↑ Click on the above
“Smart Manufacturing Home”
Follow us

Written in Front
Hello everyone, I am Xiao Zhi, the owner of Smart Manufacturing Home~
Previously, we discussed the security of industrial control systems and analyzed the Modbus protocol and Siemens S7Comm protocol from a security perspective:
Data Collection under MES and SCADA—Analysis of Siemens S7comm Protocol
Confused about Modbus’s RTU, ASCII, TCP? This will be the most comprehensive analysis you’ve ever seen
Today, we will discuss how to understand security in industrial control from the perspective of the overall five-layer architecture. Whether you are currently engaged in ERP, PLM at the enterprise level, or MES/MOM at the management level, or DCS, SCADA, PLC at the monitoring and field control levels, security is with you. If you are still unclear about the five-layer architecture, please first refer to:
How Much Do You Know About Siemens Software—Counting How Much You Don’t Know About Siemens Software
This content mainly includes:
01 Security in the Five-Layer Architecture
02 Industrial Control Networks vs. Traditional IT Networks
03 Vulnerabilities of Industrial Control System Software, Hardware, and Protocols
04 Security Standards in Industrial Control Systems
05 Characteristics of Industrial Control System Network Security
06 Sharing of Industry Control Architecture Diagrams and Security Issues

01 Security in the Five-Layer Architecture
Industrial Control System Layered Model

This standard refers to the hierarchical model defined in IEC 62264-1 and categorizes the commonalities of models such as SCADA systems, DCS systems, and PLC systems, divided into five levels: the enterprise resource layer, production management layer, process monitoring layer, field control layer, and field device layer, with different real-time requirements for each level.
The enterprise resource layer mainly includes functional units such as ERP and PLM, providing decision-making tools for enterprise decision-makers;
The production management layer mainly includes MES system functional units for managing the production process, such as manufacturing data management and production scheduling management;
The process monitoring layer mainly includes monitoring servers and HMI system functional units for data collection and monitoring of the production process, utilizing HMI systems for human-machine interaction;
The field control layer mainly includes various controller units, such as PLCs and DCS control units, for controlling execution devices;
The field device layer mainly includes various process sensing devices and execution device units for perceiving and operating the production process.
Based on the different levels of the industrial control system architecture, the business applications, real-time requirements, and communication protocols between different levels vary, requiring different industrial control security products or solutions to be deployed, especially at the boundaries involving industrial control protocol communications that need protective measures. These products not only support fine-grained access control of industrial control protocols but also meet the real-time requirements of each level.
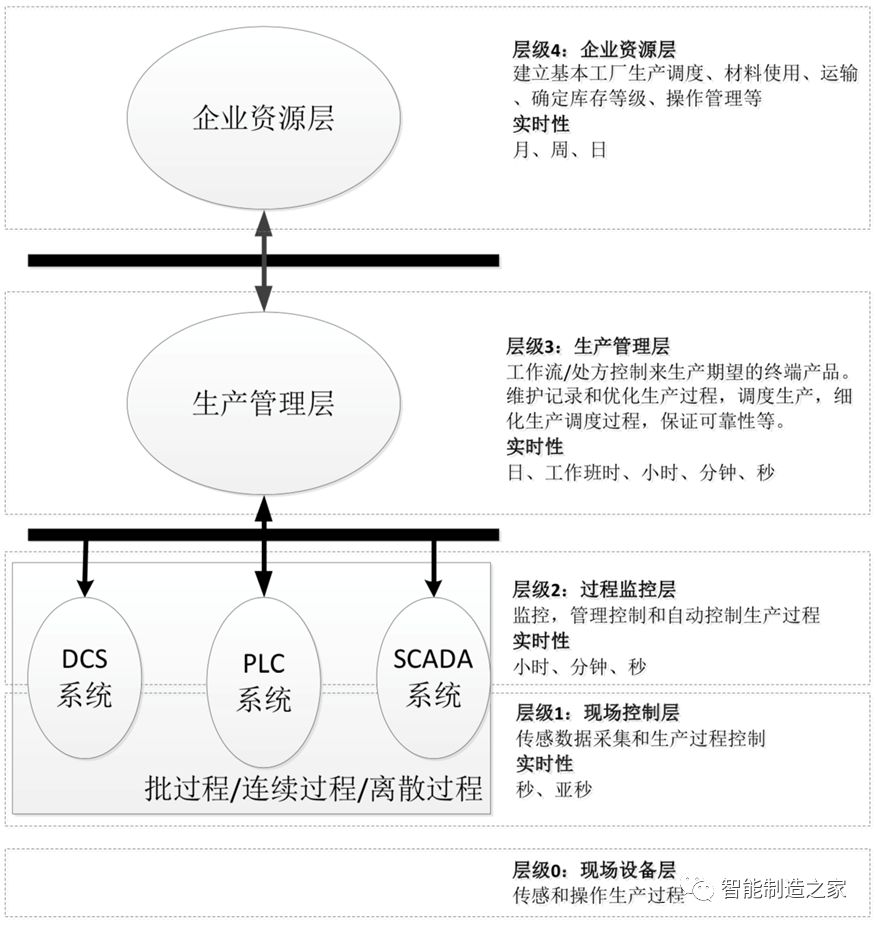
Typical Layered Architecture Model of Industrial Control Systems
This standard specifically notes that with the development of Industry 4.0 and cyber-physical systems, the aforementioned layered architecture is no longer fully applicable. Therefore, for different industries and enterprises, it allows for the merging of certain levels based on the actual development situation and can be judged according to the user’s actual scenario.
-
Mapping Relationships of Related Content
Considering the complexity of the components of industrial control systems, the diversity of networking, and the flexibility of the classification of protection objects, there is a demand for selection in the use of basic requirements for security level protection. This standard provides mapping relationships for the use of related content in each level, which can be referenced in practical applications:
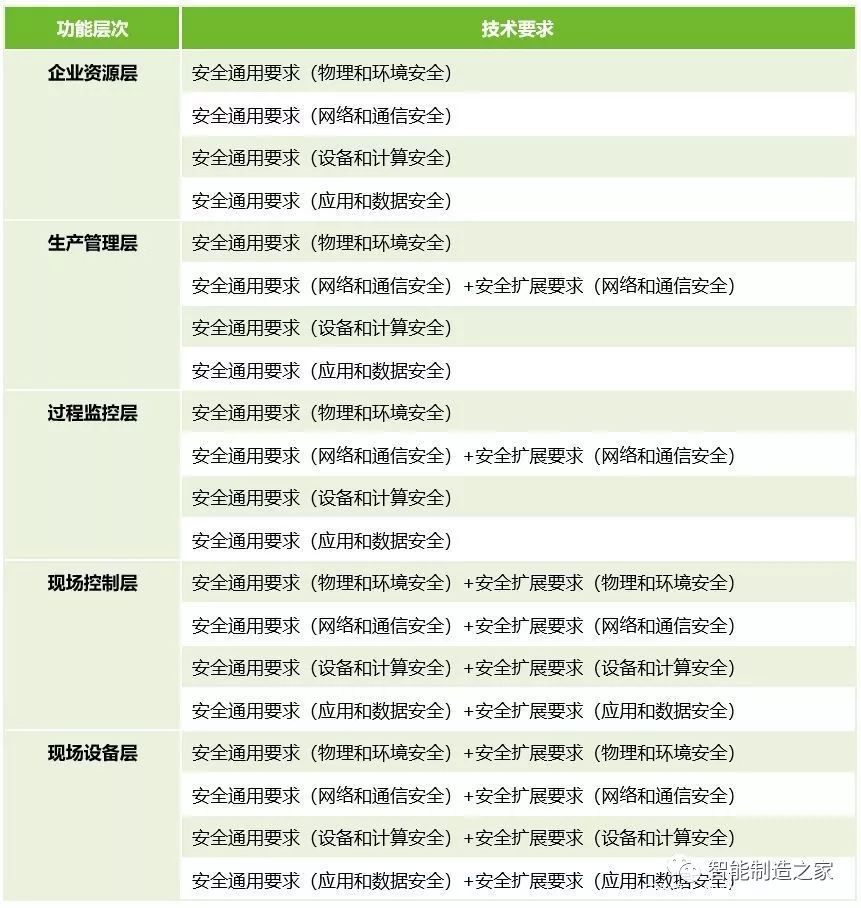

02 Industrial Control Networks vs. Traditional IT Networks
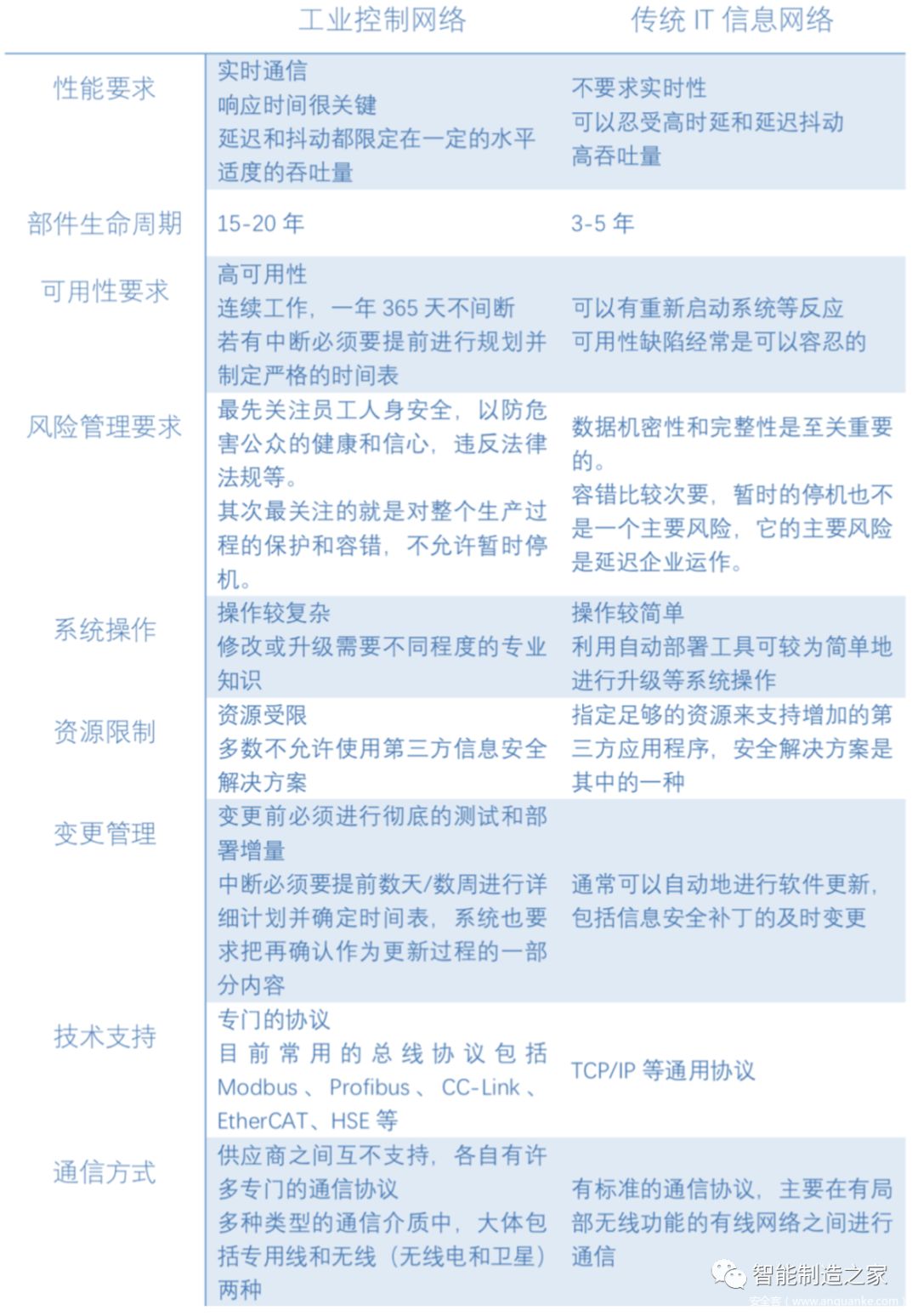
Differences Between Industrial Control Networks and Traditional IT Networks
Generally speaking, industrial control networks and traditional IT information networks differ mainly in three aspects: network edge, architecture, and transmission content.
Different network edges: Industrial control systems are widely distributed geographically, with their edge consisting of remote devices with low intelligence containing sensing and control functions, unlike the general-purpose computers at the edge of IT systems, which have significant differences in physical security requirements.
Different architectures: The structure of industrial control networks is vertically integrated, with a master-slave relationship between master nodes and terminal nodes. Traditional IT information networks are flat and peer-to-peer, with significant differences in the distribution of vulnerable nodes.
Different transmission contents: Industrial control networks transmit the “four remote information” of industrial equipment, namely remote measurement, remote signaling, remote control, and remote adjustment. Additionally, comparisons can be made between the two in terms of performance requirements, component lifecycle, and availability requirements, with detailed content as shown in Table 1.
Security in industrial control systems involves multiple disciplines including computer science, automation, communication, management, economics, and behavioral sciences, and has a broad research and application background. After the integration of IT and operational technology, the information security of IT systems has also been incorporated into the security of industrial control systems. Unlike traditional production safety (Safety), industrial control system network security (Security) aims to prevent and resist attackers from creating production accidents through malicious actions, harm, or casualties. It can be said that without industrial control system network security, there is no production safety in industrial control systems. Only by ensuring that the system is not subject to malicious attacks and destruction can the safety of the production process be effectively guaranteed. Although the security issues in industrial control networks are also caused by various malicious attacks, they differ significantly from the security issues in traditional IT systems.

03 Vulnerabilities of Industrial Control System Software, Hardware, and Protocols
Examples of Vulnerabilities Faced by Industrial Control Systems
1 Vulnerabilities in Industrial Control System Products (It can be said that almost 100% of industrial control systems have vulnerabilities)
Vulnerabilities in industrial control system products, such as Emerson RS3 vulnerabilities, SIEMENS PLC vulnerabilities. In the industrial field, due to the difficulty of software and hardware updates, upgrades, and replacements, vulnerabilities cannot be patched in a timely manner.
2 Protocol Defects of Modbus
Not only Modbus, but mainstream industrial control protocols like IEC104 and PROFINET also have some common issues. In pursuit of practicality and timeliness, many security features have been sacrificed, leading to hacker attacks.
3 Vulnerabilities of OPC Protocol (Non-OPC UA)
The OPC protocol is widely used in oil refining, steel plants, power generation, and precision manufacturing. While the OPC protocol brings convenience, it also has significant security risks. First, the OPC protocol architecture is based on the Windows platform, and the vulnerabilities and defects of the Windows system still exist in the OPC deployment environment. Moreover, to facilitate information exchange, all client sides use the same username and password to read data collected from the OPC server. Additionally, as long as the client connects, all data will be exposed, making information leakage very likely. In some less regulated deployment environments, the OPC server serves both real-time data for the site and data for the MES layer, meaning that the MES and site data share the same OPC database. If the MES is attacked, it can lead to a modification of a parameter in the OPC, affecting on-site operations.

04 Security Standards in Industrial Control
Reference Standards for Industrial Control Security
We have collected the standards and regulations mentioned below and other industrial control standards.
International Standards
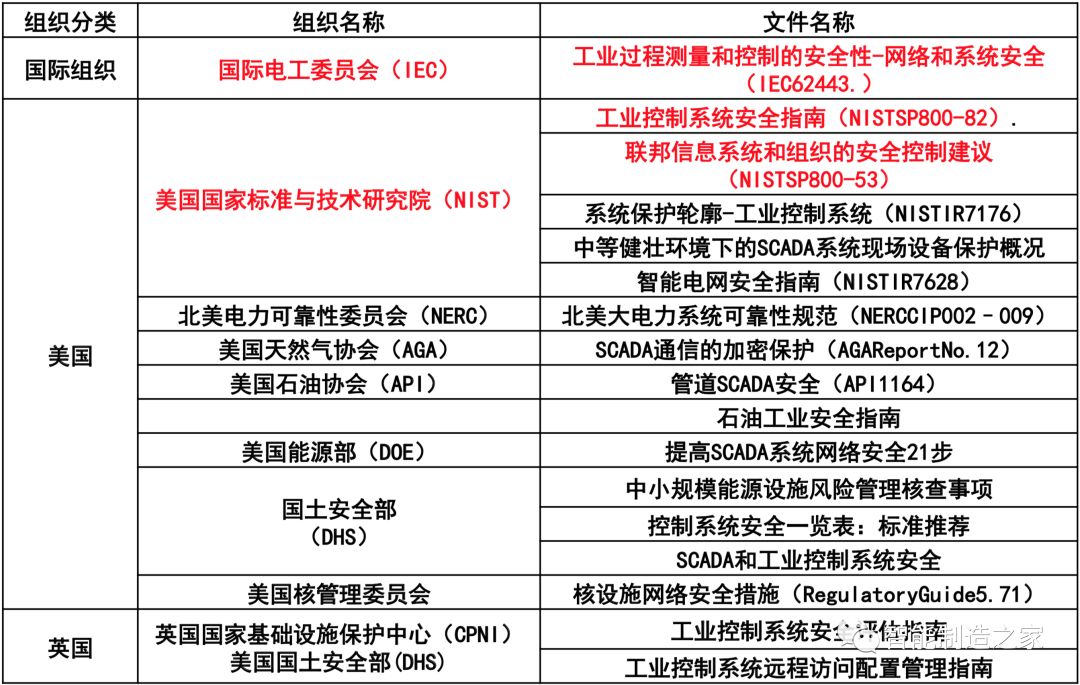
National Standards
-
“Guidelines for Information Security Protection of Industrial Control Systems”
The “Guidelines for Information Security Protection of Industrial Control Systems” is an important part of national network and information security, serving as a foundational guarantee for promoting China Manufacturing 2025 and the integration of manufacturing and the Internet. In October 2016, the Ministry of Industry and Information Technology issued the “Guidelines for Information Security Protection of Industrial Control Systems,” providing guidance for industrial enterprises to formulate industrial control security protection implementation plans. The formulation of this guideline is set against the backdrop of the deepening integration of manufacturing and the Internet in China, the prominent issues of information security in domestic industrial control systems, the issuance of multiple industrial control security standards, and the flourishing development of industrial control security technology, providing comprehensive guidance for industrial enterprises at a new height based on management, in-depth technology, and business combination.
-
“Action Plan for Information Security of Industrial Control Systems (2018-2020)”
The main goals of the action plan for information security of industrial control systems are: by 2020, firstly, to establish a security management system for industrial control, with clear responsibilities for enterprises and supervision responsibilities for various government departments, and a basically sound management mechanism. Secondly, to enhance the awareness of industrial control security throughout the system and industry, with a significant increase in the understanding of the hazards of industrial control security, treating it as an important part of production safety. Thirdly, to significantly improve the capabilities of situation awareness, security protection, and emergency response, fully strengthening the construction of the technical support system, establishing a national online monitoring network, an emergency resource library, a simulation testing platform, and an information sharing and reporting platform (one network, one library, three platforms). Fourthly, to promote the development of the industrial information security industry, enhance the supply capacity of the industry, cultivate a number of leading enterprises, and create 3-5 national new industrialization industry demonstration bases (industrial information security).
-
“Information Security Technology—Guidelines for Security Control Applications of Industrial Control Systems” (GB/T 32919-2016)
This standard was proposed by the National Information Security Standardization Committee (SAC/TC260) and is managed by the National Information Security Standardization Technical Committee. It is applicable to owners, users, designers, and information security management departments of industrial control systems, providing guidance for the design, implementation, and rectification of information security in industrial control systems, as well as reference for the operation, risk assessment, and security inspection of industrial control system information security. It facilitates the specification of security functional requirements for industrial control systems, laying the foundation for security design (including security architecture design) and security implementation.
-
“Information Security Technology—Basic Requirements for Network Security Level Protection Part 5: Extended Requirements for Industrial Control System Security”
This is essentially the equivalent of Level Protection 2.0, transforming the original standard “Information Security Technology—Basic Requirements for Information System Security Level Protection” into “Information Security Technology—Basic Requirements for Network Security Level Protection.” The level protection system has been shaped into a basic national policy and basic system for national network security in the new era. Important infrastructure systems and “cloud, IoT, mobile, big data, and industrial” are included in level protection supervision, incorporating Internet enterprises into level protection management, and detailing industrial control security in “Basic Requirements for Network Security Level Protection Part 5: Extended Requirements for Industrial Control System Security,” specifically describing contents such as the industrial control layered model.
-
GB/T 26333-2010 “Specification for Risk Assessment of Industrial Control Networks”
As China’s first national standard for industrial control security, this standard addresses the gap in China’s industrial control security standards, achieving a breakthrough from zero. This standard was issued in 2011, and its issuance shows the foresight of pioneers in China’s industrial control security. However, this standard has not been effectively implemented, becoming somewhat optional and a pioneer in the field of industrial control security standards. The reasons for this include the lack of core content in this standard (as core content is directly quoted from other standards), its overly simplistic nature, and low operability, making it difficult for this standard to be put into practice. It is recommended that relevant units revise this standard.
-
GB/T 30976.1-2014 “Information Security for Industrial Control Systems Part 1: Assessment Specification”
As China’s first national standard with content, this standard addresses the embarrassment of having no standards in industrial control security. The “Assessment Specification” is divided into management assessment and system capability (technical) assessment. Management assessments should refer to risk acceptance criteria and relevant organizational goals, identifying, quantifying, and prioritizing risks. The results of risk assessments should guide and determine appropriate management measures and their priorities, and the process of assessing risks and selecting control measures needs to be executed multiple times to cover different departments or industrial control systems. Management assessment is divided into three levels, and system capability (technical) assessment is divided into four levels. During the implementation of this assessment standard, there is currently no effective methodology to guide user units in determining the information security level they require, nor does the government have a basis for assessing information security levels. At this stage, the information security level can only be determined based on the spontaneous needs of user units, and then evaluation activities can be conducted based on the level confirmed by user units.
GB/T 30976.2-2014 “Information Security for Industrial Control Systems Part 2: Acceptance Specification”
This standard addresses the gap in China’s industrial control system information security acceptance, solving the dilemma of having standards to rely on for acceptance. The users of this standard are the users of industrial control systems, and the “Acceptance Specification” involves specialized security testing. Except for power and petrochemical industries, most users do not have the ability to complete security testing at the acceptance stage. Therefore, third-party evaluation forces are needed for acceptance, which raises project budget issues. Thus, when promoting the standard, it is necessary to consider acceptance standards and costs at the project initiation stage.
Industry Standards
Power Industry
In industrial control security, the power industry has implemented the State Electricity Regulatory Commission Order No. 5, “Regulations on the Safety Protection of Secondary Systems in Power”, which emphasizes “security zoning, dedicated networks, horizontal isolation, and vertical certification”. The petrochemical, nuclear power, and tobacco industries also have corresponding standards.
-
“Regulations on the Safety Protection of Power Monitoring Systems” (Order No. 14 of the National Development and Reform Commission of the People’s Republic of China)
The “Regulations on the Safety Protection of Power Monitoring Systems” were formulated to strengthen the information security management of power monitoring systems, preventing attacks and harms from hackers and malicious codes to ensure the safe and stable operation of power systems. This regulation was reviewed and approved by the director’s office of the National Development and Reform Commission of the People’s Republic of China, and was published on August 1, 2014, and came into effect on September 1, 2014.
-
“Overall Plan for the Safety Protection of Power Monitoring Systems” (State Energy Safety [2015] No. 36)
The “Overall Plan for the Safety Protection of Power Monitoring Systems” (State Energy Safety [2015] No. 36) is the latest safety specification document for the power system industry, proposing the safety protection plans for secondary systems at provincial dispatch centers, county-level dispatch centers, power plants, substations, and distribution, based on the principles of “security zoning, dedicated networks, horizontal isolation, and vertical certification,” comprehensively using firewalls, intrusion detection, host hardening, virus protection, log auditing, and unified management to provide a reliable environment for the safe and stable operation of secondary systems.
-
“Basic Requirements for Security Level Protection of Information Systems in the Power Industry” (Electricity Supervision Information [2012] No. 62)
In 2012, the power industry formulated its level protection standards, the “Basic Requirements for Security Level Protection of Information Systems in the Power Industry,” in accordance with national information security level protection standards and management specifications, combined with its industry status and characteristics, to guide the level protection work of information security in the industry.
-
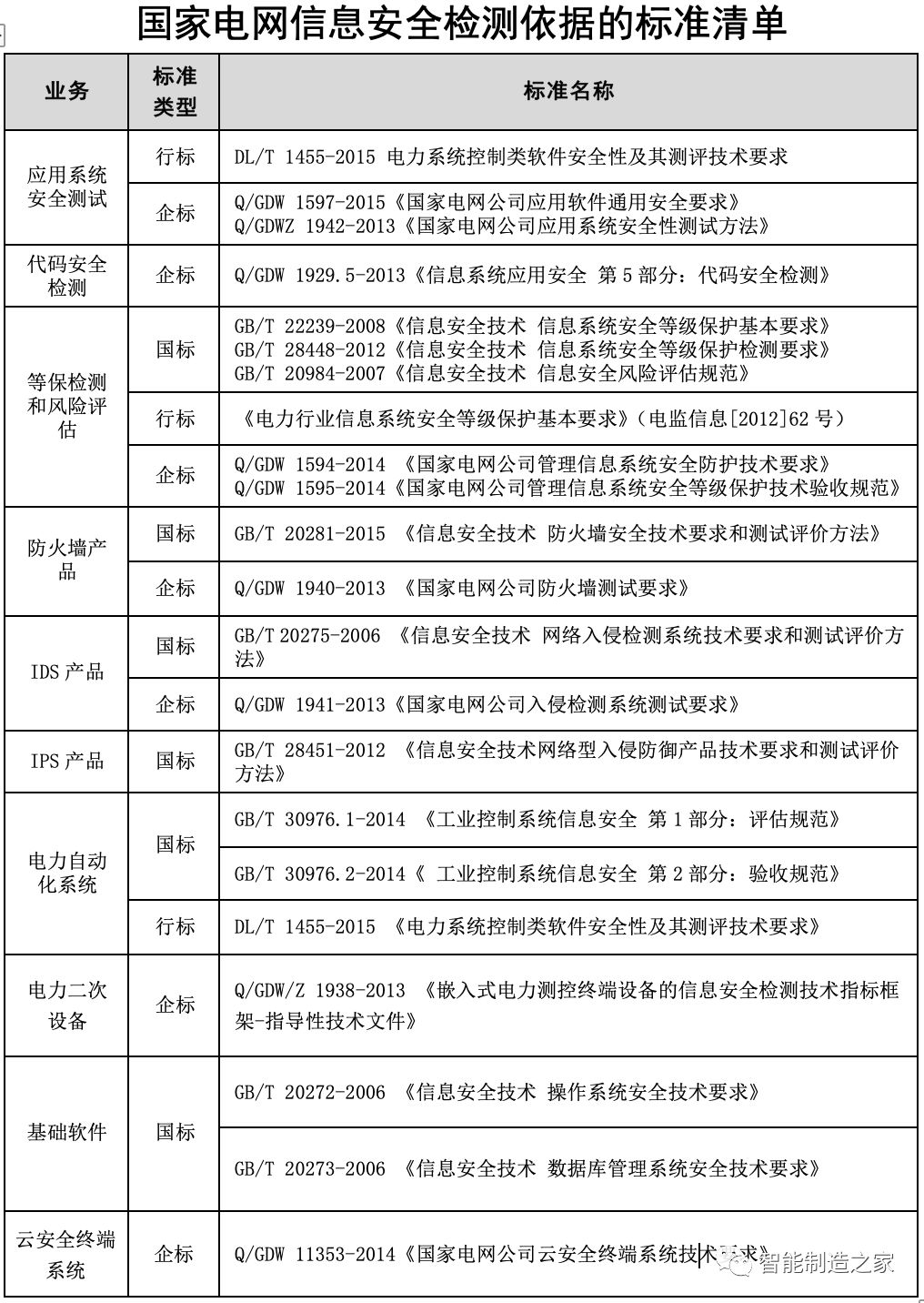
Other standards for information security testing of the State Grid (released by the State Grid in 2017)
Petrochemical Industry
-
GB/T 50609-2010 “Design Specifications for Information Systems in Petroleum and Chemical Plants”
This design specification requires safe isolation between networks and is one of the earlier industry standards emphasizing industrial control information security, issued in 2010.
Nuclear Power Industry
-
GB/T 13284.1-2008 “Safety Systems for Nuclear Power Plants Part 1: Design Guidelines”
-
GB/T 13629-2008 “Applicable Guidelines for Digital Computers in Safety Systems of Nuclear Power Plants”
The “Design Guidelines” provide guidelines that should be followed for the safety design of nuclear power plants. The standard specifies the minimum functional and design requirements for the power source, instruments, and control parts of the safety system of nuclear power plants, applicable to systems needed to prevent or mitigate the consequences of design basis events and to protect public health and safety. The “Applicable Guidelines” mainly set forth guidelines for the applicability of digital computers in safety systems of nuclear power plants.
Tobacco Industry
-
YC/T 494-2014 “Network Interconnection Security Specifications for Production and Management Networks in the Tobacco Industry”
This standard mainly regulates the network security issues between production networks and management networks in tobacco industrial enterprises.
-
“Baseline Technical Specifications for Network Security of Industrial Control Systems in the Tobacco Industry”

05 Characteristics of Industrial Control System Network Security
(1) Inherent Vulnerabilities of Industrial Control Systems
All major manufacturers’ industrial control products have vulnerabilities to varying degrees, and the industrial field faces difficulties in updating, upgrading, and replacing software and hardware.
Industrial control system protocols lacked security considerations from the outset, posing security threats such as plaintext design, lack of authentication, and misuse of function codes.
There are incomplete information security management regulations, with security threats from USB drive management, operational errors, and malicious operations.
(2) Long Construction Cycle of Industrial Control Systems
Typically, a large industrial project has a construction cycle of 5-10 years, and the period required for an industrial system to be constructed, debugged, and stabilized is long, making frequent upgrades impossible.
(3) Various Other Reasons
The integration of IT and operational technology has exposed industrial control systems to more traditional IT network threats.

06 Sharing Control Architecture Diagrams and Security Issues by Industry
Petrochemical Industry
(1) Operation stations, engineer stations, and servers use generic Windows systems, which are basically not updated with patches.
(2) DCS systems do not generally use identity authentication, rule checking, encryption transmission, or integrity checking when communicating with operation and engineer station systems.
(3) There is a lack of dynamic identification of OPC ports between the MES server at the production execution layer and the OPC server at the supervisory control layer, allowing any OPC client to connect to the OPC server and access any data.
(4) Engineer stations have very large permissions, and some are generic engineer stations that can perform operations on the control system as long as they are connected to the production network.
(5) Excessive network ports are not closed, and there is a lack of security boundary control when interconnecting industrial control networks.
(6) External operational activities lack auditing and supervision measures.
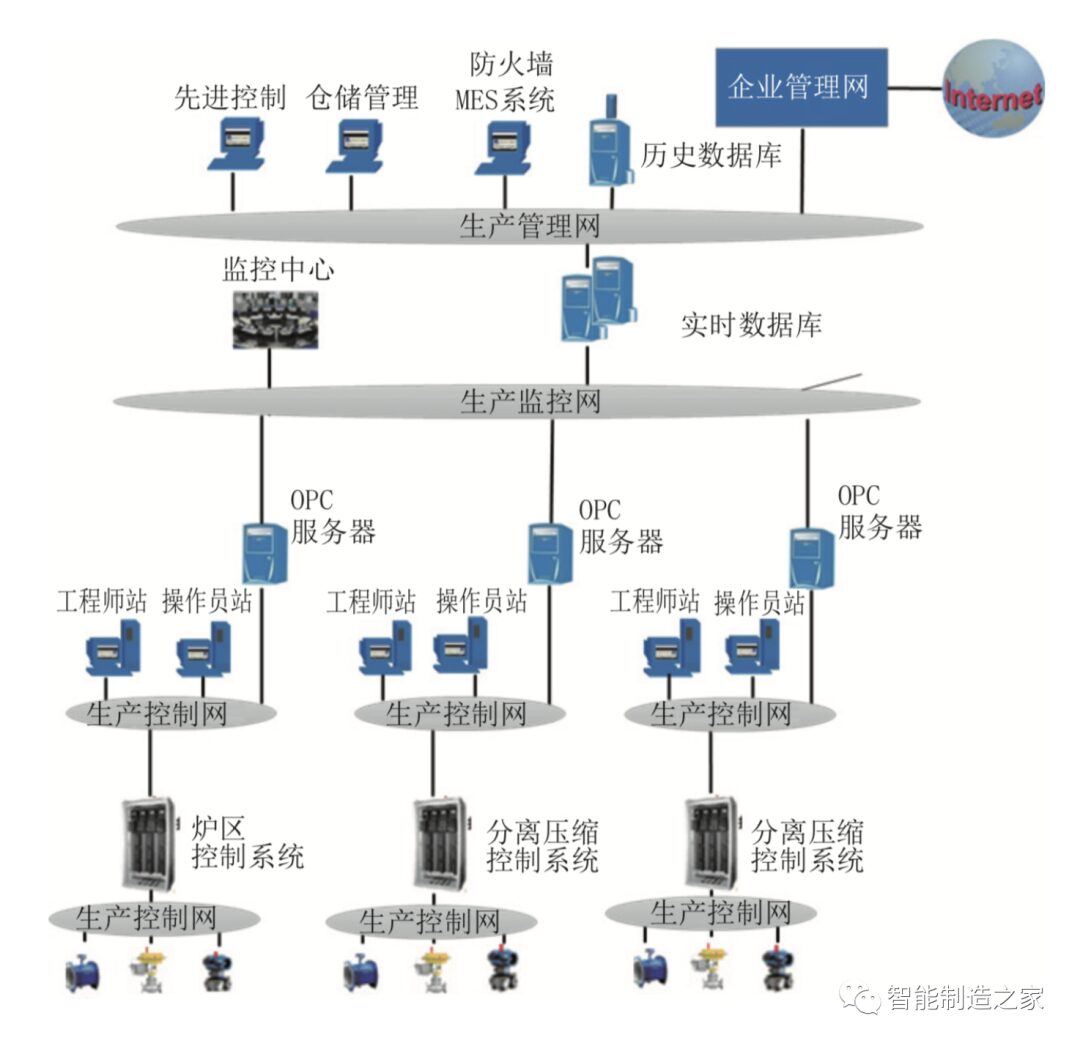
Structure Diagram of Industrial Control Systems in the Petrochemical Industry
6.2 Advanced Manufacturing
(1) Issues with default passwords for certain industrial control systems, such as SUNRISE, CUSTOMER, EVENING.
(2) Virus infections through operation stations.
(3) Serial port and network port conversions, where customized protocols are overly simplistic, lacking verification, and the risks of serial transmission environments, making abnormal business instructions difficult to detect.
(4) Data transmission, NC codes, and other file transfers have security vulnerabilities.
(5) DNC servers and other systems are placed together with office networks, using traditional databases installed on Windows systems, with extensive use of FTP for data interaction, posing risks of penetration.
(6) Third-party maintenance personnel lack audit records during equipment maintenance, posing threats of data leakage or virus intrusion.

Structure Diagram of Industrial Control Systems in Advanced Manufacturing
6.3 Power Industry
6.3.1 Current Status of Power Grid Security Construction
(1) Currently exploring information security protection for smart substations.
(2) Establishing a trusted computing password platform, updating dispatch digital certificates, vertical encryption authentication, horizontal isolation devices, firewalls, intrusion detection systems, and building a security simulation platform.
(3) Smart substation technology and distributed energy smart grids not only involve monitoring but also control. Power consumption information is transmitted over the Internet and requires encryption; users’ smart appliances exposed in the power system may be attacked.
(4) The IEC104 protocol is established between the power plant and provincial dispatching, but there are issues with protocol formats becoming chaotic in practical applications.
6.3.2 Risks Faced by Power Generation (Hydropower or Thermal Power)
(1) All power generation control systems are connected in one zone without any security protection measures.
(2) With the promotion of integrated construction of power generation plants, the risks caused by connectivity are increasing.
(3) Operation stations use generic operating systems without installed patches, making them susceptible to virus infections.
(4) OPC issues are similarly prominent.
(5) Remote maintenance issues still exist, with a lack of security operation audit devices.
The above content summarizes the security issues of industrial control in several industries. Based on this, we can further extract some common issues, as follows:
(1) No security domain division, with ambiguous security boundaries. Most industrial control systems lack isolation protection between subsystems and have not divided security zones based on the importance of areas and business needs, with unclear system boundaries and missing boundary access control policies. There is a lack of effective isolation measures between important network segments and other segments, making it impossible to control security threats within a specific area once a network security incident occurs.
(2) Vulnerabilities in operating systems, with insufficient host security protection. Engineer stations and operator stations are generally based on Windows platforms, including NT4.0, 2000, XP, Win7, Server2003, etc. Considering that antivirus software and system patches may affect the stable operation of control systems, even if antivirus software is installed, issues such as outdated virus databases can arise, leading to the decision not to install or run antivirus software. System patches are only updated or upgraded under special circumstances. Additionally, there is a lack of management for mobile storage media and software operating permissions, making control systems highly susceptible to virus infections.
(3) Insufficient security considerations for communication protocols, making them vulnerable to exploitation by attackers. Specialized industrial control communication protocols or standards generally focus only on communication real-time and availability, with little or no consideration for security issues, such as lacking sufficiently strong authentication, encryption, or authorization measures. This is especially true for wireless communication protocols in industrial control systems, which are more susceptible to eavesdropping and deceptive attacks by intermediaries. To ensure the real-time transmission of data, protocols like Modbus/TCP, OPC Classic, IEC 60870-5-104, DNP 3.0, Profinet, and EtherNet/IP often use plaintext transmission, making them easy to hijack and modify.
(4) Incomplete security policies and management systems, with insufficient personnel security awareness. Currently, most industries have not formed a complete and reasonable information security guarantee system and process, with insufficient consideration of information security requirements in all stages of planning, design, construction, operation, and evaluation of industrial control systems, and lacking supporting event handling processes, personnel responsibility systems, and supply chain management mechanisms. Furthermore, there is a lack of publicity and training on industrial control security, and insufficient emphasis on cultivating personnel security awareness. Industrial control systems often connect to various terminal devices, significantly increasing the risk of virus and Trojan infections, laying hidden dangers for the secure and reliable operation of the systems.
6.4 Pathways for Information Security Risks in Industrial Control Systems
Through the above analysis, it can be seen that industries such as advanced manufacturing, power generation, and petrochemicals generally have information security risks entering industrial control systems through several typical ports.
(1) Risks brought by “two-network connections.” Production networks connected to office networks, while control systems are separate systems, are interconnected to establish integrated control across the entire plant, with primary and auxiliary control systems all connected to one network, leading to significant risks from network interconnections.
(2) Risks brought by operation stations. Software installation, USB drive usage, and some human operational errors all enter through the operation and engineer station ports. For instance, engineer stations are often casually operated by duty personnel, leading to parameter misconfiguration.
(3) Risks from on-site and remote maintenance.
(4) Risks from industrial wireless. This risk is particularly evident in the rail transit industry.
References
https://www.kiwisec.com/news/detail/5c1c603bdb30c341099f28ab.html
https://www.venustech.com.cn/article/new_type/52.html
https://www.secrss.com/articles/3526
http://www.winicssec.com/Wap/Index/show/catid/57/id/456.html
“Industrial Control Network Security Technology and Practice” by Yao Yu, Zhu Liehuan, Wu Chuan Kun, Mechanical Industry Press
Industrial Control System Information Security – Automation Expo 2016/5
Liu Deli. Building an Industrial Information Security Barrier to Assist Aerospace Enterprises in Rapid Development[N]. China Aerospace News, 2019-02-28(003).
Source: Security Guest
Link: https://www.anquanke.com/post/id/178265

Multiple Benefits
If you have any materials related to smart manufacturing, you can download them atSmart Manufacturing Home Community and leave messages for communication~
Join the knowledge planetSmart Manufacturing Home, enhance your self-awareness, meet more friends, acquire more resources, and learn more skills~