Interview Background
Hello everyone, I am Xia Yi. Today I will continue to share my interview experience at Kuaishou, this is the 9th question. Kuaishou First Interview (48min) Experience:
Interviewer: Please introduce yourself briefly.
I: I will briefly outline my work, highlighting the key points (understanding the importance of selection).
Interviewer: Can you talk about a project? What impressed you the most about it?
I: I talked about a recent project because the technology and business aspects are quite clear (key project parts, there will be technical Q&A later).
Interviewer: Can you explain the Raft protocol?
I: At that time, I briefly explained it (for details, please refer to the first article: Kuaishou First Interview: Can You Explain the Raft Protocol? I: I output a lot, and the interviewer nodded, hmm…).
Interviewer: I see you used RPC to call other servers, can you explain why you chose RPC over other technologies? And what is the underlying principle of RPC?
I: (I couldn’t answer at that time) (for details, please refer to the second article: Kuaishou First Interview: Can You Explain Why You Used RPC Instead of Other Technologies? And What is the Underlying Principle of RPC? I: I couldn’t answer at that time, the interviewer: let’s move on to the next question).
Interviewer: No problem, let’s ask some basic questions. I see you wrote that you are familiar with collections, can you introduce one that you are familiar with? (I was hesitant about how to respond) Or can you talk about your understanding of these?
I: … (ArrayList, LinkedList, HashMap) (for details, please refer to the third article: Kuaishou First Interview: Let’s Ask Some Basic Questions, I See You Wrote That You Are Familiar with Collections, Can You Introduce One That You Are Familiar With? I: I was completely confused!).
Interviewer: What happens if the HashMap chain is too long?
I: …(I explained quite a bit at that time and also mentioned why it treeifies and the conditions for treeification) (for details, please refer to the fourth article: Kuaishou First Interview: What Happens If the HashMap Chain is Too Long? And Why Does It Treeify, What Are the Conditions? I: A piece of cake, just a rote question).
Interviewer: I see you wrote that you are familiar with concurrent programming, can you explain ThreadLocal?
I: … I am quite familiar with this. (for details, please refer to the fifth article: Kuaishou First Interview: I See You Wrote That You Are Familiar with Concurrent Programming, Can You Explain ThreadLocal? I: I thought the interviewer was really nice, another easy question).
Interviewer: What are the common methods for creating threads?
I: new Thread() with parameters implementing the Runnable interface, thread pools (actually, there is also inheriting the Thread class and then new) (I was lucky today, another rote question).
(for details, please refer to the sixth article: Kuaishou First Interview: Let’s Continue, What Are the Common Methods for Creating Threads? I: I was lucky today, another rote question).
Interviewer: Can you explain MySQL transactions?
I: … (I explained the concept at that time).
Interviewer: MySQL isolation levels? What is used to solve this?
I: …(I mentioned all four levels and MVCC).
Interviewer: InnoDB defaults to repeatable read, what happens in the case of phantom reads?
I: … (I forgot that repeatable read cannot solve certain cases of phantom reads).
Interviewer: Can you discuss HTTP and HTTPS?
I: … (both are application layer protocols, HTTPS is HTTP with an added TLS protocol, and the three risks of HTTP).
The detailed answer is organized as follows:
01HTTP
- • Definition:
- • HTTP is an application layer protocol used for transmitting hypertext data between clients and servers.
- • It is one of the most commonly used protocols on the internet for communication between browsers and servers.
- • Characteristics:
- • Plaintext Transmission:HTTP data is transmitted in plaintext, meaning that data is not encrypted during transmission, making it vulnerable to man-in-the-middle attacks (MITM), such as eavesdropping and data tampering.
- • Stateless:HTTP is a stateless protocol, meaning each request is independent, and the server does not retain the client’s request state. Each request requires a new connection to be established.
- • Simple and Efficient:The HTTP protocol is simple and easy to implement, suitable for rapid development and deployment.
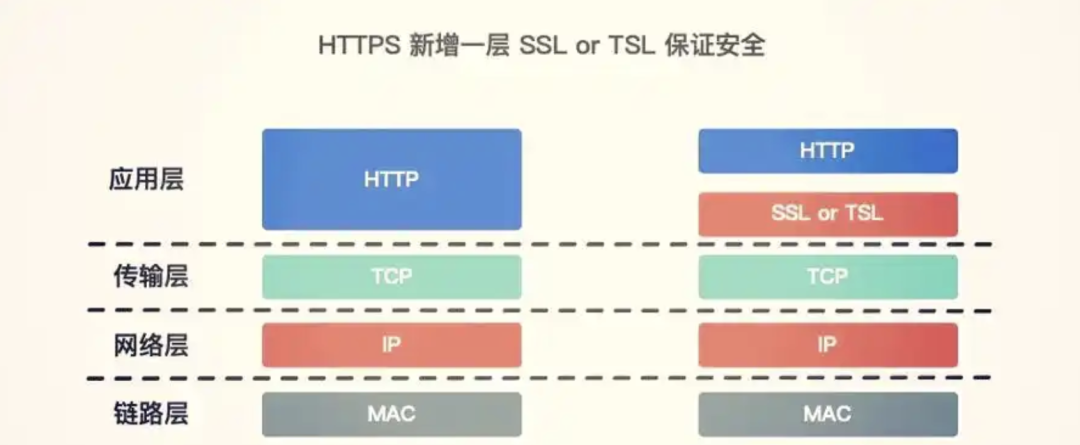
02HTTPS
- • Definition:
- • HTTPS is the secure version of HTTP, which adds the SSL/TLS (Secure Sockets Layer/Transport Layer Security) encryption protocol on top of HTTP.
- • The main purpose of HTTPS is to ensure the security of data during transmission, preventing data from being eavesdropped, tampered with, or forged.
- • Characteristics:
- • Encrypted Transmission:HTTPS uses SSL/TLS to encrypt data, ensuring that data transmitted between the client and server is encrypted. Even if data is intercepted by a man-in-the-middle, its content cannot be decrypted.
- • Authentication:HTTPS verifies the server’s identity through digital certificates (issued by Certificate Authorities, CA), ensuring that the client connects to the real server and not a disguised malicious server.
- • Data Integrity:HTTPS also provides data integrity protection, ensuring that data is not tampered with during transmission.
- • Compatibility:HTTPS is based on HTTP, so it inherits most of HTTP’s features while providing additional security.
03Comparison of HTTP and HTTPS
| Feature | HTTP | HTTPS |
| Encryption | Plaintext transmission, no encryption | Uses SSL/TLS encryption |
| Security | Low, vulnerable to man-in-the-middle attacks | High, prevents eavesdropping, tampering, and forgery |
| Performance | Faster (no encryption overhead) | Slower (encryption and decryption require additional overhead) |
| Port | Default uses port 80 | Default uses port 443 |
| Certificate | No certificate required | Requires SSL/TLS certificate |
| URL Prefix | <span>http://</span> |
<span>https://</span> |
| Application Scope | Suitable for non-sensitive data transmission | Suitable for sensitive data transmission (e.g., login, payment, etc.) |
04Why HTTPS is Necessary
- • Protect User Privacy:HTTPS ensures that user data (such as passwords, credit card information, etc.) transmitted is not stolen.
- • Prevent Data Tampering:HTTPS prevents man-in-the-middle attacks from tampering with data, ensuring data integrity and authenticity.
- • Enhance Trust:Websites using HTTPS are generally considered more secure, and users are more willing to perform actions on these sites.
- • Search Engine Optimization (SEO):Search engines like Google tend to favor websites using HTTPS, which helps improve the website’s search ranking.
05How HTTPS Works
- 1. Certificate Acquisition:
- • Website administrators need to obtain an SSL/TLS certificate from a Certificate Authority (CA).
- • The CA will authenticate the website to ensure its legitimacy.
- • The website administrator installs the certificate on the server.
- • When a client (such as a browser) accesses an HTTPS website, the server sends its SSL/TLS certificate.
- • The client verifies the validity of the certificate (including the certificate authority, expiration time, etc.).
- • If the certificate is valid, the client and server negotiate an encryption key for subsequent encrypted communication.
- • All data transmitted between the client and server is encrypted using the encryption key.
- • Data cannot be intercepted or tampered with by a man-in-the-middle during transmission.
06HTTP/2 and HTTP/3
- • HTTP/2:
- • HTTP/2 is an upgraded version of the HTTP protocol, supporting multiplexing, binary framing, header compression, and other features, significantly improving performance.
- • HTTP/2 is typically used in conjunction with HTTPS, as most browsers only support encrypted HTTP/2.
- • HTTP/3:
- • HTTP/3 is the next generation of HTTP based on the QUIC protocol.
- • QUIC is a transport layer protocol based on UDP, supporting faster connection establishment, more efficient congestion control, and better fault tolerance.
- • HTTP/3 also defaults to encryption, further enhancing security.
07Conclusion
- • HTTP:Suitable for non-sensitive data transmission, simple and efficient, but with low security.
- • HTTPS:Suitable for sensitive data transmission, ensuring data security through encryption and authentication, although performance is slightly lower, security is high.
- • Best Practice:It is recommended that all websites use HTTPS to protect user data and enhance user trust.
Finally
That’s all for today’s sharing, see you in the next article.