From: Xia Yu
Link: blog.csdn.net/yulyu/article/details/69062288

Image from the internet
0 Introduction
Mastering TCP/IP and proficiently using Sockets for network programming.
Seeing this sentence, does it feel familiar? Many people have encountered this requirement when submitting their resumes, and many might think that such knowledge is generally unnecessary in actual development, thus dismissing it.
However, the author believes that to create better apps, one must have a certain understanding of these foundational concepts, allowing for more comprehensive and refined considerations. Let’s explore what TCP/IP is.
1 What is TCP/IP?
TCP/IP is a protocol suite, a set of protocols used for network communication.
Traditionally, TCP/IP is considered a four-layer protocol.
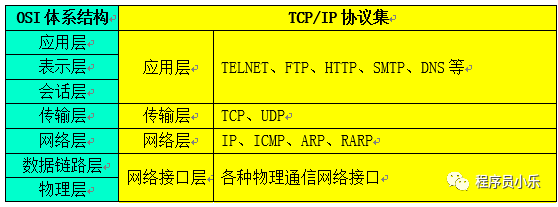
1) Network Interface Layer:
This primarily refers to some physical layer interfaces, such as cables.
2) Network Layer:
Provides hardware-independent logical addressing and implements the conversion between physical and logical addresses.
In the TCP/IP protocol suite, the network layer protocols include the IP protocol (Internet Protocol), ICMP protocol (Internet Control Message Protocol), and IGMP protocol (Internet Group Management Protocol).
3) Transport Layer:
Provides flow control, error control, and acknowledgment services for the network.
In the TCP/IP protocol suite, there are two distinct transport protocols: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
4) Application Layer:
Provides specific applications for network troubleshooting, file transfer, remote control, and Internet operations.
2 Data Packets
In the TCP/IP protocol, data is packaged from the top down and unpacked from the bottom up.
During packaging, each layer adds some information for transmission, known as headers. When the data from the upper layer reaches the current layer, it is packaged together with the current layer’s header and passed down.
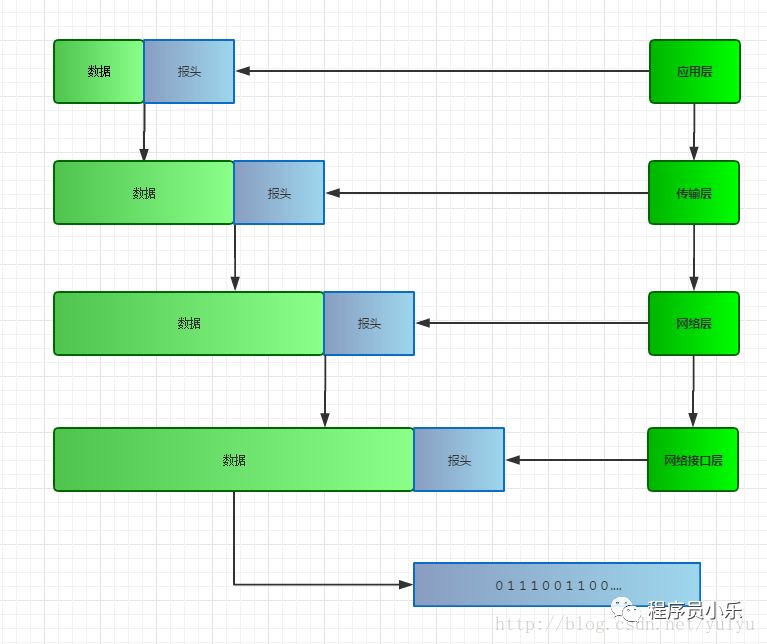
During unpacking, each layer reads the header it needs and passes the remaining data up.
This process is somewhat like Russian nesting dolls, which is why people sometimes use the term to describe it.

3 Network Interface Layer
This section mainly involves some physical transmission, such as Ethernet and wireless LAN. A detailed introduction will not be provided here.
4 Network Layer
As mentioned earlier, the network layer primarily performs the conversion between physical and logical addresses.
The most widely used in the market is the 32-bit binary IPv4. However, due to the exhaustion of IPv4 addresses, the 128-bit binary IPv6 is becoming increasingly common (the following introduction is based on IPv4).
1) IP:
Every network adapter on a TCP/IP network has a unique IP address.
An IP address is a 32-bit address, typically divided into four segments, with each segment containing 8 bits. For readability, each segment is usually converted to decimal, such as the well-known 192.168.0.1.
IP addresses consist of two parts:
-
Network ID
-
Host ID
However, there is no specification on which part belongs to the Network ID and which belongs to the Host ID.
Some networks require many hosts, meaning the part representing the Host ID must be larger, while others require fewer hosts, thus the Host ID part should be smaller.
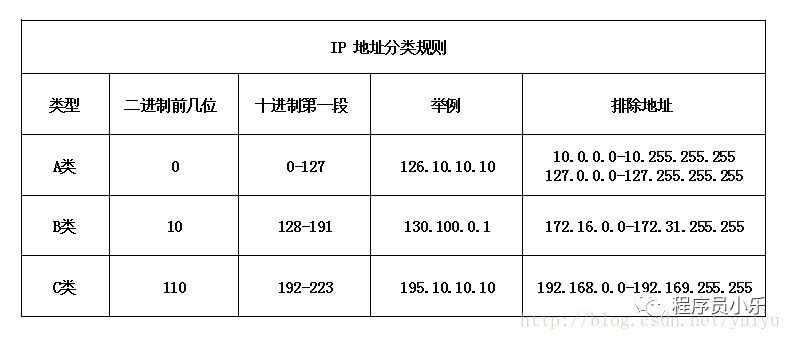
The vast majority of IP addresses fall into the following categories:
-
Class A Address: The first 8 bits of the IP address represent the Network ID, and the last 24 bits represent the Host ID.
-
Class B Address: The first 16 bits of the IP address represent the Network ID, and the last 16 bits represent the Host ID.
-
Class C Address: The first 24 bits of the IP address represent the Network ID, and the last 8 bits represent the Host ID.
It is evident that Class A addresses provide fewer Network IDs but allow for many hosts per network.
How can we determine which class an IP address belongs to?
-
If the 32-bit IP address starts with 0, it is a Class A address.
-
If the 32-bit IP address starts with 10, it is a Class B address.
-
If the 32-bit IP address starts with 110, it is a Class C address.
When converted to decimal (four segments), we can distinguish the class of the IP address based on the decimal number in the first segment.
Note:
-
Decimal numbers greater than 223 in the first segment belong to Class D and Class E addresses, which are special and uncommon, so they will not be elaborated on here.
-
Each class has some reserved addresses that do not belong to that class and are used in special situations (to be introduced later).
-
In addition to this method of classification, we can also divide each network into smaller blocks called subnets (to be introduced later).
A Host ID of all 0s represents the network itself; for example, an IP address of 130.100.0.0 indicates a Class B address with a Network ID of 130.100.
A Host ID of all 1s represents a broadcast address, used to send messages to all hosts in that network. An IP address of 130.100.255.255 is the broadcast address for the network with a Network ID of 130.100 (in binary, the IP address is all 1s, which converts to 255 in decimal).
Addresses starting with decimal 127 are loopback addresses. Messages sent to a loopback address are sent and received locally. This is mainly used to test whether TCP/IP software is functioning correctly. When using the ping function, the loopback address commonly used is 127.0.0.1.
2) Address Resolution Protocol (ARP)
In simple terms, the role of ARP is to map IP addresses to physical addresses, while the reverse ARP (RARP) maps physical addresses to IP addresses.
3) Subnetting
As mentioned earlier, the classification of IP addresses can lead to inefficiencies in network transmission due to the large number of hosts in Class A and Class B addresses. For example, a Class A address with an IP of 100.0.0.0 can have over 16 million hosts.
Thus, the introduction of subnet masks is to solve this problem.
Let’s review how to distinguish between Host IP and Network IP.
Taking the Class A address 99.10.10.10 as an example, the first 8 bits are the Network IP, and the last 24 bits are the Host IP (as shown below).
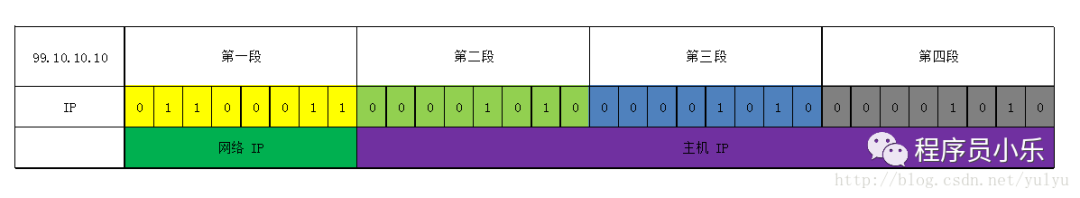
Subnet masks are also 32-bit binary numbers, which can be segmented into four decimal numbers. Each bit corresponds to the respective position of the IP address, where a value of 1 represents a non-host bit, and a value of 0 represents a host bit.
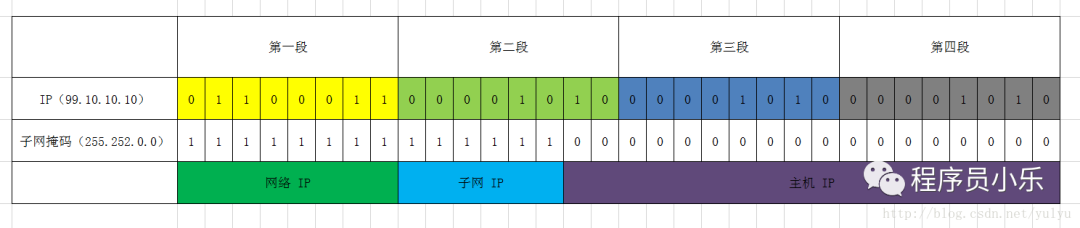
The table clearly shows that the Network IP is still determined by the previous classification, while the Host IP is determined by the number of bits in the subnet mask that are 0, and the remaining bits represent the Subnet IP.
5 Transport Layer
The transport layer provides two methods for reaching the target network.
-
Transmission Control Protocol (TCP): Provides comprehensive error control and flow control, ensuring data is transmitted correctly; it is a connection-oriented protocol.
-
User Datagram Protocol (UDP): Provides only basic error detection; it is a connectionless protocol.
Characteristics:
1) UDP:
-
Packages data
-
Data size is limited (64k)
-
No connection establishment
-
Fast speed but low reliability
2) TCP:
-
Establishes a connection channel
-
No data size limit
-
Slow speed but high reliability
Since the transport layer involves many aspects, such as ports and Sockets, which are essential for mobile development, we will cover these in detail in future articles, so we will not elaborate here.
6 Application Layer
The application layer, as the highest level of the TCP/IP protocol, is the most frequently encountered in mobile development.
Protocols running on TCP:
-
HTTP (Hypertext Transfer Protocol), primarily used for regular browsing.
-
HTTPS (Hypertext Transfer Protocol over Secure Socket Layer, or HTTP over SSL), the secure version of the HTTP protocol.
-
FTP (File Transfer Protocol), as the name suggests, is used for file transfers.
-
POP3 (Post Office Protocol, version 3), used for receiving emails.
-
SMTP (Simple Mail Transfer Protocol), used for sending emails.
-
TELNET (Teletype over the Network), used to log into the network via a terminal.
-
SSH (Secure Shell, used to replace insecure TELNET), used for secure encrypted logins.
Protocols running on UDP:
-
BOOTP (Boot Protocol), used for diskless devices.
-
NTP (Network Time Protocol), used for network synchronization.
-
DHCP (Dynamic Host Configuration Protocol), dynamically configures IP addresses.
Others:
-
DNS (Domain Name Service), used for address resolution, email forwarding, etc. (runs on both TCP and UDP).
-
ECHO (Echo Protocol), used for error checking and measuring response time (runs on both TCP and UDP).
-
SNMP (Simple Network Management Protocol), used for collecting network information and network management.
-
ARP (Address Resolution Protocol), used for dynamically resolving Ethernet hardware addresses.
If you find this useful, please don’t forget to share, like, and let more people learn. Your small effort is the best support for Xiao Le, thank you very much!
Recommended WeChat account for programmers
▼
Programmer Insider WeChat ID:
programmer0001
Recommendation:Here, we share technology related to programmers, workplace life, and industry hot news. We also occasionally share IT fun articles and images. This is a space for our programmers’ life, work, and entertainment. ▼ Long press the QR code below to follow
