
Encryption is generally about encrypting binary encoded formats, which corresponds to Python as Bytes. You need to convert str to Bytes using encode and decode.
import hashlib
def MD5(str):
h1 =hashlib.md5()
h1.update(str.encode(encoding = 'utf-8'))
return h1.hexdigest() # lowercase
if __name__ == "__main__":
str ='123232'
md5 =MD5(str)
print("Before encryption: "+ str)
print("After encryption: " + md5)
Output:
Before encryption: 123232
After encryption: 552effa0980dcec34d29ca4ad27a11e0
import base64
def Ebase64(string):
return str(base64.b64encode(string.encode("utf-8")),'utf-8')
if __name__ == '__main__':
string = '123数据'
print(f"{string}:{Ebase64(string)}")
Output:
123数据:MTIz5pWw5o2u
SHA1 encryption is more secure than MD5, but also slower.
a = "中国欢迎你".encode('utf-8')
print(a)
import hashlib
b = hashlib.sha1(a).hexdigest()
print(b)
Output:
b'\xe4\xb8\xad\xe5\x9b\xbd\xe6\xac\xa2\xe8\xbf\x8e\xe4\xbd\xa0'
1457a6057bfc0711a34595ec7a54c47fc4d7ab9f
(1) DES encryption
from Cryptodome.Cipher import DES
import binascii
# Key length 64 bits
key = b'abcddesw'
def pad(text):
# Encryption function, if text is not a multiple of 8, pad it
while len(text) % 8 != 0:
text += ' '
return text
# Create DES instance
des = DES.new(key,DES.MODE_ECB)
text = "I'm china!"
padded_text = pad(text)
print(padded_text)
# Encrypt
encrypted_text = des.encrypt(padded_text.encode("utf-8"))
print(encrypted_text)
# Decrypt, rstrip() returns a string with all characters removed from the end of the string
plain_text = des.decrypt(encrypted_text).decode().rstrip(' ')
print(plain_text)
Output:
I'm china!
b'\x04mp5.\xac\xd5\xa76M\xc6>s\x95F\xa4'I'm china!(2) 3DES enhances the difficulty of brute force by extending the DES key length.
(3) AES encryption
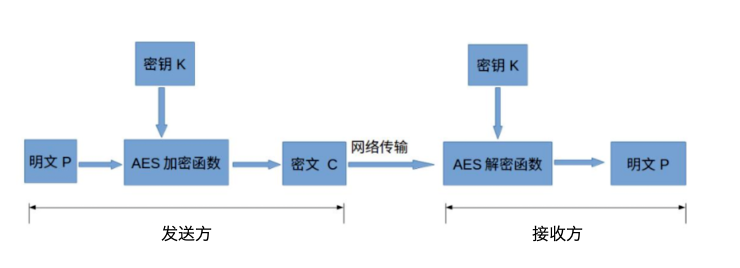
from Cryptodome.Cipher import AES
from Cryptodome import Random
from binascii import a2b_hex
data = '南来北往'
# Key must be 16 (AES-128), 24, 32
key = b'this is a 16 key'
# Generate a non-repeating key vector equal to the AES block size
iv =Random.new().read(AES.block_size)
print(iv)
# Initialize AES object using key and Iv
mycipher = AES.new(key,AES.MODE_CFB,iv)
print(mycipher)
cip = mycipher.encrypt(data.encode())
# Add iv to the beginning of the encrypted key
ciptext =iv + cip
print(ciptext)
# Decrypt requires key and iv to generate AES object, first 16 bits are iv
mydecrypt = AES.new(key,AES.MODE_CFB,ciptext[:16])
# Last 16 bits are the key
decrytext = mydecrypt.decrypt(ciptext[16:])
print(decrytext.decode())
Output:
b'"I\xa8e\xd0\x95MK>\xe7+\x07'\xde\xe2\x13'
<Cryptodome.Cipher._mode_cfb.CfbMode object at 0x000000000291B8D0>
b'"I\xa8e\xd0\x95MK>\xe7+\x07'\xde\xe2\x13\xf6\x1e\xd2^R8\xf9.\x05z\x8b\xb5'
南来北往
(3) RSA asymmetric encryption
Extension: APP security recommendations: 1. When using RSA algorithm for digital signatures, it is recommended that the key length should not be less than 512 bits, preferably 1024 bits. 2. When using RSA encryption, if the working mode is set to ECB, it is recommended that the padding method be OAEPWithSHA256AndMGF1Padding.
import rsa
def rsaEncrypt(str):
# Generate public key, private key
(pubkey,privkey)=rsa.newkeys(512)
print("pub:",pubkey)
print("priv:",privkey)
content =str.encode('utf-8')
crypto=rsa.encrypt(content,pubkey)
return (crypto,privkey)
def rsaDecrypt(str,pk):
content = rsa.decrypt(str,pk)
con=content.decode('utf-8')
return con
(a,b)=rsaEncrypt("hello")
print('Encrypted ciphertext:')
print(a)
content = rsaDecrypt(a,b)
print(content)
Output:
pub: PublicKey(10224716067198480147617638754883355202713448141531736080412727285989130693341793946859623298056210410740038704683106707884390481307747163248998182831361163, 65537)
priv: PrivateKey(10224716067198480147617638754883355202713448141531736080412727285989130693341793946859623298056210410740038704683106707884390481307747163248998182831361163, 65537, 5400282618215789429324457144231998061960774737491485919212141878285972345666166553226592021005152635629640166074005915666141173161129536124011174050492769, 5818723586322406878415248931016889575549272227294253767355937422578481050392848819, 1757209449033268399430211948686844080896027565472554340862366664022635977)
Encrypted ciphertext:
b'\x9e\xf1\xbd\x87S\xd2\xae\xb0]N\xec1mI\xd3mS.\xa8\xbd\x1f\xbc\xde\x96\xaf\xf0\xd7\xe3\xd0\xaf\x1b\x8c\xef\xa7\xd8\xe6\xd9\x8a\xdaL\x86Z\x13\x0e_Q\x9b\x97\xc2\xf6H\xa4=\x93\xad\x00\xfbNP\x19\xb04\xc1\xab'hello

 Learning arrangements!
Learning arrangements!

This premium course lasted over 8 months, went through multiple sessionswith practical training,not only added more practical cases, but also deeply integratedthe management content of executive MBA with the work content of the testing department..


If you don’t want to miss it, just mark us as a star!
Step 2: Click the upper right corner “···”
Step 3: Click “Mark as Star”
Reprinted from: http://navo.top/bqeUbm
“Looking” click it
What time is it now, cheer up a bit
👇👇👇
↓ Programmers pretending to be HR interviewing others, what can they have in mind…