I firmly believe that
| those who follow the editor’s public account are certainly people who want to change themselves;
| those who share the editor’s public account are certainly people who want to change others;
| those who comment on the editor’s public account are definitely people who are starting to take action.
Exploring the Encrypted World: A Journey from Basic Algorithms to Digital Certificate Security
In the information age, data is a treasure, and data security is the solid fortress that protects this treasure. Whether it is our personal privacy information or the commercial secrets between enterprises, they all rely on the protection of encryption technology. Today, we will take you deep into the mysterious world of encryption and decryption, explore the wonderful applications of encryption algorithms, interpret the key roles and management methods of digital certificates, and finally teach you how to use tools to generate digital certificates.

Basic Knowledge of Encryption and Decryption
In the field of information security, encryption and decryption technologies are the core means of protecting data privacy and integrity. Below, we will understand them from several aspects: symmetric encryption algorithms, asymmetric encryption algorithms, digital signatures, and hash algorithms.
Symmetric Encryption Algorithms
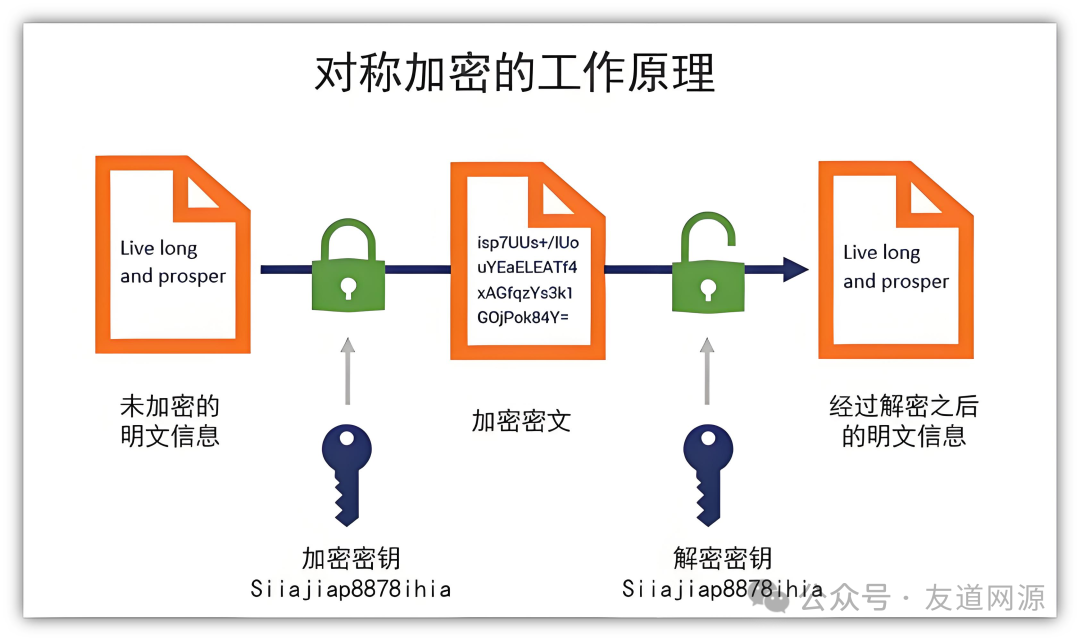
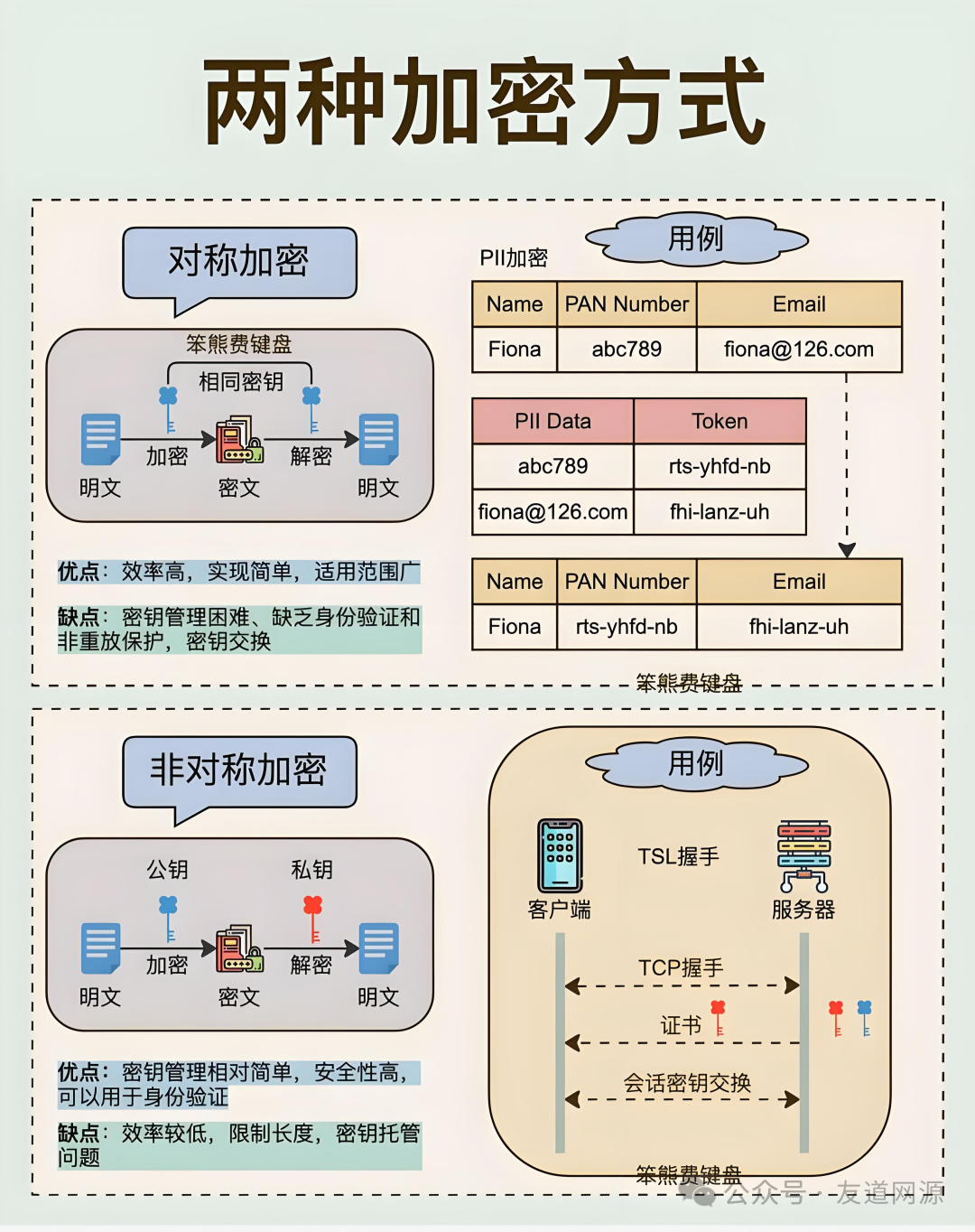
Symmetric encryption algorithms are the“big brother” of encryption technology, characterized by using the same key for both encryption and decryption. It is like you and your friend have agreed on a password that only you both know; you encrypt the message with this password and send it out, and the other party can decrypt it using the same password. This algorithm is very efficient and suitable for processing large amounts of data, often used for data storage or local file encryption. Common symmetric encryption algorithms includeAES (Advanced Encryption Standard) andDES (Data Encryption Standard).
Its advantages are obvious: the speed of encryption and decryption is fast, and the algorithm is simple and easy to implement. However, it also has disadvantages; key management and distribution are very important. If the key is accidentally leaked, the data becomes insecure. Imagine if someone knows the password you agreed upon, then all your encrypted information would be exposed.
Asymmetric Encryption Algorithms
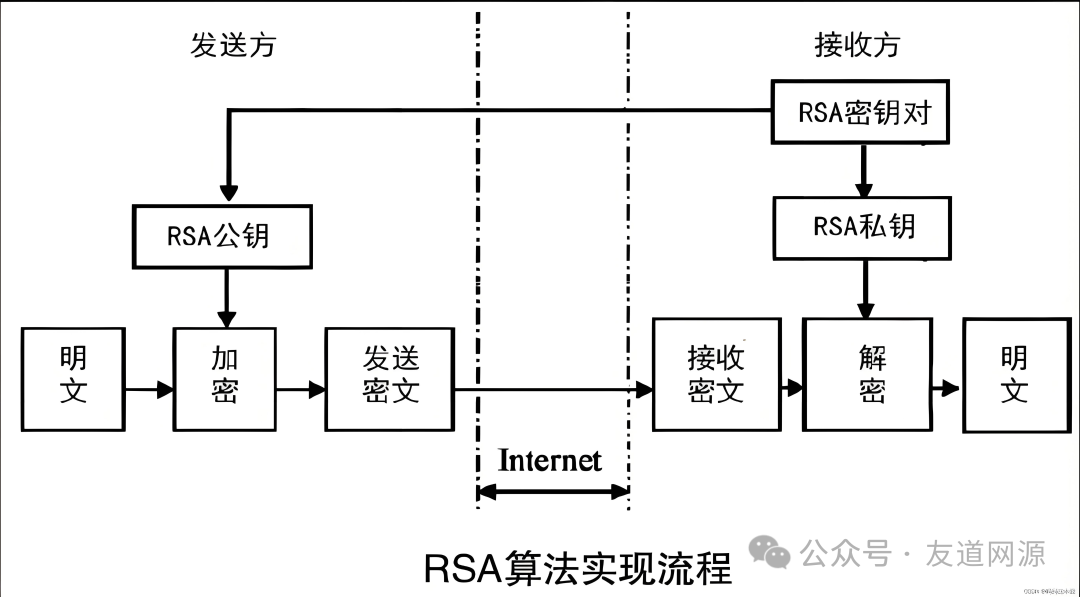
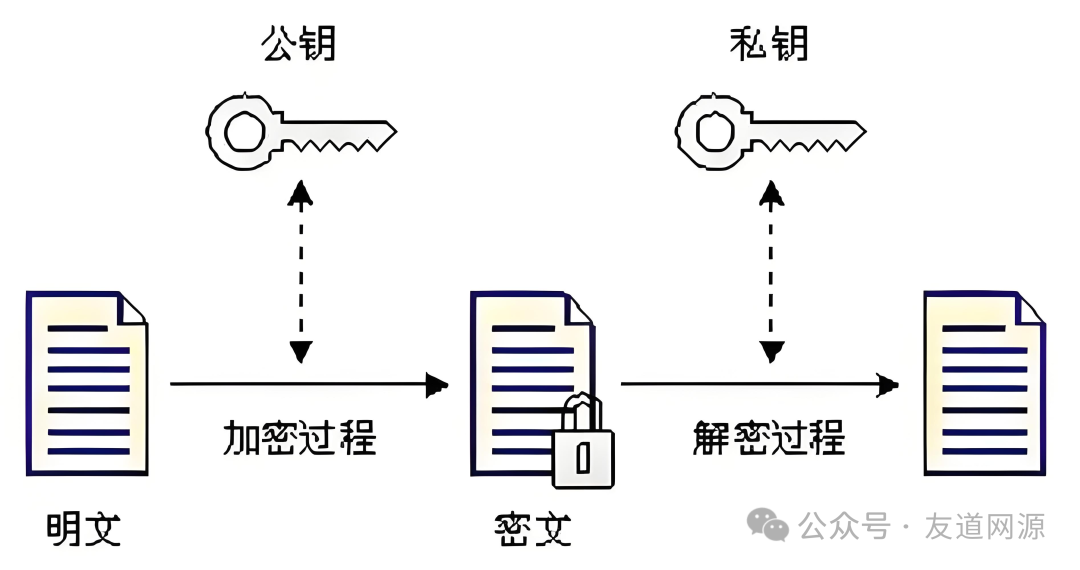
Asymmetric encryption algorithms, also known as public key cryptography, are the“backbone” of modern encryption technology. It uses a pair of keys: one called the public key, which can be shared publicly, and the other called the private key, which must be kept secret. For example, if you want to send a message to a friend, you encrypt the message using your friend’s public key, and only your friend can decrypt it with their private key. Common asymmetric encryption algorithms includeRSA andECC (Elliptic Curve Cryptography).
The advantages of asymmetric encryption are that public key distribution is convenient, and it supports digital signatures and verification, ensuring that the data is complete and the source is trustworthy. However, it also has drawbacks: the speed of encryption and decryption is relatively slow, making it less suitable for processing large amounts of data, and the algorithm is complex, consuming a lot of computational resources.
Digital Signatures and Hash Algorithms
Digital signatures and hash algorithms are“powerful assistants” for ensuring data integrity and verifying identity, usually used in conjunction with asymmetric encryption algorithms.
Hash algorithms can transform data of any length into a fixed-length output, known as the hash value. This hash value is remarkable; even a slight change in the data will result in a different hash value. Common hash algorithms includeSHA-256 and MD5. The input data length for hash algorithms is unlimited, but the output hash value length is fixed, and it isone-way, meaning the original data cannot be restored from the hash value.
A digital signature is created by encrypting the hash value of the data with the private key, used to verify the integrity of the data and the authenticity of its source. The recipient decrypts the signature with the public key and compares it with the hash value they calculate themselves to determine if the data has been altered. Its advantages include verifying data integrity and confirming the sender’s identity, preventing impersonation. However, if the hash algorithm is not secure enough, it may lead to different inputs producing the same hash value, and the verification process of digital signatures is relatively complex, consuming computational resources.
The Evolution of Encrypted Communication: From Basics to Complex Practices
The development of encrypted communication is a process of humanity continuously responding to security challenges and seeking solutions. Next, let’s look at how encrypted communication has evolved from simple to complex.
Plaintext Communication: The Starting Point of Communication
In the early days, people transmitted information over the network directly in plaintext, just like writing a letter without an envelope. For example, a client sends“Hello” to the server, and the server replies, “Hello, I am the server.” This method, while simple and direct, has significant issues; information can be easily intercepted during transmission, leading to leaks, and there is no way to verify the identities of both parties, making it vulnerable to man-in-the-middle attacks or impersonation.
The Introduction of Symmetric Encryption: A Simple Confidentiality Measure
To make communication more secure, symmetric encryption was introduced. The client and server share a key in advance and use this key to encrypt messages when sending them. For example, the client sends“{Hello}[Key|Symmetric Encryption]”. This indeed improves confidentiality; only those who know the key can decrypt it. However, new problems arise; key distribution is challenging, especially when there are many users. Moreover, once the key is leaked, all communication content is exposed.
The Emergence of Asymmetric Encryption: Introducing Public and Private Keys
To solve the key distribution problem of symmetric encryption, asymmetric encryption was born, such asthe RSA algorithm. The server generates a public key and a private key, sending the public key to the client. The client encrypts the message with the public key and sends it to the server, which decrypts it with the private key. This verifies the server’s identity, but the client’s identity cannot be confirmed, and if the information is encrypted with the public key, anyone can decrypt it, making the communication content potentially public.
The Introduction of Hybrid Encryption: Combining Symmetric and Asymmetric Encryption
Asymmetric encryption is inefficient for processing large amounts of data, leading to the emergence of hybrid encryption methods. The server sends the public key to the client, who generates a random symmetric encryption key, encrypts this key with the server’s public key, and sends it to the server. The server decrypts it with the private key to obtain the symmetric encryption key, and then uses this symmetric key for communication. This method solves the key distribution problem by transmitting the symmetric key using asymmetric encryption and improves efficiency by transmitting actual data using symmetric encryption. However, there is still the issue of public key trust; how does the client know if the server’s public key is trustworthy?
The Emergence of Digital Certificates: Solving the Public Key Trust Issue
To address the public key trust issue, digital certificates have emerged. The server obtains a digital certificate from a certificate authority, which contains the server’s public key. The client verifies the certificate’s validity upon receipt; if everything is fine, they use the public key inside to encrypt the symmetric key and send it to the server, continuing communication with symmetric encryption. This allows the client to verify the server’s identity, ensuring the public key is trustworthy, while hybrid encryption guarantees communication security and efficiency. However, digital certificates rely on trusted third-party organizations; if this organization is untrustworthy, the entire security system may fail.
HTTPS Protocol: Standardization of Encrypted Communication
In internet applications, the HTTPS protocol has become the standard for encrypted communication. The browser sends an HTTPS request to the server, which returns a digital certificate. The browser verifies the certificate, generates a symmetric encryption key, encrypts it with the server’s public key, and sends it. The server decrypts it with the private key to obtain the symmetric key, and then communication proceeds with symmetric encryption. HTTPS is widely used in web browsing, online payments, and other scenarios, ensuring identity verification and data confidentiality for both parties in communication.
The Composition and Principles of Digital Certificates
Digital certificates are crucial in modern information security systems, serving as the key to mutual trust between communicating parties. Let’s understand their composition and working principles.
The Basic Composition of Digital Certificates
A complete digital certificate typically includes the following parts:
Issuing Authority (Issuer): The organization responsible for issuing the certificate, such as DigiCert, GlobalSign, and Let’s Encrypt, which are common issuing authorities. Their reputation directly affects the certificate’s credibility.
Certificate Validity Period (Valid From and Valid To): Digital certificates are not valid indefinitely; they typically have a validity period of one to two years. They can be trusted during the validity period, but must be renewed or re-applied once expired.
Public Key (Public Key): This is the core of the certificate, used for encrypting information or verifying digital signatures, existing in pairs with the private key, where the public key is public and the private key is kept secret.
Certificate Holder (Subject): This refers to the owner of the certificate, which can be an individual, organization, or website, with detailed information about the holder clearly displayed in the certificate.
Signature Algorithm (Signature Algorithm): Used to generate the digital signature of the certificate, ensuring the integrity and immutability of the certificate’s content.
Thumbprint and Thumbprint Algorithm (Thumbprint and Thumbprint Algorithm): The thumbprint is the hash value of the certificate, which can confirm the integrity of the certificate. The thumbprint algorithm transforms the certificate content into a fixed-length string, often encrypted with the issuing authority’s private key to ensure authenticity.
The Working Principle of Digital Certificates
Digital certificates rely on public key encryption technology and digital signature technology to ensure communication security and identity authenticity.
Generating Certificate Requests: The certificate holder first generates a pair of keys, then packages the public key and other necessary information into a certificate request and submits it to the certificate authority.
Verification and Signing by the Certificate Authority: The certificate authority verifies the request, confirming the applicant’s identity and the validity of the public key. Once approved, it signs the applicant’s public key and related information with its private key, generating the digital certificate.
Using Digital Certificates for Identity Verification: During communication, the server sends the digital certificate to the client. The client verifies the certificate through the root certificate store built into the operating system or browser, checking if it was issued by a trusted authority, if it has expired, and if it has been tampered with. If verification passes, the client can trust the server and use the public key in the certificate to encrypt communication data.
Ensuring Data Integrity and Confidentiality: In actual communication, data is encrypted using the public key in the certificate, and only the recipient holding the corresponding private key can decrypt it. Moreover, the signature algorithm in the certificate ensures that the data has not been tampered with during transmission, safeguarding data integrity.
By understanding these encryption concepts, have you gained a deeper insight into information security? I hope this content helps you better protect your data security in the digital world. If you want to know how to use tools to generate digital certificates, feel free to continue following our subsequent content!
For practice with real questions, you can follow “Zhongzhi Education Classroom” for question practice!
ClickRead the original text for detailed video explanations of real questions!