Blue Team – Technical Exchange
In the field of information security, the characteristics of network security can be classified according to the OSI reference model, facilitating a systematic approach to analyzing and researching information network security risks.
What is the OSI Reference Model?
The OSI (Open System Interconnect) model, commonly known as the “OSI Reference Model”, is a network interconnection model studied by the ISO organization in 1985. This architecture standard defines a seven-layer framework for network interconnection (physical layer, data link layer, network layer, transport layer, session layer, presentation layer, and application layer), known as the OSI Open System Interconnect Reference Model.
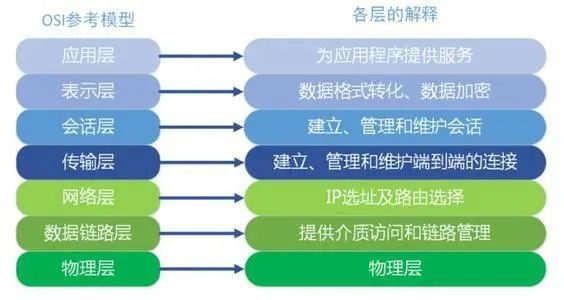
Functions of the Seven Layers of the OSI Reference Model
1
Application Layer
The Application Layer is the highest layer of the OSI reference model, serving as the interface between computer users and various applications and networks. Its function is to directly provide services to users, completing various tasks users wish to accomplish over the network.
2
Presentation Layer
The Presentation Layer is the sixth layer of the OSI model. It interprets commands and data from the Application Layer, assigns meanings to various syntaxes, and transmits them to the Session Layer in a specific format. Its main function is to handle the representation of user information, such as encoding, data format conversion, and encryption/decryption.
3
Session Layer
The Session Layer is the fifth layer of the OSI model, serving as the interface between user applications and the network. Its main task is to provide methods for establishing and utilizing connections between the Presentation Layers of two entities. The connection between the Presentation Layers of different entities is called a “session.” Therefore, the task of the Session Layer is to organize and coordinate communication between two session processes and manage data exchange.
4
Transport Layer
Main functions:
-
The Transport Layer is an interface layer that connects high and low layers in the network architecture. The Transport Layer is not just a standalone structural layer, but the core of the entire analytical protocol system. The Transport Layer mainly provides End-to-End services to users, addressing issues such as datagram errors and packet sequencing. It is a critical layer in computer communication architecture, shielding higher layers from the communication details of lower layers, allowing users to ignore the detailed workings of the physical layer, data link layer, and network layer. The Transport Layer uses the network connection services provided by the Network Layer and can choose between connection-oriented or connectionless services based on system requirements.
Common:
-
Transport data includes segments (Segment), TCP, UDP, processes, and ports.
5
Network Layer
Main functions:
-
The Network Layer primarily creates logical links for data transmission between nodes, selecting the best path for packets through routing algorithms to achieve functions such as congestion control and network interconnection. The Network Layer is a key layer that oversees the network from the highest node, the router, responsible for routing packets from the source network to the target network. The Internet is a collection of multiple networks, and it is the routing path selection function of the Network Layer that allows for smooth connections between multiple networks, enabling information sharing.
Common:
-
Transport data includes packets (Packet), routers, multilayer switches, firewalls, IP, IPX, RIP, OSPF.
6
Data Link Layer
Main functions:
-
The Data Link Layer establishes data link connections between communication entities, with the basic unit of transmission being a “frame,” and provides error control and flow control services to the Network Layer. The Data Link Layer consists of the MAC (Media Access Control sublayer) and LLC (Logical Link Control sublayer). The main task of the Media Access Control sublayer is to specify how frames are transmitted over physical lines. The Logical Link Control sublayer manages communication between devices on the same network link. The Data Link Control sublayer is primarily responsible for logically identifying different protocol types and encapsulating them. In other words, the Data Link Control sublayer receives network protocol data, packet datagrams, and adds more control information to transmit the packet to its target device.
Common:
-
Transport data includes frames (Frame), network cards, bridges, and layer 2 switches.
7
Physical Layer
Main functions:
-
The Physical Layer is the lowest layer of the reference model, primarily defining the electrical, mechanical, procedural, and functional standards of the system, such as voltage, physical data rates, maximum transmission distances, physical connectors, and other similar characteristics. The main function of the Physical Layer is to provide physical connections for the Data Link Layer using transmission media, responsible for the physical transmission of data streams. The basic unit of transmission for the Physical Layer is the bit stream, which consists of 0s and 1s, representing the most basic telecommunication signals or optical signals, and is the fundamental physical transmission characteristic.
Common:
-
Transport data includes bits (Bit), repeaters, hubs, and network cables.
There are slight differences between TCP/IP and OSI in layered modules. The OSI model emphasizes “what are the necessary functions of communication protocols,” while the TCP/IP model emphasizes “what kind of programs should be developed to implement protocols on computers.”
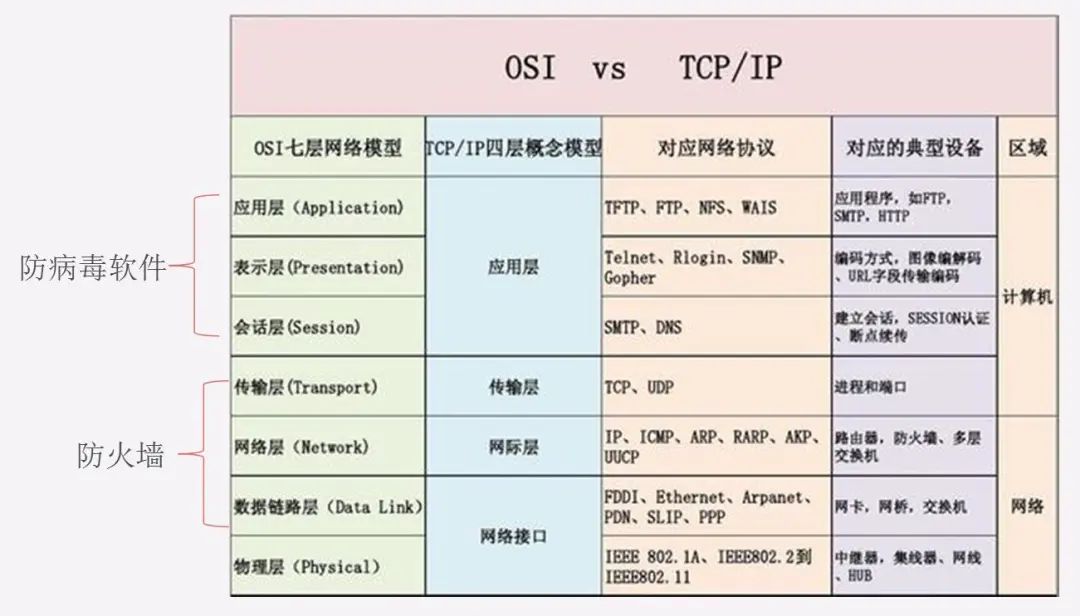
Comparison of OSI and TCP/IP
Data Encapsulation Principles
The OSI reference model defines the function of each layer, and the protocols that define the function of each layer focus on the functionality of communication protocols. Data encapsulation involves encapsulating data according to the protocol headers and trailers of the current layer, and then passing the encapsulated data to the lower layer.
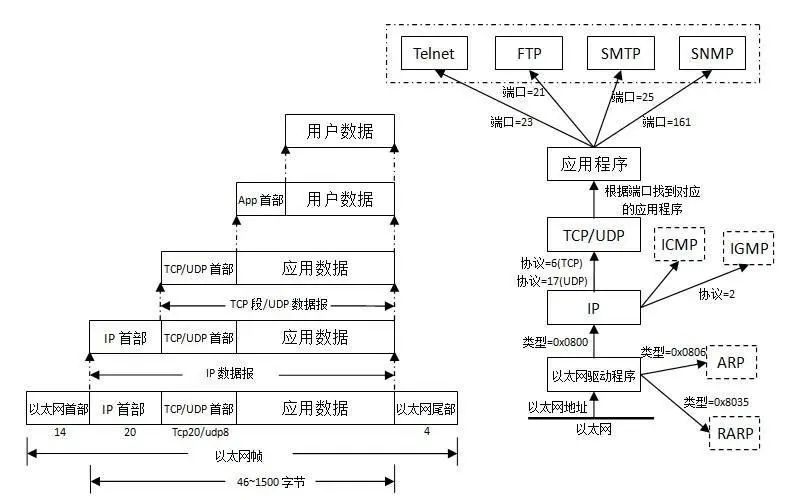
Data Encapsulation Diagram
Data Encapsulation – Application Data
Encapsulating user data with the App header as application data corresponds to the application layer, presentation layer, session layer in the OSI model, as well as the application layer in the TCP/IP model.
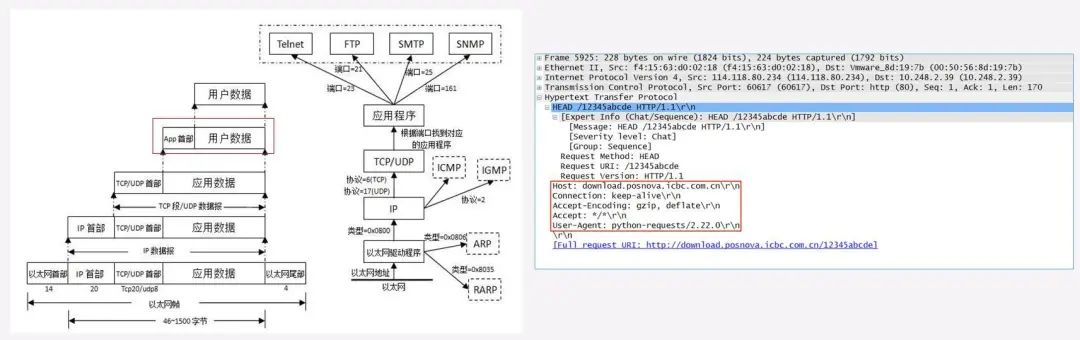
Data Encapsulation – TCP Segment/UDP Datagram
Encapsulating application data with the TCP/UDP header into TCP segments/UDP datagrams corresponds to the transport layer in the OSI model as well as the TCP/IP model. This process provides End-to-End services, addressing issues such as datagram errors and packet sequencing.
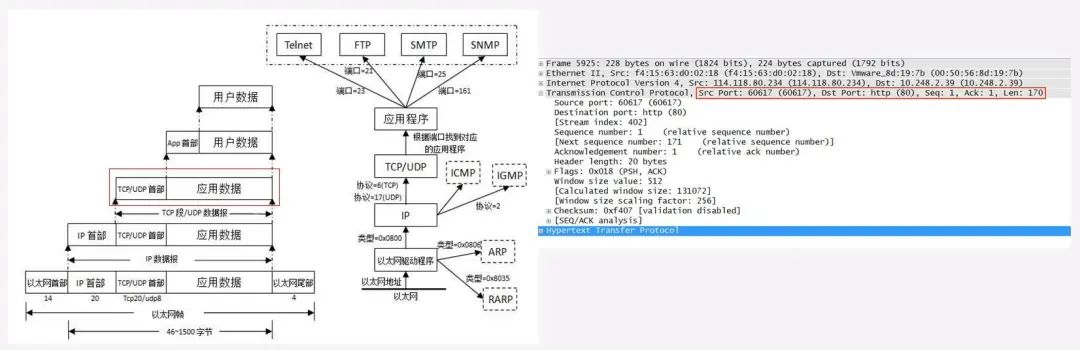
Data Encapsulation – IP Datagram
Encapsulating TCP segments/UDP datagrams with the IP header into IP datagrams corresponds to the network layer in the OSI model as well as the internet layer in the TCP/IP model. This process creates logical links for data transmission between nodes, selecting the best path for packets through routing algorithms to achieve functions such as congestion control and network interconnection.
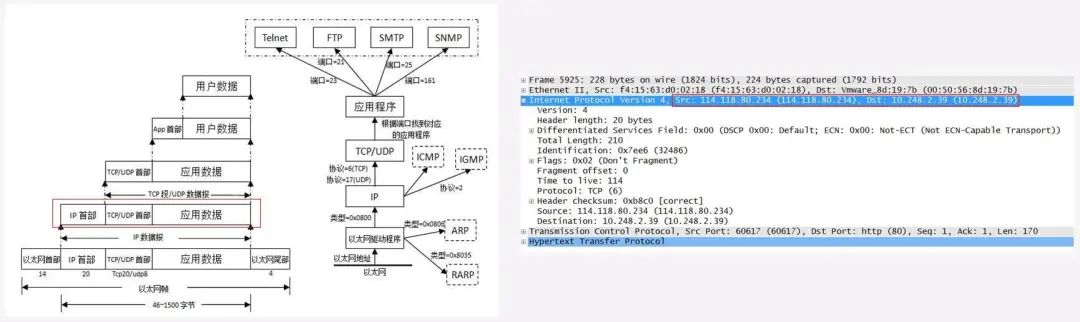
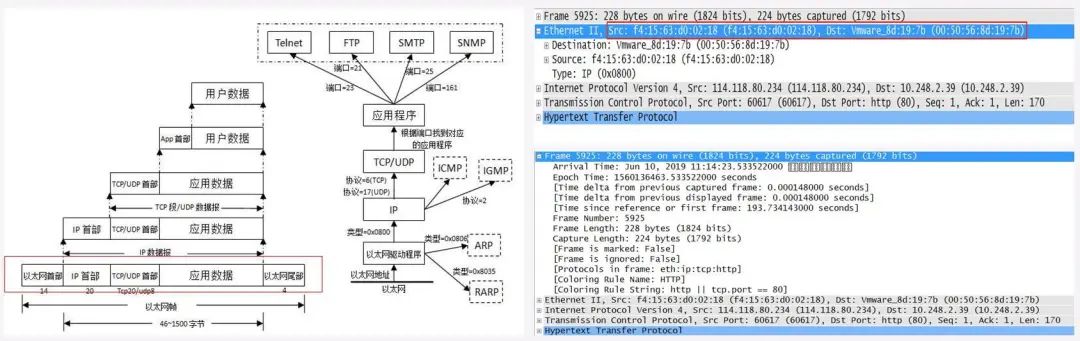
Data Encapsulation – Ethernet Frame
Encapsulating IP datagrams with Ethernet headers and trailers into Ethernet frames corresponds to the data link layer in the OSI model. This process establishes data link connections between communication entities, with the basic unit of transmission being a “frame,” and provides error control and flow control services to the Network Layer. Subsequently, these Ethernet packets will be transmitted to the receiving end through the Physical Layer.
Purpose and Significance of the OSI Reference Model
The OSI reference model employs a layered structural technique with the aim of logically grouping functions, allowing the issues of information exchange in open systems to be decomposed into a series of manageable hardware and software module layers. Each layer of the OSI reference model has independent functions and interfaces only with its adjacent layers for data communication.
In the field of information security, the OSI reference model can be referenced to classify network security characteristics corresponding to each layer, facilitating a systematic approach to analyzing and researching information network security risks. For example, network intrusions generally occur at the network layer, program vulnerabilities generally occur at the application layer, and data leaks generally occur at the data link layer, etc.
More Exciting Content
-
Risks Related to Financial Enterprises’ Self-Media Public Accounts
-
Discussion on the Principles and Exploitation of CVE-2019-0708 Remote Desktop Code Execution Vulnerability
-
The Next Decade’s C Position – Internet of Things
-
2019 Research Report on Cyber Financial Black Industry
-
“True Fragrance” Warning: Password Snatching Tools in Internal Network Penetration – Mimikatz


FCC30+
Long press the QR code on the left
Follow us to stay on track