Abstract: In the digital age, the rapid delivery and efficient deployment of software applications are crucial for the success of enterprises. Traditional application deployment methods are often complex and time-consuming, leading to operational difficulties and resource waste. Enterprises face the constant change of software functional requirements and need to quickly respond to product changes and deploy software to generate benefits. With the development of cloud-native technologies such as containerization and microservices, technical guarantees have been provided for frequent service releases, rapid delivery, and risk feedback. This system is based on the cloud-edge collaborative scenario, utilizing cloud-native, cloud-edge collaboration, and secure data channel technologies to achieve a remote security operation and maintenance system that integrates local cloud and remote services.
With the digital transformation and upgrading of enterprises, businesses are gradually becoming internet-based, multi-cloud, and mobile. The boundaries between internal and external networks are becoming increasingly blurred. At the same time, the continuous upgrading of offensive and defensive technologies, as well as the pressure for drill assurance from regulatory bodies, make the network security challenges faced by enterprises increasingly severe. Traditional network security protection architectures and deployment operation and maintenance methods can no longer meet the increasingly complex security needs. In addition, constrained by the cost pressure of security investments, enterprises need a new model of security operation and maintenance that is simpler, safer, smarter, and more convenient to use and maintain.
Software-Defined Wide Area Network (SD-WAN) is a collection of technologies that mainly applies software-defined networking technology to manage wide area networks. SD-WAN technology uses virtualization technology to simplify the management and operation of data centers, applying relevant technologies on top of wide area networks, thus simplifying enterprise-level users’ control over wide area networks.
The cloud-edge collaborative architecture is an emerging computing model applied in various industries and fields, such as smart cities, smart transportation, and smart retail in IoT scenarios. It aims to integrate cloud computing and edge computing to achieve more efficient data processing and decision support in cloud-native scenarios. The continuous evolution of cloud-edge collaboration technology has become key to achieving deeply integrated cross-layer services. Its typical architecture consists of: the cloud providing data processing, collection, computation, and central business logic processing; the edge providing data collection, requesting data from the cloud, and receiving commands from the cloud. Often, one cloud will be associated with multiple edge devices, leading to complex operations for deploying, maintaining, and upgrading cloud-edge services. With the help of cloud-edge collaboration, enterprises can only allow legitimate and trusted terminal devices to access the network for collaborative computing and security protection.
Relying on the SD-WAN network as the underlying network access, this paper designs a remote security operation and maintenance system based on cloud-edge collaboration technology, aiming for rapid response and improved remote operation and maintenance efficiency.
1. Research Status
1. Research Status
1.1 Current Status of Remote Security Operation and Maintenance
With the continuous development of technology, convenience and automation have become important trends in the deployment and operation of security devices. How to provide fast, efficient, and high-quality services is a significant challenge for relevant security enterprises. Cloud-edge collaboration, as the core technological architecture for promoting remote security operation and maintenance systems, plays an increasingly prominent role. Therefore, from both technical and application perspectives, there is a need to establish a unified, intuitive, and automated security operation and maintenance system that automatically realizes resource integration, location tracking, and predictive analysis, which has profound significance for reducing operation and maintenance costs and improving response rates, aiming to shift from a passive operation and maintenance model focused on acceptance to a proactive service model focused on prevention. The in-depth application of cloud-edge collaboration technology has brought new changes to various industries. Edge products led by intelligent terminals of cloud-edge collaboration technology are gradually occupying an important position in smart operation and maintenance. Combined with high-tech intelligent products, they not only achieve high reliability in remote image and data collection and analysis but also enable high-fidelity transmission of real-time dynamic data and images, bringing new opportunities for remote security operation and maintenance work.
In response to the challenges and characteristics of the aforementioned remote security operation and maintenance system, many scholars are committed to researching technologies such as automated rapid deployment, configuration management, and intelligent monitoring and early warning to improve the management efficiency and protection capability of security devices. Operation and maintenance personnel at all levels are increasingly focusing on the timeliness and defect elimination rates of on-site operations. Literature [4] summarizes the implementation process of existing intelligent operation and maintenance into three stages: acquiring various types of data (indicators, logs, call chains, configuration files, workflows, and multimedia data), preprocessing the collected data, and visualizing the analysis results. Additionally, in a review of future trends, some scholars have adapted intelligent operation and maintenance technologies to the maintenance objects of virtualization technologies (such as hypervisors, virtual machines, and containers) to accommodate more complex operation and maintenance scenarios.
1.2 Research Needs for Remote Security Operation and Maintenance
With the continuous development of offensive and defensive technologies, as well as the drill assurance pressure from regulatory bodies, the construction of security protection in various industries is gradually shifting from a pile of security products to the delivery of security services. The operational assurance model is evolving from security operation and maintenance to security operations, and teams of on-site personnel are being formed to further enhance security protection capabilities. However, constrained by cost pressures for security investments, enterprises still face severe challenges during the security protection process, such as the quality of security teams not being effectively guaranteed, continuous coverage of security threat monitoring being insufficient, insufficient personnel during critical periods, inadequate attention to threat alerts, and delays in security response times, leaving opportunities for network attacks and resulting in frequent security incidents. How to save security investment costs and improve security operation efficiency is an urgent issue that needs to be addressed under the trend of network security service. Therefore, there is an urgent need to build a comprehensive three-dimensional remote security operation and maintenance system that allows remote security protection services to be provided for enterprises, enhancing overall network security.
2. Remote Security Operation and Maintenance System Architecture and Implementation
2. Remote Security Operation and Maintenance System Architecture and Implementation
2.1 Overall System Architecture
The cloud-edge collaborative remote security operation and maintenance system is based on a cloud-native architecture, using the Edge Security Service Gateway (ESSG) as a carrier. Through the shared services of the cloud security operation center, it provides integrated cloud-edge collaborative security operations to empower remote security, achieving 7×24 h remote monitoring and handling of security data and security events, saving costs for clients’ security operation construction, and improving the efficiency of security operation assurance work. The system mainly consists of modules such as the cloud security operation center, virtual operation backbone network, and edge security service gateway, as shown in Figure 1.
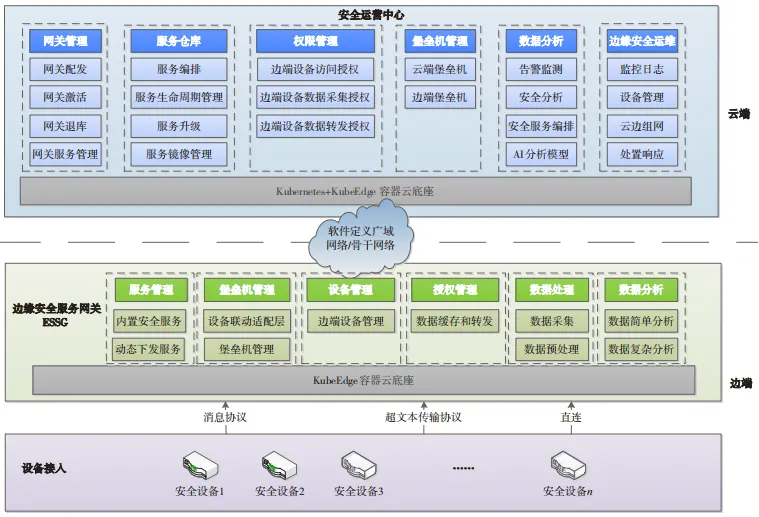
Figure 1 Overall Architecture of the Remote Security Operation and Maintenance System
The cloud security operation center consists of a security operation platform and security experts. The security operation platform has capabilities such as monitoring analysis, command management, security operation and maintenance, asset management, threat intelligence, and website cloud defense. Security experts are composed of operation delivery personnel and offensive and defensive penetration personnel. Clients can access the operation center through ESSG and utilize shared platform tools and personnel team services to conduct 7×24 h monitoring analysis, response handling, and other remote security operation and maintenance services as needed.
The virtual operation backbone network is an integrated foundational support network that connects the cloud operation center with the edge client networks, consisting of SD-WAN access points (Point-of-Presence, PoP) distributed across the country. The range includes data centers of various network service providers, public cloud nodes, etc., belonging to the logical link of the internet. Through proprietary virtual network tunnel protocols and internet transmission status monitoring, combined with the cloud operation center’s network control platform, it optimizes routing site selection and improves network transmission quality and cloud-edge collaboration efficiency.
ESSG is an essential service tool for the remote security operation and maintenance system. It is equipped with the SD-WAN access foundational module of the security operation backbone network and a security data collection module, capable of establishing a secure connection with the cloud security operation center. It adopts a Docker architecture to achieve dynamic combination of security components, meeting clients’ personalized security hosting needs. At the same time, it can provide two modes of hardware gateway and image deployment according to different client network environments, achieving full-scene coverage of traditional data center and cloud network security hosting.
2.2 Analysis of Remote Security Operation and Maintenance Scenarios
The remote security operation and maintenance system deploys central management services, related business modules, and data processing modules in the cloud, utilizing the built-in collector of ESSG to collect security logs from the client side and dynamically transmit them to the cloud security operation center. This establishes a full-scene security hosting model both on the cloud and at the edge, achieving security visibility and collaborative response in the cloud, and through the data analysis center in the cloud, analyzing massive security logs, intelligently discovering security threats, and utilizing ESSG for security device linkage handling, achieving human-machine collaborative security hosting, with remote security operation and maintenance mainly covering the following three scenarios.
2.2.1 Cloud-Edge Collaborative Service Remote Security Service Delivery
The cloud-edge collaborative service empowerment process is shown in Figure 2, detailed as follows:
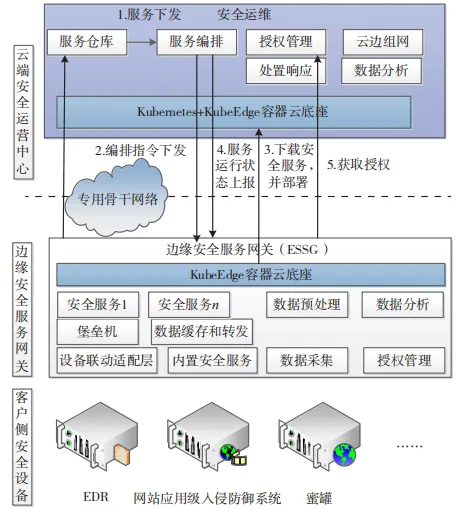
Figure 2 Cloud-Edge Collaborative Remote Security Service Delivery Scenario
(1) Service Issuance. Through ESSG, link the cloud security operation center’s service warehouse, dynamically extending the security service capabilities in the service warehouse to the edge, achieving functions such as immediate availability and destruction of security services on the edge security service gateway, ensuring that gateway storage and computing resources are not occupied.
(2) Orchestration Command Issuance.
(3) Downloading and Deploying Security Services.
(4) Reporting Service Operation Status.
(5) Authorization Acquisition. The cloud issues security services to the edge and needs to obtain user authorization while monitoring the operation status of the edge services from the cloud.
2.2.2 Cloud-Edge Collaborative Remote Emergency Response Handling
After the deployment of ESSG, a dedicated operation and maintenance channel is automatically established with the operating center’s security services. After obtaining user authorization, the operation center can conduct emergency responses such as vulnerability scanning and Internet Protocol (IP) blocking handling. Depending on different scenarios, the handling processes can be divided into built-in security service handling processes and security service handling processes, as shown in Figure 3, detailed as follows:
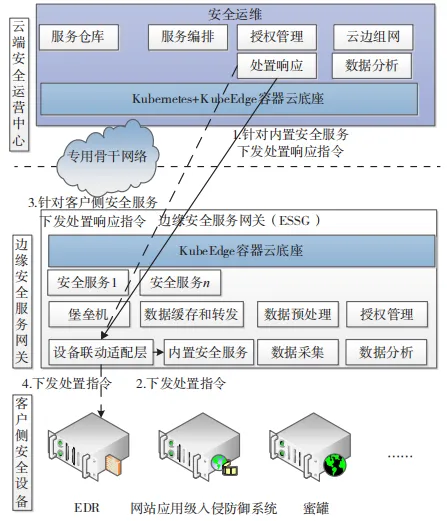
Figure 3 Cloud-Edge Collaborative Remote Emergency Response Handling Scenario
(1) Security Service Handling Process.
① The emergency response module issues handling response commands to the device linkage adaptation layer for built-in security services;
② The device linkage adaptation layer issues commands to the built-in security service module on ESSG.
(2) Client-Side Security Service Handling Process.
① The emergency response module issues handling response commands to the device linkage adaptation layer for client-side security services;
② The device linkage adaptation layer issues commands to the endpoint detection and response (EDR) of the client-side security devices.
2.2.3 Cloud-Edge Collaborative Remote Operation and Maintenance Risk Situation Monitoring
The security data collection module of ESSG achieves secure interaction among the cloud, edge, and endpoint based on dedicated network channels and permission management models. Through dedicated security data channels, remote operation and maintenance commands are securely issued, and the permission management model controls the operations of various operation and maintenance personnel, ensuring the secure use of remote operation and maintenance tools. The cloud-edge collaborative remote operation and maintenance risk situation monitoring is shown in Figure 4, detailed as follows:
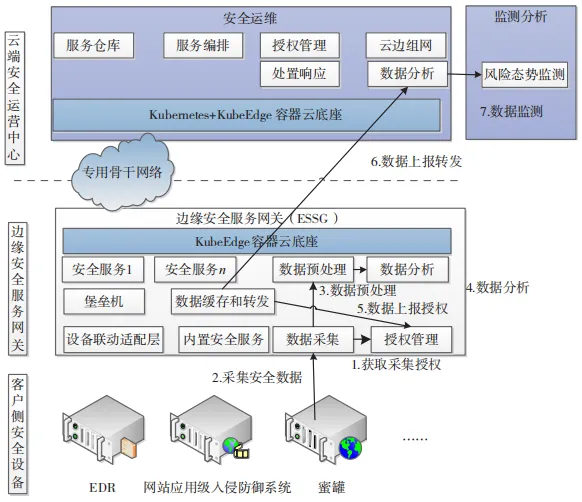
Figure 4 Cloud-Edge Collaborative Remote Operation and Maintenance Risk Situation Monitoring Scenario
(1) Obtaining Collection Authorization. Use the authorization management module on ESSG for permission judgment.
(2) Collecting Security Data. Passively collect alarm data from all security devices and systems on the client side.
(3) Data Preprocessing. Synchronize the collected data from the client-side security devices to ESSG for paradigm parsing and preprocessing, and label the collected data, marking the source device information to distinguish data from different client units.
(4) Data Analysis. Conduct analysis through the data analysis module on ESSG.
(5) Data Reporting Authorization. Obtain data reporting permission based on the authorization management module.
(6) Data Reporting and Forwarding. The data that needs to be reported is encrypted and transmitted back to the operation center’s analysis platform via the SD-WAN tunnel.
(7) Data Monitoring. The cloud operation center conducts automated fusion analysis and intelligence collision of the reported data while performing 7×24 h continuous monitoring. For security threat events generated during the client’s security situation monitoring, the operation center’s operation team provides real-time security notifications to users and regularly pushes monitoring reports. Additionally, based on client needs, the operation center can regularly push threat intelligence to ESSG for clients to obtain artificial intelligence and integrate machine-readable intelligence with local security devices, enhancing clients’ local security situation monitoring capabilities. At the same time, it can link to the emergency response handling module to achieve remote security handling operation and maintenance based on security analysis.
2.3 Key Technologies
The remote security operation and maintenance system based on cloud-edge collaboration technology relies on Kubernetes and KubeEdge as the underlying foundation to achieve the image-based management of security services and cloud-edge collaboration, thereby enabling dynamic management of edge ESSG and dynamic issuance of security services. The remote security operation and maintenance system is deployed in the cloud operation center, where operation and maintenance personnel can select the required security service images and the corresponding edge ESSG for deployment on the edge ESSG. The edge security data channel is used to ensure the data upload of edge services or the issuance of cloud service orchestration commands.
The key to the remote security operation and maintenance system based on cloud-edge collaboration technology lies in the construction of the service warehouse, service orchestration, service operation monitoring, and secure data channels. This system has the following features: unified service warehouse and service monitoring of cloud-edge collaboration, service orchestration of cloud-edge collaboration, and dedicated data channels.
2.3.1 Service Warehouse Based on Virtual Containerization Technology
The service warehouse is used to store security service products, which refer to the security service images on ESSG. In order to unify the service operating environment and avoid potential environmental anomalies during deployment, ESSG uses Docker container technology as the technical foundation, isolating only the running environment of applications while allowing services to share the same operating system [7]. The service usage process of the service warehouse is shown in Figure 5.
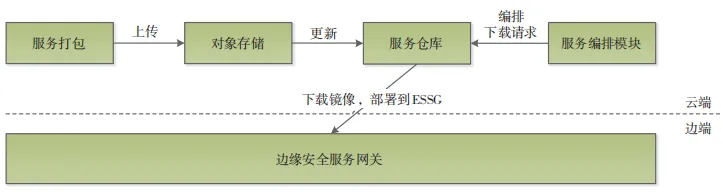
Figure 5 Service Warehouse Usage Process
The specific operational process is as follows:
(1) Production of Service Products. Developers package services into image files using Docker technology and store them as .tar format files, outputting corresponding configuration parameter documents.
(2) Uploading Service Products. Operation and maintenance personnel upload service product files and configuration parameters to the service warehouse for storage, and then synchronize updates to the corresponding image repository (Harbor) based on specific business needs, where version management of service products is required.
(3) Running Service Products. Based on needs, operation and maintenance personnel utilize the service orchestration module and the dedicated backbone network’s data security channel to issue image files to the remote ESSG for deployment.
(4) Updating Service Products. When a security service needs to be upgraded, the service must be repackaged as an image file and uploaded again, synchronized to Harbor, where each version is a separate product that needs to be backed up.
2.3.2 Service Orchestration Based on Cloud-Edge Collaboration Technology and Container Orchestration Technology
After services are packaged and managed through virtual containerization technology, they need to be deployed to edge servers, which is also the core module of remote security operation and maintenance. In this operation and maintenance scenario, it is necessary to transform the service image files into running container states and run them on the edge servers, and this process needs to be automated. To address these two core technical points, this paper adopts Kubernetes container orchestration management technology and KubeEdge cloud-edge collaboration technology.
Kubernetes provides orchestration and management capabilities for large-scale deployment of containers, enabling the construction of multi-container application services, scheduling or scaling these containers on clusters, and managing their health states over time. Kubernetes solves many common issues arising from container proliferation by classifying containers into Pods. A Pod provides an abstraction layer for grouping containers, assisting in workload scheduling and providing necessary services such as networking and storage for these containers. Other components of Kubernetes help users balance the load on Pods to ensure an adequate number of containers support user workloads [9]. The main advantage of using Kubernetes in a production environment lies in its ability to schedule and run containers on physical or virtual machine clusters. More broadly, Kubernetes helps users build container-based infrastructure in production environments. Since Kubernetes is essentially an automation platform for operation and maintenance tasks, users can perform operations supported by other application platforms or management systems, with the only difference being that the operation objects are containers.
KubeEdge extends the orchestration capabilities of containerized applications to the edge hosts. It is built on top of Kubernetes and provides infrastructure support for network applications, deployment, and metadata synchronization between cloud and edge, thus enabling edge computing and extending container orchestration capabilities to edge nodes and devices while providing infrastructure support for networking, application deployment, and metadata synchronization between cloud and edge. KubeEdge also supports Message Queuing Telemetry Transport (MQTT) and allows developers to write custom logic and enable devices with certain resources to communicate at the edge.
By leveraging Kubernetes container orchestration technology combined with KubeEdge cloud-edge collaboration technology, the service deployment of cloud-edge collaboration is completed, realizing the demand-driven delegation of security service capabilities to the edge.
The specific underlying operation process is as follows:
(1) Service Startup. First, when operation and maintenance personnel need to deploy a new service product to the edge, they select a service and its corresponding version in the service orchestration module, determining the uniqueness of the service. Next, they directly send a deployment command, and the service orchestration module will issue the product from the service warehouse to the edge for running. The service orchestration module can view the running status and log output of the service in real-time, confirming whether the service is running normally.
(2) Service Update. This module has a rolling update feature to ensure that existing business and functionalities are not affected. A rolling update means that when a new version is updated, the original service will not be stopped immediately. Instead, the new service will be started first, and once it runs normally, all network traffic will be directed to the new service, at which point the old service will be stopped. If an exception occurs during the startup of the new service, traffic will not be directed to it. This way, throughout the update process, the service runs normally, not affecting existing business and preventing data loss during service updates. For example, when upgrading a security service from version 1.0 to 1.1, once the 1.1 version of the service is uploaded to the service warehouse, both versions can be seen on the service list of the service warehouse, and the service status version running on the ESSG to be updated will be version 1.0, allowing the 1.1 version number to be sent to the service orchestration module for updating.
(3) Service Stopping. When a service needs to be stopped, operation and maintenance personnel first send a stop request to the service orchestration module. The orchestration module generates a stop command based on the service name that needs to be stopped and the information of the edge ESSG where the service is located, and finally issues the stop command directly to the edge server to delete that service.
2.3.3 Operation Monitoring Based on Replication Controller and Kubelet Technology
To ensure the safe and reliable operation of edge services, this system guarantees the secure operation of the system from two dimensions: normal operation of services and status monitoring.
First, it is necessary to ensure that services are running normally. After edge services run through Kubernetes, the Replication Controller (RC) of Kubernetes ensures that containers remain in a continuously running state, thus guaranteeing high availability of services. The working principle of RC is to continuously monitor the running state of Kubernetes containers, and if an anomaly is found, RC will control Kubernetes to start a new Pod, thus ensuring the high availability of that service. A Pod is the basic unit of deployment in Kubernetes. A Pod consists of one or more containers that share the same network namespace and IP address. In simple terms, services run in containers within Pods, and Pods run on servers.
Secondly, to achieve precise status monitoring of the edge, it is necessary to enable the cloud to monitor the running status of all edge services. This system integrates each edge node into the cluster through Kubelet technology, achieving cloud monitoring of CPU utilization, memory usage, disk pressure, and network bandwidth of edge servers, as well as monitoring the corresponding index data of the running Pod environment for each service. Through remote monitoring from the cloud, the resource usage of each Pod on the server can be intuitively observed, providing data guidance for operation and maintenance and development personnel, facilitating daily maintenance and iterative upgrades by operation and maintenance personnel, thus achieving reasonable resource utilization.
2.3.4 Dedicated Data Channels Based on SD-WAN Technology
The dedicated data channel between the cloud and edge is secured by the inherent security of the SD-WAN network, which employs identity authentication, data encryption, data validation, and permission control measures to prevent unauthorized access, information leakage, and data tampering. Particularly for the access scenarios of edge security service gateways (hereinafter referred to as “service gateways”), the SD-WAN solution is based on a zero-trust security concept, strictly verifying the identity information of service gateways to prevent identity spoofing and ensuring that only legitimate and trusted service gateways can access, thereby avoiding unauthorized remote device access. The data communication of this system is primarily based on the dedicated data channels of SD-WAN.
In addition to utilizing SD-WAN technology, this system has also established different security mechanisms based on different data types to ensure the security of data channels. The security mechanisms include the following two points:
(1) Issuance of Service Orchestration Commands. Issued through the Websocket data channel of KubeEdge, which encrypts data based on Websocket+Tls and verifies it through cloud tokens, ensuring the security of orchestration command data.
(2) Data Access of Cloud-Edge Services. Data forwarding is performed through this service, primarily utilizing EdgeMesh for data forwarding of cloud-edge services. The EdgeMesh project addresses complex communication issues in edge computing scenarios, with a centralized EdgeMesh-Server acting as a relay component to assist other nodes in network penetration and traffic forwarding. This component has high availability, capable of handling performance bottlenecks and single-point failure scenarios, ensuring more stable system operation, and covering multiple pain points of edge networks, such as distributed dynamic relay connection scenarios and network autonomy scenarios in private local area networks.
Through the explanation of the security operation and maintenance system architecture, scenarios, and key technologies, it can be seen that this system can solve the deployment issues of individual services. First, each service is packaged as an image product, which can run in any environment and contains all the environments needed for service operation, solving the problem of various plugins that need to be installed during service operation. Second, through Kubernetes’ container orchestration tools, services are orchestrated for deployment and updates, and cloud-edge collaborative management is achieved through KubeEdge, extending the automated orchestration deployment capabilities to remote locations, truly realizing service management, automated deployment, and monitoring of the service lifecycle. Finally, the security operation and maintenance system realizes the automation and streamlining of processes such as service production, deployment, upgrading, monitoring, and termination, while this process requires no additional command-line operations, allowing all services to be completed with a single click.
3. Application of the Remote Security Operation and Maintenance System
3. Application of the Remote Security Operation and Maintenance System
The remote security operation and maintenance system mainly targets areas such as cloud-edge collaboration, edge computing, and security operation and maintenance, focusing on enhancing security protection capabilities and efficiency while saving security investment costs. Under the cloud-edge collaborative mechanism, it can achieve on-demand dynamic allocation, elastic scaling, automated deployment, and upgrading of long-term security capabilities. The deployment of the remote security operation and maintenance system is shown in Figure 6.
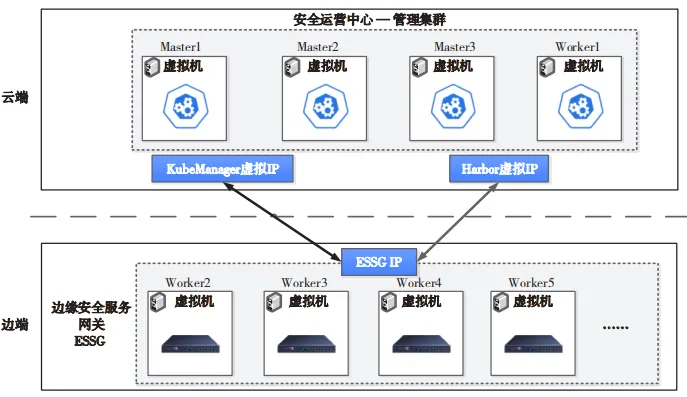
Figure 6 Deployment of the Remote Security Operation and Maintenance System
The management end cluster in the remote security information deployment mainly consists of Master nodes deployed in the cloud environment, used for managing the remote security operation and maintenance system of cloud-edge collaboration, such as the registration and activation of edge ESSG, service orchestration, etc. The edge ESSG acts as a Worker node of the cloud node, primarily carrying users’ edge businesses and linking with the cloud operation center.
Operation and maintenance personnel first complete the production and activation of edge security service gateways through the operation and maintenance module of the cloud operation center. Then they manage the addition and deletion of remote security services, service lifecycle policy management, service start-stop, monitoring, configuration, and publishing. Finally, they apply for remote security operation and maintenance operation permissions. Clients can log into the cloud security operation center to complete the approval of remote security operation and maintenance operation permissions and dynamically monitor the edge security service gateways.
In the business scenarios of edge data collection and analysis, unified management can be achieved at the operation center, realizing low latency and high availability of services. After ESSG connects to the cloud-end cluster management, it is uniformly managed by the cloud operation center. Operation and maintenance personnel unify the networking, activation, initialization, and monitoring of ESSG. As a connection terminal with rich capabilities for interfacing security devices, ESSG connects to security terminals through a security device adaptation layer for data collection and processing. It outputs processed data and reports it to the operation center for comprehensive analysis, fully utilizing cloud resources and processing capabilities to ultimately achieve a business closure and high-efficiency production optimization, providing clients with high-performance and convenient data collection and analysis services. ESSG can dynamically upgrade the security device adaptation layer in the cloud as needed, continuously enhancing the interfacing capabilities of security devices, and can also issue algorithms from the cloud data center to the edge ESSG, decoupling algorithms from devices while customizing data processing strategies according to specific client situations, achieving remote automated deployment and significantly reducing security operation and maintenance costs.
To visually display the running status of edge services, this system provides a visual big screen solution, displaying the current running status of all services through service dimensions, illustrating the network associations and data flow between various services through relationship graphs, while deeply drilling into the resources related to each service, such as deployed Node resources, Pod status, and the current service’s start-stop history and running logs; truly achieving one-screen monitoring of the entire system.
4. Conclusion
4. Conclusion
The remote security operation and maintenance system based on cloud-edge collaboration not only solves the remote deployment issues of individual services but also realizes uninterrupted upgrades of services, optimizing remote operation and maintenance for edge security devices and edge ESSG. Users can perform one-click remote operations for service deployment, upgrades, and daily operation and maintenance management of edge ESSG at the cloud operation center, eliminating the need to log into multiple remote machines individually and input various complex commands for service deployment, and avoiding routine inspections to check service status. At the same time, this paper also addresses the security risks associated with remote login to servers during server operation and maintenance management. It can be seen that compared to traditional security operation and maintenance methods, the remote security operation and maintenance system based on cloud-edge collaboration proposed in this paper truly supports security operation and maintenance and can effectively address the challenges faced by traditional enterprises in digital transformation. It is hoped that this can provide a reference for remote security operation and maintenance.
Original Source: Journal of Information Security and Communication Security
