Exploring the GD32C231 MCU: A Look at the Cortex®-M23
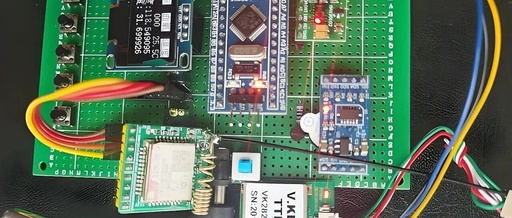
Today I checked the news and saw that ST has been breached? Then I noticed the new product from GD32. I took a quick look and felt that the Cortex®-M23 was somewhat unfamiliar, so I gathered some information to write about it before going to sleep. GD32C231-MCU.png On June 5, 2025, GigaDevice (stock code 603986), … Read more