Shenzhen Insight Wisdom Technology Co., Ltd.
This article explains and organizes the concept definition and development context of the Trusted Execution Environment (TEE), analyzes the comparison between TEE and cryptographic-based privacy protection technologies, and discusses its application in federated learning, finally introducing the existing frameworks and related applications of TEE.
With the rapid development of mobile internet and cloud computing technologies, more and more data are stored, shared, and computed in cloud environments. The security of data and privacy protection in cloud environments has gradually become a hot topic of concern in both academia and industry. Currently, privacy protection technologies mainly rely on cryptographic algorithms and protocols (such as secure multi-party computation, homomorphic encryption, etc.) to implement scenarios, which mainly have advantages in high security and reliability. However, these algorithms or protocols rely on a large number of complex computations (such as multiplication on cyclic groups, exponentiation, pairing operations, mathematical operations on lattices, etc.), leading to significant performance bottlenecks, making large-scale application in practical scenarios difficult.
As an alternative to cryptographic-based privacy protection technologies, the Trusted Execution Environment (TEE) implements secure computing based on memory isolation using hardware-secured CPUs, allowing privacy-preserving computations to be completed while ensuring computational efficiency.
This article will clarify and organize the definition and development context of TEE, analyze the comparison between TEE and cryptographic-based privacy protection technologies, and discuss its application in federated learning, and finally introduce the existing frameworks and related applications of TEE.
1. Definition and Development Context of TEE
Concept and Distinction: TEE vs REE
TEE is an independent processing environment with computational and storage capabilities that can provide security and integrity protection. The basic idea is to allocate a separate isolated memory block for sensitive data in hardware, where all computations involving sensitive data are performed, and other parts of the hardware cannot access the information in this isolated memory except through authorized interfaces. This achieves privacy computing for sensitive data.
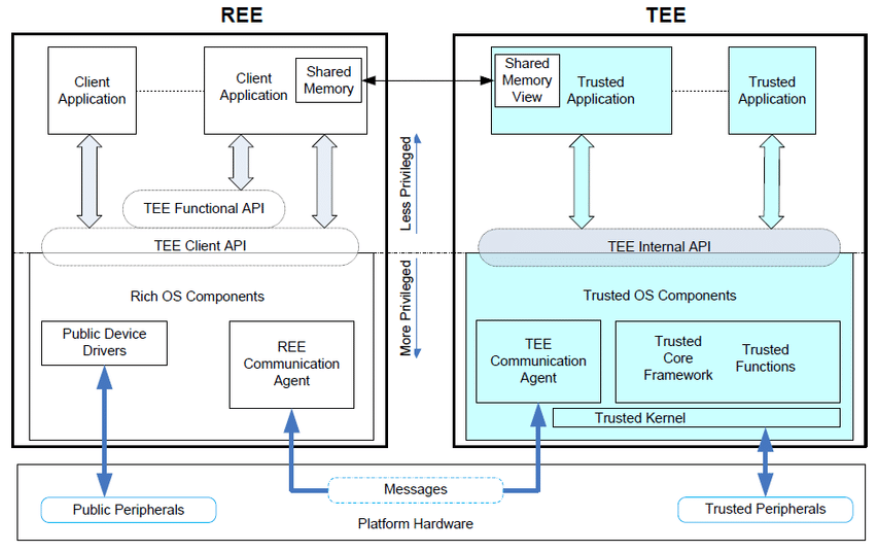
The Rich Execution Environment (REE) refers to the environment in which the operating system runs, allowing general operating systems (such as Android, iOS, etc.) to operate. REE is an open environment that is easily attacked, such as sensitive data theft and mobile payment fraud. In contrast, TEE is a secure area on the central processing unit that ensures sensitive data is processed in an isolated and trusted environment, thus protecting it from software attacks from REE. Additionally, compared to other secure execution environments, TEE can end-to-end protect the integrity and confidentiality of Trusted Applications (TA), providing stronger processing capabilities and greater memory space. In the typical architecture of a trusted execution environment shown below, TEE provides interfaces for software in REE, allowing it to call TEE to process data without leaking sensitive information.
Diagram of TEE and REE Relationship
The powerful data security and privacy protection capabilities of TEE make it one of the main technical streams in privacy computing, gaining broader application than REE.
After discussing the concept of TEE, we further analyze its deeper definition. There are many forms of definitions for TEE, which vary based on different security requirements and platforms. However, all definitions of TEE include two critical points: an independent execution environment and secure storage. In the GlobalPlatform, TEE System Architecture, 2011, GlobalPlatform defines TEE as follows: TEE is an execution environment that runs in parallel to the device’s operating system but is isolated from it. TEE can protect the data within it from general software attacks, and it can be implemented using various technologies, with different security levels depending on the underlying technology used.
At the IEEE International Conference on Trust 2015, Mohamed Sabt et al. provided a new, more generalized definition of TEE using a separation kernel. The separation kernel was first used to simulate distributed systems and must meet the following security criteria:
1. Data Separation: Data stored in one partition cannot be read or modified by other partitions.
2. Temporal Separation: Data in the public resource area does not leak information from any partition.
3. Control of Information Flow: Communication between partitions is not allowed unless specifically permitted.
4. Fault Isolation: Security vulnerabilities in one partition cannot spread to other partitions.
Based on the security characteristics of the separation kernel, TEE can be defined as “an immutable execution environment running on a separation kernel.” This means that TEE can guarantee the security, authenticity, and integrity of its internal code; can prove its security to third parties; can resist nearly all software and physical attacks on the main system; and can effectively prevent attacks that exploit backdoor vulnerabilities.
Development Context and Current Status of TEE
The TEE technology can be traced back to 2006. The Open Mobile Terminal Platform (OMTP) first proposed a dual-system security solution for mobile terminals, which deploys two operating systems on the same terminal system, one being a conventional operating system and the other being an isolated secure operating system. The secure operating system runs in an isolated hardware environment, specifically processing sensitive information to ensure its security.
Building on the OMTP solution, ARM proposed a hardware virtualization technology called TrustZone and its related hardware implementation, releasing the TrustZone technology white paper for the first time in 2008. Currently, ARM is the most influential solution provider for mobile devices, and its TEE technology is leading in the industry: Qualcomm’s Snapdragon 835/845 series chips, HiSilicon’s Kirin 950/960 series chips, MediaTek’s HelioX20, X25, X30, and Samsung’s Exynos8890, 7420, 5433, and other mainstream mobile processors are all based on ARM architecture, and the TEE technology they use is also based on ARM architecture. Additionally, a relatively mainstream TEE product is Intel’s Software Guard Extensions (SGX).
In July 2010, Global Platform officially proposed the concept of TEE and began drafting relevant TEE standard specifications from 2011, designing a series of specifications for TEE system design, standardizing functions such as application interfaces, application processes, secure storage, and identity authentication. GP is a cross-industry international standard organization dedicated to formulating and publishing hardware security-based technical standards. The international standards developed and published by the GP organization are referred to as GP standards. In addition, GP has established a TEE testing and certification system to test the functionality of TEE products and issue certificates, with most Trust OS based on TEE technology internationally following GP’s standard specifications.
In China, UnionPay has been collaborating with the industry chain since 2012 to formulate standards across various levels, including TEE hardware, TEE operating systems, TEE basic services, and applications, and published the UnionPay TEEI standard after passing a review by the Technical Management Committee in 2015. In early 2017, the People’s Bank of China began formulating requirement standards for TEE at various levels. In July 2020, the China Academy of Information and Communications Technology released a standard titled “Technical Requirements and Testing Methods for Data Computing Platforms Based on Trusted Execution Environments,” jointly developed with 20 participating units.
2. TEE Compared with Other Privacy Computing Technologies
Comparison of TEE with Secure Multi-Party Computation and Homomorphic Encryption
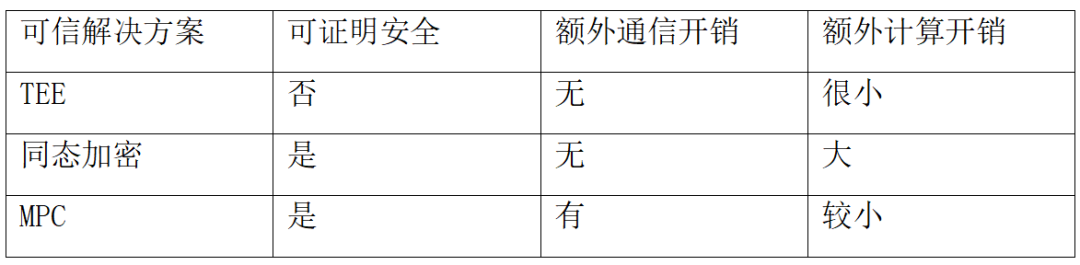
Secure multi-party computation (MPC) and homomorphic encryption are both privacy computing technologies that, like TEE, have their strengths.
MPC and homomorphic encryption are the two most mainstream privacy computing technologies in the field of cryptography. Both technologies can be proven secure based on mathematical difficulty assumptions, which gives them characteristics such as logical rigor, strong interpretability, and provable security. However, the enhancement of security leads to higher computational or communication complexity, which limits the usability of both technologies. For example, the computational overhead caused by large number operations on groups during the encryption and decryption process of homomorphic encryption, the increase in ciphertext length, and the communication overhead from multiple rounds of communication in secure multi-party computation technology, although there are many optimization solutions for these issues, the performance bottleneck has not been fundamentally resolved. Therefore, general-purpose MPC protocols are difficult to be widely applied in large-scale computing environments, and more often targeted at specific problems, such as Private Information Retrieval (PIR) and Private Set Intersection (PSI), while homomorphic encryption technology is mostly applied only to key steps of certain computational protocols.
Compared with MPC and homomorphic encryption, TEE can be seen as a combination of cryptography and system security, incorporating a cryptographic foundation at the bottom layer while combining hardware and system security at the upper implementation level. Its security derives from the ability of isolated hardware devices to resist attacks, while avoiding additional communication processes and the significant computational overhead of public-key cryptography. However, its disadvantage is that its security largely depends on the hardware implementation, making it difficult to define specific security boundaries, and it is more susceptible to side-channel attacks from different attack surfaces. Moreover, the current TEE security standards are mainly established by GlobalPlatform, and there are relatively few products certified for security by GlobalPlatform, making it challenging to further develop clear TEE security standards.
The comparison between TEE, MPC, and homomorphic encryption is shown in the table below:
Application of TEE in Federated Learning
As a hardware-based privacy computing technology, TEE can be integrated with federated learning to ensure computational efficiency and security.
Federated learning is a novel machine learning technology that has emerged in recent years, similar to distributed learning under privacy protection, where multiple parties collaboratively train a model using their own data, but the data of each party remains undisclosed. Its core idea is: the data does not move, but the model does; the data is available but not visible.
In horizontal federated learning, each party (party) needs to independently train a model based on the data in hand and then upload the gradients and other model parameters to the server for aggregation operations, subsequently generating a new model to distribute to each party. In this process, although the original data remains only with each party, attackers can recover the original data from the gradient information. To address this issue, most practical applications protect gradient information through noise addition or homomorphic encryption.
Additionally, TEE can replace the parameter server in the above scenario, performing federated learning parameter aggregation in a trusted execution environment. Assuming TEE is trusted, interaction between the trusted execution environment and computation nodes can be achieved through simple digital envelopes, thereby omitting the complex homomorphic encryption computation process and significantly improving the efficiency of federated learning training.
This article briefly introduces the application of TEE technology in federated learning using the FLATEE framework as an example. As shown in the figure below, in FLATEE, TEE can generate symmetric encryption keys and public keys for data and code transmission. Each party trains the model based on their own data in TEE, encrypts the model parameters using these keys, and uploads them to the server. After receiving the encrypted model parameters, the server decrypts the encrypted model in TEE, then aggregates to obtain a new model. If the loss function of the new model is below the threshold, the algorithm can be declared complete, and the new model is sent to each party encrypted with the keys generated by TEE; otherwise, a new round of iterative training is conducted until the maximum iteration count is reached or the model training is successful. In this model, TEE simultaneously performs the functions of encryption, decryption, and isolated computation, effectively ensuring the security of the federated learning algorithm without sacrificing computational efficiency.
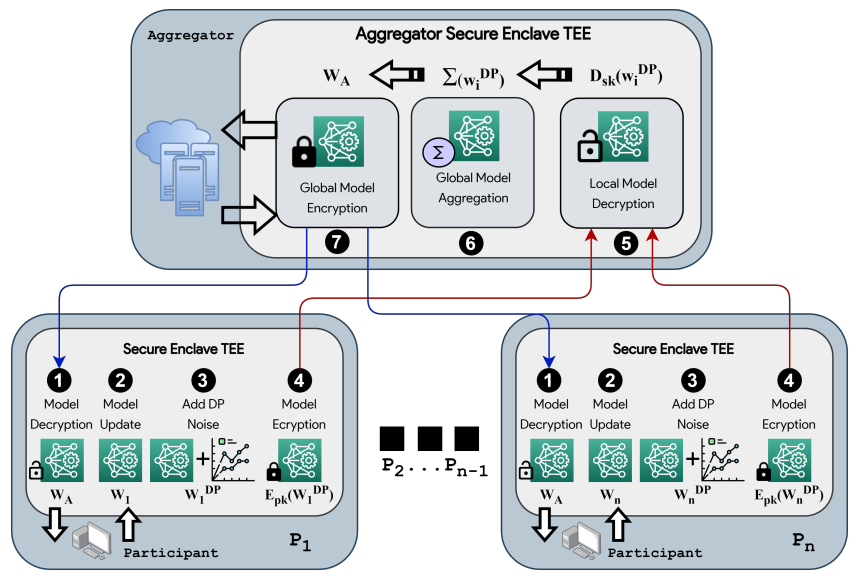
Image Source Literature 5
3. TEE Framework and Applications
As TEE technology and standards mature, development frameworks and applications based on TEE continue to emerge.
As shown in the table below, many companies have developed their respective TEE systems. Nokia and Samsung have publicly released their TEE frameworks. The TEE framework integrated by Nokia and Microsoft is called ObC, which has been deployed on Nokia’s Flowlight devices. Samsung’s TEE framework is named TZ-RKP and has been deployed on Samsung’s Galaxy series devices. Additionally, there are several undisclosed TEE frameworks, such as Trustonic’s
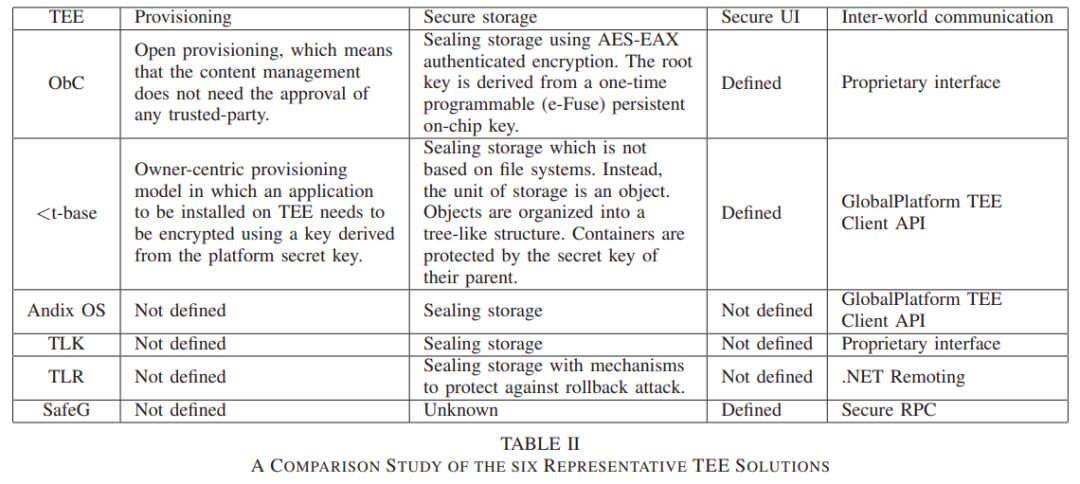
Table Source Literature 1
TEE can provide good security in a complex and interconnected system, with most TEE application scenarios currently directed towards smartphones. In this scenario, the security services that TEE can provide include: privacy-protecting ticketing services, online transaction confirmations, mobile payments, media content protection, cloud storage service authentication, etc. Moreover, TEE can also implement TPM (Trusted Platform Module) in purely software-based scenarios. A current research trend is to use TEE to secure various embedded system platforms, such as sensors and the Internet of Things.
Hardware-based TEE technology has a high implementation efficiency, but it also leads to a reliance on the underlying hardware architecture. Compared to general secure multi-party computation, TEE has the following advantages and disadvantages:
-
The trusted hardware part can support multi-level, high-complexity algorithm logic implementation.
-
High computational efficiency, with only 3-4 times loss compared to plaintext computation, while technologies like MPC have hundreds of times the computational loss.
-
Can resist malicious adversaries.
-
The implementation of the solution relies on the underlying hardware architecture.
-
Updates and upgrades require simultaneous software and hardware upgrades.
-
The TEE technologies of different vendors vary, necessitating the formation of unified industry standards.
Based on the advantages and disadvantages of TEE technology, we can summarize that TEE technology is suitable for the following application scenarios:
-
Computational scenarios with relatively complex logic.
-
Large data volume, with high costs for data transmission and encryption/decryption.
-
High performance requirements, needing computations to be completed and results returned in a short time.
-
Privacy computing scenarios requiring trusted third-party participation, where data (partially or indirectly) can be obtained or inferred by trusted third parties.
-
Data transmission and usage environments that directly interact with the internet, needing to guard against external attacks.
-
Scenarios where the parties involved in data collaboration do not fully trust each other, with potential malicious attacks from participating parties.
Among the most common existing application scenarios are: authentication comparison of private identity information, large-scale cross-institutional joint modeling analysis of data, protection of data asset ownership, confidential computation on-chain data, and privacy protection for smart contracts.
As an emerging system security and privacy protection technology, TEE technology achieves a good balance between security and usability, serving as a better alternative under the limitations of traditional public key cryptography performance, and can be used as a trust root in some computational protocols to reduce the performance cost introduced by distrust.
However, currently, TEE technology cannot be applied as a universal security technology, mainly due to its security relying to some extent on trust in hardware vendors, as well as having multiple attack surfaces and unclear security boundary definitions, which are significant factors limiting its large-scale application. For users, it is essential to understand the application scenarios and limitations of TEE technology during its application process to avoid unforeseen security issues and financial losses.
[1] Sabt M, Achemlal M, Bouabdallah A. Trusted Execution Environment: What It is, and What It is Not[C]//2015 IEEE Trustcom/BigDataSE/ISPA. IEEE, 2015.
[2] Sun Nan. Implementation of Security Functions Based on Cryptographic Algorithms in Trusted Execution Environments[D]. Shandong University.
[3] GlobalPlatform, “TEE system architecture,” 2011. [Online]. Available: http://www.globalplatform.org/specificationsdevice.asp
[4] ARM Ltd, “Arm security technology – building a secure system using trustzone technology,” 2009.
[5] Mondal A, More Y, Rooparaghunath R H, et al. Poster: FLATEE: Federated Learning Across Trusted Execution Environments[C]//2021 IEEE European Symposium on Security and Privacy (EuroS&P). IEEE Computer Society, 2021: 707-709.

© THE END
For reprints, please contact this public account for authorization
Submissions or inquiries: [email protected]