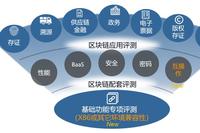
Detailed Explanation of MODBUS Protocol 8: Unlock Advanced Techniques to Optimize Communication Efficiency
Click to follow and never lose your way in learning! On the stage of industrial automation, the application of the MODBUS protocol is like a war without gunpowder, where everyone is pursuing more efficient, stable, and intelligent communication effects. Today, we will dig into the advanced application techniques of the MODBUS protocol, uncovering these “hidden … Read more