Abstract
Various emerging technologies provide the potential for advancing the development of hardware security concepts. A review of some emerging technologies includes spintronics, memristors, carbon nanotubes and related transistors, nanowires and related transistors, as well as 3D and 2.5D integration. These emerging devices share some interesting characteristics that are difficult to achieve with traditional CMOS technology. This article discusses the applications of emerging hardware security technologies in enhancing hardware security and outlines the associated challenges.
Keywords: hardware security, spintronics, memristors, carbon nanotubes, nanowire transistors, 3D integration, 2.5D integration, reverse engineering, tampering

1. Introduction
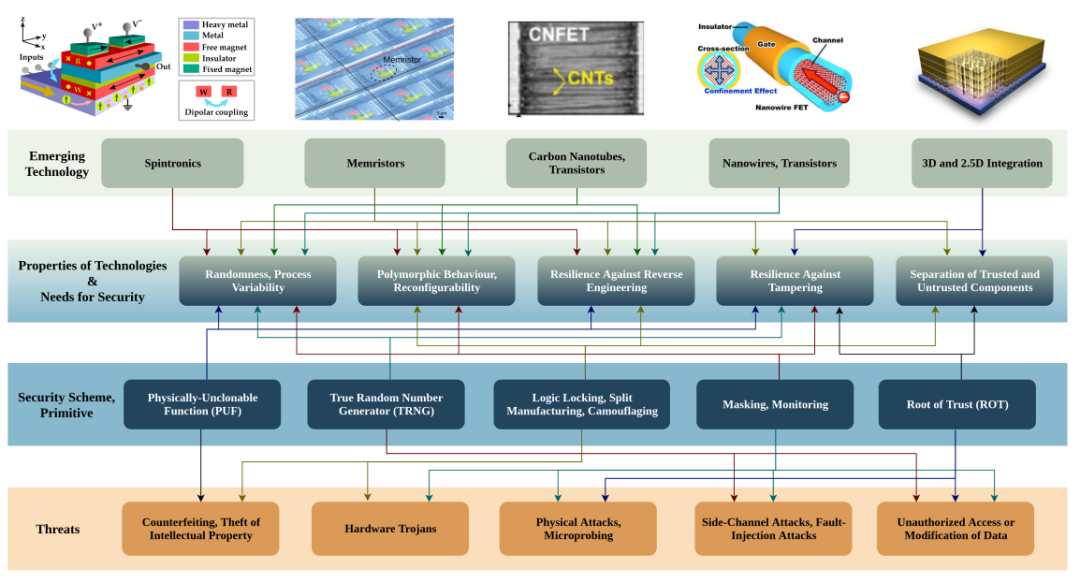
Figure 1
2. Emerging Devices
Table 1: Selected works on enhancing hardware security using 2.5D/3D integration
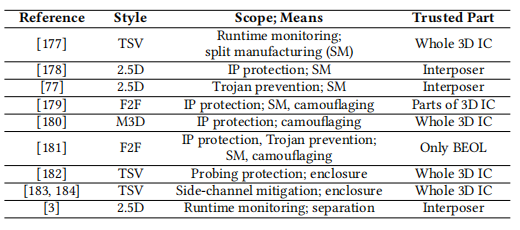
3. 3D and 2.5D Integration
This camouflage is achieved through virtual contacts, a method that has already been proposed in classical two-dimensional integrated circuits. Therefore, although not conceptually novel, the work in [22] leverages the benefits provided by M3D integrated circuits to strive for improved scalability of camouflage. This is noteworthy because camouflage in existing technologies may incur significant layout costs. In fact, such costs only consider a few gates to be camouflaged; while limited camouflage scales make such schemes vulnerable to SAT attacks. In contrast, the work reported in [22] consumes, on average, only 25% of the power, 15% of the delay cost, and 43% area savings compared to conventional 2D gates.
References
[1] J. Rajendran et al., “Nano meets security: Exploring nanoelectronic devices for security applications,” Proc. IEEE, vol. 103, no. 5, pp. 829–849, 2015. https: //doi.org/10.1109/JPROC.2014.2387353
[2] S. Ghosh, “Spintronics and security: Prospects, vulnerabilities, attack models, and preventions,” Proc. IEEE, vol. 104, no. 10, pp. 1864–1893, 2016. https://doi. org/10.1109/JPROC.2016.2583419
[3] F. Rahman et al., “Security beyond CMOS: Fundamentals, applications, and roadmap,” Trans. VLSI Syst., vol. PP, no. 99, pp. 1–14, 2017. https://doi.org/10. 1109/TVLSI.2017.2742943
[4] Q. Alasad, J. Yuan, and D. Fan, “Leveraging all-spin logic to improve hardware security,” in Proc. Great Lakes Symp. VLSI, 2017, pp. 491–494. https://doi.org/10. 1145/3060403.3060471
[5] T. Winograd et al., “Hybrid STT-CMOS designs for reverse-engineering prevention,” in Proc. Des. Autom. Conf., 2016, pp. 88–93. https://doi.org/10.1145/ 2897937.2898099
[6] S. Patnaik et al., “Spin-orbit torque devices for hardware security: From deterministic to probabilistic regime,” Trans. Comp.-Aided Des. Integ. Circ. Sys., vol. 39, pp. 1591–1606, 2019. https://doi.org/10.1109/TCAD.2019.2917856
[7] F. Parveen, Z. He, S. Angizi, and D. Fan, “Hybrid polymorphic logic gate with 5-terminal magnetic domain wall motion device,” in Proc. Comp. Soc. Symp. VLSI, 2017, pp. 152–157. https://doi.org/10.1109/ISVLSI.2017.35
[8] S. Patnaik et al., “Advancing hardware security using polymorphic and stochastic spin-hall effect devices,” in Proc. Des. Autom. Test Europe, 2018, pp. 97–102. https://doi.org/10.23919/DATE.2018.8341986
[9] N. Rangarajan et al., “Opening the doors to dynamic camouflaging: Harnessing the power of polymorphic devices,” Trans. Emerg. Top. Comp., vol. Early Access, 2020. https://doi.org/10.1109/TETC.2020.2991134
[10] A. Roohi and R. F. DeMara, “PARC: A novel design methodology for power analysis resilient circuits using spintronics,” Trans. Nanotech., vol. 18, pp. 885– 889, 2019. https://doi.org/10.1109/TNANO.2019.2934887
[11] A. S. Iyengar, S. Ghosh, and K. Ramclam, “Domain wall magnets for embedded memory and hardware security,” J. Emerg. Sel. Topics Circ. Sys., vol. 5, no. 1, pp. 40–50, 2015. https://doi.org/10.1109/JETCAS.2015.2398232
[12] N. Rangarajan, A. Parthasarathy, and S. Rakheja, “A spin-based true random number generator exploiting the stochastic precessional switching of nanomagnets,” J. Appl. Phys., vol. 121, no. 22, p. 223905, 2017. https://doi.org/10.1063/1.4985702
[13] N. Rangarajan et al., “SMART: A secure magnetoelectric antiferromagnet-based tamper-proof non-volatile memory,” vol. 8, pp. 76 130–76 142, 2020. https://doi. org/10.1109/ACCESS.2020.2988889
[14] H. Nili et al., “Hardware-intrinsic security primitives enabled by analogue state and nonlinear conductance variations in integrated memristors,” Nature Electronics, vol. 1, no. 3, pp. 197–202, 2018. https://doi.org/10.1038/s41928-018-0039-7
[15] A. Rezaei, J. Gu, and H. Zhou, “Hybrid memristor-CMOS obfuscation against untrusted foundries,” in Proc. Comp. Soc. Symp. VLSI, 2019, pp. 535–540. https: //doi.org/10.1109/ISVLSI.2019.00102
[16] L. Liu, H. Huang, and S. Hu, “Lorenz chaotic system-based carbon nanotube physical unclonable functions,” Trans. Comp.-Aided Des. Integ. Circ. Sys., vol. 37, no. 7, pp. 1408–1421, 2018. https://doi.org/10.1109/TCAD.2017.2762919
[17] C. K. H. Suresh, B. Mazumdar, S. S. Ali, and O. Sinanoglu, “A comparative security analysis of current and emerging technologies,” Micro, vol. 36, no. 5, pp. 50–61, 2016. https://doi.org/10.1109/MM.2016.87
[18] Y. Bi et al., “Emerging technology-based design of primitives for hardware security,” J. Emerg. Tech. Comp. Sys., vol. 13, no. 1, pp. 3:1–3:19, 2016. https: //doi.org/10.1145/2816818
[19] S. Rai et al., “Security promises and vulnerabilities in emerging reconfigurable nanotechnology-based circuits,” Trans. Emerg. Top. Comp., vol. Early Access, 2020. https://doi.org/10.1109/TETC.2020.3039375
[20] Y. Cui et al., “Encoding molecular information in plasmonic nanostructures for anti-counterfeiting applications,” Nanoscale, no. 6, pp. 282–288, 2014. https: //doi.org/10.1039/C3NR04375D
[21] J. Knechtel, S. Patnaik, and O. Sinanoglu, “3D integration: Another dimension toward hardware security,” in Proc. Int. On-Line Test Symp., 2019, pp. 147–150. https://doi.org/10.1109/IOLTS.2019.8854395
[22] C. Yan et al., “Hardware-efficient logic camouflaging for monolithic 3D ICs,” Trans. Circ. Sys., vol. 65, no. 6, pp. 799–803, 2018. https://doi.org/10.1109/TCSII. 2017.2749523
[23] J. Dofe et al., “Security threats and countermeasures in three-dimensional integrated circuits,” in Proc. Great Lakes Symp. VLSI, 2017, pp. 321–326. https: //doi.org/10.1145/3060403.3060500
[24] Y. Xie, C. Bao, and A. Srivastava, “Security-aware 2.5D integrated circuit design flow against hardware IP piracy,” Computer, vol. 50, no. 5, pp. 62–71, 2017. https://doi.org/10.1109/MC.2017.121
[25] P. Gu et al., “Cost-efficient 3D integration to hinder reverse engineering during and after manufacturing,” in Proc. Asian Hardw.-Orient. Sec. Trust Symp., 2018, pp. 74–79. https://doi.org/10.1109/AsianHOST.2018.8607176
[26] S. Patnaik, M. Ashraf, O. Sinanoglu, and J. Knechtel, “A modern approach to IP protection and trojan prevention: Split manufacturing for 3D ICs and obfuscation of vertical interconnects,” Trans. Emerg. Top. Comp., vol. Early Access, 2019. https://doi.org/10.1109/TETC.2019.2933572
[27] J. Dofe, Q. Yu, H. Wang, and E. Salman, “Hardware security threats and potential countermeasures in emerging 3D ICs,” in Proc. Great Lakes Symp. VLSI, 2016, pp. 69–74. https://doi.org/10.1145/2902961.2903014
[28] M. Wang, A. Yates, and I. L. Markov, “SuperPUF: Integrating heterogeneous physically unclonable functions,” in Proc. Int. Conf. Comp.-Aided Des., 2014, pp. 454–461. https://doi.org/10.1109/ICCAD.2014.7001391
[29] C. Wang et al., “TSV-based PUF circuit for 3DIC sensor nodes in IoT applications,” in Proc. Electron. Dev. Solid State Circ., 2015, pp. 313–316. https://doi.org/10.1109/ EDSSC.2015.7285113
[30] J. Dofe and Q. Yu, “Exploiting PDN noise to thwart correlation power analysis attacks in 3D ICs,” in Proc. Int. Worksh. Sys.-Level Interconn. Pred., 2018. https: //doi.org/10.1145/3225209.3225212
[31] J. Knechtel and O. Sinanoglu, “On mitigation of side-channel attacks in 3D ICs: Decorrelating thermal patterns from power and activity,” in Proc. Des. Autom. Conf., 2017, pp. 12:1–12:6. https://doi.org/10.1145/3061639.3062293
[32] P. Gu et al., “Thermal-aware 3D design for side-channel information leakage,” in Proc. Int. Conf. Comp. Des., 2016, pp. 520–527. https://doi.org/10.1109/ICCD. 2016.7753336
[33] C. Bao and A. Srivastava, “3D integration: New opportunities in defense against cache-timing side-channel attacks,” in Proc. Int. Conf. Comp. Des., 2015, pp. 273–280. https://doi.org/10.1109/ICCD.2015.7357114
[34] J. Rodriguez, A. Baldomero, V. Montilla, and J. Mujal, “LLFI: Lateral laser fault injection attack,” in Proc. Worksh. Fault Diag. Tol. Cryptogr., 2019, pp. 41–47. https://doi.org/10.1109/FDTC.2019.00014
[35] J. Knechtel, S. Patnaik, and O. Sinanoglu, “3D integration: Another dimension toward hardware security,” in Proc. Int. On-Line Test Symp., 2019, pp. 147–150. https://doi.org/10.1109/IOLTS.2019.8854395
Chinese Confidentiality Association
Science and Technology Branch
Scan to follow us

Author: Liu Siyuan
Editor: Xia Tian Tian
Top 5 Highlights of 2023
Cross-Network Attacks: Introduction to the Technology of Breaching Physical Isolation
Introduction to LaserShark Non-Contact Attack Implant Technology
Recent Highlights Review
Hardware Security of CMOS Technology
Out-of-Band Signal Injection Attacks Based on Sound
Applications of Artificial Intelligence in Cybersecurity
How Browser Fingerprinting Identifies Traffic from Web Crawlers
Overview of Key Technologies in Physical Layer Security