Click the blue text above Tanshi Laboratory
for more automotive cybersecurity news.
1.1 Fundamentals of Hardware Security
In today’s world, where information technology is ubiquitous and highly interconnected, cybersecurity is becoming increasingly challenging. For instance, with the rise of the Internet of Things (IoT), most such devices connect to the internet in some way, often making it difficult for ordinary users to understand the mechanisms behind them. As depicted in Figure 1.1, the vast number of attacks occurring in the real world over the years has indeed expanded the attack surface and can lead to severe consequences. In the field of cybersecurity, hardware security focuses on achieving security and trust directly through underlying electronic components. For example, researchers have warned about severe attacks on modern processors due to speculative execution [Koc+19a, Lip+18a], or analyzed the side-channel leakage issues of cryptographic hardware modules [Ler+18]. Additionally, many commercial computers and other custom devices utilize so-called Root of Trust (RoT) technologies for isolation and proof of computation [Mae+18, Zha+19, Nab+20].
Next, we will discuss the fundamental aspects of hardware security and review selected existing technologies, which will be regarded as common knowledge in the remaining chapters of this monograph.
It should be understood that this chapter can only provide an overview of this vast and rapidly evolving field, but we will focus on important technical aspects and the most groundbreaking protective schemes, allowing readers to acquire the necessary background knowledge to understand this monograph.
1.1.1 Runtime Data Security
The confidentiality, integrity, and availability of data processing in electronic products can be affected by various threats, such as (1) unauthorized access to or modification of data, (2) attacks exploiting side channels, fault injection, physical reading, or probing.
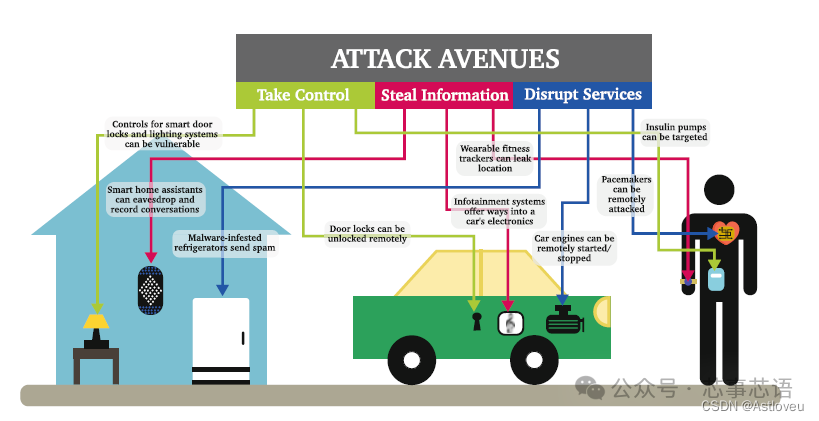
Figure 1.1 Modern hardware devices are deployed around us and connected to the internet, yet often lack built-in security concepts and measures. This brings numerous security risks to people’s daily lives. This figure is excerpted from [Gra16].
1.1.1.1 Unauthorized Access to or Modification of Data
Conventional attacks aimed at stealing or damaging data are primarily implemented at the software layer and interconnect systems. In this regard, cryptography represents a universally applicable protective scheme, but as shown below, there are also many dedicated, hardware-centric security features:
-
Isolation enclaves for trusted execution (TEEs), such as ARM TrustZone in the industry, Intel SGX, and the MIT Sanctum solution in academia (see Fig. 1.2; for more background on each TEE, see [Mae+18])
-
Wrappers for monitoring and cross-checking untrusted third-party intellectual property (IP) modules [Bas+17]
-
Centralized intellectual property protection (IP) infrastructure for secure system design [Wan+15b]
-
Computational verification [Wah+16]
-
Secure task scheduling [Liu+14]
-
Secure Network-on-Chip (NoC) architectures [Fio+08], etc.
However, without careful design and implementation, the aforementioned security features themselves are also susceptible to hardware-targeted attacks. Specifically, refer to chapters [BCO04, Bay+16, Qiu+19, OD19, CH17], which discuss such attacks in greater detail.
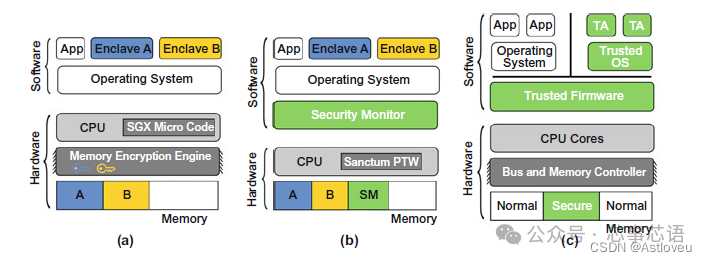
Figure 1.2 Isolation enclaves for trusted execution are typical hardware-centric security features. The figure shows (a) Intel SGX, (b) MIT Sanctum, and (c) ARM TrustZone’s high-level architectures.
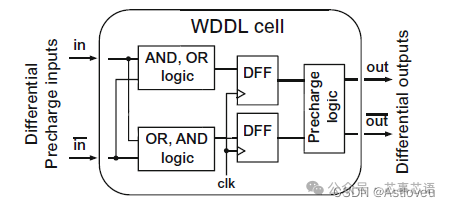
Figure 1.3 Wave Dynamic Differential Logic (WDDL) can be used to mitigate power side-channel attacks. This is achieved through redundant differential combinational logic paths that implement reverse switching for any operation, thereby masking the power consumption differences of specific state transitions. Additionally, precharging logic is used to reduce peak power consumption during switching. This figure is excerpted from [Fuj+14].
1.1.1.2 Side-Channel and Fault Injection Attacks
Due to the sensitivity and fragility of underlying electronic components, side-channel attacks can infer relevant information by exploiting leaks from physical channels [ZF05]. For instance, it is well-known that when hardware implementations are not protected, the Advanced Encryption Standard (AES) is vulnerable to power-based side-channel attacks [BCO04, OD19, SW12].
Another example concerns information leakage related to timing behavior in modern processors or speculative execution characteristics based on caches and buffers [OST05, Lip+18a, Sch+19].
Most security countermeasures against side-channel attacks employ some form of masking or shielding technique. This involves controlling the diffusion of information leaked through side channels.
Specific implementations can be achieved through various means, ranging from system-level solutions [GMK16] to individual gate circuits [Bel+18], as illustrated in Figure 1.3. However, the resilience of such countermeasures still depends on their overall physical implementation. For example, Fujimoto et al. [Fuj+14] demonstrated that even advanced WDDL schemes could be affected by slight asymmetries in layout, allowing attackers to ultimately deduce keys.
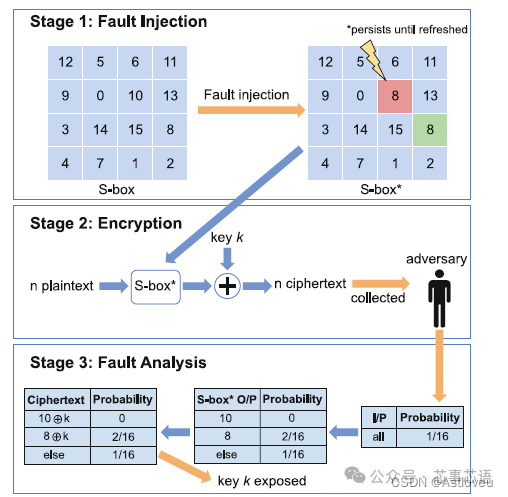
Figure 1.4 Multi-stage attacks on the AES algorithm. First, a random but persistent fault is injected into the S-box, causing subsequent encryption to deviate. Then, by sampling enough ciphertexts, this deviation can help infer the key. This figure is excerpted from [Pan+19].
Fault injection attacks induce faults to infer sensitive information. Therefore, refer to the example in Figure 1.4, where fault injection is also used to support or advance other attacks. Fault injection attacks include (1) direct, intrusive fault injection, such as through lasers [SHS16] or electromagnetic waves [CH17, Bay+16, Deh+12], and (2) indirect fault injection, such as through repeated writes to specific memory locations [Vee+16] or by intentionally “abusing” dynamic voltage and frequency scaling (DVFS) features [Qiu+19].
Security countermeasures include detection of runtime faults and implementing fortification measures against fault injection during the design and manufacturing phases [Kar+18b, LM06, Dut+18]. Note that distinguishing between naturally occurring faults and maliciously induced faults is not easy, posing practical challenges for runtime recovery.
1.1.1.3 Physical Reading and Probing Attacks
If attackers can access electronic components and implement invasions using traditional fault analysis or detection methods, such as optical probing or focused ion beam milling tools [Pri+17a], they can launch quite powerful read-out attacks. These attacks include:
(1) Probing transistors and wires through metal layers or the back of the substrate [Wan+17a, Hel+13]
(2) Monitoring photon emissions caused by CMOS transistor switching [Taj+17, Kra+21]
(3) Monitoring charges in memory [CSW16]
If applied carefully, these attacks can reveal all signals inside the device. For example, Figure 1.5 demonstrates the concept and examples of optical probing technology, allowing inference of bit data during device operation.
Security countermeasures aim to detect or prevent attackers’ physical access. Previous solutions attempted to place shielding structures in the back-end of line (BEOL) [Wan+19, Lee+19, YPK16], place deflection or scrambling structures in the substrate [She+18] (see also Figure 1.6), and detector circuits [Wei+18]. Earlier studies, such as [ISW03], also considered formal security techniques. However, this approach is limited by assumptions about the attacker’s capabilities, which may become outdated over time, rendering these formal guarantees ineffective.
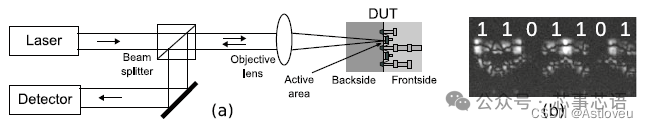
Figure 1.5 The concept (a) and example (b) of laser voltage probing, which serves to read bit data during device operation. In example (b), a set of registers is shown, where dark units store bit “0” and bright units store bit “1”. Subfigure (a) is excerpted from [Loh+16], (b) from related microscopic images provided by Shahin Tajik.
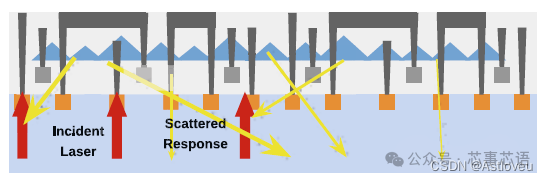
Figure 1.6 The concept of pyramid structures in silicon substrates, which can be achieved through dedicated etching steps. The result leads to the reflected light from incident lasers being scattered and mixed, making it more difficult to read data clearly. Excerpted from [She+18].
Source: Chip Matters
Professional Community

Recommended Events

More Articles
Don’t miss out, this could be the largest exclusive community in the automotive cybersecurity industry!
Lawyer’s statement regarding the alleged imitation of the AutoSec conference brand.
One article takes you through the onboard network communication security architecture of smart vehicles.
Cybersecurity: TARA methods, tools, and cases.
Key analysis of automotive data security compliance.
A brief analysis of security boot in automotive chip information security.
Exploring automotive onboard communication security solutions in domain-centralized architectures.
Vehicle network security architecture in system security architecture.
Privacy protection issues in the Internet of Vehicles.
Research on cybersecurity technologies for intelligent connected vehicles.
Analysis of the AUTOSAR information security framework and key technologies.
What are the information security mechanisms in AUTOSAR?
Underlying mechanisms of information security.
Automotive network security.
Usage of AUTOSAR hardware security modules (HSM).
First release! Lei Jun from Xiaomi offers suggestions on building a complete automotive data security management system during the two sessions.