
On October 17, 2016, the Ministry of Industry and Information Technology released the “Guidelines for Information Security Protection of Industrial Control Systems” to guide industrial enterprises in conducting industrial control security protection work. On January 19, 2024, the Ministry released a new version of the “Guidelines for Cybersecurity Protection of Industrial Control Systems” (hereinafter referred to as “the Guidelines”).The new version of the Guidelines has evolved from 30 protection guidelines across 11 aspects in the 2016 version to 33 protection guidelines across 4 aspects.
Compared to the 2016 version, which focused on the security protection of industrial control systems, the new version places greater emphasis on the security protection of industrial control systems in operational, management, and usage scenarios, aligning better with the security needs of industrial enterprises during the digital transformation process in the context of new industrialization. This article provides a detailed interpretation of the four major aspects of security management, technical protection, security operations, and responsibility implementation mentioned in the Guidelines and proposes solutions to help users better understand and apply the Guidelines.

Practice Leads to True Knowledge The Solutions of the Guidelines
The Guidelines include four aspects: security management, technical protection, security operations, and responsibility implementation, listing 33 specific protection guidelines. For ease of learning and reference, a structural summary of the Guidelines is provided below:
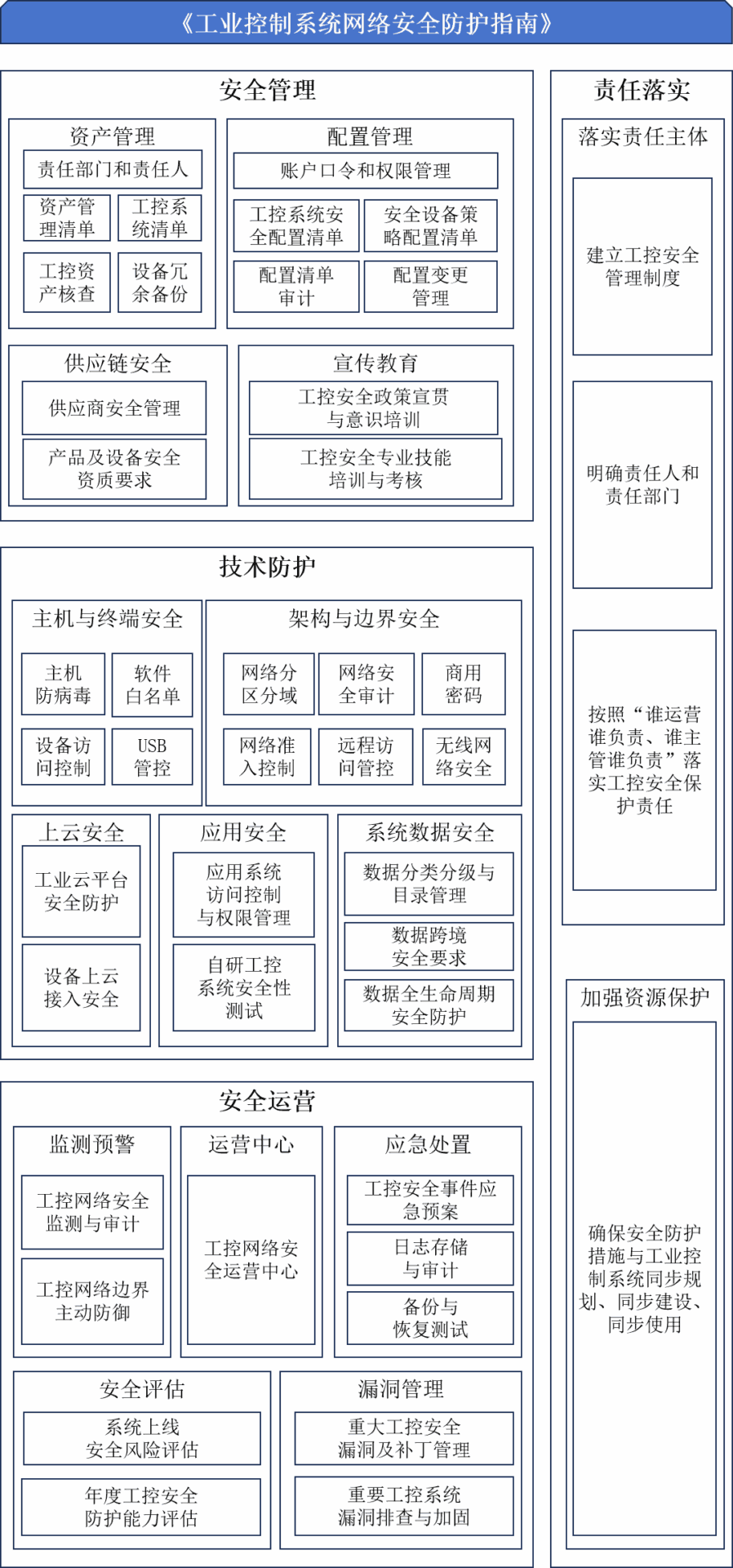
From the diagram, it can be seen that the guidance content of the Guidelines in various aspects is very concise, focusing on practicality, significantly reducing the complexity of reference practices for industrial enterprises, while comprehensively considering the needs of industrial enterprises in terms of cost, feasibility, and operability.
Security Management

In terms of security management, the management is highly targeted and content-focused, mainly focusing on assets, configuration, supply chain, and education.
1. Asset management and configuration management are important foundations for strengthening industrial control security management. Strengthening security management in these two areas can not only enhance the enterprise’s ability to respond to high-risk threats such as industrial control security vulnerabilities and ransomware but also effectively improve the enterprise’s traceability, emergency response, and recovery capabilities after a security incident.
2. Supply chain security is a blind spot that has been generally overlooked in industrial control security. The development of information technology and digitization has continuously expanded the number and types of enterprise suppliers. How to conduct security management for suppliers is also an important issue that needs to be addressed urgently, and security management requirements are an important step in supplier security management.
3. Personnel security is an important aspect of network security construction. Promoting security awareness and skills training is a vital means to enhance personnel security. The requirements for personnel security awareness and professional technical capabilities in industrial control security are more specialized and urgent.
Technical Protection

In terms of technical protection, there are no complex technical requirements; it directly addresses the weak links in industrial control security, offering highly targeted and practical guidance recommendations, emphasizing practical operations.
1. Hosts and terminals have been major disaster areas for industrial control security incidents in recent years, with ransomware and high-risk vulnerabilities commonly appearing in industrial host and terminal environments. Due to the special usage scenarios and environments, industrial enterprises have always been very cautious in host and terminal security protection. The Guidelines focus on strengthening protection capabilities for antivirus, software whitelisting, USB control, and device access, which not only aligns with users’ actual security concerns but also covers typical security risks and is a capability that relevant protective products can specifically implement.
2. The application of cloud platforms, the Internet of Things, and 5G networks has raised new requirements for industrial enterprises’ network architecture and boundary security. The Guidelines focus on security protection in scenarios such as network partitioning, wireless networks, remote access, and commercial password usage, which can further enhance the boundary security protection capabilities of enterprises.
3. Migrating industrial equipment to the cloud is an essential aspect of enterprises’ industrial Internet construction. The security threats and risks associated with this migration are also key focuses of industrial control security construction. The Guidelines provide corresponding suggestions regarding access requirements, processes, and environments for cloud migration.
4. Access to manufacturing execution systems (MES), configuration software, and industrial databases has become commonplace in the production processes of industrial enterprises. Security protection in terms of access control, permission management, and development iteration for these applications and software is also a key area that industrial enterprises need to strengthen.
5. System data security has not traditionally been a primary focus for industrial control security. However, recent emphasis by the Ministry of Industry and Information Technology on data security management in the industrial sector and the importance of data security in the digitalization process have made building capabilities around data security an essential foundational capability for industrial enterprises.
Security Operations

In terms of security operations, the Guidelines propose guidance recommendations from five aspects: monitoring and early warning, operation center, emergency response, security assessment, and vulnerability management, covering the basic needs of industrial enterprises’ security operations.
It is recommended that enterprises deploy monitoring and auditing equipment or platforms related to industrial control networks and adopt threat capture techniques such as honeypots for industrial control systems to enhance security monitoring, early warning, and proactive defense capabilities; encourage enterprises with conditions to establish industrial control system network security operation centers; emphasize emergency plans, log storage, and backup recovery capabilities to enhance enterprises’ emergency response capabilities to security incidents; regularly conduct security risk assessments and establish security vulnerability management mechanisms to enhance the enterprises’ own security immunity capabilities.
Responsibility Implementation

In terms of responsibility implementation, the Guidelines also provide a comprehensive plan for the responsibilities of industrial enterprises regarding industrial control security from the perspective of safety supervision, strictly adhering to the principle of “whoever operates is responsible, whoever supervises is responsible”, effectively implementing the responsibilities for industrial control security protection and strengthening resource guarantees for enterprises according to the principle of three synchronizations.

As the pace of digital transformation in industrial enterprises accelerates and the trend of open interconnection of industrial control systems becomes evident, the network security risks faced by industrial enterprises are increasing day by day. The release and implementation of the Guidelines will effectively enhance the baseline protection level of industrial enterprises in industrial control system cybersecurity, addressing prominent issues in cybersecurity faced during the new industrialization process. For many years, Qihoo 360 has been deeply engaged in the field of industrial control security, continuously making efforts in technology research and development, security research, and industry deepening, accumulating deep technical advantages and experience, providing more comprehensive, effective, and feasible solutions for the digital transformation of industrial enterprises, and ensuring the high-quality development of new industrialization.
•
END
•

