Click the blue text above Tansy Laboratory
Get more information on automotive cybersecurity

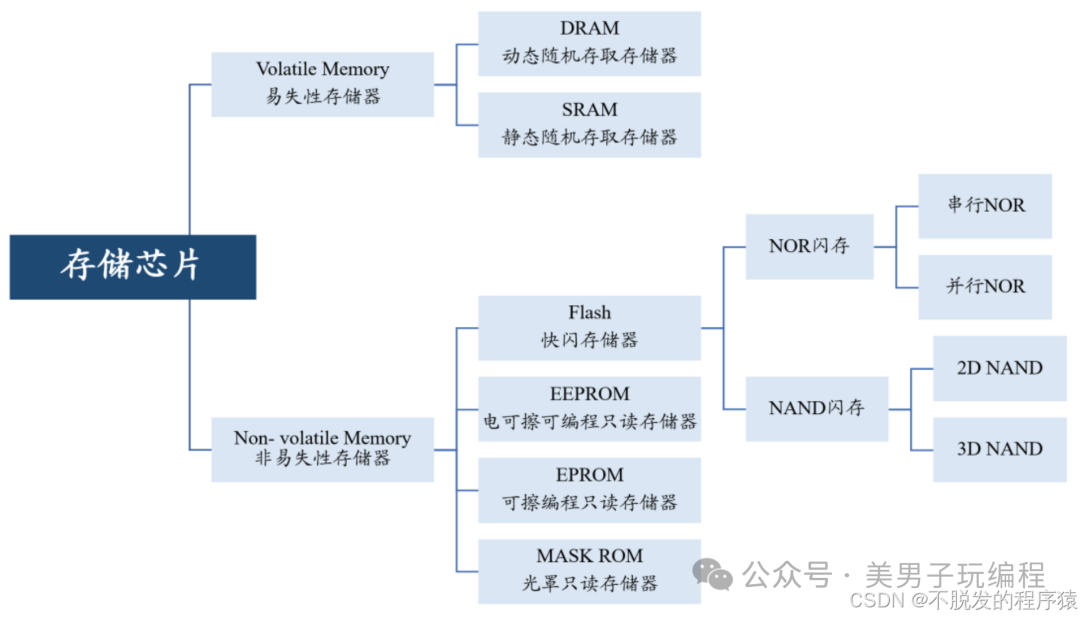
Flash memory is widely used in embedded systems, especially in scenarios requiring large-capacity non-volatile storage, such as firmware storage, logging, and data backup. However, due to the physical characteristics of Flash, it faces the risk of failure after a limited number of erase-write cycles.
Flash storage is mainly divided into NAND Flash and NOR Flash, which differ in structure and application scenarios:
-
NAND Flash: High density, low cost, suitable for data storage, such as eMMC, UFS, etc.
-
NOR Flash: Fast read speed, suitable for code storage and execution, such as firmware and Bootloader.
The lifespan of Flash is mainly determined by the erase-write cycles (P/E Cycle). After a limited number of erase-write operations, each storage block may experience unrecoverable write errors, manifested as bit flips, data loss, etc.
The goal of lifespan prediction is to assess the remaining usable cycles of Flash based on its current usage state. Common methods include:
-
Estimation based on erase counts: Count the number of erase operations for each block and compare it with the maximum erase count.
-
Prediction based on Bit Error Rate (BER): Regularly read and verify data to estimate lifespan based on the trend of BER changes.
-
Prediction based on failure models: Construct specific failure models and predict remaining lifespan based on actual working conditions of the device.
The goal of monitoring methods is to obtain the health status of Flash in real-time, allowing for measures to be taken as the lifespan approaches its end.
-
Bad Block Management (BBM): Detect and mark bad blocks, redirecting data.
-
Wear Leveling: Balance the erase counts across blocks to extend overall lifespan.
-
ECC Verification and Correction: Use Error Correction Code (ECC) to repair errors caused by erase operations.
Below is an example of Flash lifespan prediction code based on erase counts.
#define MAX_PE_CYCLES 10000
#define BLOCK_NUM 256
unsigned int wear_count[BLOCK_NUM] = {0};
void write_block(int block_id) {
if (wear_count[block_id] >= MAX_PE_CYCLES) {
printf("Block %d has reached the maximum erase count and needs to be replaced or marked as bad block.\n", block_id);
} else {
wear_count[block_id]++;
printf("Block %d has been written %d times.\n", block_id, wear_count[block_id]);
}
}
void check_flash_health() {
for (int i = 0; i < BLOCK_NUM; i++) {
if (wear_count[i] >= MAX_PE_CYCLES * 0.8) {
printf("Warning: Block %d's erase count is approaching lifespan limit.\n", i);
}
}
}
int main() {
for (int i = 0; i < 10050; i++) {
write_block(0);
}
check_flash_health();
return 0;
}This code simulates the erase-write operations of Flash blocks and performs simple monitoring and warning of lifespan status.
Prediction and monitoring of Flash lifespan are important means to enhance the stability of embedded systems.
Through reasonable prediction and monitoring methods, the lifespan of Flash can be effectively extended, reducing the risk of data loss and system crashes.
end
Recommended Premium Events



AutoSec China Tour Series Salon


Professional Community

Some experts in the group come from:
New force car companies:
Tesla, Hozon New Energy – Nezha, Li Auto, Zeekr, Xiaomi, Binnli Auto, Jiyue, Leap Motor, Avita, Zhiji Auto, Xiaopeng, Lantu Auto, NIO, Geely Auto, Seres……
Foreign traditional mainstream car companies:
Volkswagen China, Volkswagen Cool Wing, Audi, BMW, Ford, Daimler-Benz, General Motors, Porsche, Volvo, Hyundai, Nissan, Jaguar Land Rover, Scania……
Domestic traditional mainstream car companies:
Geely Auto, SAIC Passenger Cars, Great Wall Motors, SAIC Volkswagen, Changan Automobile, Beijing Automotive, Dongfeng Motor, GAC, BYD, FAW Group, FAW Jiefang, Dongfeng Commercial, SAIC Commercial……
Global leading Tier 1 suppliers:
Bosch, Continental Group, United Automotive Electronics, Aptiv, ZF, KOSTAL, Schaeffler, Honeywell, DJI, Hitachi, Harman, Huawei, Baidu, Lenovo, MediaTek, Preh, Desay SV, Honeycomb Steering, Junlian Zhixing, Wuhan Guangting, Xingji Meizu, CRRC Group, Wintech, Weichai Group, Horizon, Unisoc, ByteDance,……
Tier 2 suppliers (over 500):
Upstream, ETAS, Synopsys, NXP, TUV, Shanghai Software Center, Deloitte, Zhongke Shucai, Qihoo 360, Xinchang Security, Weichan Xinan, Yunchi Future, Xinda Jiexin, Xinchangcheng, Zelu Security, Niuchuang Xinan, Fudan Microelectronics, Tianrongxin, Qihoo 360, China Automotive Center, China Automotive Research, Shanghai Automotive Inspection, Ruann Technology, Zhejiang University……
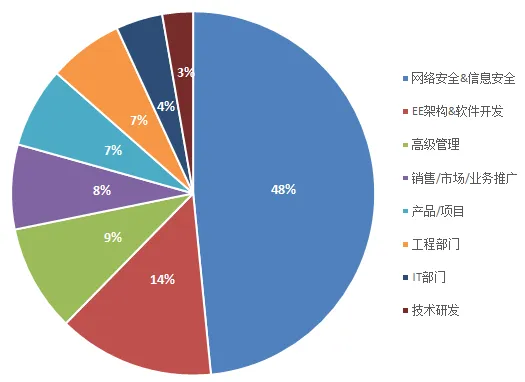
Personnel Proportion
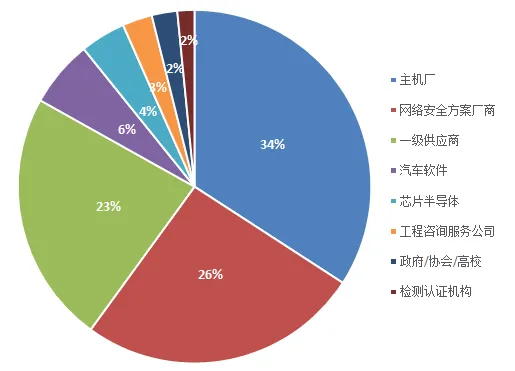
Company Type Proportion
More Articles
Don’t miss out, this could be the largest exclusive community in the automotive cybersecurity industry!
About the lawyer’s statement regarding the suspected imitation of the AutoSec conference brand
One article to help you understand the in-vehicle network communication security architecture of intelligent vehicles
Cybersecurity: TARA methods, tools, and cases
Key analysis of automotive data security compliance
Analysis of automotive chip information security and secure boot
Exploration of automotive in-vehicle communication security solutions in domain centralized architecture
System security architecture of vehicle network security architecture
Privacy protection issues in the Internet of Vehicles
Research on cybersecurity technology for intelligent connected vehicles
AUTOSAR information security framework and key technology analysis
What are the information security mechanisms of AUTOSAR?
Underlying mechanisms of information security
Automotive network security
Use of AUTOSAR hardware security module HSM
First release! Lei Jun from Xiaomi made suggestions on automotive data security issues at the Two Sessions: Suggestions on building a complete automotive data security management system