ECU Control of Fuel Injection in Motorcycles: Six Conditions Explained
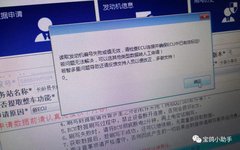
Follow 【Finger Motorcycle】 for fresh insights on motorcycle maintenance and repair! Author: Weibo Yesterday, some enthusiasts in the group discussed the operation of the fuel injection system, particularly when fuel cut-off during deceleration begins and which sensor controls it. Some said it’s controlled by the rapid return of the throttle, while others claimed it’s controlled … Read more