Table of Contents:
- Introduction
-
I. Conventional Devices
-
1. Patent Protection
-
2. Code Encryption
-
3. Authorization Verification
-
4. Continuous Updates and Improvements
-
II. Embedded Devices
-
1. Polishing Key Chip Logos
-
2. Disabling Debug Serial Ports
-
3. Flash Read Protection Settings
-
4. Encrypting and Obfuscating Key Information
-
III. Cracking the Junzheng T Series Program
-
1. Locating the Root File System
-
2. Decompressing and Restoring the Root File System
-
IV. How to Prevent Reverse Engineering?
-
1. Encrypting the Entire Root File System
-
2. Encrypting Only Key Information
-
Conclusion
Introduction:
In product design and development in China, it is difficult to avoid being copied or imitated. Before establishing a technological barrier, preventing product cloning is an unavoidable issue.
I. Conventional Devices
The main protective measures for conventional devices include:
- Patent Protection
- Code Encryption
- Authorization Verification
- Continuous Updates and Improvements
1. Patent Protection
For significant technological inventions or innovations, patents should be applied for as soon as possible. Although the current protection of intellectual property rights in China is limited, applying for a patent is still useful, as it can at least prevent others from applying for the patent first, which could lead to infringement.
2. Code Encryption
This involves balancing encryption with performance and cost. If the device cost is not very sensitive, an encryption chip can be added; if the program needs to be encrypted, this may affect the execution efficiency of the program.
3. Authorization Verification
Introduce an authorization verification mechanism in the product, such as using encryption keys or authorization certificates to verify the legitimacy of the product. This can effectively prevent unauthorized copying and use.
4. Continuous Updates and Improvements
Timely fix vulnerabilities and defects in the software, and continuously improve and upgrade functionalities. This helps maintain a competitive advantage and reduces the motivation for cloning.
II. Embedded Devices
For embedded devices, the main considerations involve structural appearance, hardware circuits, and embedded software. In addition to the methods mentioned above, several other approaches can increase the difficulty of being cloned.
- Polishing Key Chip Logos
- Disabling Debug Serial Ports
- Flash Read Protection Settings
- Encrypting and Obfuscating Key Information
1. Polishing Key Chip Logos
In embedded systems, different processors use different cross-compilation tools, and the program partition layout varies, which can increase the difficulty of reverse engineering analysis.
2. Disabling Debug Serial Ports
For normal products, the debug serial ports should be disabled during mass production for two reasons:
- First, to avoid signal interference from the debug serial port, which can affect system stability;
- Second, the debug serial port usually prints some debugging and system information, which can be used by others for reverse analysis.
3. Flash Read Protection Settings
Some MCUs allow read protection to be set in their programming tools, meaning that the program inside the MCU cannot be directly read using tools. Regular flash also has protection mechanisms, but the protection level is weak. Adding an encryption chip can prevent the program from being directly copied, but it may affect program efficiency and increase device costs.
4. Encrypting and Obfuscating Key Information
In embedded systems, due to the limited flash capacity, the execution program is generally converted in format and then compressed. During runtime, it is first decompressed, then converted, and finally executed. An additional step can be added here: encrypting and obfuscating key information before conversion and compression, which can significantly increase the difficulty of reverse analysis.
III. Cracking the Junzheng T Series Program
Below is an analysis based on the Junzheng Guangfa solution:
The execution program of Junzheng is placed on the root file system. After the root file system is mounted, some initialization settings are performed, and then the execution program runs directly from the root file system.
To crack an official firmware of the Junzheng T series, the basic process should be as follows:
- Locate the root file system
- Decompress the root file system
- Restore the file system format
- Find the executable program
- Perform disassembly and other operations on the executable program
1. Locating the Root File System
This involves the starting position and size of the root file system.
Generally, the root file system is in a separate partition, and the partition information can be obtained from the boot parameters, along with the type of the root file system.
For the official firmware from Junzheng, bootargs and bootcmd information can be found in the boot:
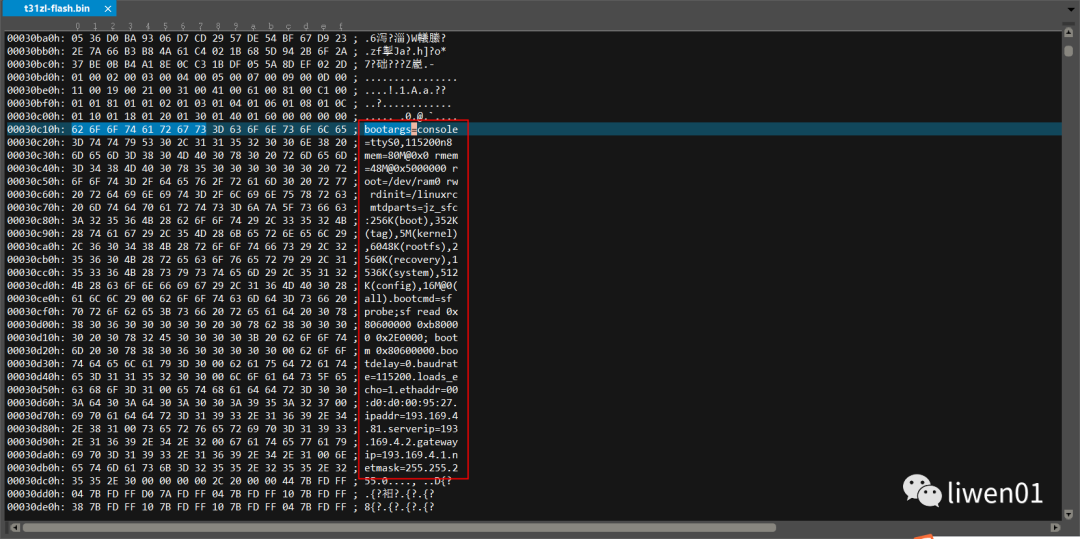
From this, we can see that the size of rootfs is 6048K, and the starting position is 5728K = 0X598000.
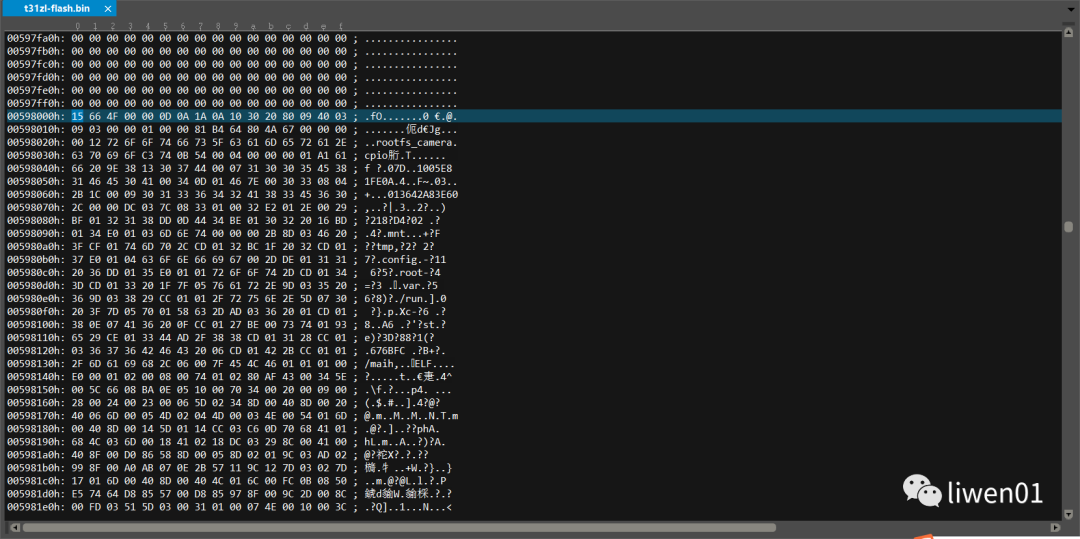
2. Decompressing and Restoring the Root File System
The official packaging method is:
find . | cpio -H newc -o > ../rootfs_camera.cpio
lzop -9 -f rootfs_camera.cpio -o rootfs_camera.cpio.lzo
find . | cpio -H newc -o > ../rootfs_camera.cpio
This uses the cpio command to package the current files and their subfiles into the rootfs_camera.cpio file, using the newc file format.
lzop -9 -f rootfs_camera.cpio -o rootfs_camera.cpio.lzo
This uses the lzop command to compress rootfs_camera.cpio into rootfs_camera.cpio.lzo.
If you want to reverse the operation, you can execute the following commands:
lzop -d rootfs_camera.cpio.lzo
cpio -i < rootfs_camera.cpio
lzop -d rootfs_camera.cpio.lzo
This decompresses the rootfs_camera.cpio.lzo file to the current directory:
cpio -i < rootfs_camera.cpio
The contents of the rootfs_camera.cpio file will be unpacked and restored to the original file and directory structure, which will appear in the current working directory.
By examining the etc/init.d/rcS file, you can find which programs are started, where the corresponding programs are placed, and ultimately obtain the desired information through disassembly and other means.
IV. How to Prevent Reverse Engineering?
Based on the analysis of the official design from Junzheng, it is relatively easy for knowledgeable engineers to crack it. So what measures can be taken to increase the difficulty of cracking?
1. Encrypting the Entire Root File System
Encryption can be symmetric or asymmetric. In embedded systems, symmetric encryption algorithms, such as AES, are recommended.
Compilation and Packaging Process:
- Select AES key length
- Generate key
- Use the key to encrypt files
- Package the encrypted
rootfs_camera.cpio.lzointo the firmware package
Device Operation Process:
- The kernel will copy the root file system into memory during startup and then decompress it
- Before decompression, use the key from the packaging process to decrypt it, and then continue executing as per the original process.
Advantages and Disadvantages Comparison:
- Advantages include the ability to encrypt the entire file system, making cracking more difficult;
- Disadvantages include potential impacts on startup speed, which can be a concern for systems requiring fast boot times.
2. Encrypting Only Key Information
For embedded systems, key information may include:
- Certain key algorithm libraries
- Product serial numbers and other information
- Algorithm model files, etc.
The encryption and decryption methods are similar to those for encrypting the root file system, with the difference being that decryption occurs at different stages of system operation.
- Advantages include no impact on system startup speed;
- Disadvantages include relatively easier reverse analysis.
Conclusion:
All encryption can potentially be cracked. Actual product designs should vary encryption levels based on the security level of the product industry. While it is not encouraged to copy or crack others’ devices, it is essential to protect one’s intellectual property reasonably.
Continuously updating and improving product design solutions can help establish technological barriers, reducing concerns about product cloning.
END
Source: liwen01
Copyright belongs to the original author. If there is any infringement, please contact for deletion.
▍Recommended Reading
C Language, Circular Queue
Embedded Development: Should You Take Side Jobs?
The Most Popular Software in the World Abandons Git
→ Follow for more updates ←