Tailscale is a networking tool based on Wireguard that allows point-to-point connections between nodes without the need for a public IP address, achieving decentralization. The configuration is simple and user-friendly, supporting various platforms and clients. Below is the configuration process on OpenWrt.
1. Download Software
Download the Tailscale software package to a specified directory. Click here to find the latest software package and download it locally. Then use WinSCP to upload the downloaded software to the /tmp directory of OpenWrt, or find the download link and use the wget command to download directly.
wget https://github.com/adyanth/openwrt-tailscale-enabler/releases/download/v1.32.2-98e126e-autoupdate/openwrt-tailscale-enabler-v1.32.2-98e126e-autoupdate.tgz2. Extract Software
tar x -zvC / -f openwrt-tailscale-enabler-v1.32.2-98e126e-autoupdate.tgz3. Install Dependencies
opkg update
opkg install libustream-openssl ca-bundle kmod-tun4. Set to Start on Boot, Verify Boot Start
/etc/init.d/tailscale enable
ls /etc/rc.d/S*tailscale*5. Start Tailscale
/etc/init.d/tailscale start6. Get Login Link, Configure Routing
tailscale upCopy the displayed address and open it in a browser. Log in to the Tailscale management homepage using a Google or Microsoft account for verification.
7. Enable Subnet Routing
Enter the following command on OpenWrt to open the local subnet route. The subnet address is the LAN network of OpenWrt.
tailscale up --advertise-routes=192.168.18.0/24 --accept-dns=falseOn the Tailscale management page, click the more icon on the right side of the device list, disable key expiration, and enable subnet routing.
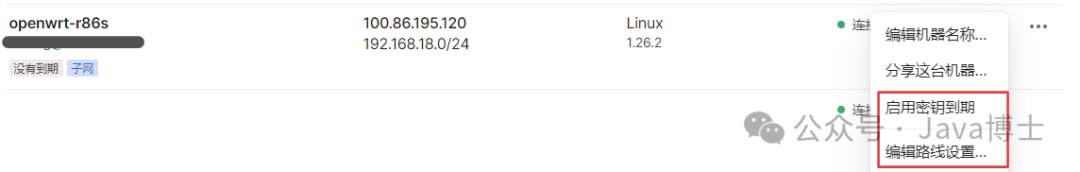
Now you can ping other Tailscale nodes from OpenWrt, but other nodes still cannot connect to the OpenWrt node. You need to add the Tailscale interface on OpenWrt.
8. Add Interface
Create a new interface on OpenWrt, select static address for the protocol, select tailscale0 for the device, and enter the address assigned on the Tailscale management page with a mask of 255.0.0.0. Select the LAN zone for the firewall area.
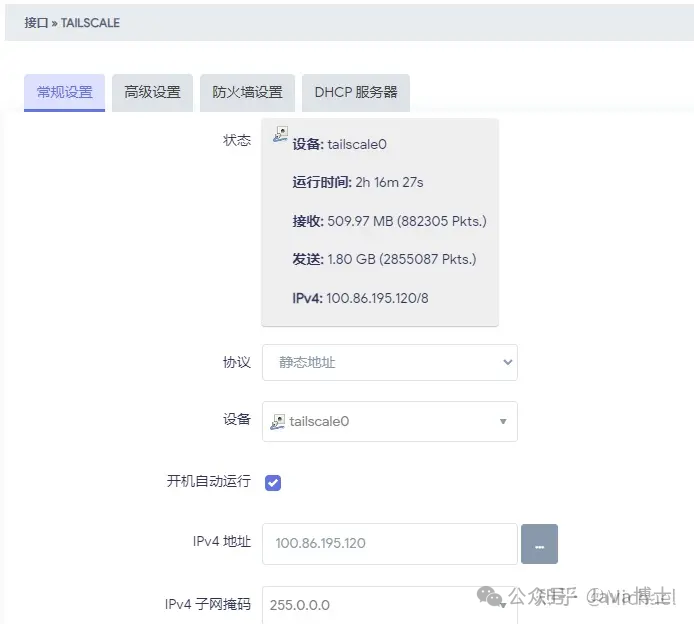
After configuration, it should look like the following:
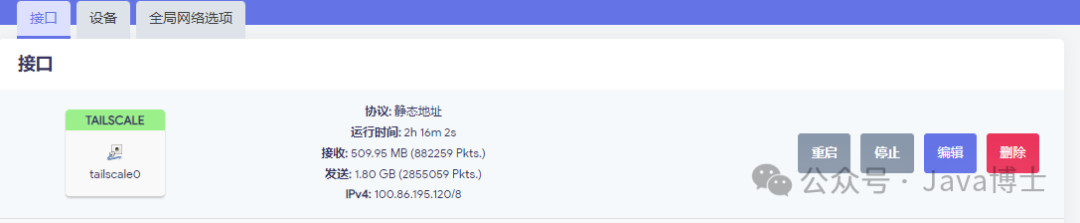
9. Add Firewall Rules
Add the following content to the custom rules of the firewall and restart the firewall.
iptables -I FORWARD -i tailscale0 -j ACCEPT
iptables -I FORWARD -o tailscale0 -j ACCEPT
iptables -t nat -I POSTROUTING -o tailscale0 -j MASQUERADENow all Tailscale nodes can communicate with each other normally.