1. What is it
Symmetric encryption refers to the use of the same key for both encryption and decryption. The process of encryption and decryption is illustrated in the following diagram:
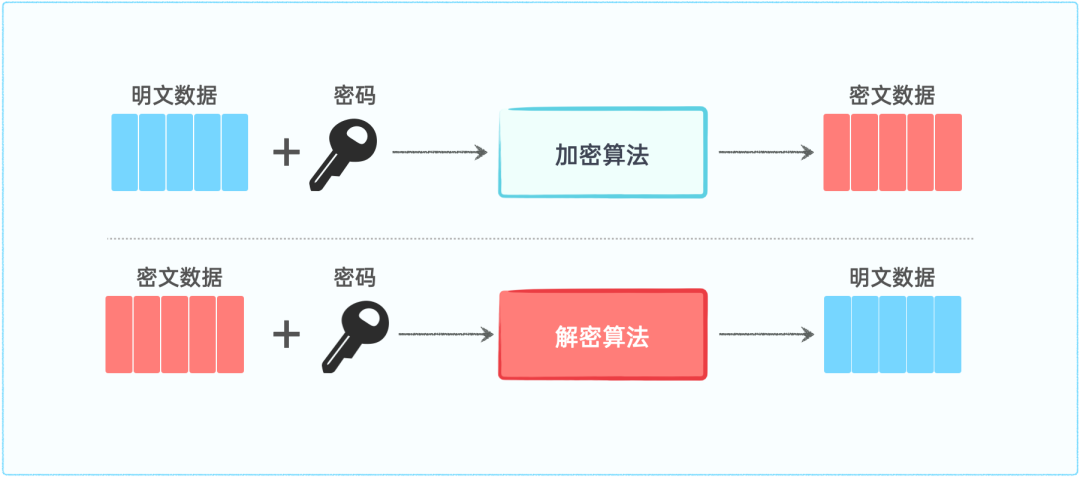 Symmetric encryption algorithms have the advantages of fast speed and high efficiency, but they face challenges in key distribution and are susceptible to eavesdropping. Once the key is compromised, the security of the communication is lost. However, clever humans have solved this problem, and we will write a dedicated article discussing this issue later.2. What are the types
Symmetric encryption algorithms have the advantages of fast speed and high efficiency, but they face challenges in key distribution and are susceptible to eavesdropping. Once the key is compromised, the security of the communication is lost. However, clever humans have solved this problem, and we will write a dedicated article discussing this issue later.2. What are the types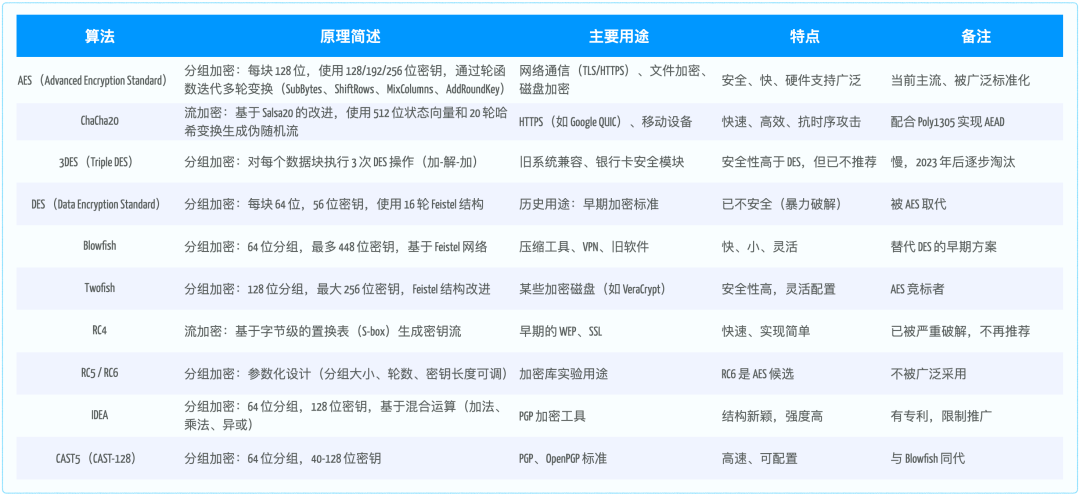
The most commonly used algorithms currently are actually the first two: AES and ChaCha20.
3. An example: AES algorithm
The AES (Advanced Encryption Standard) algorithm is the most widely used symmetric encryption algorithm, very secure, and has not been substantially cracked. It is commonly used in HTTPS, VPNs, and disk encryption scenarios. AES uses block cipher modes, with a fixed block size of 128 bits (16 bytes), and there are three key length types: AES-128 / AES-192 / AES-256. It supports chip-level hardware acceleration (with corresponding instruction sets available on Intel/AMD/Arm platforms).
The AES-128 algorithm processes a block of plaintext data through 11 rounds, divided into three major steps, as shown below:
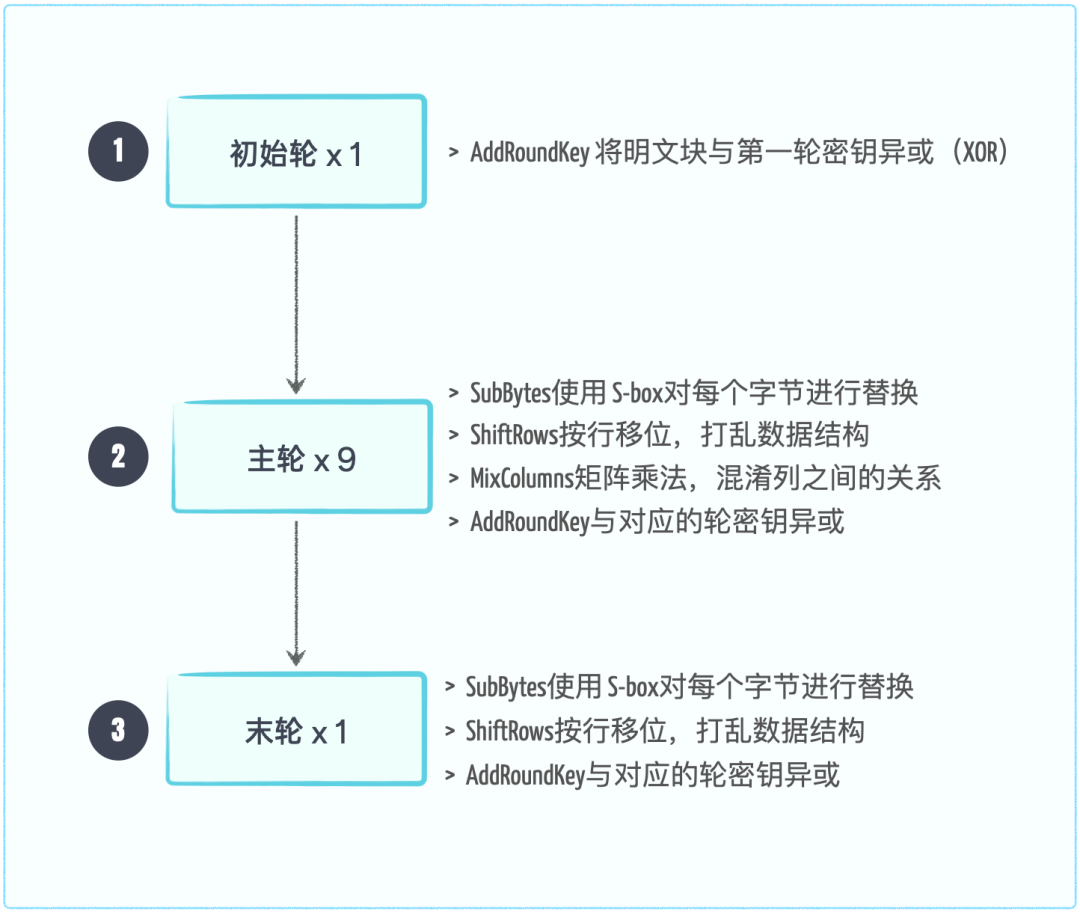
The key length of AES only affects the number of rounds of data processing and does not affect the length of the block data. The corresponding relationship is as follows:
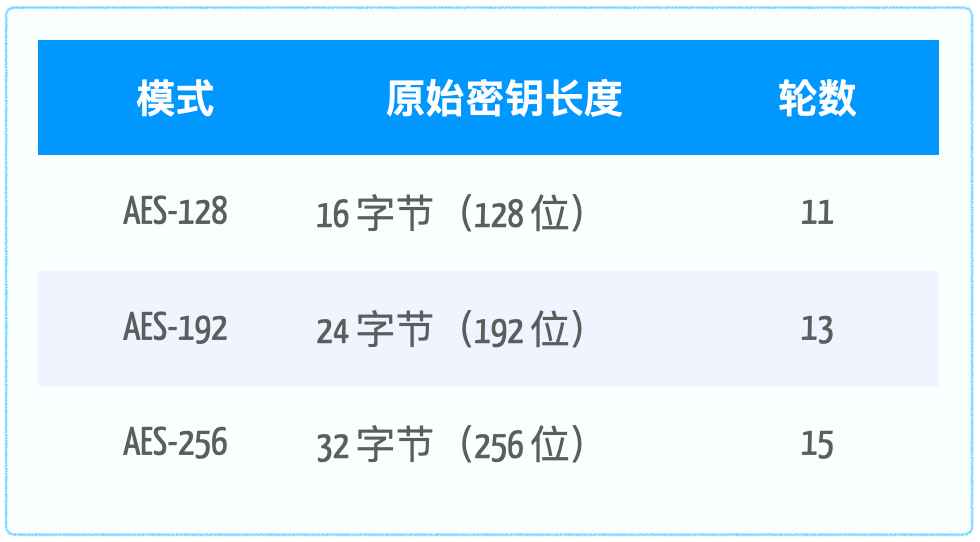 4. Underlying logicSymmetric encryption algorithms are based on a “framework model” known as the encryption mode, which defines the strategy for encrypting multiple data blocks. There are two main categories of encryption modes: block ciphers and stream ciphers.Block ciphers divide plaintext data into fixed-size blocks and encrypt them according to different strategies. Common block cipher modes are as follows:
4. Underlying logicSymmetric encryption algorithms are based on a “framework model” known as the encryption mode, which defines the strategy for encrypting multiple data blocks. There are two main categories of encryption modes: block ciphers and stream ciphers.Block ciphers divide plaintext data into fixed-size blocks and encrypt them according to different strategies. Common block cipher modes are as follows: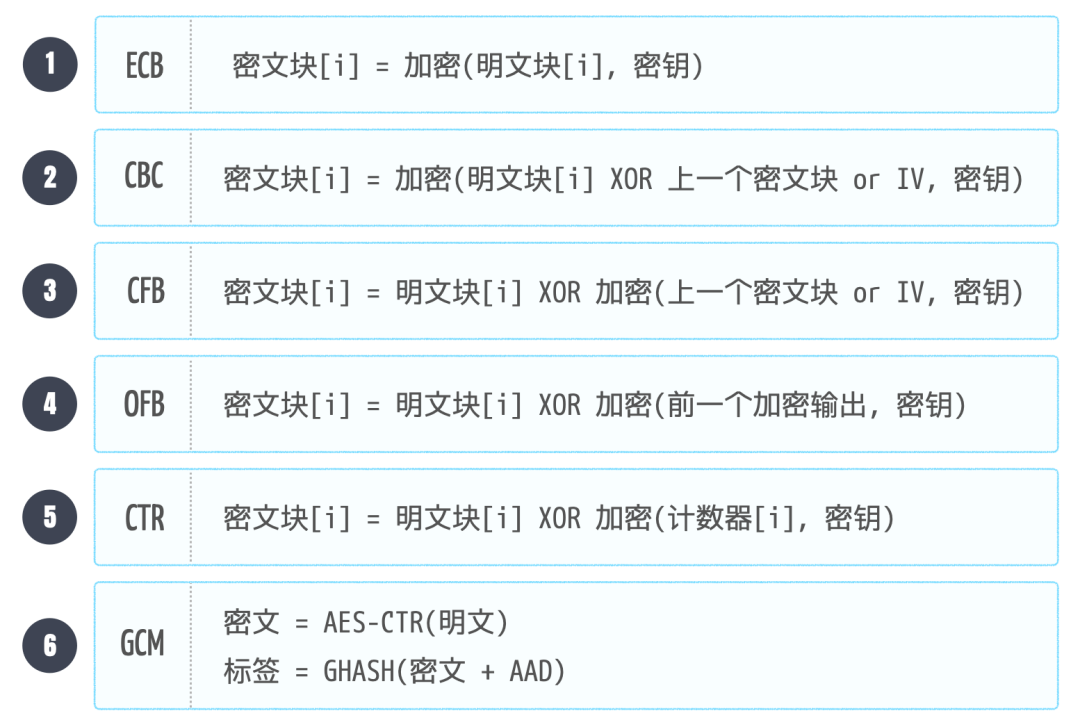 Stream ciphers encrypt plaintext in a bit stream, byte stream, or byte block manner, offering low latency and good timeliness. Common stream cipher modes are as follows:
Stream ciphers encrypt plaintext in a bit stream, byte stream, or byte block manner, offering low latency and good timeliness. Common stream cipher modes are as follows: 5. Multi-faceted analysisWhen considering which encryption and decryption mode to use, multiple factors need to be taken into account:
5. Multi-faceted analysisWhen considering which encryption and decryption mode to use, multiple factors need to be taken into account: