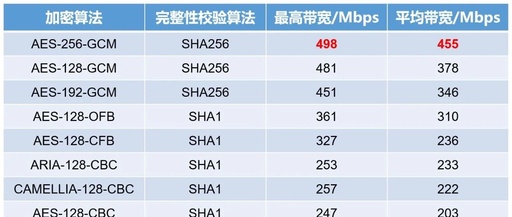
Performance Comparison of Different Encryption Algorithms in OpenVPN
We previously introduced that the forwarding performance of IPsec VPN varies with different encryption algorithms (using vSRX to test the performance differences of various IPsec VPN encryption algorithms), but does OpenVPN have this issue? First, we need to confirm the algorithm information used during the OpenVPN negotiation process. For the default configuration, the algorithm information … Read more