In a recent cybersecurity study, Tesla’s keyless entry system revealed a major security vulnerability, allowing attackers to unlock a Tesla Model 3 or Model Y within 10 seconds through a BLE (Bluetooth Low Energy) relay attack.

The method to execute this attack is not complicated. It merely requires placing a decoding sensing device near the car owner’s phone or key card, capturing the corresponding digital password, and transmitting it to a receiving device next to the car. At this point, the vehicle mistakenly believes the receiving device is the key, and after executing a simple code, it can unlock the vehicle and allow the attacker to drive away. The total cost of the hardware and software needed to complete such an attack is under 1000 yuan, and these device components can easily be purchased online.

According to a summary by GeekNB.com, a Chinese cybersecurity portal, this breach of Tesla’s keyless entry feature targets the security vulnerabilities of BLE low-power Bluetooth, which is a type of Bluetooth communication technology characterized by ultra-low power consumption and low cost. It is commonly used in Internet of Things (IoT) smart devices, such as smart locks, smart home appliances, and health bands. Compared to regular Bluetooth communication, BLE can significantly reduce power consumption and cost while maintaining the same communication range, making it the optimal solution for connecting sensors and control devices.
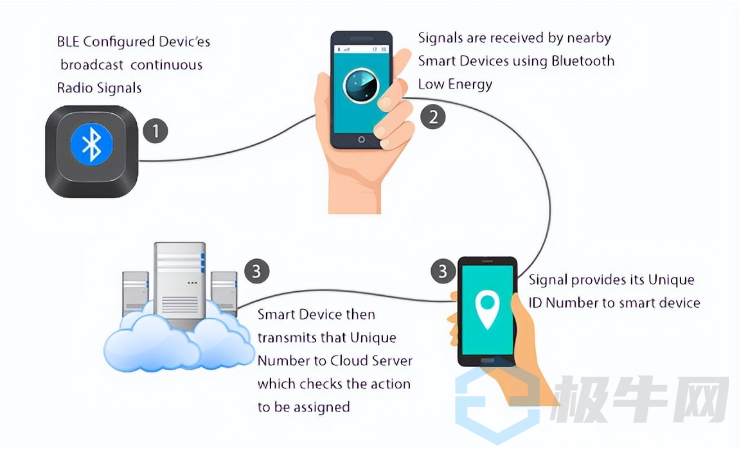
Cybersecurity researchers state that the exposure of this Tesla vulnerability does not imply that all smart devices using BLE low-power Bluetooth have similar security risks. The core issue lies in Tesla’s communication and verification mechanisms. However, currently, the keyless entry functions in domestic new energy vehicles are quite similar to Tesla’s and also carry related vulnerabilities. It is recommended that various automobile manufacturers conduct internal security reviews as soon as possible.
It is no longer news that Tesla has been exposed for security vulnerabilities. In 2020, the Tesla Model X was reported to have its autopilot system hacked multiple times. Additionally, cybersecurity researchers used a Raspberry Pi to DIY a car key, exploiting vulnerabilities in the Tesla key, allowing them to “copy” the original key within a 15-meter range of the owner. The copied key could unlock and start the vehicle normally. In early 2022, a 19-year-old hacker exploited a programming vulnerability in Tesla, successfully hacking 25 cars and remotely controlling the doors, music system, and even the ability to drive the car away.
Looking back at the numerous security vulnerabilities of Tesla, we should realize that the increasingly connected new energy smart vehicles also face similar security threats. If these high-risk vulnerabilities are exploited by malicious individuals, cars could become deadly weapons, endangering people’s safety.
