Notes on Learning the DES Algorithm
DES (Data Encryption Standard) is a classic symmetric encryption algorithm developed by IBM and adopted by the U.S. National Bureau of Standards in 1977. It uses a fixed-length 56-bit key to encrypt 64-bit data blocks, transforming plaintext into ciphertext through a series of complex permutations and substitutions.
This is for educational purposes only; if there is any infringement, it will be deleted immediately.
1. Basic Principles
DES is a block cipher in symmetric key algorithms, with a key length of 64 bits, of which 56 bits are used in operations, including 8 parity bits, which are 8, 16, 24, 32, 48, 56, and 64.
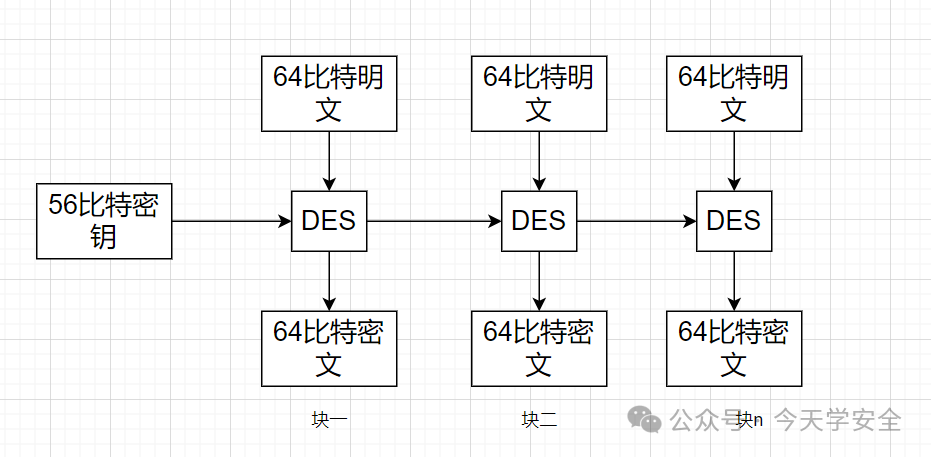
During encryption, plaintext is divided into n 64-bit data blocks, which are then encrypted, and the resulting n ciphertext blocks are concatenated to form the final ciphertext, as shown in the figure:
2. Encryption Process
The plaintext undergoes an IP (Initial Permutation), dividing the 64 bits into two 32-bit halves, followed by the F-function operation to obtain two 32-bit outputs, which are then subjected to the inverse IP to produce the nth ciphertext block, as shown in the figure:
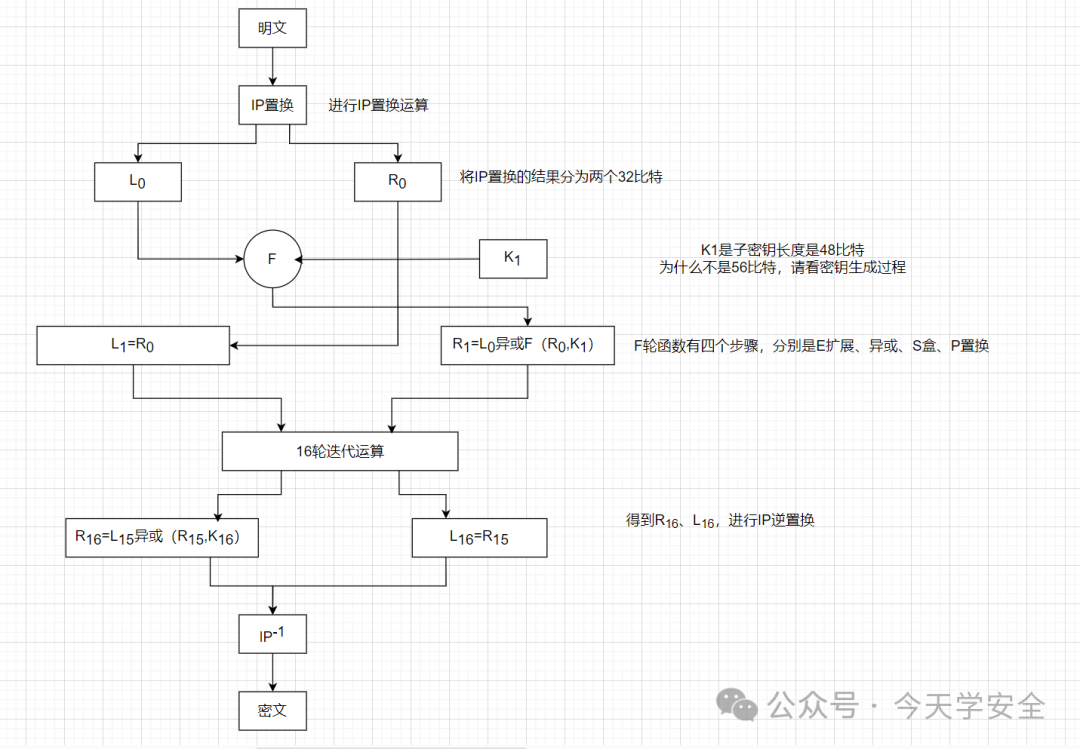
The following will explain the IP, F-function (E expansion, S-box, P permutation) without detailing the XOR operations.
The length transformation during operations is as follows:
(1)IP Permutation
Rearranging the 64-bit binary according to specific rules.
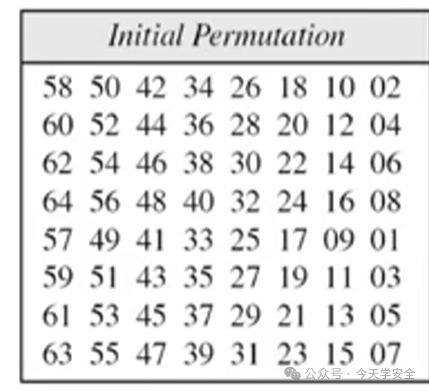
Example: Move the 58th bit to the first position.
(2)Inverse IP Permutation
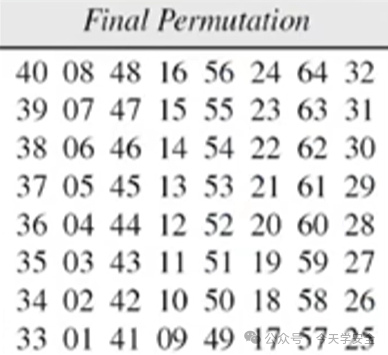 Similar to the IP permutation principle, it is used to scramble the order.
Similar to the IP permutation principle, it is used to scramble the order.
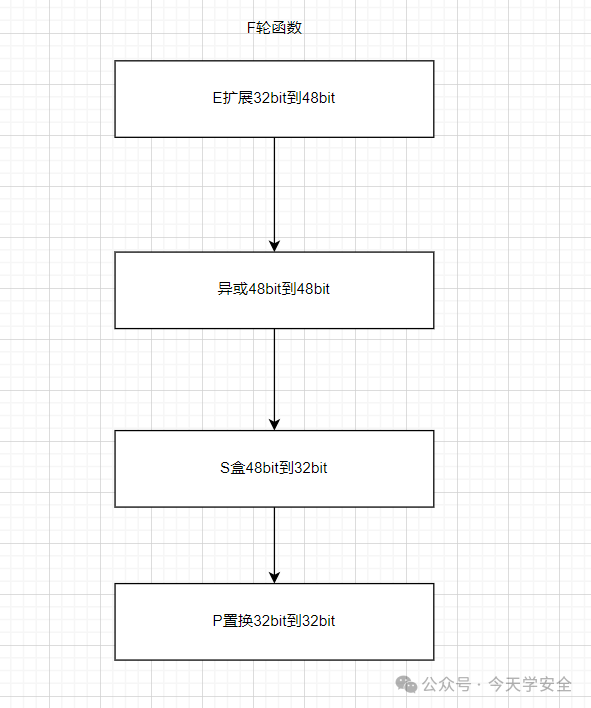
3. F-function
(1) Round Function – E Expansion Permutation
The 64-bit output after IP permutation is divided into two 32-bit halves.
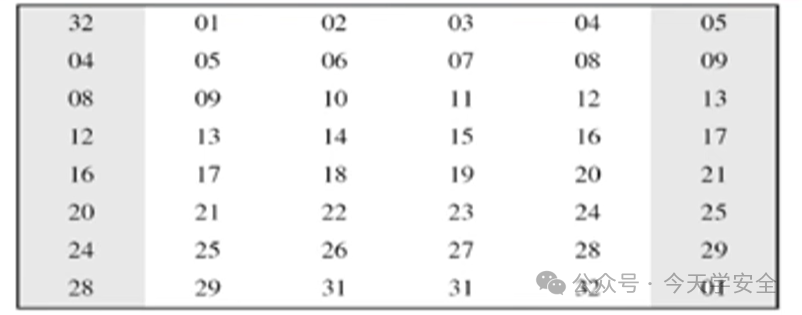
Expanding the 32 bits to 48 bits.
Expansion rules:
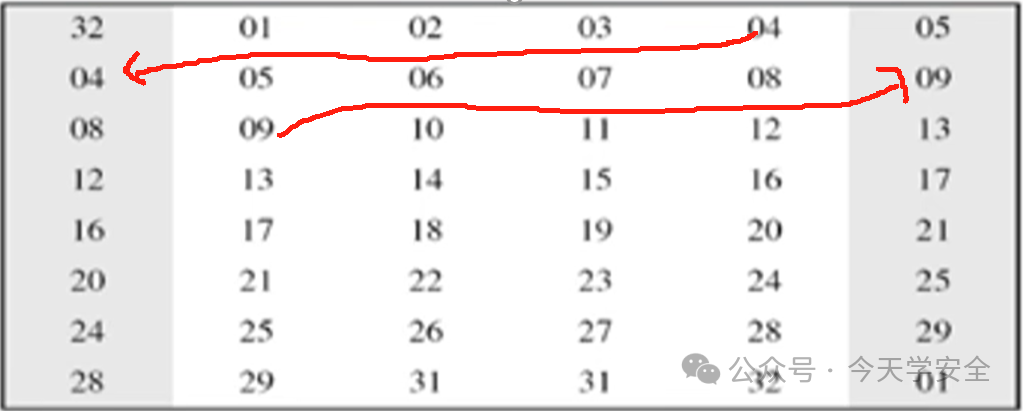
For example, the last bit of the previous row is added to the first position, and the first bit of the next row is added to the last position. This results in 48 bits.
(3)Round Function – S-box Compression Processing
The expanded 48 bits are XORed with the 48-bit key (the reason for 48 bits will be explained later in key generation) and then divided into 8 blocks of 6 bits each, using 8 S-boxes to compress to 32 bits.
For example:
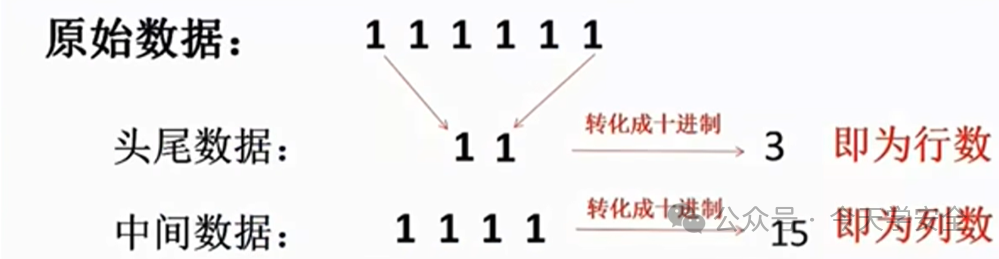
Querying the S-box gives 13, which converts to binary as 1101, thus compressing 6 bits to 4 bits.
(4)Round Function – P-box Permutation
Finally, after the P-box permutation
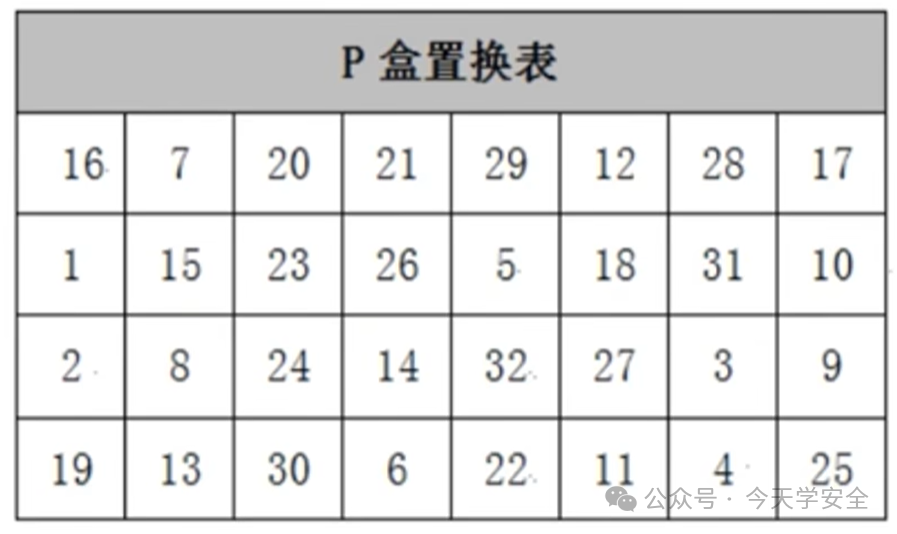
the 16th bit is moved to the first position, and so on.
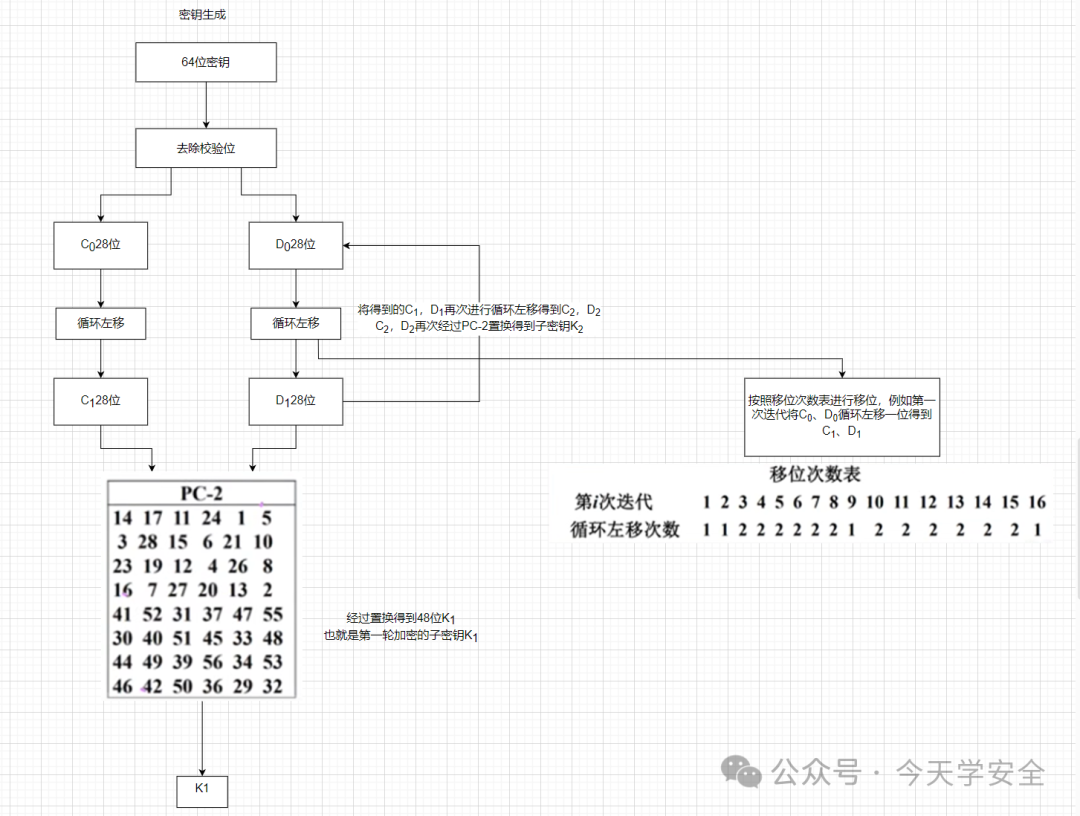
4. Key Generation
The initial key is 64 bits, with 8 parity bits removed, and the binary is sorted according to the table below, which contains no parity bits, thus eliminating them.

The generated 56 bits are divided into C0,D0, then undergo left circular shifts, followed by another permutation to obtain the 32-bit key Ki, which is the subkey in the F-function as shown in the figure: