We previously introduced that the forwarding performance of IPsec VPN varies with different encryption algorithms (using vSRX to test the performance differences of various IPsec VPN encryption algorithms), but does OpenVPN have this issue?
First, we need to confirm the algorithm information used during the OpenVPN negotiation process. For the default configuration, the algorithm information is not displayed during the connection process.
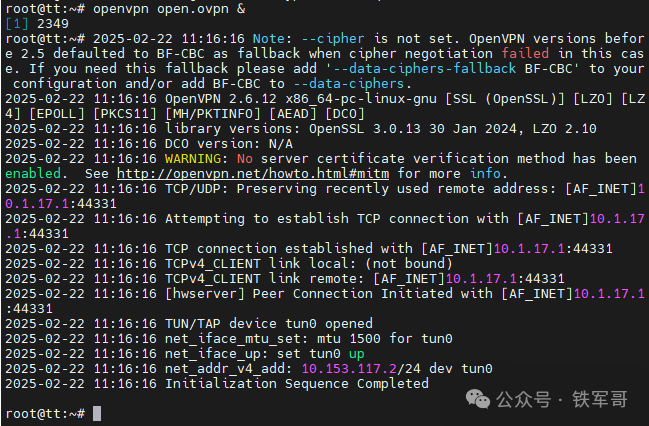
At this point, we can add a line of configuration verb 4 in the configuration file to output negotiation process information.
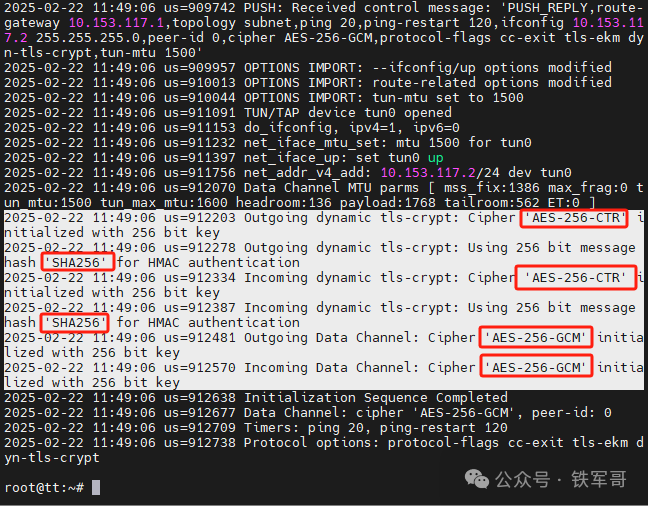
After that, we can see the negotiation process regarding the algorithms; the default encryption algorithm used is AES-256-GCM, and the default integrity check algorithm is SHA256. Of course, based on our previous experience, the main factor affecting transmission performance is the encryption algorithm, while the impact of the integrity check algorithm is minimal.
Next, let’s take a look at the version of OpenVPN and the supported integrity check algorithms.
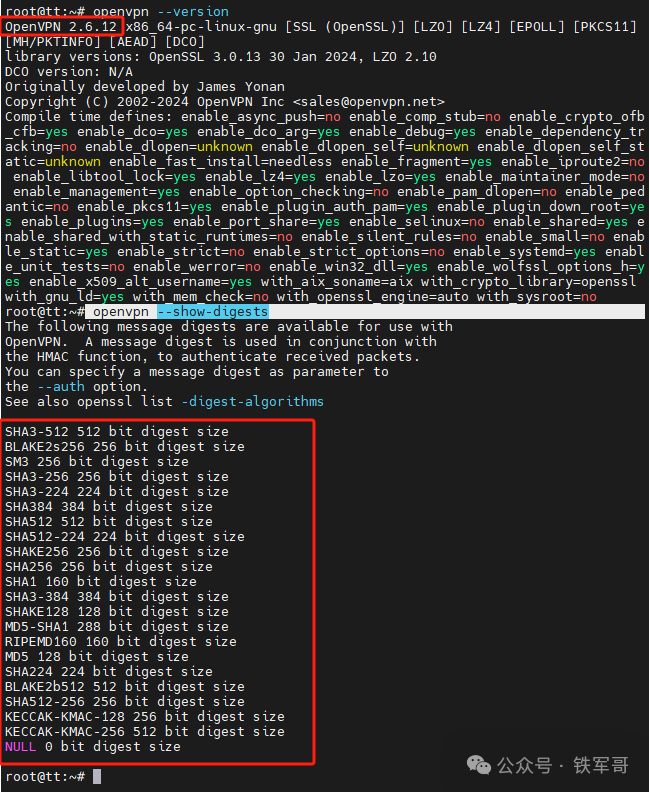
It seems that mainstream algorithms are supported; let’s take a look at the supported encryption algorithms.
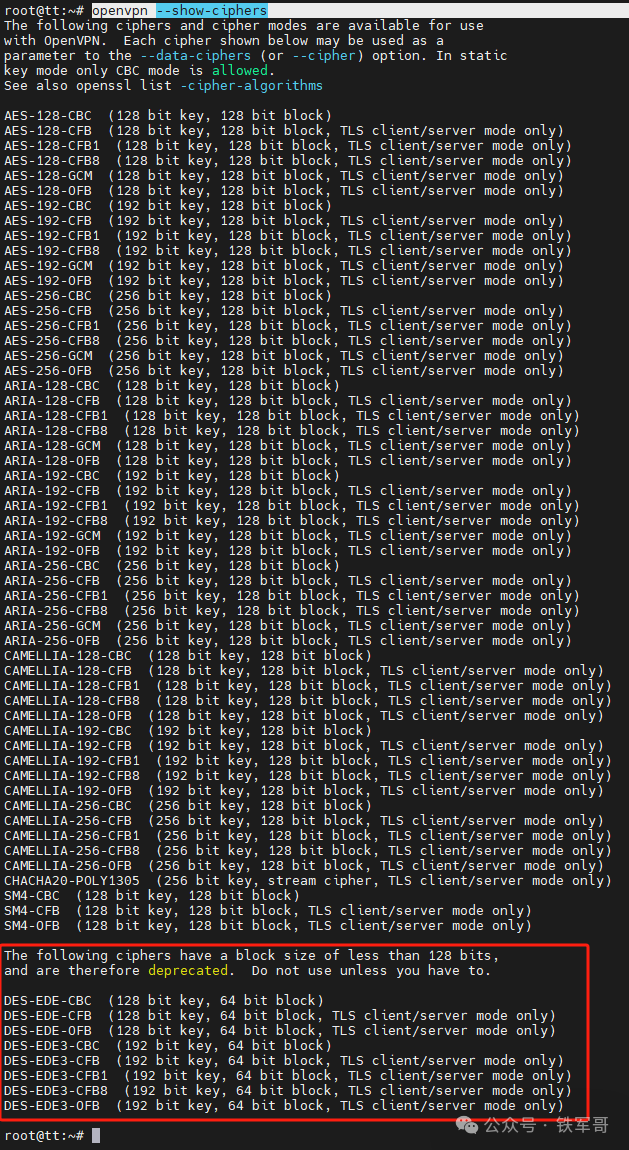
Of course, it is still comprehensive, but it is mentioned that algorithms with a block size smaller than 128 bits are not recommended for use; conversely, these algorithms generally have higher performance.
Next, let’s first look at the transmission bandwidth when two hosts are directly streaming.
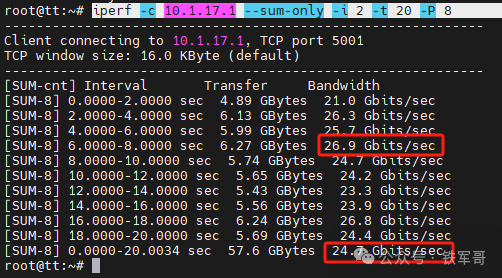
Maximum bandwidth is 26.9 Gbps, average bandwidth is 24.7 Gbps.
Then we will check the streaming bandwidth using the OpenVPN tunnel.
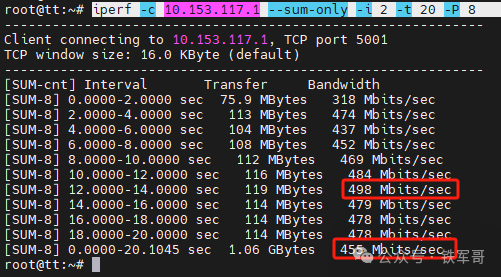
Maximum bandwidth is 498 Mbps, average bandwidth is 455 Mbps.
Observing the resource usage on the host, OpenVPN utilized one core of the CPU while iperf used about 70%, so the performance on hosts with less than two cores should be lower unless the clock speed is higher.
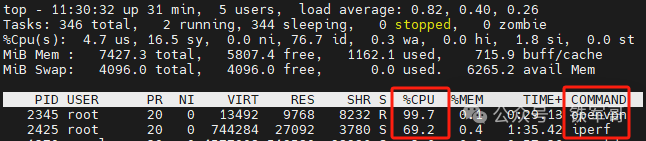
Next, I attempted to change the integrity check algorithm to the 160-bit SHA1 algorithm, but it did not take effect. Upon investigation, I found that starting from OpenVPN version 2.6, when using AEAD (Authenticated Encryption with Associated Data) encryption algorithms (such as GCM), the integrity check of the data channel is provided by the encryption algorithm itself, rather than a separate auth parameter.
Therefore, configuring the SHA1 algorithm will not take effect; if changes are to be made, it will affect stability, and I do not want to revert to version 2.5, so I will not test the integrity check algorithm for now, as it does not have a significant impact; I will directly test the encryption algorithms.
In comparing encryption algorithms, we find they are divided into three segments: the first segment is the algorithm name, which determines the basic encryption logic, mainly divided into AES, ARIA, and CAMELLIA; the second segment is the key length, which is a key parameter balancing security and performance, mainly 128, 192, and 256; the third segment is the encryption mode, which affects the data processing flow and security enhancement features, divided into CBC, CFB, CFB1, CFB8, GCM, and OFB, etc.
We will first test the impact of key length by switching the encryption algorithm to AES-192-GCM.
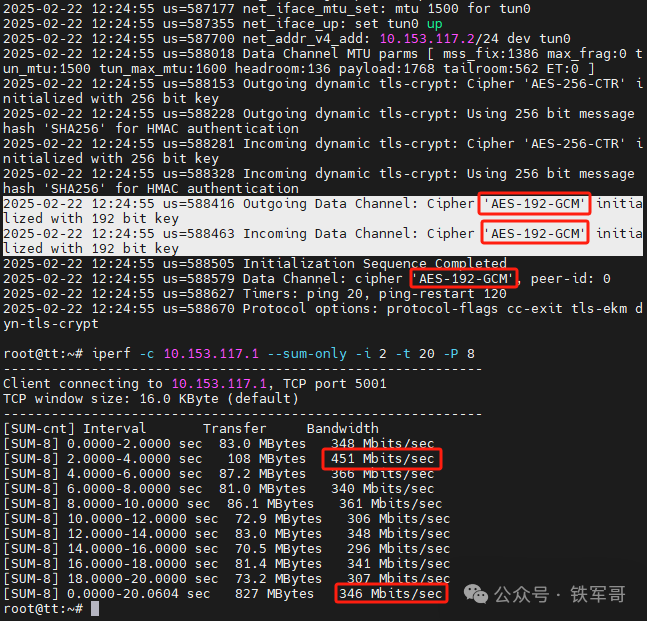
Compared to AES-256-GCM, performance has decreased, with maximum bandwidth of 451 Mbps and average bandwidth of 346 Mbps.
Next, we will switch the encryption algorithm to AES-128-GCM.
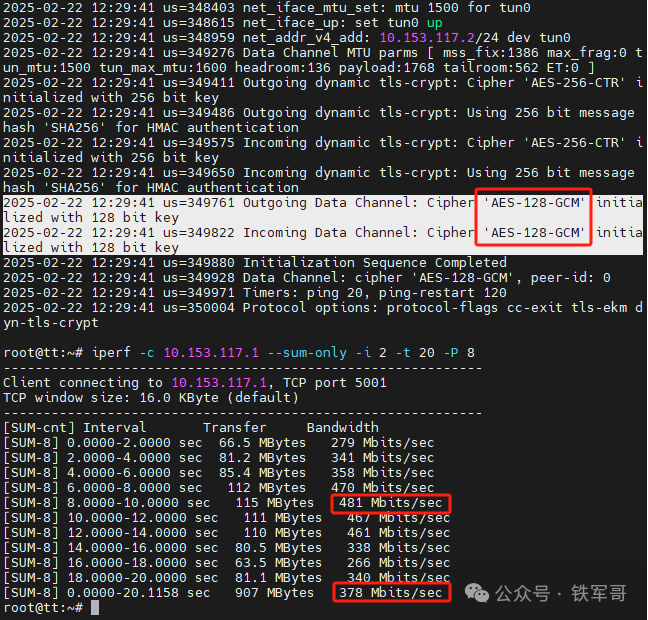
Performance changes are minimal, with maximum bandwidth of 481 Mbps and average bandwidth of 378 Mbps.
Then we will compare different encryption modes, starting with testing AES-128-CFB.
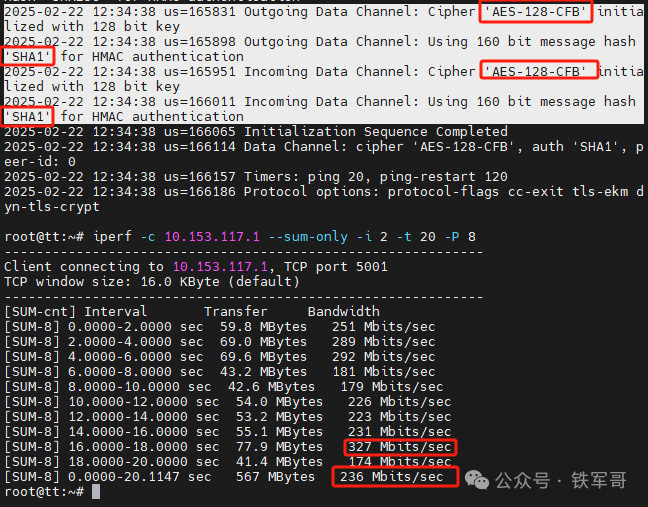
Indeed, when using the AES-128-CFB encryption algorithm, the integrity check algorithm automatically switched to SHA1, with maximum bandwidth of 327 Mbps and average bandwidth of 236 Mbps.
Next, we will test AES-128-CFB1.
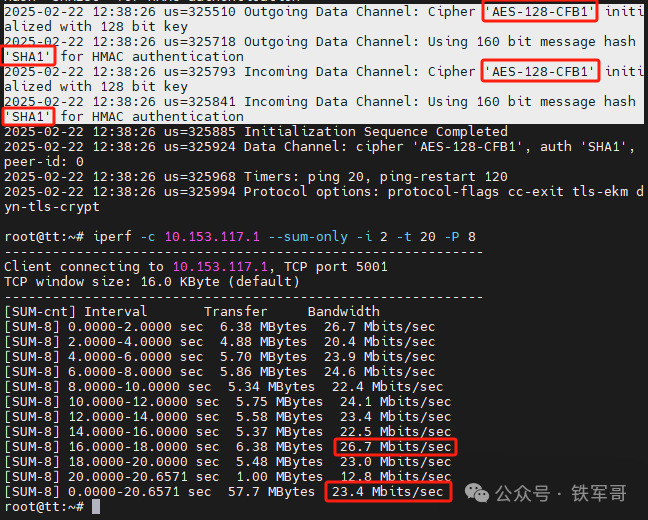
Performance has significantly decreased, with maximum bandwidth of 26.7 Mbps and average bandwidth of 23.4 Mbps.
Next, we will test AES-128-CFB8, with maximum bandwidth of 128 Mbps and average bandwidth of 124 Mbps.
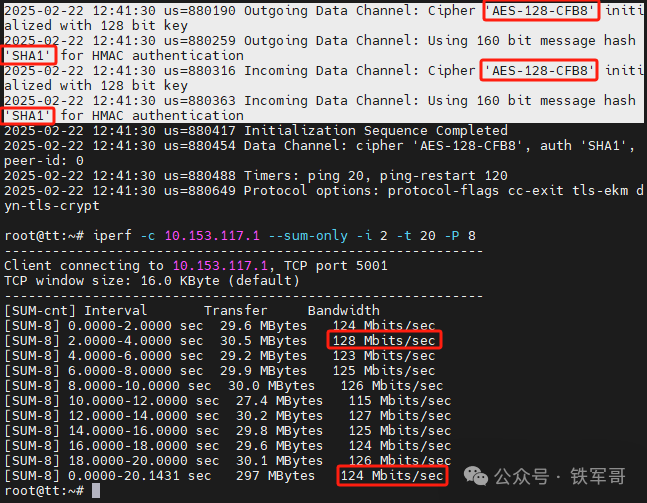
Next, we will test AES-128-CBC, with maximum bandwidth of 247 Mbps and average bandwidth of 203 Mbps.
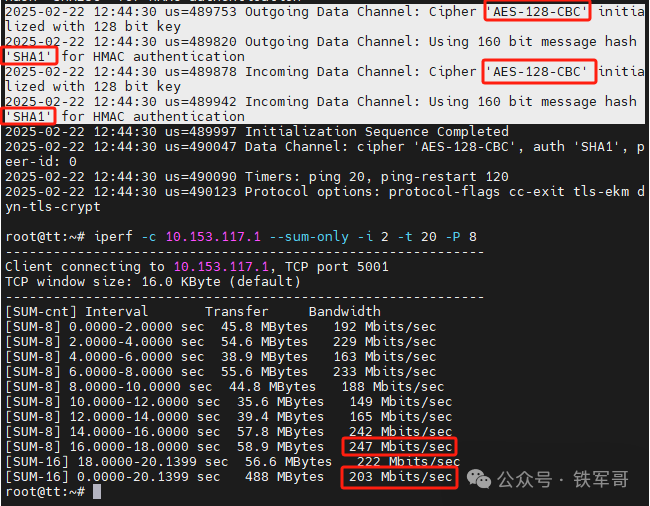
Finally, for AES-128-OFB, maximum bandwidth is 361 Mbps and average bandwidth is 310 Mbps.
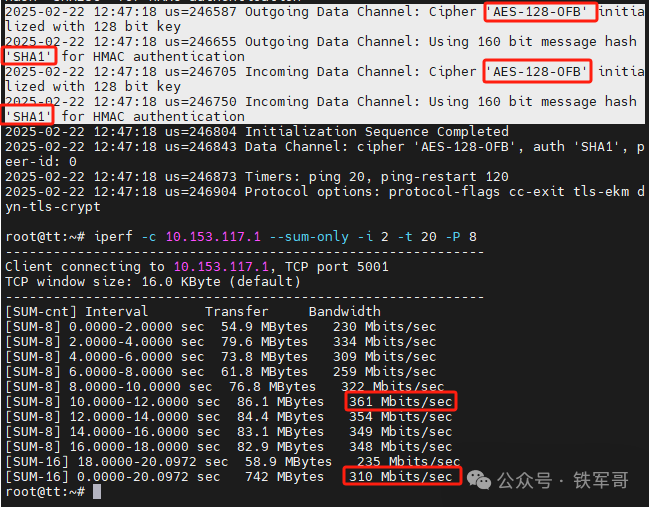
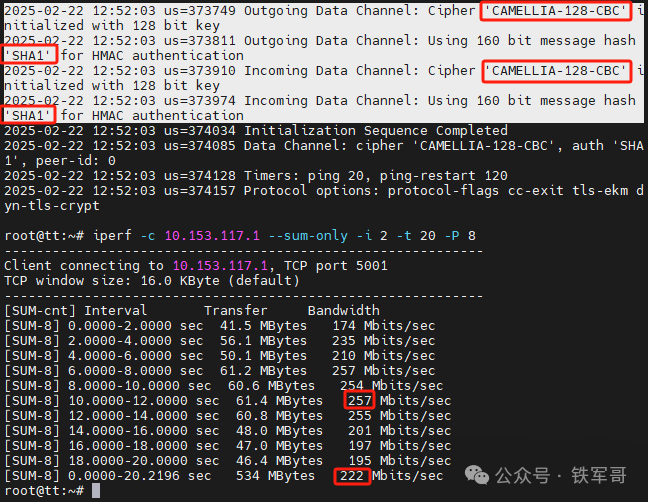
Next, we will compare different encryption algorithms, testing CAMELLIA-128-CBC and ARIA-128-CBC against AES-128-CBC.
Using the CAMELLIA-128-CBC encryption algorithm, maximum bandwidth is 257 Mbps and average bandwidth is 222 Mbps.
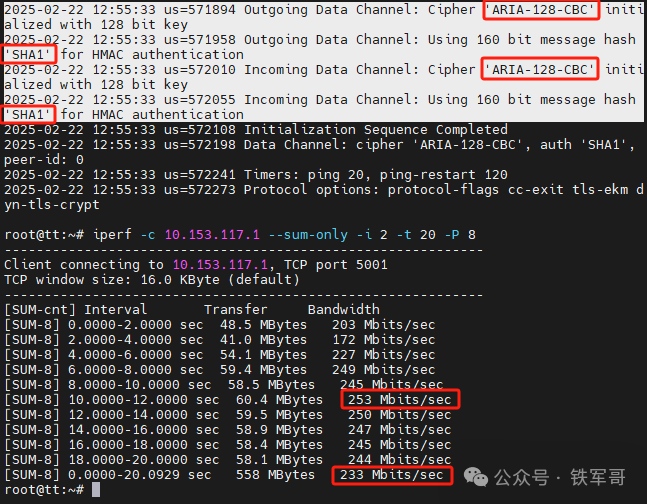
Using the ARIA-128-CBC encryption algorithm, maximum bandwidth is 253 Mbps and average bandwidth is 233 Mbps.
Summarizing the test results:
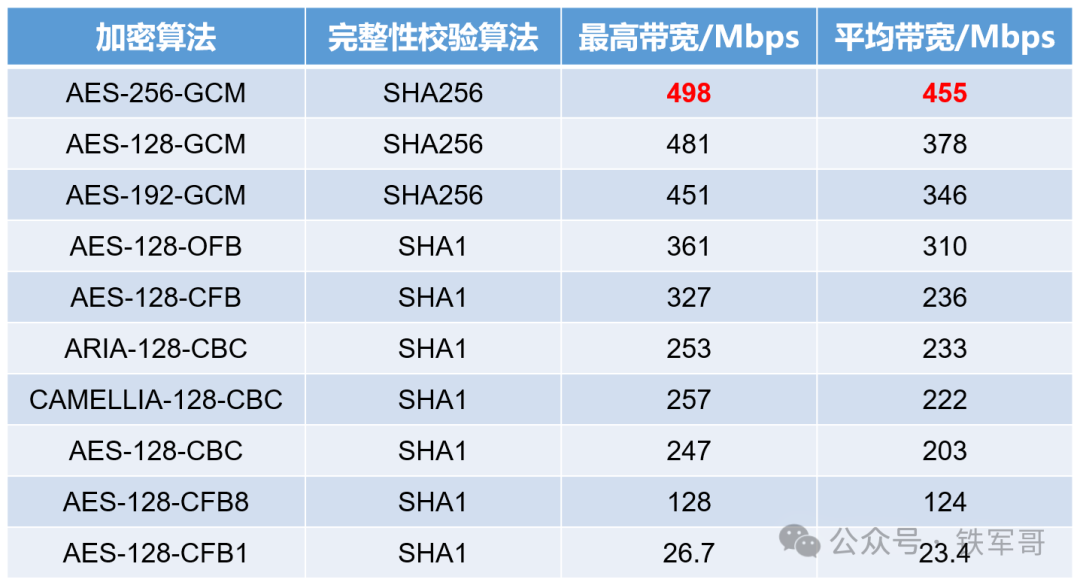
It seems that in terms of encryption modes, the ranking is GCM > OFB > CFB > CBC > CFB8 > CFB1; in terms of encryption algorithms, the ranking appears to be ARIA > CAMELLIA > AES; and regarding key length, it is currently difficult to determine. It seems that OpenVPN has also helped us choose the most suitable encryption algorithm by default. But is this the actual situation? I will test all these algorithms later.
***Recommended Reading***A fourth-grade math problem, the DeepSeek-R1 model under 32b has completely failed, as evidenced by the video!
Even running DeepSeek on a laptop with a 4070 GPU is much faster than a 128-core CPU!
Save you 20 bucks! Just two commands to deploy the DeepSeek-R1 model locally via Ollama.
The offline file is shared, come and copy the homework, deploy a personal assistant with DeepSeek locally.
A math problem in a game that stumped all AI: ChatGPT, DeepSeek, Doubao, Tongyi Qianwen, Wenxin Yiyan.
The Linux client of OpenVPN surprisingly outperforms the Windows client by more than five times.
How to quickly deploy an Ubuntu 24.10 Server virtual machine without a graphical interface.
When you buy a Linux cloud host, how should you test the host’s performance?
Complete experience of installing, configuring, operating, and evaluating MySQL database on Ubuntu.
What to do when Ubuntu runs out of disk space or has configuration errors? How to expand it?
The latency from Beijing to Singapore has already exceeded 300+, can WireGuard or OpenVPN save the day?
Using WireShark to compare the differences in packet encapsulation under different configurations and algorithms of IPsec VPN.
Using vSRX to test the performance differences of various IPsec VPN encryption algorithms.