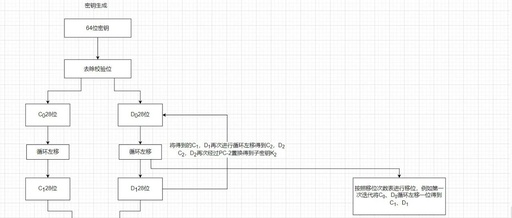
C# DES Algorithm Encryption: The Glory and Challenges of Classic Encryption
Introduction Hello everyone! If you are interested in encryption algorithms, then the DES algorithm is certainly a topic you cannot avoid. DES is like the classic sports car of the encryption world—debuting in 1977, it once enjoyed great popularity. Although it is no longer the safest choice today, DES remains a very interesting and useful … Read more