Hardware Security Module
A Hardware Security Module, abbreviated as HSM, is a physical device specifically designed to securely generate, store, and manage digital keys.
HSM plays a crucial role in the field of information security, especially in application scenarios that require high security levels, such as financial services, government agencies, data centers, and the automotive industry.
The main features and functions of HSM include:
Key Management:
HSM provides a secure key storage environment that can generate, store, and distribute keys, including symmetric keys and asymmetric key pairs.
Encryption Operations
HSM is capable of performing encryption and decryption operations, supporting various encryption algorithms such as RSA, AES, and ECC.。
Digital Signatures:
HSM supports the creation and verification of digital signatures, ensuring data integrity and non-repudiation.
Tamper Resistance:
HSM is designed with tamper resistance mechanisms, including tamper evidence and tamper resistance, ensuring physical security.High Availability:
HSM is typically designed with multiple power supplies and hot-swappable components to support the high availability requirements of data centers.
Certification:
HSM is usually certified by internationally recognized standards, such as Common Criteria and FIPS 140, to ensure its security and reliability.。
Performance:
HSM can provide high-performance encryption operations, reducing the CPU load on the host, especially in public key cryptography operations.
Flexibility:
Some HSMs allow users to run specially developed modules on their internal processors, increasing application flexibility.
Application Scenarios of HSM:– Public Key Infrastructure (PKI):
HSM is used in PKI for generating, storing, and using key pairs, supporting the issuance and management of digital certificates.
– Financial Services:
In banking and financial services, HSM is used to protect transaction data and customer information.
– Government Agencies:
Used to store and manage encryption keys for sensitive government data.。
– Healthcare:
Protecting the privacy and security of patient records.
– Automotive Industry:
Used for key management and secure communication in in-vehicle networks, such as V2X communication and firmware updates.
Implementation Architecture of HSM:
Separate from the CPU.
Integrated HSM:
HSM integrated with CPU on the same chip, providing higher security and cost-effectiveness.
Programmable Security Kernel:
Provides flexibility, allowing the extension and updating of security features.
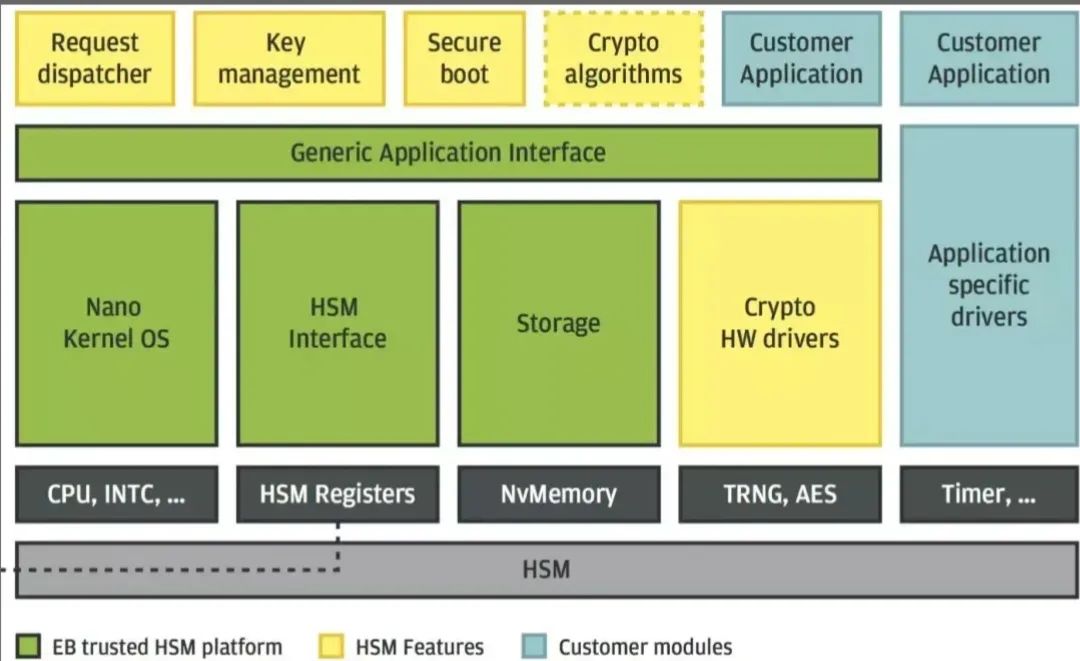
HSM Block Diagram
May vary by different manufacturers and products; if a detailed block diagram is needed, it is usually found in the technical documentation or product manuals of HSM suppliers. Here are some key points about HSM block diagrams and architectures:
General Architecture of HSM:
– HSM typically includes one or more dedicated processors for performing encryption and decryption operations.
– They have dedicated storage areas for securely storing keys and sensitive data.
– HSM can provide True Random Number Generators (TRNG) and other cryptographic hardware accelerators.
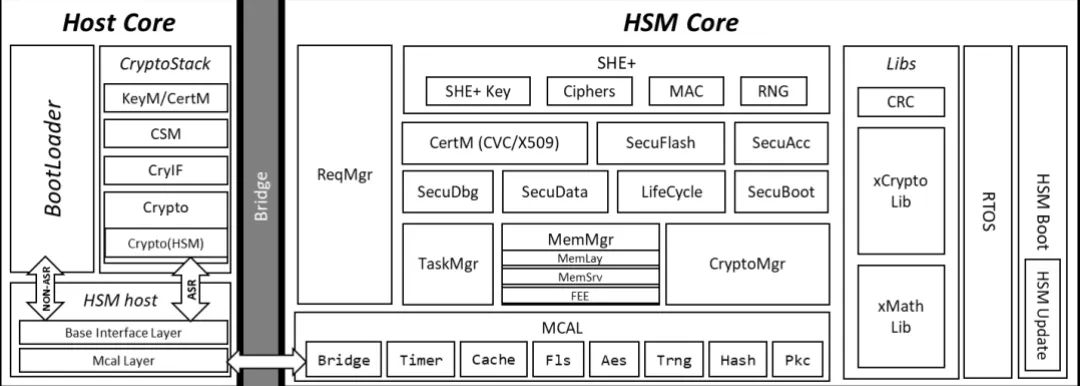
HSM in the EVITA Project:
– The EVITA project defines three levels of HSM: Full, Medium, and Light, each with different functionalities and performance.
– Full HSM supports hardware acceleration of asymmetric algorithms, mainly used for V2X secure communication.
– Medium HSM is suitable for domain controllers, supporting symmetric acceleration engines and secure storage.
– Light HSM is used for subcontrollers, implementing secure boot and SecOC functionalities.
Infineon AURIX Series Microcontroller HSM:
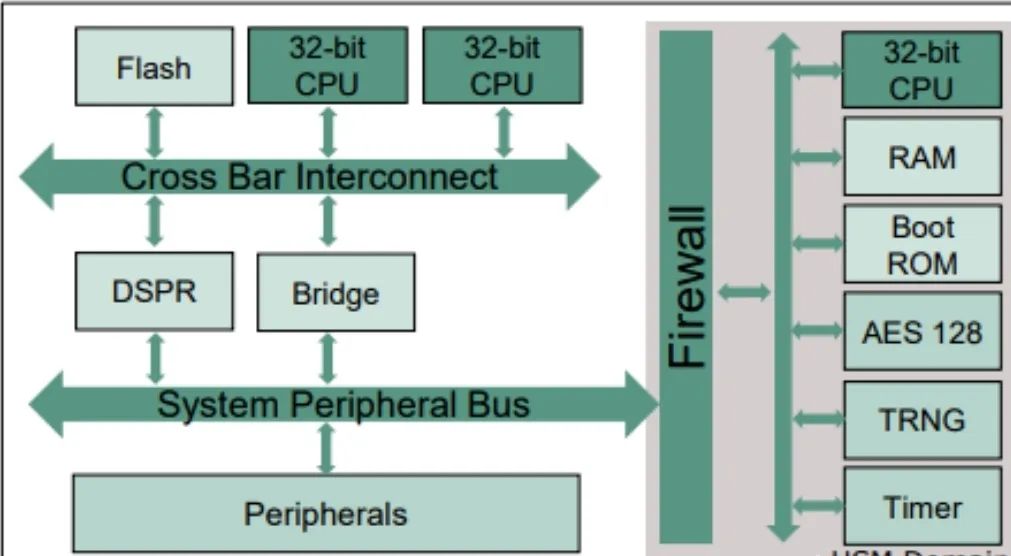
– The AURIX series microcontroller integrates HSM, providing an ARM Cortex-M3 based CPU.
– Includes TRNG and hardware accelerators for AES, Hash, and PKC algorithms.
– HSM connects to other parts of the chip via the System Peripheral Bus (SPB).
HSM Interfaces in AUTOSAR:
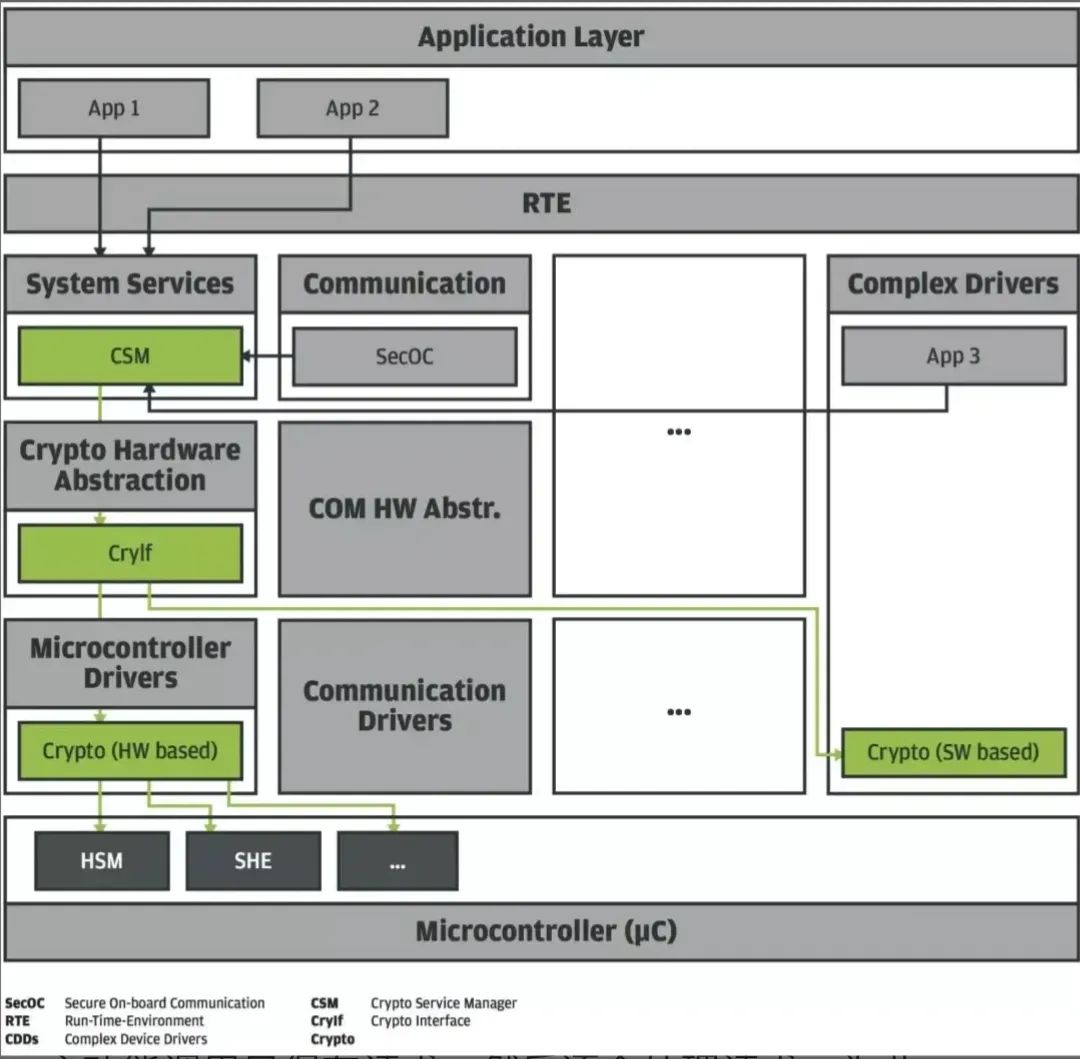
– The HSM interfaces in AUTOSAR include Crypto Service Manager (CSM), Crypto Interface (CryIf), and Crypto Driver (CryDrv).
– CSM serves as the first interface for application layer software components to invoke encryption and decryption modules.
– CryIf supports distributing related tasks and invoking different drivers.
– Crypto Driver implements specific encryption and decryption operations.
– CP20-11 starts defining the above specifications.
Vector’s HSM Firmware Solutions:
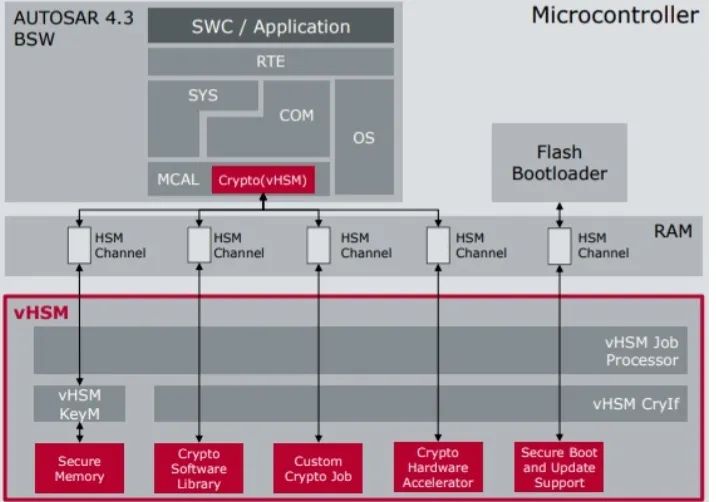
– Vector provides HSM firmware solutions vHSM that meet AUTOSAR requirements.
– The Crypto(vHSM) part corresponds to CSM in AUTOSAR, providing abstract encryption services.
– The CryIf part is implemented through inter-process communication or shared memory to access different drivers.
– Supports secure boot.
Conclusion:
As a key component of information security, HSM provides a solid security foundation for various industries with high security requirements through its hardware encryption and key management capabilities. With the development of technology and the increasing demand for security, the application and importance of HSM will continue to grow.
References:
HSM Public Account: Automotive Electronics and Software
Discussing the Functional Safety of HSM in AutoSAR
Hardware Encryption Module Public Account: Elektroauto
Hardware Security Module – HSM
Public Account: Yan Zhi Smart Car
The Anchor of Automotive Information Security: HSM
Thanks for your attention Automotive Software Engineers
