
Dog
Yu
 If this article is helpful to you
If this article is helpful to you
 Please give a “like” or “view” to support us
Please give a “like” or “view” to support us
 Thank you~
Thank you~
This article is quite lengthy, totaling around 7000 words, so it is recommended to bookmark it for leisurely reading~~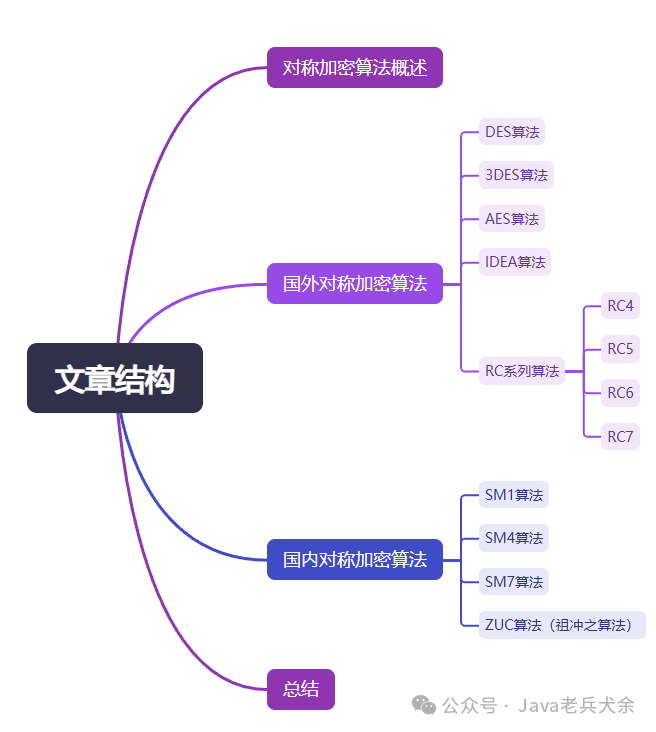 1. Overview of Symmetric Encryption Algorithms Symmetric encryption algorithms are one of the cornerstones of modern cryptography, characterized by the use of the same key for both encryption and decryption. This method of encryption originated from ancient substitution ciphers, the most famous being the Caesar cipher, which encrypts by shifting the alphabet by a fixed amount. With the development of cryptography, symmetric encryption algorithms have evolved from simple substitutions to complex modern algorithmic systems. Early symmetric encryption primarily relied on character substitution and permutation until the 1970s when IBM developed DES (Data Encryption Standard), marking the beginning of modern symmetric encryption algorithms. DES employs a Feistel network structure and enhances encryption strength through multiple rounds of iterative operations, a design philosophy that profoundly influenced subsequent algorithm development. Symmetric encryption algorithms can be divided into two main categories based on how they process data: block ciphers and stream ciphers. Block ciphers encrypt plaintext by dividing it into fixed-length blocks, with representative algorithms including DES and AES; stream ciphers continuously encrypt data streams, such as RC4 and the ZUC algorithm. Each of these algorithm types has its advantages, with block ciphers offering higher security and stream ciphers providing faster encryption and decryption speeds. Compared to asymmetric encryption, the greatest advantage of symmetric encryption lies in its fast computation speed and high encryption efficiency. This makes it particularly suitable for encrypting large amounts of data, widely used in network communications, data storage, and other scenarios. However, symmetric encryption also faces challenges in key distribution and management, as both parties must securely share the key beforehand. Modern cryptographic systems typically employ a combination of “symmetric encryption + asymmetric encryption” to securely transmit the symmetric encryption key. During the encryption process, symmetric encryption algorithms transform plaintext into ciphertext through a series of complex mathematical operations. These operations typically include substitution, permutation, and XOR, ensuring encryption strength through multiple rounds of iteration. The decryption process is the inverse operation of encryption, using the same key to revert ciphertext back to plaintext. The entire process must ensure that even if an attacker obtains the ciphertext, they cannot deduce the plaintext without knowing the key.
1. Overview of Symmetric Encryption Algorithms Symmetric encryption algorithms are one of the cornerstones of modern cryptography, characterized by the use of the same key for both encryption and decryption. This method of encryption originated from ancient substitution ciphers, the most famous being the Caesar cipher, which encrypts by shifting the alphabet by a fixed amount. With the development of cryptography, symmetric encryption algorithms have evolved from simple substitutions to complex modern algorithmic systems. Early symmetric encryption primarily relied on character substitution and permutation until the 1970s when IBM developed DES (Data Encryption Standard), marking the beginning of modern symmetric encryption algorithms. DES employs a Feistel network structure and enhances encryption strength through multiple rounds of iterative operations, a design philosophy that profoundly influenced subsequent algorithm development. Symmetric encryption algorithms can be divided into two main categories based on how they process data: block ciphers and stream ciphers. Block ciphers encrypt plaintext by dividing it into fixed-length blocks, with representative algorithms including DES and AES; stream ciphers continuously encrypt data streams, such as RC4 and the ZUC algorithm. Each of these algorithm types has its advantages, with block ciphers offering higher security and stream ciphers providing faster encryption and decryption speeds. Compared to asymmetric encryption, the greatest advantage of symmetric encryption lies in its fast computation speed and high encryption efficiency. This makes it particularly suitable for encrypting large amounts of data, widely used in network communications, data storage, and other scenarios. However, symmetric encryption also faces challenges in key distribution and management, as both parties must securely share the key beforehand. Modern cryptographic systems typically employ a combination of “symmetric encryption + asymmetric encryption” to securely transmit the symmetric encryption key. During the encryption process, symmetric encryption algorithms transform plaintext into ciphertext through a series of complex mathematical operations. These operations typically include substitution, permutation, and XOR, ensuring encryption strength through multiple rounds of iteration. The decryption process is the inverse operation of encryption, using the same key to revert ciphertext back to plaintext. The entire process must ensure that even if an attacker obtains the ciphertext, they cannot deduce the plaintext without knowing the key.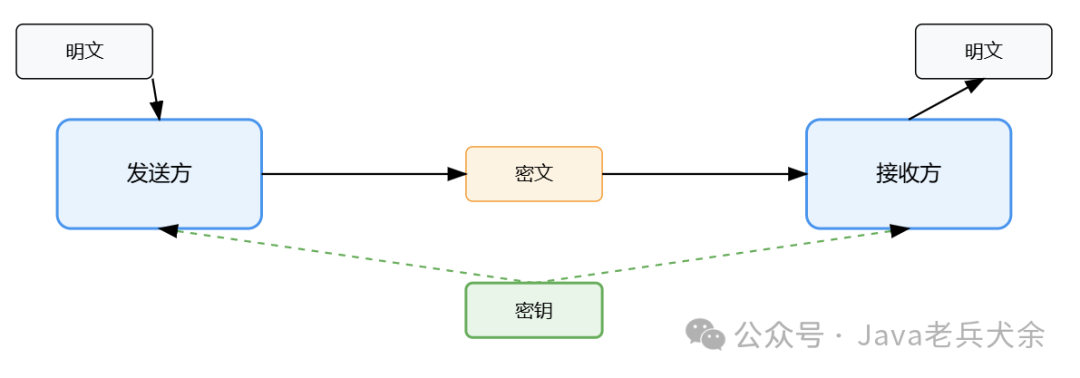 Cryptographers must balance security and performance when designing symmetric encryption algorithms. Increasing the number of rounds can enhance security but will reduce encryption and decryption speed; expanding key length can resist brute-force attacks but will increase computational overhead. Additionally, algorithms must withstand various known cryptanalysis attacks, such as differential and linear cryptanalysis. With the development of quantum computing, cryptographers are beginning to study symmetric encryption algorithms that are resistant to quantum computing. Although symmetric encryption is relatively less threatened by quantum computing compared to asymmetric encryption, it still needs to address future challenges by increasing key lengths and other means. Currently, symmetric encryption algorithms continue to evolve, with new algorithm designs and security analysis methods emerging.2. Foreign Symmetric Encryption Algorithms2.1 DES Algorithm
Cryptographers must balance security and performance when designing symmetric encryption algorithms. Increasing the number of rounds can enhance security but will reduce encryption and decryption speed; expanding key length can resist brute-force attacks but will increase computational overhead. Additionally, algorithms must withstand various known cryptanalysis attacks, such as differential and linear cryptanalysis. With the development of quantum computing, cryptographers are beginning to study symmetric encryption algorithms that are resistant to quantum computing. Although symmetric encryption is relatively less threatened by quantum computing compared to asymmetric encryption, it still needs to address future challenges by increasing key lengths and other means. Currently, symmetric encryption algorithms continue to evolve, with new algorithm designs and security analysis methods emerging.2. Foreign Symmetric Encryption Algorithms2.1 DES Algorithm
The DES algorithm (Data Encryption Standard) is the first publicly available symmetric cipher algorithm standard released by the National Bureau of Standards of the United States in 1977. It was developed by IBM and finalized with the participation of the NSA. As the first publicly available commercial cipher standard, DES made significant contributions to the development of modern cryptography.
DES uses a Feistel network structure, employing a 64-bit block size and a 56-bit effective key length. The core of the algorithm is 16 rounds of iterative operations, each round consisting of expansion permutation, round key XOR, S-box substitution, and P-box permutation. Among these, the S-box is the algorithm’s nonlinear component, implementing complex nonlinear transformations through eight different 4×16 substitution tables; the P-box provides diffusion by rearranging positions, ensuring that small changes in input affect multiple output positions.
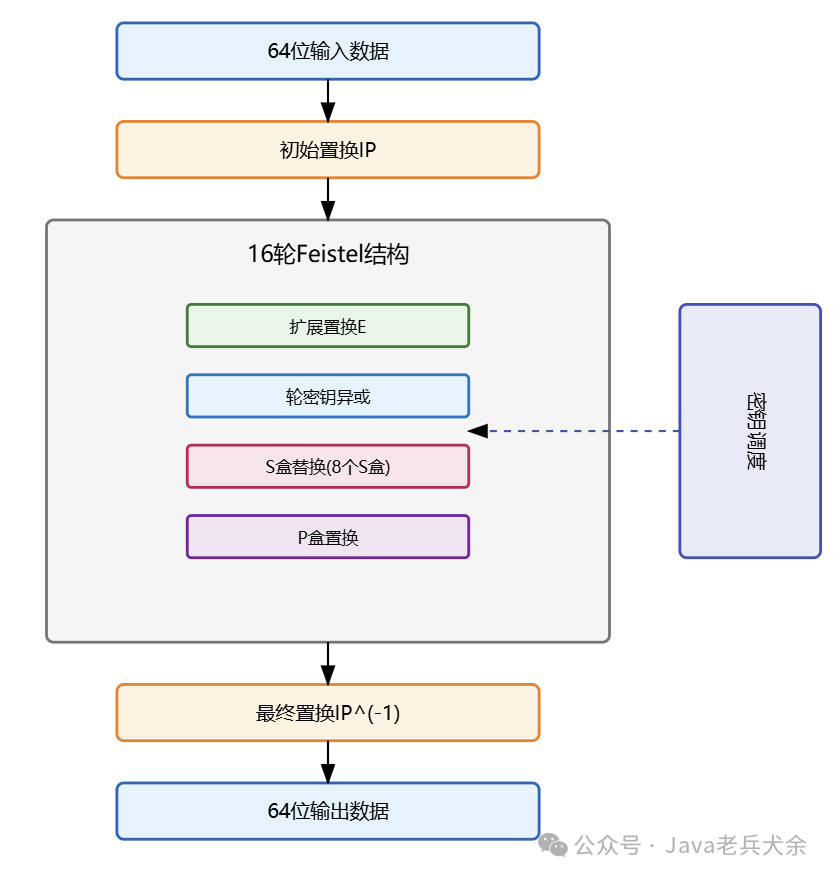
During the encryption process, DES first performs an initial permutation (IP) on the 64-bit input data, dividing it into a left half (L) and a right half (R). In each round of the Feistel structure, the right half is expanded to 48 bits through the expansion permutation (E) and XORed with the round key. The 48-bit data is then compressed back to 32 bits through the S-box and permuted through the P-box. Finally, the result is XORed with the left half, completing one round of transformation. After 16 rounds of transformation, the final permutation (IP^(-1)) yields the ciphertext output.
Key scheduling is an important component of DES. The 64-bit master key (including 8 parity bits) is first permuted using the permutation choice 1 (PC-1) to remove the parity bits, resulting in a 56-bit effective key. Then, through left shifts and permutation choice 2 (PC-2), 16 round keys of 48 bits each are generated. Each round uses a different round key in the operations, enhancing the algorithm’s security.
Although DES is elegantly designed, its 56-bit key length is insufficient against modern computational capabilities. In 1998, the Electronic Frontier Foundation cracked DES in 56 hours using specialized equipment. This prompted the birth of the next generation encryption standard, AES. Nevertheless, the design philosophy of DES, particularly the Feistel network structure and S-box design criteria, has had a profound impact on the development of subsequent cipher algorithms.
2.2 3DES Algorithm
The 3DES (Triple DES) algorithm is an improved version of DES, which became a NIST standard in 1999. It employs a triple DES encryption structure to enhance security while maintaining compatibility with the original DES algorithm. 3DES uses three 56-bit DES keys, resulting in a total key length of 168 bits, significantly improving resistance to brute-force attacks.
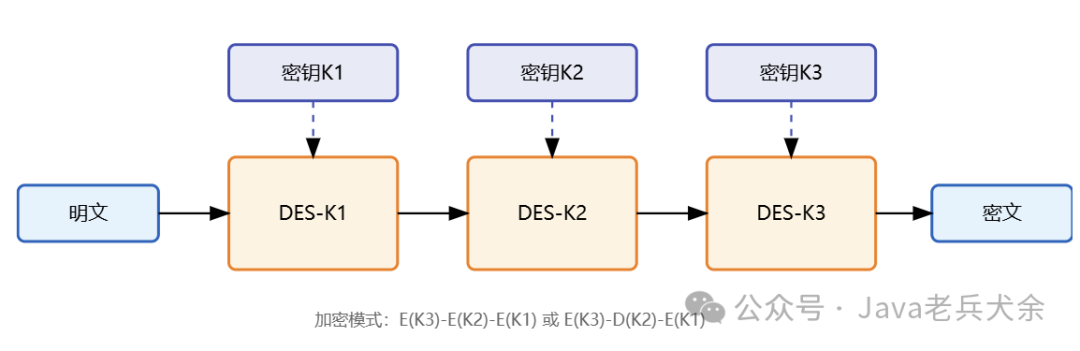
Technically, 3DES has two operating modes: EEE mode (Encrypt-Encrypt-Encrypt) and EDE mode (Encrypt-Decrypt-Encrypt). The EDE mode is more commonly used because it can backward-compatible with single DES when all three keys are the same. Each encryption process involves performing three DES operations on 64-bit data blocks, with the intermediate result serving as the input for the next encryption.
Key management is an important feature of 3DES. Although the theoretical total key length is 168 bits, due to the 8 bits used for parity in each DES key, its actual security strength is about 112 bits. The three keys can be completely different (K1≠K2≠K3) or have two identical keys (K1≠K2=K3), providing flexibility to meet different security needs.
3DES is widely used in the financial sector, particularly in credit card transactions and ATM networks. Its main advantage lies in its ability to reuse existing DES hardware, significantly enhancing security with just a software upgrade. However, due to the need for three DES operations, its encryption and decryption speed is about three times slower than single DES, and it has gradually been replaced by AES in high-performance scenarios.
2.3 AES Algorithm
The AES (Advanced Encryption Standard) algorithm is based on the Rijndael algorithm, designed by Belgian cryptographers Joan Daemen and Vincent Rijmen, and was adopted as the next-generation encryption standard by the National Institute of Standards and Technology (NIST) in 2001. It uses an SPN (Substitution-Permutation Network) structure and supports three key lengths of 128 bits, 192 bits, and 256 bits, corresponding to 10, 12, and 14 rounds of iterative operations, respectively.
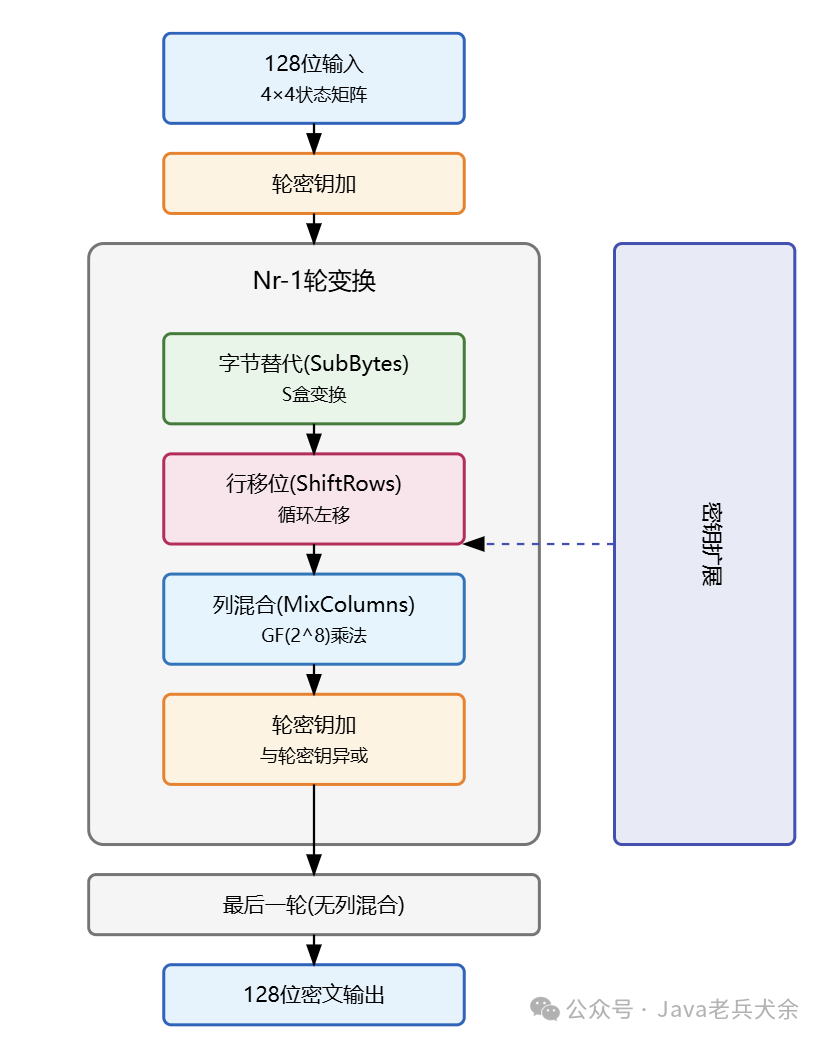
The basic processing unit of AES is the state matrix, which arranges the 128-bit data block into a 4×4 byte matrix. Each round transformation consists of four basic operations: SubBytes, ShiftRows, MixColumns, and AddRoundKey. The SubBytes operation uses a fixed S-box for nonlinear transformation; ShiftRows performs position permutation through cyclic left shifts; MixColumns conducts matrix multiplication in the finite field GF(2^8) to provide diffusion.
The key expansion algorithm is an important component of AES, which expands the master key into round keys. The expansion process uses S-box substitution, word rotation, and round constant XOR operations to ensure that each round uses a different key. The round key generation process has strong nonlinear characteristics, making it difficult to deduce other round keys even if some round keys are obtained.
AES is designed with efficiency for both software and hardware implementations in mind. All operations are byte-based, making it easy to implement on 8-bit processors; at the same time, operations like SubBytes and MixColumns can also be optimized through lookup tables. Modern processors generally provide an AES-NI instruction set, which can directly accelerate AES operations at the hardware level, significantly improving encryption performance.
AES has excellent security, effectively resisting classical attack methods such as linear and differential cryptanalysis. Its S-box design exhibits good nonlinear properties, and the MixColumns operation provides strong diffusion characteristics, ensuring that AES maintains high security strength even after years of cryptanalysis.
In terms of applications, AES has become the de facto standard in the field of symmetric encryption, widely used in security systems such as TLS/SSL protocols, disk encryption, and VPNs. It supports various operating modes, such as ECB, CBC, and CTR, allowing for the selection of appropriate modes based on different scenarios. In emerging fields like the Internet of Things and cloud computing, AES also plays a significant role.
2.4 IDEA Algorithm
The IDEA (International Data Encryption Algorithm) was proposed in 1991 by Xuejia Lai and James Massey from ETH Zurich, and is a block cipher algorithm based on a 128-bit key. It was initially used in PGP encryption software, designed to enhance encryption strength by combining operations from different algebraic groups.
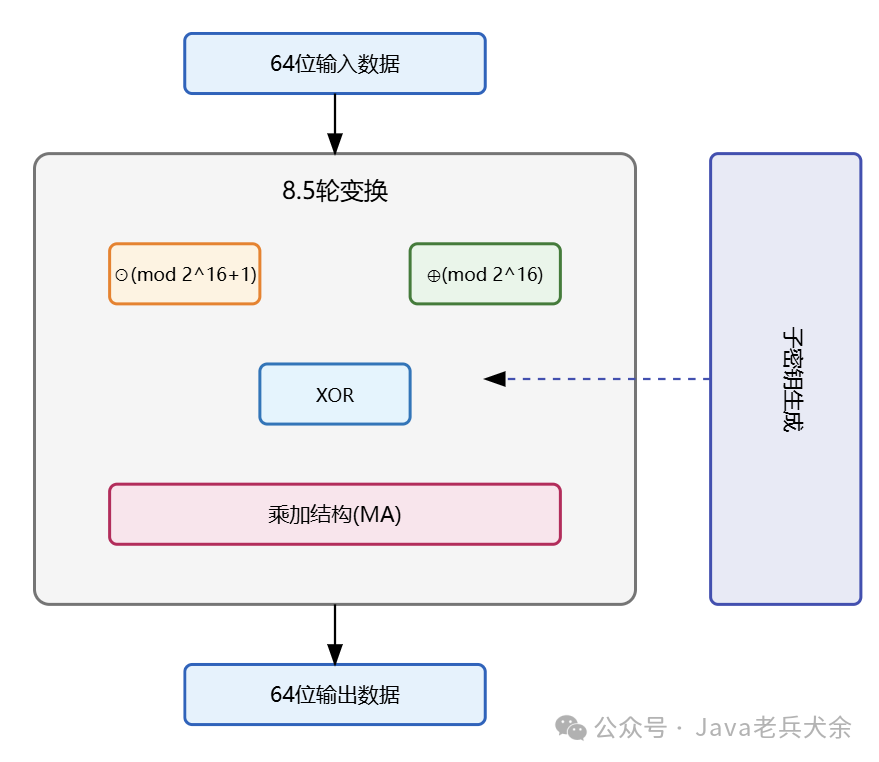
IDEA uses a 64-bit block size and implements encryption through 8.5 rounds of iteration (8 complete rounds plus an additional output transformation). Its core features include the use of three different algebraic operations: mod 2^16 addition (⊕), mod 2^16+1 multiplication (⊙), and XOR. This mixed operation design gives the algorithm strong algebraic properties, effectively resisting known cryptanalysis methods at the time.
In each round transformation, the 64-bit data block is divided into four 16-bit sub-blocks, which are operated on with six 16-bit sub-keys. The algorithm consists of two main steps: data transformation and MA (Multiplication-Addition) structure. The data transformation uses modular addition, modular multiplication, and XOR operations; the MA structure provides additional confusion and diffusion through two modular multiplications and two modular additions.
Key expansion is an important component of IDEA. The 128-bit master key is cyclically left-shifted to generate 52 16-bit sub-keys, ensuring that each round uses different key material. The sub-key generation process is simple yet effective, producing the required sub-keys through position rearrangement and segmented extraction.
In practical applications, IDEA is popular due to its excellent security and reliability. Although its operations involve modular multiplication, making it relatively slow in software implementations, it can achieve efficient encryption processing on dedicated hardware. Due to the algorithm being patent-protected, its application is somewhat limited, which is one reason it has not become a global standard like AES.
2.5 RC Series Algorithms The RC series algorithms were designed by Ron Rivest for RSA, showcasing significant developments in symmetric encryption from RC4 to RC6. This series is known for its simple and efficient design, having a profound impact on commercial cryptography.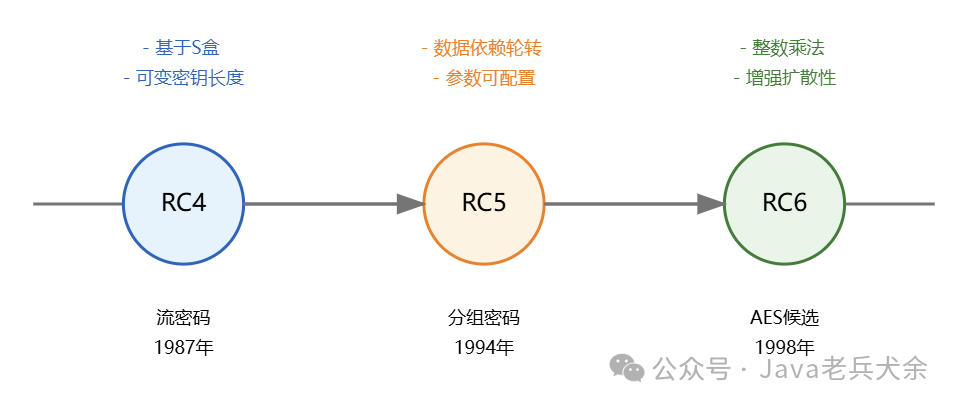 RC4 is a stream cipher algorithm designed in 1987, widely used in SSL/TLS and WEP protocols. It employs variable-length keys (ranging from 8 to 2048 bits, but commonly used lengths are 40 bits, 128 bits, etc.), generating a key stream through a 256-byte S-box and two pointers for permutation operations. The design of RC4 is extremely simple, making it easy to implement with fast encryption and decryption speeds, but due to several cryptographic flaws, it is no longer recommended for use. RC5 is a block cipher algorithm released in 1994. It introduced the innovative feature of data-dependent rotations, where the number of bits rotated is determined by the data itself. RC5 supports variable block sizes, key lengths, and rounds, providing flexibility to meet different security needs. The algorithm structure is simple, primarily using addition, XOR, and cyclic left shifts, making it easy to implement in both software and hardware. RC6 is an improved version of RC5 and was one of the five candidates in the AES competition. It adds 32-bit integer multiplication to enhance the diffusion and confusion properties of the algorithm through the introduction of a mixing transformation with a square function. RC6 retains the configurable parameters of RC5 while providing better diffusion performance. Although it ultimately did not become the AES standard, its design philosophy has significantly inspired the development of subsequent algorithms. The evolution of the RC series algorithms reflects several important trends in symmetric encryption: the transition from stream ciphers to block ciphers, the configurability of algorithm parameters, and the balance between computational complexity and security. Their designs pursue simplicity and efficiency, minimizing complex algebraic operations, a pragmatic design approach that has influenced many subsequent commercial cipher algorithms. In terms of performance, the RC series algorithms exhibit high software implementation efficiency. RC4 is the simplest to implement with extremely fast encryption and decryption speeds; while RC5 and RC6 introduce more complex operations, they still achieve good performance on modern processors through reasonable structural design. Initially, these algorithms were patented technologies of RSA, limiting their application, but the patent for RC4 expired in 2015, significantly reducing application restrictions, although the patents for RC5 and RC6 may still be valid.
RC4 is a stream cipher algorithm designed in 1987, widely used in SSL/TLS and WEP protocols. It employs variable-length keys (ranging from 8 to 2048 bits, but commonly used lengths are 40 bits, 128 bits, etc.), generating a key stream through a 256-byte S-box and two pointers for permutation operations. The design of RC4 is extremely simple, making it easy to implement with fast encryption and decryption speeds, but due to several cryptographic flaws, it is no longer recommended for use. RC5 is a block cipher algorithm released in 1994. It introduced the innovative feature of data-dependent rotations, where the number of bits rotated is determined by the data itself. RC5 supports variable block sizes, key lengths, and rounds, providing flexibility to meet different security needs. The algorithm structure is simple, primarily using addition, XOR, and cyclic left shifts, making it easy to implement in both software and hardware. RC6 is an improved version of RC5 and was one of the five candidates in the AES competition. It adds 32-bit integer multiplication to enhance the diffusion and confusion properties of the algorithm through the introduction of a mixing transformation with a square function. RC6 retains the configurable parameters of RC5 while providing better diffusion performance. Although it ultimately did not become the AES standard, its design philosophy has significantly inspired the development of subsequent algorithms. The evolution of the RC series algorithms reflects several important trends in symmetric encryption: the transition from stream ciphers to block ciphers, the configurability of algorithm parameters, and the balance between computational complexity and security. Their designs pursue simplicity and efficiency, minimizing complex algebraic operations, a pragmatic design approach that has influenced many subsequent commercial cipher algorithms. In terms of performance, the RC series algorithms exhibit high software implementation efficiency. RC4 is the simplest to implement with extremely fast encryption and decryption speeds; while RC5 and RC6 introduce more complex operations, they still achieve good performance on modern processors through reasonable structural design. Initially, these algorithms were patented technologies of RSA, limiting their application, but the patent for RC4 expired in 2015, significantly reducing application restrictions, although the patents for RC5 and RC6 may still be valid.
3. Domestic Symmetric Encryption Algorithms
3.1 SM1 Algorithm The SM1 encryption algorithm is a symmetric block cipher algorithm released by China’s National Cryptography Administration, designed to provide an efficient and secure encryption solution for the information security field. The algorithm has a block length of 128 bits and supports key lengths of 128 bits, 192 bits, and 256 bits, processing data through block encryption by encrypting plaintext in 128-bit blocks to ensure data confidentiality. This design allows the SM1 algorithm to perform excellently in handling large-scale data while also meeting the requirements of high real-time applications. During the encryption process, the SM1 algorithm employs iterative operations to achieve data confusion and diffusion. Each round of iteration includes operations such as permutation, XOR, and S-box substitution, which collectively ensure that the statistical properties of the data are sufficiently disrupted, thereby enhancing the algorithm’s resistance to attacks. However, the details of this algorithm are classified as commercial secret level and are not publicly disclosed, so we cannot confirm more detailed implementation specifics. In practical applications, SM1 is primarily used for data encryption in dedicated communication fields, including financial payments and government information systems. Cryptographic chips based on SM1 have been widely used in products such as bank cards and smart password keys. Although SM4 has become the mainstream national cryptographic algorithm, SM1 still plays an important role in certain specific fields.3.2 SM4 Algorithm The SM4 encryption algorithm is a block symmetric encryption algorithm released by China’s National Cryptography Administration in 2006. It uses a 128-bit key and a 128-bit block size, achieving encryption through 32 rounds of iteration, borrowing advantages from international mainstream algorithms like AES while incorporating unique innovations. In terms of technical implementation, SM4 is based on an iterative structure of block ciphers, similar to the SPN (Substitution-Permutation Network) structure of AES, with each round of operation containing two key steps: a nonlinear transformation τ and a linear transformation L. The nonlinear transformation uses an S-box for byte substitution, disrupting the statistical properties of the data; the linear transformation achieves data diffusion through XOR and cyclic shift operations, enhancing the algorithm’s resistance to attacks. This design ensures both security and ease of implementation in software and hardware.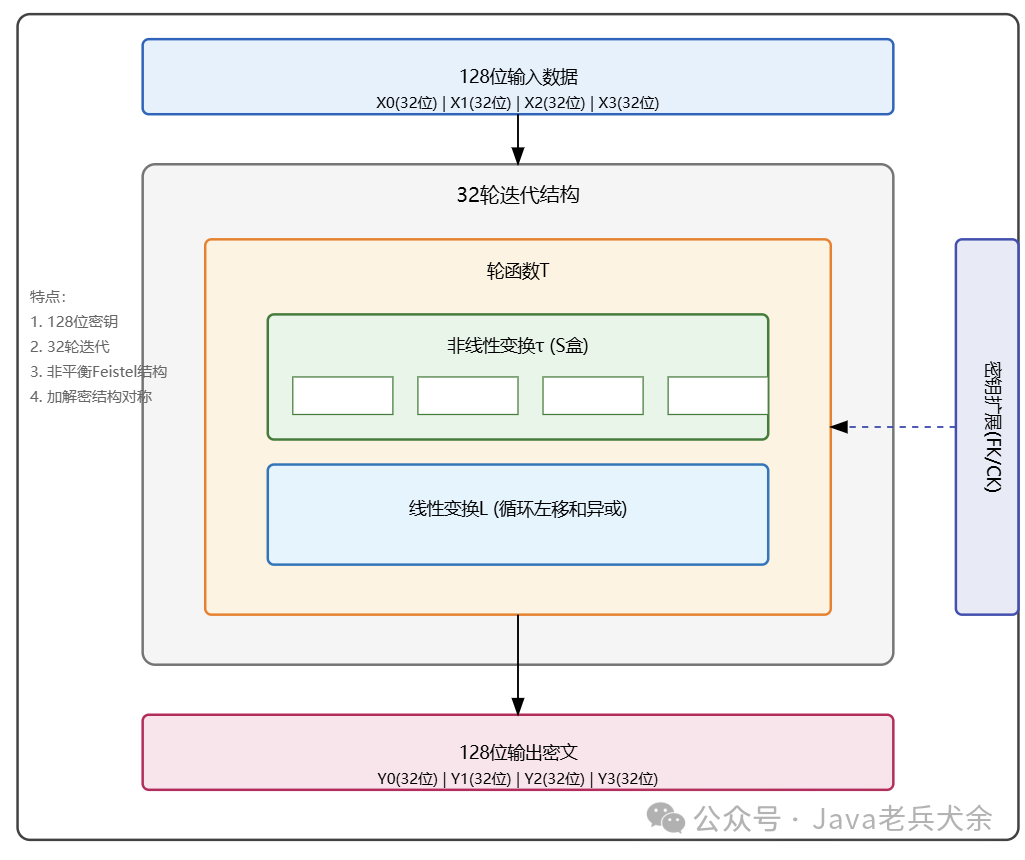 Key expansion is an important feature of SM4, which expands the 128-bit master key into 32 32-bit round keys, with each round using a different key in the operations. This design enhances the algorithm’s security, making it difficult to deduce the master key even if some round keys are obtained. The round key generation process also introduces fixed parameters FK and constants CK, further increasing the complexity of key scheduling. The encryption process of SM4 divides the 128-bit input data into four 32-bit words, encrypting them progressively through 32 rounds of transformation. Each round transformation updates the value of one word, affecting the calculations of the next round. The decryption process is identical to the encryption process, requiring only the round keys to be used in reverse order. This symmetric design greatly simplifies the algorithm’s implementation, allowing encryption and decryption to share the same hardware circuitry. In terms of performance, optimized software implementations of SM4 can achieve high speeds on general-purpose processors, especially on modern processors that support the AES-NI instruction set. In hardware implementations, the key operations of SM4 are well-suited for hardware acceleration, enabling efficient circuit designs on FPGA and ASIC. Years of practice have shown that SM4 achieves a good balance in speed, resource usage, and power consumption. To accommodate different application scenarios, SM4 offers various operating modes, including Electronic Codebook mode (ECB), Cipher Block Chaining mode (CBC), Output Feedback mode (OFB), Counter mode (CTR), and XEX Tweakable Block Cipher mode with ciphertext stealing (XTS). Additionally, there are legacy modes such as the Block Chaining mode (BC) and Output Feedback mode with nonlinear functions (OFBNLF) that are not recommended for new applications. Each of these modes has its characteristics, allowing for the selection of the appropriate mode based on specific needs. For example, CTR mode can be chosen for parallel processing, while CBC mode can be selected for high security requirements. Compared to the earlier SM1 algorithm, the most significant feature of SM4 is its complete openness and transparency, allowing it to undergo extensive security testing. Over the years, cryptography experts both domestically and internationally have conducted in-depth cryptanalysis of SM4, including differential analysis, linear analysis, and related-key attacks, without discovering significant security vulnerabilities. This openness has also facilitated the international recognition and application of SM4.3.3 SM7 Algorithm
Key expansion is an important feature of SM4, which expands the 128-bit master key into 32 32-bit round keys, with each round using a different key in the operations. This design enhances the algorithm’s security, making it difficult to deduce the master key even if some round keys are obtained. The round key generation process also introduces fixed parameters FK and constants CK, further increasing the complexity of key scheduling. The encryption process of SM4 divides the 128-bit input data into four 32-bit words, encrypting them progressively through 32 rounds of transformation. Each round transformation updates the value of one word, affecting the calculations of the next round. The decryption process is identical to the encryption process, requiring only the round keys to be used in reverse order. This symmetric design greatly simplifies the algorithm’s implementation, allowing encryption and decryption to share the same hardware circuitry. In terms of performance, optimized software implementations of SM4 can achieve high speeds on general-purpose processors, especially on modern processors that support the AES-NI instruction set. In hardware implementations, the key operations of SM4 are well-suited for hardware acceleration, enabling efficient circuit designs on FPGA and ASIC. Years of practice have shown that SM4 achieves a good balance in speed, resource usage, and power consumption. To accommodate different application scenarios, SM4 offers various operating modes, including Electronic Codebook mode (ECB), Cipher Block Chaining mode (CBC), Output Feedback mode (OFB), Counter mode (CTR), and XEX Tweakable Block Cipher mode with ciphertext stealing (XTS). Additionally, there are legacy modes such as the Block Chaining mode (BC) and Output Feedback mode with nonlinear functions (OFBNLF) that are not recommended for new applications. Each of these modes has its characteristics, allowing for the selection of the appropriate mode based on specific needs. For example, CTR mode can be chosen for parallel processing, while CBC mode can be selected for high security requirements. Compared to the earlier SM1 algorithm, the most significant feature of SM4 is its complete openness and transparency, allowing it to undergo extensive security testing. Over the years, cryptography experts both domestically and internationally have conducted in-depth cryptanalysis of SM4, including differential analysis, linear analysis, and related-key attacks, without discovering significant security vulnerabilities. This openness has also facilitated the international recognition and application of SM4.3.3 SM7 Algorithm
The SM7 algorithm is a high-strength block cipher algorithm independently developed in China, classified as a military-grade cryptographic algorithm. Compared to SM4, SM7 uses a block length and key length of 128 bits, providing higher security strength by increasing computational complexity, primarily applied in military and special fields for data encryption.
In terms of technical features, SM7 is a block cipher algorithm that employs an iterative block cipher design method, achieving data confusion through multiple rounds of complex nonlinear transformations and linear diffusion operations. Each round transformation includes multiple parallel S-box operations and complex linear transformations, ensuring both the algorithm’s security and good performance on dedicated hardware.
Due to the military-grade nature of SM7, its specific implementation details and technical parameters are not publicly disclosed. However, from known information, it is evident that SM7 has been designed with consideration for resisting various advanced cryptanalysis attacks, employing unique key expansion mechanisms and round function structures to ensure the algorithm’s security in its application scenarios.
In terms of applications, the SM7 algorithm is primarily used in contactless IC card applications, including identity verification (access cards, work permits, etc.), ticketing (large event tickets, etc.), and payment and universal cards (campus cards, corporate cards, etc.). Thus, while SM7 is classified as a military-grade algorithm, its application scope is not limited to military fields. Additionally, SM7 typically adopts hardware implementation methods, requiring strict security certification for these hardware devices and usage in specific secure environments, with strict management regulations for the deployment and use of the algorithm to ensure the security of cryptographic services.
3.4 ZUC Algorithm
The ZUC algorithm (Zuc Chongzhi algorithm) is a stream cipher algorithm independently developed in China, adopted as one of the core algorithms for 4G mobile communication encryption standards by 3GPP in 2011, and subsequently applied in 5G communications. This is China’s first cryptographic algorithm to become an international standard, marking the country’s advancement to an internationally advanced level in cryptographic technology.
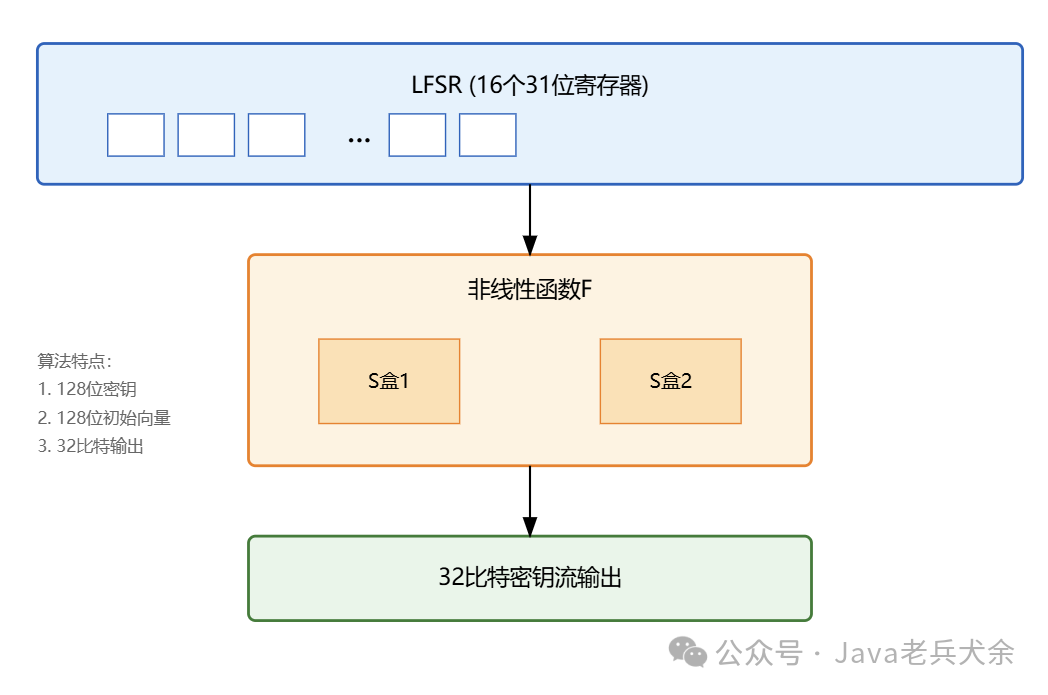
In terms of technical implementation, ZUC combines a linear feedback shift register (LFSR) with a nonlinear function F. The LFSR consists of 16 31-bit registers, generating pseudo-random sequences through a complex feedback mechanism. The nonlinear function F includes two S-boxes and linear transformations to disrupt the statistical properties of the LFSR output. This design ensures both high security and relatively high operational speed for the algorithm.
Key initialization is an important step in the ZUC algorithm. The algorithm accepts a 128-bit key and a 128-bit initialization vector as input, diffusing these inputs into the internal state of the LFSR through a complex initialization process. Once initialized, the algorithm can produce 32 bits of key stream output each time. The randomness and unpredictability of the key stream directly determine the algorithm’s security strength.
In mobile communications, the ZUC algorithm primarily serves two security objectives: first, to protect the confidentiality of user data through the EEA3 algorithm, and second, to ensure data integrity through the EIA3 algorithm. Both algorithms use ZUC as the core, employing its output key stream in different ways. EEA3 is used to encrypt user voice and data services, while EIA3 generates message authentication codes to prevent data tampering.
One significant advantage of ZUC is its excellent hardware implementation efficiency. The key operations of the algorithm are well-suited for hardware acceleration, enabling high-speed processing on FPGA and ASIC. Additionally, the software implementation is also quite efficient, meeting the performance requirements of most application scenarios on general-purpose processors. This flexibility allows ZUC to adapt to the hardware capabilities of different terminal devices.
4. Conclusion
Symmetric encryption algorithms have developed a complete technical system over decades, from the earliest DES to the currently widely used AES, with increasing key lengths and improving algorithm structures. China’s SM4 and ZUC algorithms have also reached internationally advanced levels, playing important roles in specific fields.
With the development of quantum computing technology, symmetric encryption algorithms face new challenges. Although symmetric encryption is less affected by quantum computing compared to asymmetric encryption, it still needs to address potential threats by increasing key lengths and improving algorithm structures. Additionally, emerging applications such as the Internet of Things and 5G impose higher demands on the performance and resource consumption of encryption algorithms.
In terms of algorithm selection, it is necessary to weigh specific application scenarios and security needs. For scenarios requiring high security levels, AES-256 or SM4 can be chosen; for high-performance requirements, hardware acceleration solutions can be considered; for specialized fields, certified dedicated algorithms should be selected. In the future, symmetric encryption algorithms will continue to evolve towards greater security, efficiency, and flexibility, providing a solid guarantee for information security.
|
Dog
Yu
Follow Dog Yu for mutual progress
Technology is no longer lonely