Follow and star our public account to access exciting content
Source: Online materials
With the advent of artificial intelligence and the Internet of Things, data applications have become more frequent. How should data security be protected? What software encryption algorithms are available, and in what areas are these algorithms applied? As you read on, you will discover the “small passwords” surrounding us.
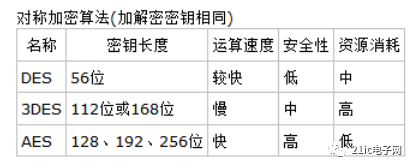
Symmetric Encryption Algorithms
Symmetric encryption algorithms are among the earliest encryption algorithms, with mature technology. In symmetric encryption algorithms, the data sender processes the plaintext (original data) along with the encryption key through a special encryption algorithm, transforming it into complex encrypted ciphertext for transmission. In symmetric encryption algorithms, only one key is used, and both the sender and receiver use this key to encrypt and decrypt the data, which requires the decryption party to know the encryption key in advance. The characteristics of symmetric encryption algorithms include public algorithms, low computational load, fast encryption speed, and high encryption efficiency. However, a drawback is that both parties use the same key, which does not guarantee security. Symmetric encryption algorithms are relatively difficult to use in distributed network systems, mainly due to key management challenges and high usage costs.
DES Encryption Algorithm
The DES encryption algorithm is a block cipher that encrypts data in 64-bit blocks, with a key length of 56 bits, using the same algorithm for encryption and decryption. The DES encryption algorithm keeps the key secret while the algorithm, including encryption and decryption, is public. Thus, only those who possess the same key as the sender can interpret the ciphertext encrypted by the DES algorithm. Therefore, breaking the DES encryption algorithm essentially involves searching for the key’s code. For a 56-bit key, if exhaustive search is used, the number of operations required is 2^56.
As computer system capabilities continue to develop, the security of DES is much weaker than when it first appeared; however, from a practical standpoint, it can still be considered sufficient. Nevertheless, DES is now only used for authentication in legacy systems, with newer encryption standards being preferred.
3DES Encryption Algorithm
3DES, or Triple Data Encryption Standard, is a block cipher that applies the DES encryption algorithm three times to each data block. Due to the increased computational power of computers, the original DES key length has become susceptible to brute-force attacks; 3DES was designed to provide a relatively simple method to avoid similar attacks by increasing the key length of DES rather than designing an entirely new block cipher algorithm.
3DES serves as a transitional encryption algorithm from DES to AES, with the specific implementation as follows: Let Ek() and Dk() represent the encryption and decryption processes of the DES algorithm, K represent the key used by the DES algorithm, M represent the plaintext, and C represent the ciphertext, then:
The 3DES encryption process is: C=Ek3(Dk2(Ek1(M)))
The 3DES decryption process is: M=Dk1(Ek2(Dk3(C)))
AES Encryption Algorithm
The AES encryption algorithm is the Advanced Encryption Standard in cryptography, employing a symmetric block cipher system with a minimum key length of 128, 192, or 256 bits, and a block length of 128 bits. The algorithm should be easy to implement in various hardware and software. This encryption algorithm is the block encryption standard adopted by the U.S. federal government, designed to replace the original DES, and has been widely analyzed and used globally.
The AES encryption algorithm is designed to support data block sizes of 128/192/256 bits (/32=nb) and key lengths of 128/192/256 bits (/32=nk), corresponding to 34×10^38, 62×10^57, and 1.1×10^77 keys in decimal.
Asymmetric Encryption Algorithms
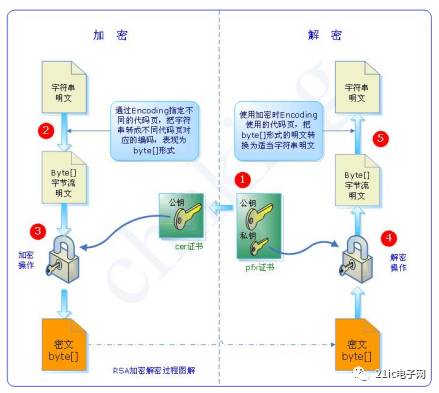
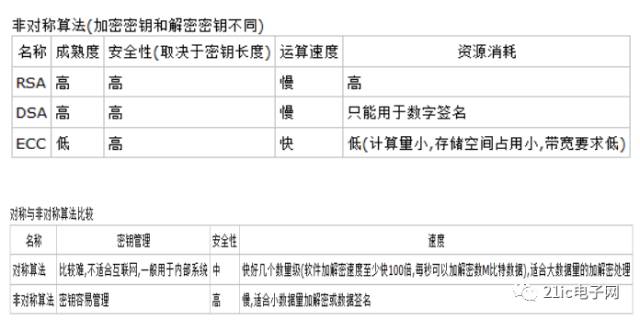
Asymmetric encryption algorithms use two completely different but perfectly matched keys—a public key and a private key. When using an asymmetric encryption algorithm to encrypt a file, only the matching pair of public and private keys can complete the encryption and decryption process of the plaintext. In asymmetric encryption algorithms, the receiving party must send their randomly generated public key to the sender before communication while retaining the private key. Due to the two-key nature of asymmetric algorithms, they are particularly suitable for data encryption in distributed systems. Widely used asymmetric encryption algorithms include RSA and DSA proposed by the U.S. National Institute of Standards and Technology. Encryption technologies based on asymmetric encryption algorithms are widely applied.
RSA Encryption Algorithm
The RSA encryption algorithm is currently the most influential public key encryption algorithm and is widely regarded as one of the best public key schemes available. RSA is the first algorithm that can be used for both encryption and digital signatures, capable of resisting all known cryptographic attacks to date, and has been recommended by ISO as a public key data encryption standard. The RSA encryption algorithm is based on a very simple number theory fact: multiplying two large prime numbers is easy, but factoring their product is extremely difficult, allowing the product to be made public as the encryption key.
DSA Encryption Algorithm
DSA is based on the discrete logarithm problem in finite fields, with security comparable to RSA. An important feature of DSA is that two primes are public, so when using someone else’s p and q, even without knowing the private key, you can verify whether they were randomly generated or manipulated. RSA cannot do this. DSA is only an algorithm; unlike RSA, it cannot be used for encryption and decryption or key exchange, only for signing, and it is much faster than RSA.
ECC Encryption Algorithm
Elliptic Curve Cryptography (ECC) is a public key encryption system initially proposed by Koblitz and Miller in 1985, based on the difficulty of computing discrete logarithms on rational points of elliptic curves. Public key cryptosystems are generally divided into three categories based on the problems they rely on: large integer factorization, discrete logarithm problems, and elliptic curves. Sometimes, elliptic curves are classified under discrete logarithm problems. The elliptic curve cryptosystem is currently known to provide the highest encryption strength per bit among public key systems. The best algorithm for solving the discrete logarithm problem on elliptic curves is the Pollard rho method, which has a time complexity that is completely exponential.
Irreversible Encryption Algorithms
Irreversible encryption algorithms are characterized by not requiring a key during the encryption process. After inputting plaintext, the system directly processes it into ciphertext through the encryption algorithm, and this encrypted data cannot be decrypted. Only by re-inputting the plaintext and processing it again through the same irreversible encryption algorithm can the same encrypted ciphertext be obtained and recognized by the system for true decryption. In computer networks, widely used irreversible encryption algorithms include the MD5 algorithm invented by RSA and the irreversible encryption standard SHS recommended by the U.S. National Institute of Standards and Technology.
MD5 Encryption Algorithm
MD5 is a widely used hash function in the field of computer security, providing message integrity protection. A brief description of the MD5 encryption algorithm is that it processes input information in 512-bit blocks, with each block divided into 16 sub-blocks of 32 bits. After a series of processing, the algorithm outputs four 32-bit blocks, which are concatenated to generate a 128-bit hash value.
MD5 is widely used for password authentication and key identification in various software. MD5 uses a hash function, and its typical application is to generate a message digest to prevent tampering. A typical application of MD5 is to produce a fingerprint of a message to prevent “tampering.” If a third-party certification authority uses MD5, it can also prevent the file author’s “denial,” which is known as digital signature application. MD5 is also widely used in operating system login authentication, such as UNIX, various BSD system login passwords, digital signatures, and many other aspects.
SHA1 Encryption Algorithm
SHA1 is a popular message digest algorithm similar to MD5. The SHA encryption algorithm mimics the MD4 encryption algorithm. SHA1 is designed to be used with the Digital Signature Algorithm (DSA).
SHA1 is mainly suitable for the digital signature algorithm defined in the digital signature standard. For messages shorter than 2^64 bits, SHA1 produces a 160-bit message digest. When a message is received, this message digest can be used to verify data integrity. During transmission, data may change, resulting in a different message digest. SHA1 cannot restore information from the message digest, and two different messages will not produce the same message digest. Thus, SHA1 can verify data integrity, making it a technology to ensure file integrity.
The SHA1 encryption algorithm can accept data inputs of up to 2^64 bits and produce a 160-bit digest. The input is divided into 512-bit blocks and processed individually. A 160-bit buffer is used to store the intermediate and final results of the hash function. The buffer can be represented by five 32-bit registers (A, B, C, D, and E). SHA1 is a more secure algorithm than MD5; theoretically, any digital verification algorithm that uses a “message digest” method has “collisions”—that is, two different items produce the same message digest, which is a common cheating method. However, finding a specified data “collision” in a highly secure algorithm is very difficult, and calculating a “collision” using formulas is even more challenging. So far, only MD5 has been cracked among commonly used secure algorithms.
Of course, besides the above encryption algorithms, there are other methods. I found a chart for supplementary information.
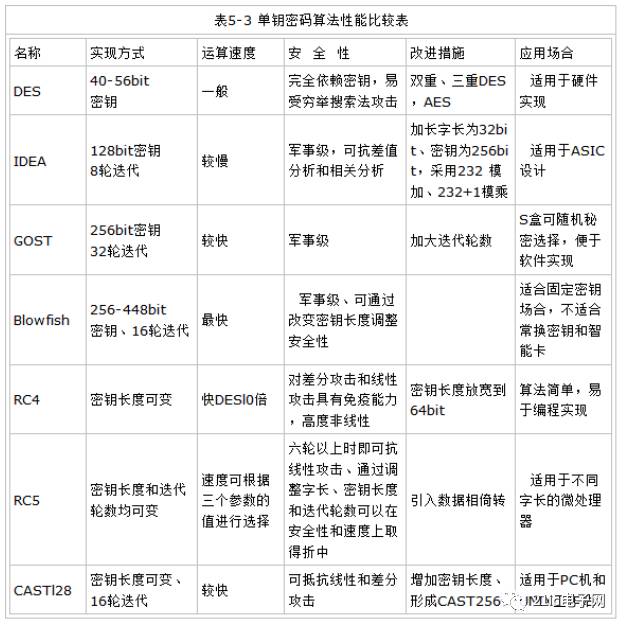
Copyright Statement: This article is sourced from the internet, freely conveying knowledge, and the copyright belongs to the original author. If there are any copyright issues, please contact me for deletion.
‧‧‧‧‧‧‧‧‧‧‧‧‧‧‧‧ END ‧‧‧‧‧‧‧‧‧‧‧‧‧‧‧
Follow my public account and reply "Join Group" to join the technical exchange group according to the rules.Click "Read the original text" for more shares. Feel free to share, bookmark, like, and view.