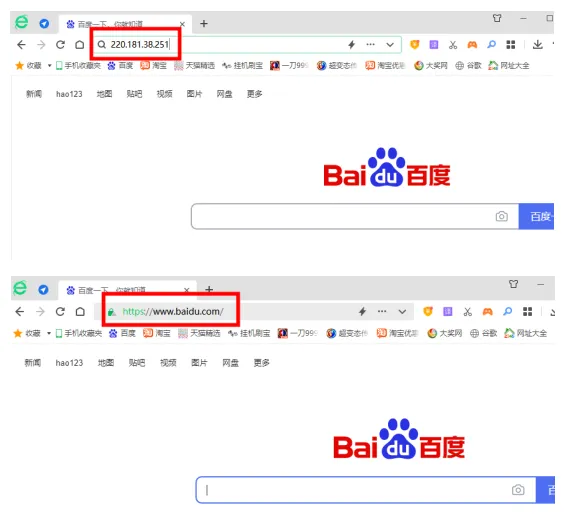
(2) Naming Rules for Domain Names:Hierarchical Naming Method (www.baidu.com)
A complete domain name can consist of up to five parts, separated by “.“. The rightmost subdomain is the highest level (top-level domain), while the leftmost subdomain is the lowest level.
(3) The naming format of the Internet domain structure is as follows:
Host Name.Unit Name.Unit Nature Type.Country Code (www.sub.edu.cn)
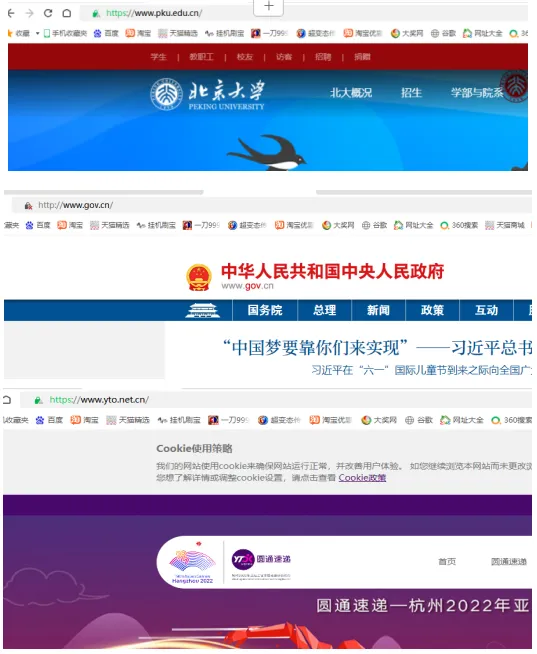

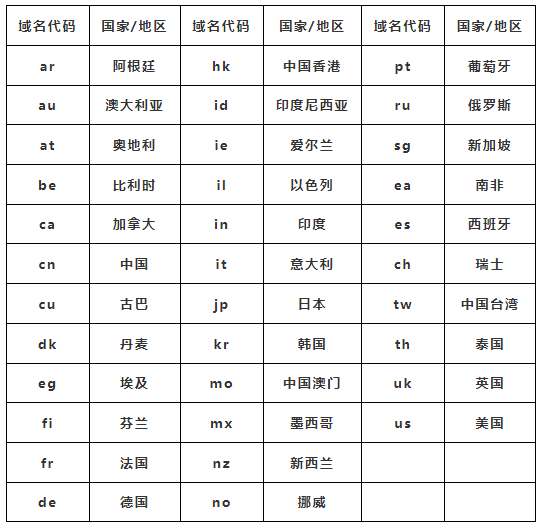
(3) Correspondence of Domain Names:
One IP address can correspond to multiple domain names
One domain name corresponds to one IP address
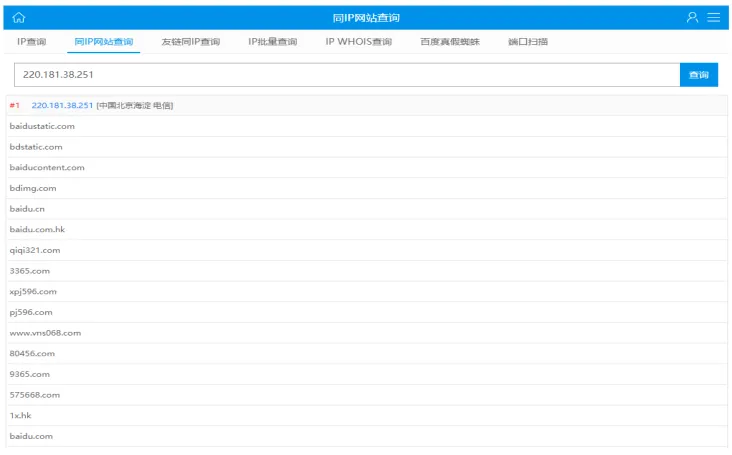
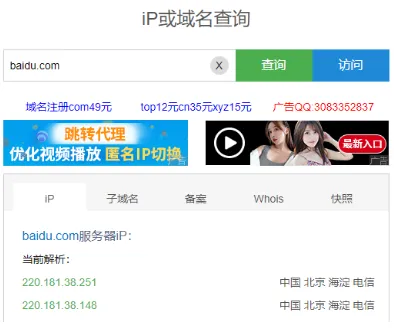
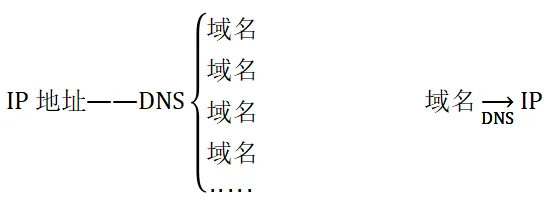
(4) The Role of DNS Domain Name Servers:Translate domain names into IP addresses.
DNS stores a mapping table of IP addresses and domain names. When accessing a computer, both IP addresses and domain names can be used.
For any questions regarding education, add WeChat for consultation 👇


Educational Advancement

end