Operating Systems in Embedded Systems
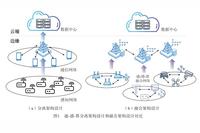
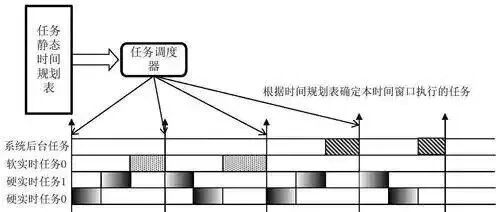
Concepts and Characteristics of Embedded Systems Embedded Systems are specialized computer systems that are embedded within larger devices or systems to perform specific functions. In Internet of Things (IoT) systems, embedded systems act like neural nodes, playing a crucial role in various fields such as smart homes, industrial control, smart energy, intelligent transportation, and smart … Read more