Abstract: The application of NB-IoT in the Internet of Things is becoming increasingly widespread. However, due to characteristics such as massive access, low terminal computing power, and a variety of services, NB-IoT IoT systems face numerous security issues. This article first analyzes the system architecture of NB-IoT IoT systems, dissecting the security risks faced at the terminal layer, network layer, and application layer. It proposes an integrated “cloud-network-terminal” security architecture for NB-IoT IoT systems, and provides a detailed analysis of security architecture from three aspects: terminal security reinforcement, network security protection, and application service security, offering a reference for security solutions for NB-IoT projects.
The Chinese government places great importance on the development of the Internet of Things. In June 2017, the Ministry of Industry and Information Technology issued a notice on comprehensively promoting the construction and development of mobile IoT (NB-IoT), requiring the acceleration of network deployment and the establishment of NB-IoT (Narrow Band Internet of Things) network infrastructure. By 2020, the NB-IoT network is expected to achieve comprehensive general coverage, with deep coverage for indoor, traffic networks, underground pipelines, and other application scenarios, with a base station scale reaching 1.5 million. In 2016, China Mobile launched the first standardized NB-IoT network application. According to Gartner’s predictions, by 2020 there will be 26 billion IoT devices globally, with a market value exceeding $300 billion. By 2021, IoT terminals are expected to exceed the number of Internet terminals by more than two times.
“Narrowband IoT” is a communication technology designed for the application scenarios of interconnecting things. Compared to traditional “human-to-human” connections that require high bandwidth and continuous internet access, machine-to-machine communication generally belongs to low-consumption, sporadic applications. NB-IoT is an emerging technology in the IoT (Internet of Things) field, built on existing cellular networks and can be directly deployed on existing GSM (Global System for Mobile Communications), UMTS (Universal Mobile Telecommunications System), and LTE (Long Term Evolution) networks. It supports low-power devices in wide-area cellular data connections, featuring high coverage, low power consumption, low cost, and large connectivity. The NB-IoT system adopts a “cloud-network-terminal” architecture, where “cloud” is the IoT business/service platform established by operators/users, “network” is the NB-IoT network deployed by operators, and “terminal” refers to various NB-IoT IoT terminals.
NB-IoT IoT and mobile internet are both open networks, facing the same security risks as mobile internet. At the same time, NB-IoT IoT has characteristics such as a huge number of terminals, fragmented service access, and a variety of service types, making the security risks more complex. This article will analyze the security risks of NB-IoT IoT systems and propose a security system architecture and solutions for NB-IoT IoT systems.
1. Security Risk Analysis of NB-IoT IoT System Architecture
We first analyze the system architecture, service characteristics, and security risks of NB-IoT, based on which we will design the security architecture.
The architecture of the NB-IoT IoT system is shown in Figure 1. The system consists of three layers: terminal layer, network layer, and application layer.
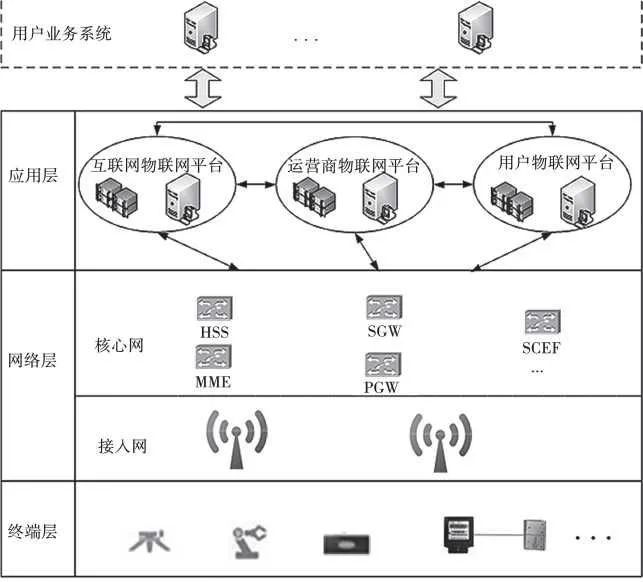
Figure 1: Schematic Diagram of NB-IoT System Architecture
The terminal layer, often referred to as the sensing layer, is the foundation for all upper layers and services of the NB-IoT architecture. The terminal layer includes NB-IoT terminals that meet various user needs, which vary in form, functionality, and the operating systems and computing environments they use. All terminals are equipped with NB-IoT communication modules. The terminal devices have low power consumption, long standby times, weak computing power, and are difficult to upgrade, with small data transmission volumes and long communication intervals. The network layer primarily consists of the operator’s NB-IoT basic network, with few users establishing their own NB-IoT networks, including NB-IoT access networks and core networks. The NB-IoT network features wide coverage and large connectivity, with a single sector capable of supporting up to 100,000 connections, which is 50 to 100 times the capacity of traditional mobile communications.
The application layer serves as the IoT business platform. Since the user business system is part of the user information system, it is not included in the application layer of the NB-IoT IoT system. The application layer includes public internet business platforms, operator business platforms, and user-built business platforms, primarily responsible for collecting, aggregating, and processing information from IoT terminals; managing and controlling terminal status; and facilitating information exchange with user business systems. The operator’s business platform typically implements functions for collecting and managing terminal information, forwarding terminal business information, and providing users with open services such as terminal positioning information publication and terminal status queries.
1.2 Security Risk Analysis
Based on the system architecture of NB-IoT IoT systems, we primarily analyze security risks from the terminal layer, network layer, and application layer.
The NB-IoT terminal, in addition to the security risks associated with mobile terminal devices, faces the following security risks:
(1) Security risks arising from the complex deployment environment of terminals. Many NB-IoT terminals are deployed in outdoor and unsafe locations, making them vulnerable to theft and control. Once a terminal is compromised, it can easily lead to the leakage of user privacy and other information, resulting in counterfeit terminals accessing the system to launch attacks.
(2) Security risks arising from low terminal capabilities. NB-IoT terminals are characterized by simple functionality, ultra-low power consumption, and low cost, leading to simple system architecture with low computing and storage capabilities. The terminal’s computing power is insufficient to support the migration of security and encryption functions from mobile terminals/computers, and lightweight security and encryption functions have not been deployed in a timely manner. As a result, the majority of NB-IoT terminals have weak security protection capabilities, even in a “naked” state, posing significant security risks to the system.
(3) Security risks arising from difficulties in terminal upgrades. Vulnerabilities in information devices are gradually discovered and patched, making upgrade capability essential for all information devices. NB-IoT terminals are widely deployed in large numbers, and the lack of rich network communication resources makes timely upgrades challenging. Terminals that cannot be upgraded in time are security hazards for the system.
The security risks faced by the NB-IoT system’s network layer are as follows:
(1) Security risks posed by massive terminal access to the network. The number of NB-IoT terminals is extremely large, requiring the network layer to have efficient and rapid security access capabilities, which presents significant challenges and security risks to the NB-IoT system.
(2) Security risks arising from open networks. The NB-IoT access network and core network are open to massive terminals, making the network layer susceptible to DDOS attacks, man-in-the-middle attacks, and other network attacks from terminals and wireless space, posing risks of system intrusion and information tampering. The NB-IoT core network needs to be open to IoT business platforms to provide services such as positioning, thus the network layer faces security attacks initiated from the public network.
The security risks faced by the application layer of the NB-IoT system are as follows:
(1) Security risks posed to user IoT platforms by public network access. The IoT business platform connects to the operator’s NB-IoT core network and access network, and may also connect to the internet for information exchange based on business needs. Therefore, the user IoT platform faces security attacks initiated from terminals and the internet, with the business platform facing risks of privacy leakage and information tampering.
(2) Security risks posed to the operator’s IoT platform by multi-user/multi-business access. The operator’s IoT platform exchanges information with multiple users/multiple business terminals, and also exchanges information with multiple user business systems. If the security protection mechanisms are inadequate, it will lead to cross-access of user business information and illegal information flow, posing security risks to the user’s business platform.
(3) Security risks arising from the open services provided by the operator’s IoT business platform. The operator’s IoT business platform needs to provide users with open services such as terminal positioning information publication and terminal status queries, facing attacks from the internet/user information systems.
2. NB-IoT IoT Security Architecture
The NB-IoT IoT security architecture will be designed based on the system architecture to address the security risks faced. The goal of constructing the security architecture is to establish an integrated security protection system for the NB-IoT IoT system, achieving manageable and controllable terminals, stable and reliable networks, and usable application layers. Based on the above principles, we propose the security architecture of the NB-IoT IoT system as shown in Figure 2.
Below, we will explain the security architecture of the IoT system from the terminal layer, network layer, and application layer.
Currently, there are no unified standards for the form, structure, functionality, and architecture of NB-IoT terminals. Therefore, we adopt “terminal security reinforcement” to indicate the security protection functions of terminals. The NB-IoT terminal primarily focuses on security protection in the following aspects.
(1) Achieving physical security for terminals, such as physical protection for terminal interfaces and chips; adding anti-tamper designs to terminals where structurally feasible, allowing for forced disassembly and self-destruction protective functions.
(2) Achieving system security for terminals, using trusted computing architecture to establish a secure operating environment for terminals where conditions allow; applying the principle of least privilege for terminal control, disabling debugging functions and other potentially hazardous interface functions.
(3) Designing lightweight encryption algorithms, encryption systems, and security protection mechanisms suitable for the NB-IoT system, using encryption technology as the basis for achieving overall security protection for terminals.
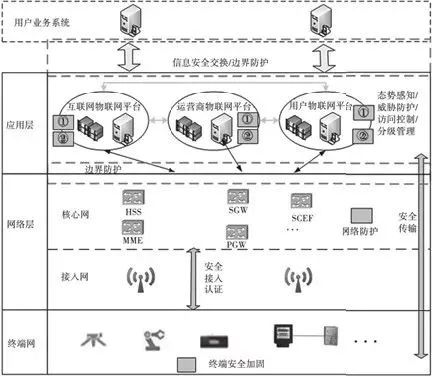
Figure 2: Schematic Diagram of NB-IoT IoT System Security Architecture
(4) Encrypting and controlling access to important data such as user privacy, sensitive information, and configuration files within the terminal.
(5) Supporting real-time status monitoring of terminals, enabling emergency protective measures such as network shielding, remote locking, and remote data erasure for terminals with abnormal statuses.
(6) Providing remote upgrade services for terminals, supporting remote upgrade package pushing and mandatory upgrades to timely patch security vulnerabilities in terminals.
(7) Implementing a terminal system access control system, establishing security standards for terminals, testing and evaluating incoming terminals, and restricting access to the system for terminals that do not pass evaluation.
The NB-IoT network, characterized by massive terminal access and openness, requires security protection for the network layer in the following aspects.
(1) Supporting terminal identity authentication for network access, implementing mutual identity authentication between terminals and the network to restrict illegal terminal access. Utilizing lightweight encryption algorithms to design a lightweight, efficient, and large-scale mutual network access authentication mechanism.
(2) Providing end-to-end encryption communication protection for high-security users between terminals and business platforms, ensuring the confidentiality, integrity, and non-repudiation of information transmission.
(3) Establishing boundary security protection mechanisms such as network access control, abnormal traffic detection/traffic cleansing, and intrusion detection and prevention between the NB-IoT core network and access network, as well as between the core network and business platforms.
(4) Building foundational network security protection capabilities against DDOS (Distributed Denial of Service) attacks, tampering, intrusion, and viruses at the NB-IoT network layer, capable of defending against signaling deception, replay attacks, man-in-the-middle attacks, etc.
The application layer of the NB-IoT IoT system requires the following security protections:
(1) Basic protection capabilities for the business platform
1) The IoT business platform needs to implement security functions such as identity authentication, access control, security auditing, and security monitoring to ensure the secure operation of the business platform.
2) Implement boundary security protection between the IoT business platform and the core network, as well as between the business platform and user information systems; achieve controlled information exchange between the business platform and user information systems.
3) The IoT business platform should provide data storage protection, data transmission protection, and access control for data to ensure the confidentiality, integrity, and availability of business platform data.
(2) Business security and management security capabilities for the business platform
1) Access control and hierarchical management.
Since the business platform supports the access of various terminals and the processing of multiple types of services, it is necessary to implement partitioned and hierarchical protection of the business. Control can be implemented according to user access to the business platform, strictly limiting illegal access and information retrieval between different partitions. Hierarchical control of business can be implemented based on the business level to manage resource allocation and access control.
2) Situational awareness and threat protection.
The IoT business platform can achieve situational awareness of network security, real-time status monitoring of all terminals and network elements, prohibiting illegal terminals and “compromised” network elements from accessing the system. The IoT business platform can monitor business activities and prevent threats, supporting protocol analysis of business data to identify security attacks based on application protocols and filter/limit illegal business access. The business platform can perform big data analysis on the collected system business data for threat identification, risk warning, and emergency response.
With the gradual expansion of NB-IoT applications and the refinement of user demands, the architecture presented in this article may differ from the final system architecture. However, this article primarily analyzes the common security risks faced by NB-IoT IoT systems based on a common system architecture, proposing a universal security architecture that can be tailored and enhanced according to the actual deployment and business needs of the system.
Original Source: Journal of Information Security and Communication Confidentiality



