
#Abstract#
Traditional anomaly localization of IoT sensor nodes suffers from poor accuracy due to neglecting the actual communication range limitations of the nodes. This paper proposes a study on anomaly localization of IoT sensor nodes based on the differential evolution algorithm. By utilizing known anchor nodes and the communication distances to unknown nodes, the positions of the unknown nodes are estimated, constructing a minimized error metric function while considering the contributions of all anchor nodes and communication range constraints. The differential evolution algorithm’s population iteration operation approximates the true positions, effectively localizing the anomalous nodes. Test results indicate that the proposed method achieves a higher coverage rate for anomalous nodes and demonstrates ideal localization accuracy.


0
Introduction
With the rapid development of IoT technology, sensor nodes, as the fundamental components of IoT systems, play a crucial role in fields such as environmental monitoring, smart homes, and industrial automation. Sensor nodes are responsible for collecting various environmental parameters and transmitting them to a data center for analysis and processing[1-2]. However, in practical applications, due to environmental factors, hardware failures, or human interference, sensor nodes may exhibit anomalies, leading to inaccurate data collection or transmission failures, which in turn affects the overall performance and reliability of IoT systems[3]. Therefore, how to achieve anomaly localization of IoT sensor nodes and timely detect and repair faulty nodes has become one of the key issues that urgently need to be addressed in the IoT field.
Currently, relevant scholars have conducted in-depth research on sensor node localization algorithms.
Reference [4] enhances the identification capability of anomalous nodes by simulating the movement of ants in the search space and the pheromone update mechanism, introducing the signal strength differences between nodes as weights. However, in complex and variable wireless environments, signal strength is easily interfered with by obstacles, leading to inaccurate pheromone weight calculations, which in turn affects localization accuracy.
Reference [5] achieves precise localization of nodes by simulating the process of cuckoos searching for optimal nests, while introducing the relative positional relationships between nodes as constraints to ensure the consistency of localization results. However, the performance of this algorithm highly depends on the accuracy and comprehensiveness of the fitness function. In practical environments, the construction of the fitness function is often influenced by various uncertainties such as noise and interference, resulting in poor localization accuracy.
Reference [6] utilizes high-pass graph filters to obtain high-frequency components of network signals, dividing heterogeneous hash networks to determine subgraph feature frequency components, comparing suspected anomalies with subgraph node sets to detect anomalous nodes, and estimating distances based on the hops between anchor nodes and unknown nodes, filtering out anomalous factors to optimize the global optimal solution for anomaly localization. However, this method faces issues in large-scale complex networks, such as high computational load for signal processing, susceptibility to interference, and the impact of single basis for area division on localization accuracy and efficiency.
The differential evolution algorithm simulates the iterative mechanism of biological evolution to search the solution space, capable of finding global optimal or near-optimal solutions. This study aims to propose a method for anomaly localization of IoT sensor nodes based on the differential evolution algorithm to address the low accuracy and susceptibility to environmental interference of traditional localization methods. By utilizing the communication distance information between known anchor nodes and unknown nodes, a minimized error metric function is constructed, combined with the population iteration operation of the differential evolution algorithm to accurately capture the positions of anomalous nodes.
1
Method for Anomaly Localization of IoT Sensor Nodes Based on Differential Evolution Algorithm
1.1
Description of the Anomaly Localization Problem for IoT Sensor Nodes
To achieve anomaly localization of IoT sensor nodes, the communication distance information between known anchor nodes and unknown sensor nodes is first utilized to estimate the positions of the unknown nodes while constructing a minimized error metric function[7]. Assume there are M known anchor nodes in the IoT sensor network with coordinates (x1,y1),(x2,y2),…,(xM,yM), and N unknown sensor nodes[8-9]. Some of these nodes may exhibit certain anomalous behaviors. The modeling objective of this paper is to utilize the communication distance information between anchor nodes and unknown nodes, along with the possible wireless communication radius, to determine the positions of those anomalous nodes. Let the coordinates of unknown node i and anchor node j be (xi,yi) and (xj,yj), respectively, then the distance dij is expressed as
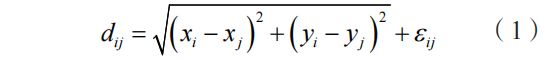
Where: εij is the measurement error.
Due to the presence of measurement errors, this paper seeks a set of position coordinates that minimizes the error metric[10-11], resulting in the function expression as follows:
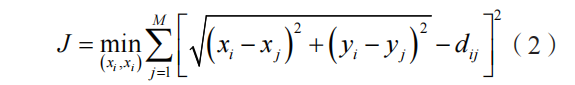
Through the above operations, the anomaly localization problem of IoT sensor nodes is modeled, transforming it into a problem of minimizing the sum of squared errors between observed and predicted position coordinates.
1.2
Wireless Communication Range and Non-Negative Position Constraints of Sensor Nodes
This paper comprehensively considers the contributions of all anchor nodes to the localization of unknown nodes, constructing a fitness function and imposing wireless communication range constraints and non-negative position coordinate constraints to achieve boundary condition design for anomaly localization. To consider the contribution levels of different anchor nodes to the localization results, a weight coefficient wij is introduced. It is mainly influenced by distance factors[12-13], calculated as follows:
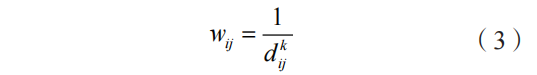
Where: k is a positive parameter used to adjust the rate at which weights change with distance; when k≥1, the weight decreases faster with increasing distance; when k<1, the weight decreases more slowly with increasing distance[14].
Since the wireless communication range of IoT sensor nodes is limited, it is necessary to ensure that the distance between unknown nodes and anchor nodes does not exceed the maximum communication radius R. The specific constraint condition is as follows:
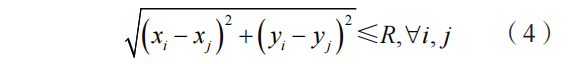
In most cases, the position coordinates of IoT sensor nodes are non-negative. Therefore, it is necessary to add the constraints xi≥0,yi≥0,∀i to restrict the position coordinates of unknown nodes.
1.3
Anomaly Localization of IoT Sensor Nodes Based on Differential Evolution Algorithm
The differential evolution algorithm has strong global search capabilities and is adept at handling high-dimensional and nonlinear problems, making it suitable for the complex scenarios of anomaly localization of IoT sensor nodes. Therefore, this paper combines the differential evolution algorithm to achieve anomaly localization, with individuals representing possible sensor node positions, iterating population operations to approach the true positions of unknown nodes.
Randomly generate initial solutions, each representing a sensor node position. Assume the population size is NP, and each individual Xi=(i=1,2,…,NP) represents a two-dimensional vector of unknown node coordinates[15]. For each Xi, evaluate its performance. Then select two other individuals Xr1 and Xr2 to perform differential operations, generating a mutated individual Vi, expressed as:
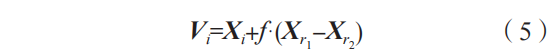
Where: f is the scaling factor used to control the magnitude of the mutation. For the obtained mutated individual Vi and the current individual, perform crossover operations to generate trial individual Ui. The specific expression is as follows:
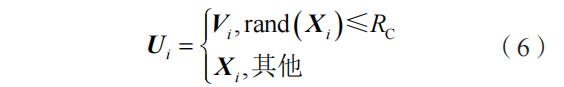
Where: RC is the crossover probability; rand(Xi) is the random number generation function. By comparing Ui and Vi, select the optimal individual as the next generation and repeat the operation until convergence[16], with the iterative result being the estimated position of the unknown nodes. If the estimated position of a certain node significantly differs from other nodes or does not meet expectations, it is regarded as an anomalous node, achieving anomaly localization.
2
Experimental Verification
2.1
Experimental Preparation
In practical IoT applications, the distribution of sensor nodes is often three-dimensional. Therefore, the experiment simulates a three-dimensional area with a side length of 120m to mimic the working scenario of the IoT sensor network. In this three-dimensional area, 60 anchor nodes are set, and their positions change randomly during each simulation run to simulate the uncertainty of node deployment in real scenarios. The coordinates of each anchor node serve as known parameters, providing critical reference for subsequent anomaly localization of nodes.
The transmission power and receiving sensitivity parameters of anchor nodes directly affect their communication capabilities and range. To simulate different performances of sensor devices in reality, various settings for these parameters are made, making the experimental results more universal and practically significant. Thirty unknown nodes are randomly distributed within the three-dimensional area, which are the target objects to be localized using the differential evolution algorithm. In the constructed sensor distribution space, the proposed method for anomaly localization based on the differential evolution algorithm is employed and compared with the localization methods based on simulated parallel ant colony algorithm (conventional method A) and improved cuckoo search algorithm (conventional method B). To ensure the fairness and effectiveness of the comparison, the parameters of the differential evolution algorithm are configured with a population size of 100, a mutation factor of 0.8, a crossover probability of 0.7, a maximum iteration count of 500, and a dimension of 3. A total of 36 sets of test data are selected to conduct anomaly localization experiments on the simulated sensor node distribution space, comprehensively evaluating the localization performance and accuracy of the proposed method by comparing the results obtained from different methods with the actual simulation results.
2.2
Results of Anomaly Localization of Sensor Nodes
The experiment retrieves the iterative convergence results of anomaly localization trajectories with 3, 4, and 5 anchor nodes, as shown in Figure 1.
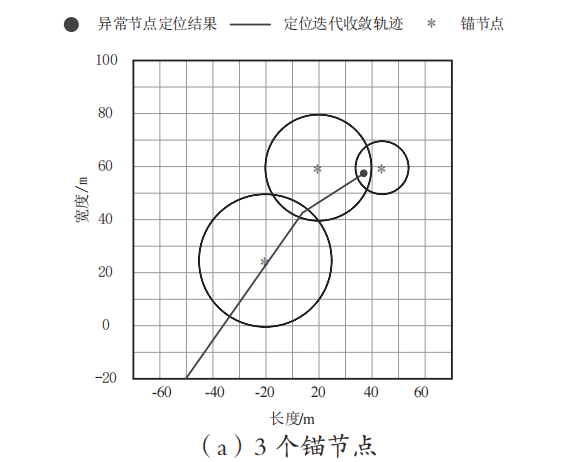
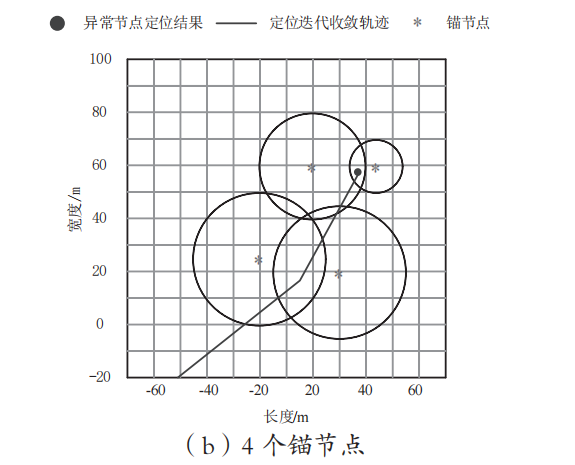
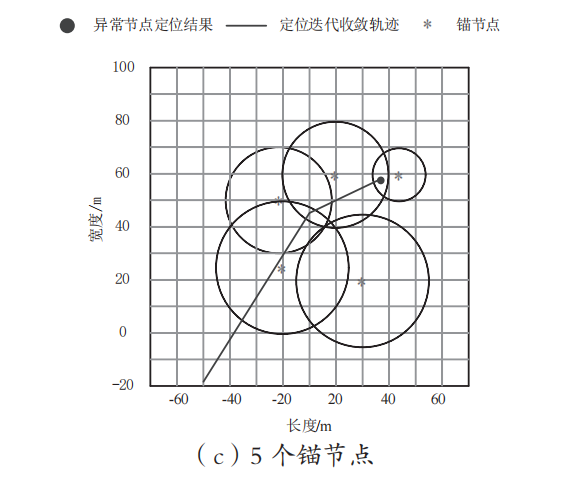
Figure 1: Iterative convergence of anomaly localization trajectories under different numbers of anchor nodes
As seen in Figure 1, the proposed algorithm can estimate the position information of anomalous nodes based on the known positional information of anchor nodes; compared to the information provided by 3 anchor nodes, the multi-anchor scenario algorithm yields more accurate localization results for anomalous nodes.
2.3
Comparison of Localization Accuracy
The experiment uses the coverage rate of anomalous nodes from different localization methods as a comparative metric to measure actual localization accuracy. This metric evaluates the proportion of anomalous nodes covered by the localization method. The higher the coverage rate, the stronger the method’s ability to handle anomalous nodes in different positions and states. The specific experimental results are shown in Figure 2.
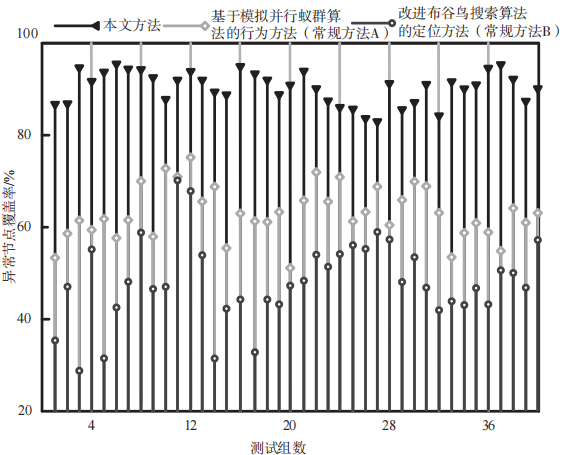
Figure 2: Comparison of coverage rates of anomalous nodes using different methods
As shown in Figure 2, the proposed method demonstrates excellent performance in terms of coverage rate for anomalous nodes, with a coverage rate significantly higher than the other two comparison methods, achieving an average coverage rate of 92.5%. This is because the differential evolution algorithm employed in this paper effectively addresses optimization problems in complex spaces, allowing the algorithm to quickly locate the precise positions of anomalous nodes.
3
Conclusion
This research has made significant progress in the field of anomaly localization of IoT sensor nodes, providing important support for the development of related technologies. Experimental results show that the proposed method achieves a coverage rate of anomalous nodes as high as 92.5%, far exceeding that of comparison algorithms, fully demonstrating its outstanding performance in localization accuracy and handling complex anomaly localization scenarios, thus providing a strong guarantee for the stable operation of IoT sensor networks.
References
Scroll up to browse
[1] Ye Miao, Cheng Jin, Huang Yuan, et al. Fusion reconstruction mechanism and contrast learning method for WSN anomaly node detection [J]. Journal of Communications, 2024, 45(9): 153-169.
[2] Zhang Hang, Wei Wei, Fan Yuancheng, et al. Surface heterogeneous wireless sensor network node localization algorithm based on similar paths [J]. Journal of Sensor Technology, 2023, 36(2): 301-308.
[3] Shan Haomin, Lin Shouhe. A wireless sensor network node localization method based on improved spider monkey algorithm [J]. Journal of Hunan University of Technology (Natural Science Edition), 2023, 33(3): 51-57.
[4] Li Lu. Adaptive localization method for anomalous nodes in wireless sensor networks based on simulated parallel ant colony algorithm [J]. Journal of Harbin Normal University Natural Science Edition, 2024, 40(1): 55-60.
[5] Li Baomi. Design of wireless sensor node localization method based on improved cuckoo search algorithm [J]. Journal of Jiamusi University (Natural Science Edition), 2024, 42(7): 48-51.
[6] Jia Wenya, Yang Hongju. Rapid localization algorithm for anomalous nodes in mobile IoT environments [J]. Journal of Sensor Technology, 2024, 37(8): 1448-1453.
[7] Yang Di, Zhao Xuan, Zhang Wen, et al. CADV-Hop localization method for wireless sensor network nodes based on classified average hop distance [J]. Laser Magazine, 2024, 45(1): 172-178.
[8] Yang Jiangfeng, Wang Wansheng, Liu Ming. Wireless sensor network localization algorithm based on molecular force model [J]. Journal of Yunnan Minzu University (Natural Science Edition), 2024, 33(6): 731-735.
[9] Qu Aiyan, Li Jianguo, Zhao Qi, et al. Wireless sensor network node localization based on fruit fly algorithm optimized Monte Carlo anchor box mobile algorithm [J]. Electrical Automation, 2023, 45(1): 86-88.
[10] Zhai Yongqi. Low-complexity wireless sensor network localization algorithm based on Bayesian hierarchical model [J]. Modern Information Technology, 2024, 8(8): 106-110.
[11] Li Hongyu, Song Shaoqian. Multi-node transmission strategy for wireless sensor networks based on UAV dynamic relay [J]. Journal of Changchun University of Technology, 2024, 45(6): 519-524.
[12] Xie Lixia, Tian Yuqi. Identification of WSN anomalous nodes based on importance score CUR matrix decomposition [J]. Computer Engineering and Design, 2024, 45(4): 997-1003.
[13] Zheng Junhua, Wei Jinhong. Detection of anomalous data streams in wireless sensor networks based on feature completion [J]. Journal of Sensor Technology, 2024, 37(6): 1061-1066.
[14] Xiang Dan, Zhai Chenkai, Lin Libin, et al. Underwater sensor network node localization method based on improved whale optimization algorithm [J]. Journal of South China Normal University (Natural Science Edition), 2024, 56(2): 119-128.
[15] Zhang Junxing, Chen Zidi, Xie Fengling. Research on wireless sensor network localization based on improved sparrow search algorithm [J]. Journal of Sensor Technology, 2024, 37(3): 524-532.
—— Intelligent IoT Technology
Content Source | “Intelligent IoT Technology” Vol. 57, No. 1 (2025)
Original Author | Hu Xingtong
Chart Production | “Intelligent IoT Technology”
Original Statement: This article is an exclusive original work of “Intelligent IoT Technology” and may not be reproduced without permission. Feel free to share it with friends to benefit more people. Respect originality and work together to maintain a good online environment! For reprints, please contact us, and kindly indicate the source when quoting.


Follow our public account for more exciting content

■ Research and Application of Fundus Image Segmentation Technology Based on Image Projection Network
■ Selected News | Policy Guidance, Industry Dynamics, and Technological Insights in AI and IoT – Issue 33
■ Design and Implementation of Intelligent Security System Based on IoT Technology
■ Application of Digital Base in Virtual Manufacturing Platform in Automotive Industry – Case Display of “China Intelligent Manufacturing Technology Progress”
■ Research on Intelligent Bird Scaring Method at Airports Based on Biological Characteristics
■ Has your phone upgraded to 5G-A yet?

Share, recommend, and like; at least I want to have one!