In traditional network environments, network operators typically adopt and maintain a large number of dedicated hardware devices. As network services continue to increase, these network hardware also need to be updated or added, which not only increases economic costs but also complicates management and maintenance as the number of devices grows. This has led to the emergence of Network Function Virtualization (NFV) technology.
1. Overview
NFV was initially proposed by network operators, aiming to virtualize various network device functions (such as deep packet inspection, load balancing, data switching, etc.) onto industry-standard physical devices (servers, switches, storage devices, or end-user terminals) through IT virtualization technology, thereby changing the current network operation architecture model. NFV abstracts network functions from traditional devices and runs them on IT industrial standard equipment, thus reducing the costs associated with migration and deployment.
2. Relationship between NFV and SDN
Network Function Virtualization and Software Defined Networking are highly complementary but not completely interdependent. From the perspective of problem-solving, NFV and SDN emphasize different aspects.
SDN originated in campus networks, emphasizing the separation of control and forwarding functions. Through centralized management and the use of open standard interfaces, it abstracts the network to achieve faster and more flexible network management. In contrast, NFV is driven by network operators and aims to address the growing deployment of dedicated network devices. NFV can be deployed independently of SDN, and the two can also be combined.
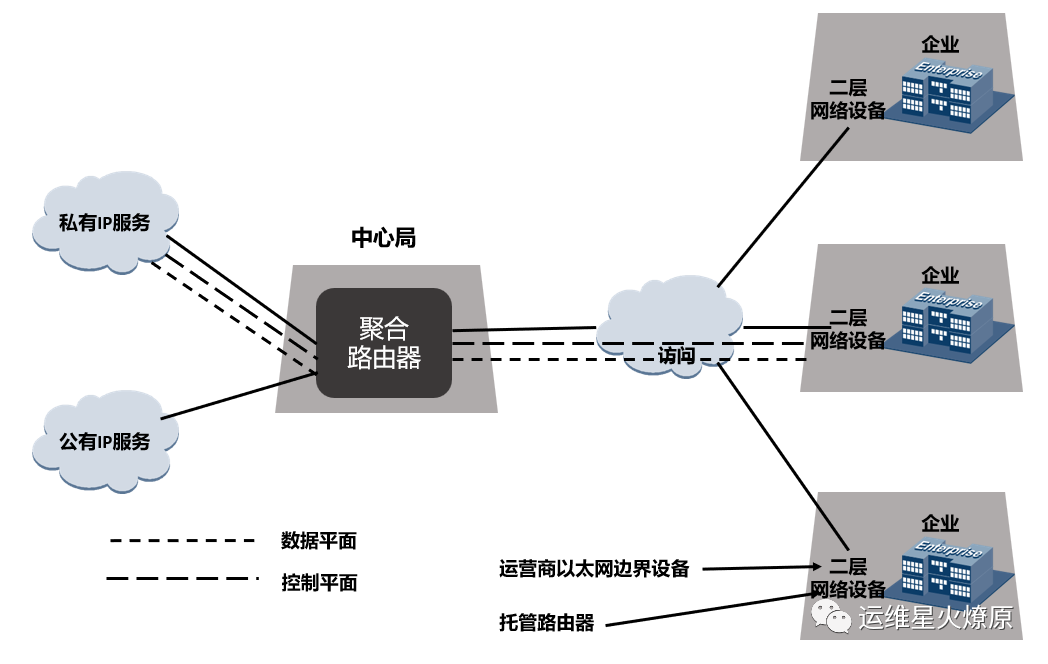
The following diagram illustrates the traditional router service deployment model, where each customer using the service requires a router to provide it.
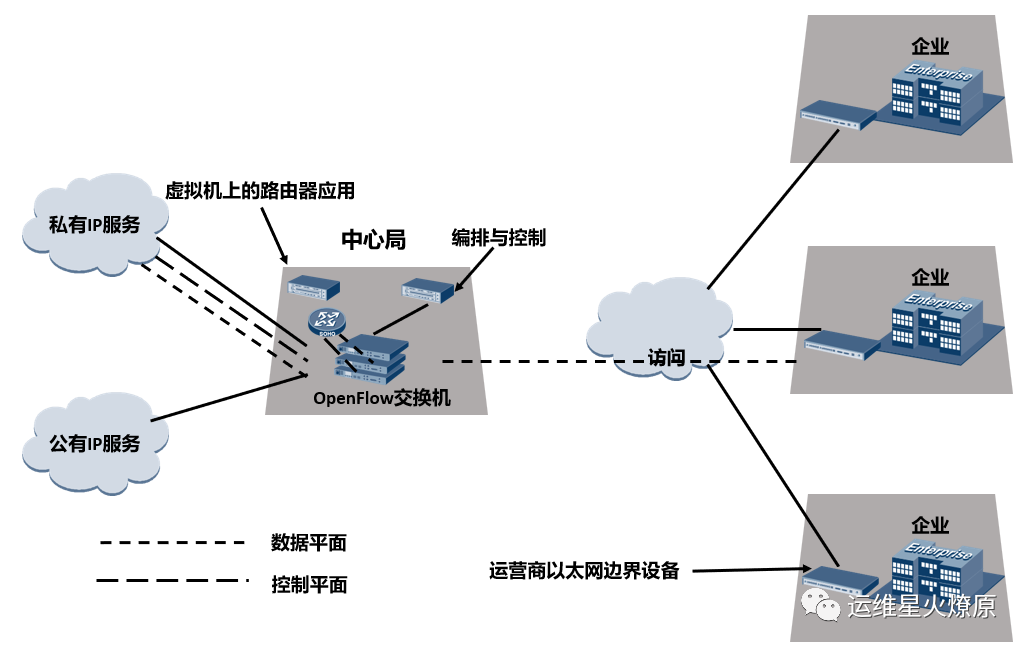
With the introduction of NFV, using the functionality of virtual routers, all user sites can access services through the network interface device (NID) on the left side—virtual routers.
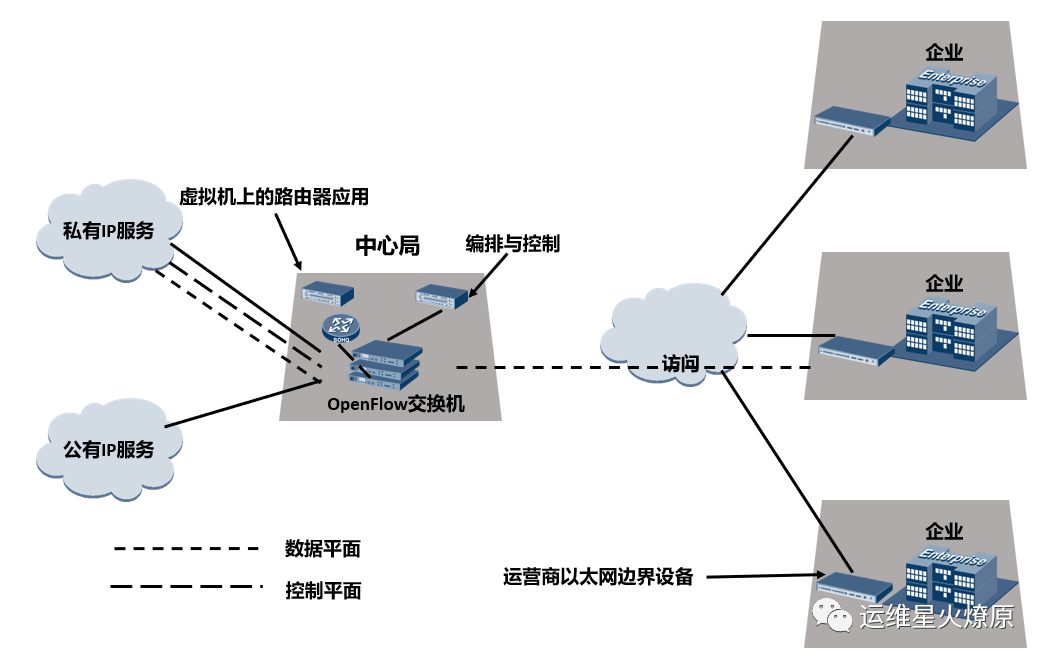
By introducing SDN on top of NFV, the forwarding plane and control plane are separated, with the packet forwarding controller elevated to the control plane, while the specific forwarding actions are executed by the forwarding plane.
3. Applicable Scenarios for NFV
With the development of cloud computing and big data, an increasing number of business demands have emerged, which puts tremendous pressure on network operators for expansion and maintenance, while also requiring operators to manage traffic at lower costs to enhance data traffic revenue. Therefore, network operators need a more open, flexible, and efficient architecture. By utilizing NFV technology, hardware and software functions can be decoupled, allowing for efficient use of hardware resources while enhancing system flexibility in deployment and maintenance.
Although NFV is developing rapidly, it is not suitable for every scenario. For example, network products that support low-latency and high-throughput data transmission are not well-suited for NFV, as these products typically have high performance requirements and rely on high-performance switches or routers. NFV is more suitable for CPU-intensive scenarios, such as mobile core networks.
4. Challenges Facing NFV
As NFV develops, it also faces several challenges:
-
Portability/Interoperability: Currently, there is no unified standard in data centers, making it difficult for different operators to define a common standard interface when invoking and executing virtualized devices, thus highlighting issues of portability and interoperability.
-
Migration from traditional devices and compatibility with existing systems: Network Function Virtualization breaks the traditional network operation architecture model, so the development of NFV needs to consider coexistence and migration with the original network devices of operators. In other words, NFV should be able to work collaboratively in a mixed mode of traditional physical network devices and virtualized network devices.
-
Security: The introduction of NFV needs to consider the network security of operators, while ensuring that availability is not compromised. Network Function Virtualization should allow for the reconstruction of network functions after failures to enhance network security and availability.
-
Management and Business Processes: Under an open and standardized architecture, consistency in management and business processes needs to be ensured. NFV provides a way to unify management, business, and defined standards and requirements quickly through software network integrated devices.
-
Performance Issues: The performance bottleneck of virtualized core networks mainly focuses on I/O interface data forwarding, and the challenge lies in how to maintain performance metrics without significant degradation.
-
Standardization Issues: The standardization of NFV differs significantly from traditional telecommunications standardization work, as the standardization content required for NFV virtualization architecture is not only focused on network architecture or network functions but also heavily concentrated on management interfaces. Currently, the standardization of interfaces and protocols related to virtualization architecture involves multiple organizations, making the standardization work for NFV a long-term endeavor.
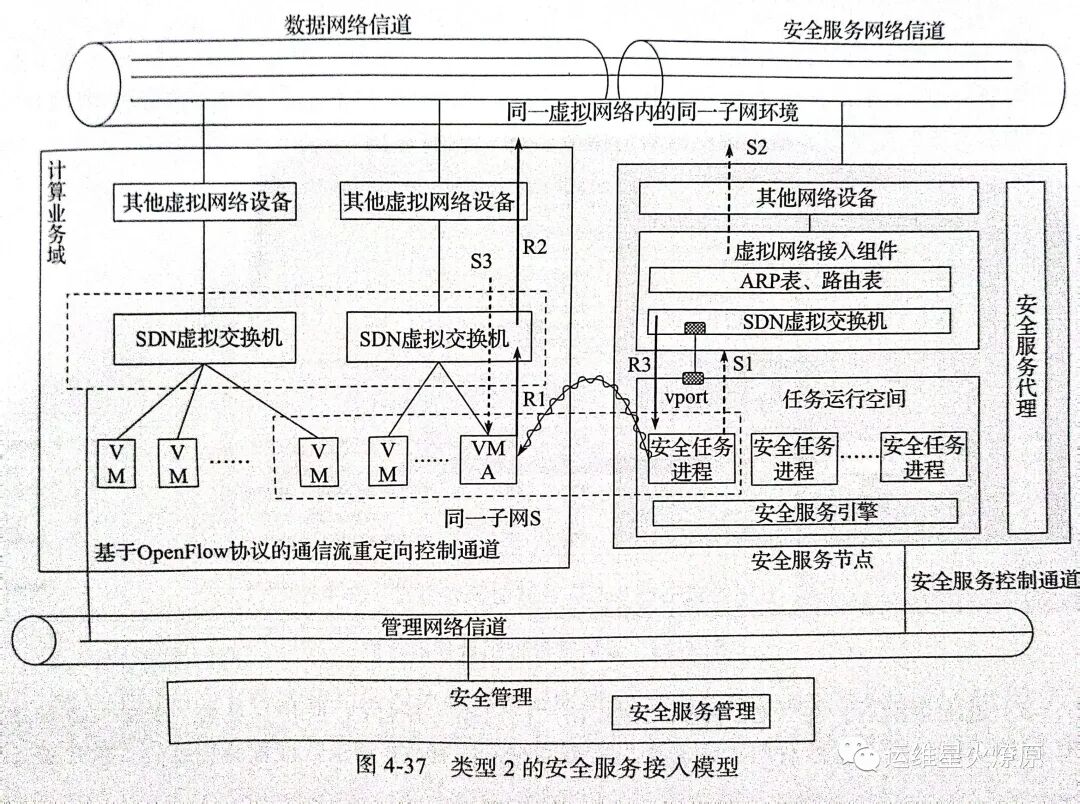
Accessing Security Services in Cloud Environments
For IaaS virtual network environments, hardware-based security services are transparent to the virtual network environment. Therefore, traditional security services such as virtual firewalls and vulnerability scanning need to consider new methods and technologies to access multi-tenant networks in cloud environments.
Types of Security Services
Current mainstream and relatively mature network security services (such as firewalls, vulnerability scanning, intrusion detection systems, etc.) can be roughly divided into two types based on their operating modes.
-
Type 1: Security service components do not send communication flows themselves but process the received data to achieve system security protection. For example, firewalls filter communication for the data flows that pass through, and IDS makes intrusion detection judgments based on the received communication flows.
-
Type 2: Security service components need to send communication flows themselves, and based on the feedback information from the sent data packets, they comprehensively assess the system’s security status and provide security evaluation reports. For example, vulnerability scanning and port scanning security services.
Accessing Type 1 Security Services
Type 1 security services do not generate any data flows but only process and forward the data flows. In this case, the security service needs to have a software implementation foundation and also requires some type of carrier to host the software. It should also use methods such as traffic redirection to ensure that the communication traffic of specified virtual machines can reach the security service tools, allowing them to serve tenant virtualization.
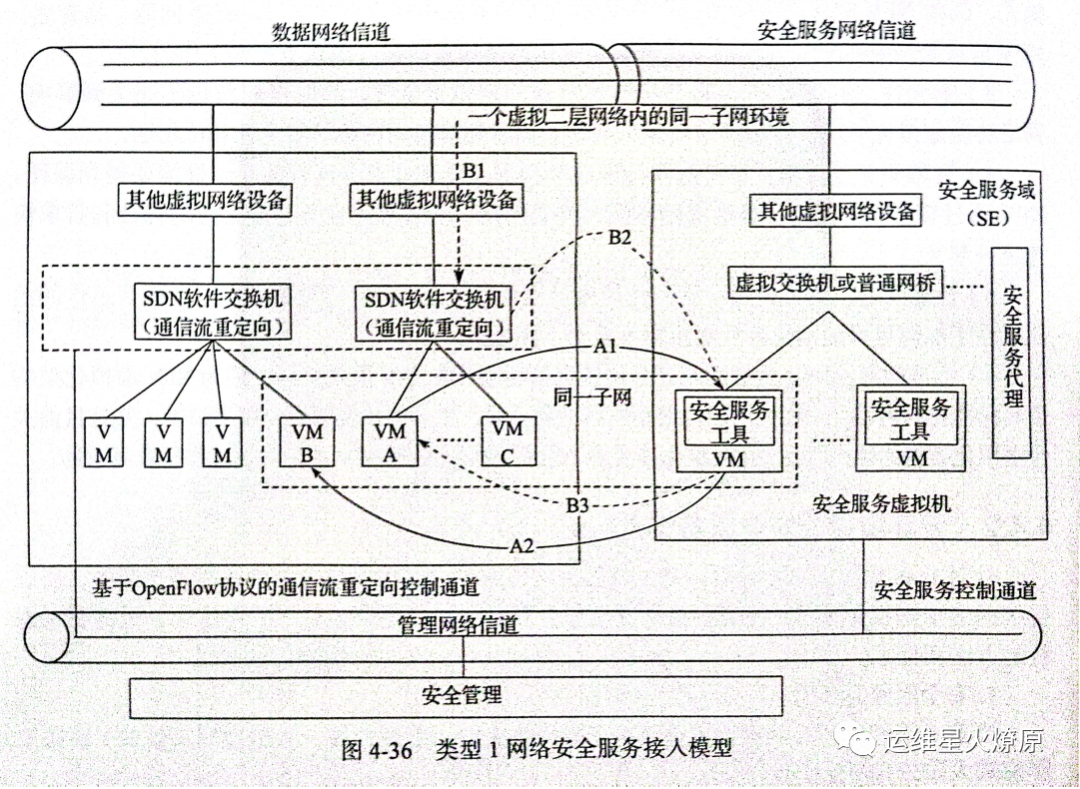
Accessing Type 2 Security Services
Type 2 security services need to send communication flows and comprehensively assess the system’s security status based on feedback information. This access method is suitable for tools like vulnerability scanning. Similarly, in addition to requiring a software implementation foundation, it is also necessary to consider how the communication sent by the security service component reaches the tenant network. Although this type of security service can also adopt Type 1 access methods by encapsulating the security service tools within virtual machines and instantiating them in the tenant virtual machine’s network, this approach often overlooks the capability of security tools to support multi-task parallel processing. For example, vulnerability scanning systems can scan multiple target hosts within a network in parallel. Using Type 1 access methods would prevent this capability from being utilized. Additionally, since vulnerability scanning engines and plugins generally require significant storage space, the overhead introduced by instantiating vulnerability scanning virtual machines as the number of tenants increases also needs to be considered.